Holistic Security in the Modern workplace Introduction https




























- Slides: 52

Holistic Security in the Modern workplace

Introduction https: //www. twitter. com/rvackooij/ https: //www. linkedin. com/in/rvackooij/

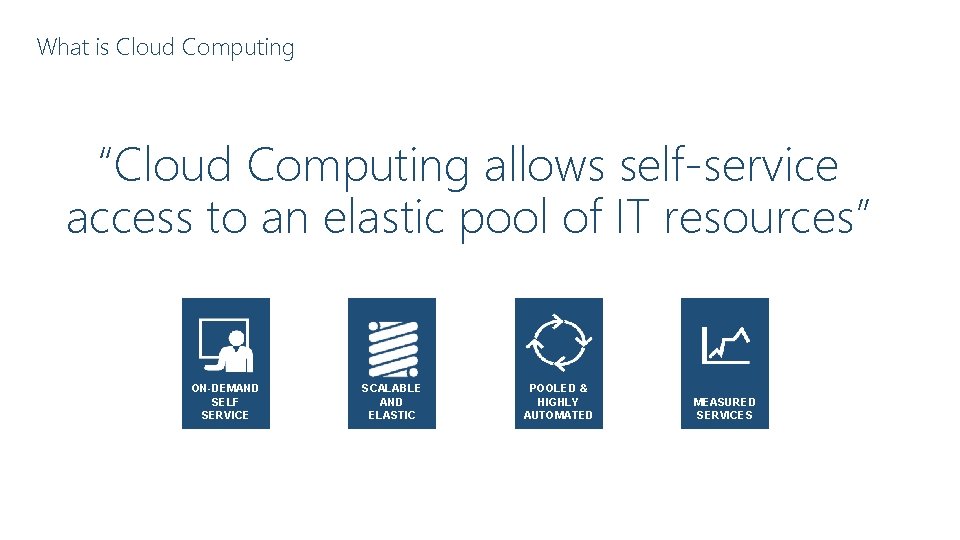
What is Cloud Computing “Cloud Computing allows self-service access to an elastic pool of IT resources” ON-DEMAND SELF SERVICE SCALABLE AND ELASTIC POOLED & HIGHLY AUTOMATED MEASURED SERVICES

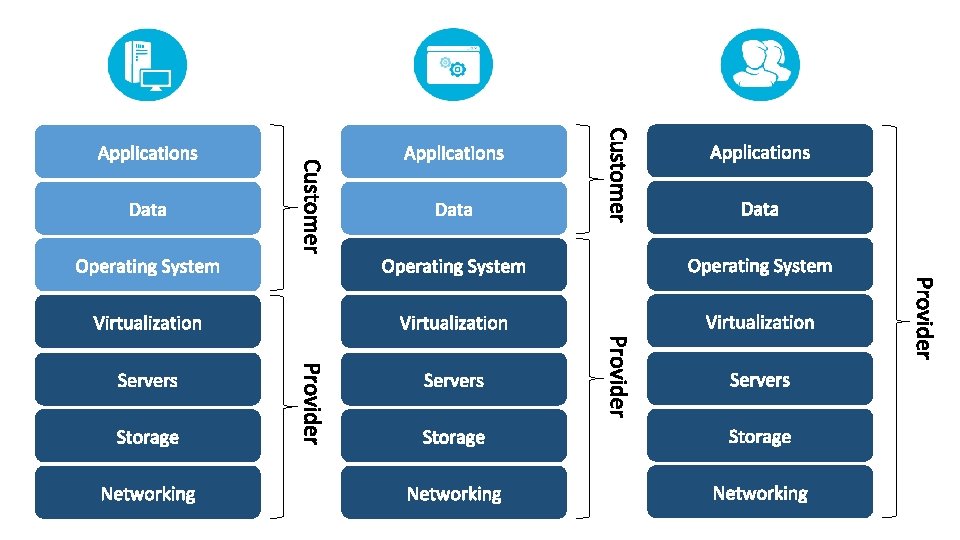
Cloud Service Models INFRASTRUCTURE AS A SERVICE DESKTOP AS A SERVICE DISASTER RECOVERY PLATFORM AS A SERVICE BACKUP AS A SERVICE SOFTWARE AS A SERVICE ANYTHING ……. . AS A SERVICE


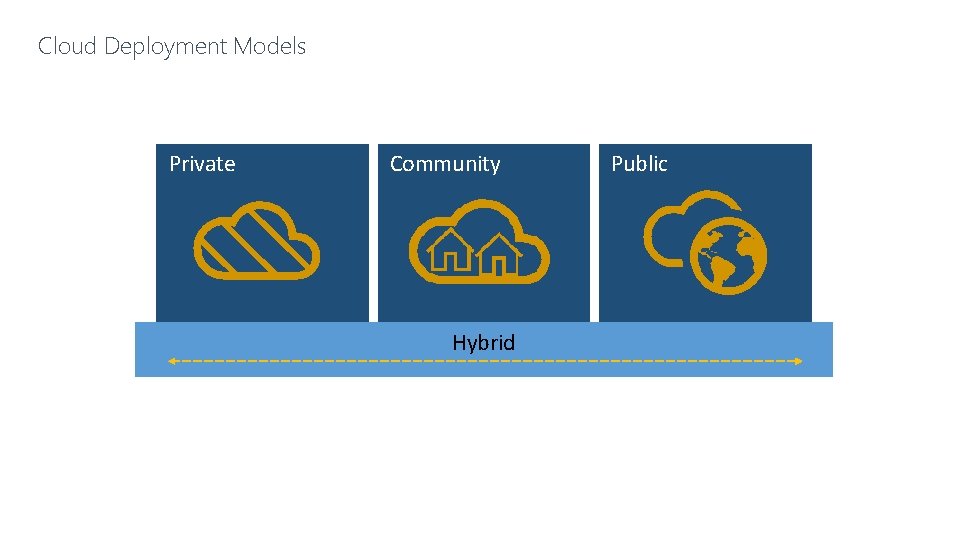
Cloud Deployment Models Private Community Hybrid Public

Why a Cloud strategy COST CONTROL SCALABILITY CONTINUITY COMPLIANC E FEATURE SET

Why a Cloud strategy SCALABILITY CONTINUITY



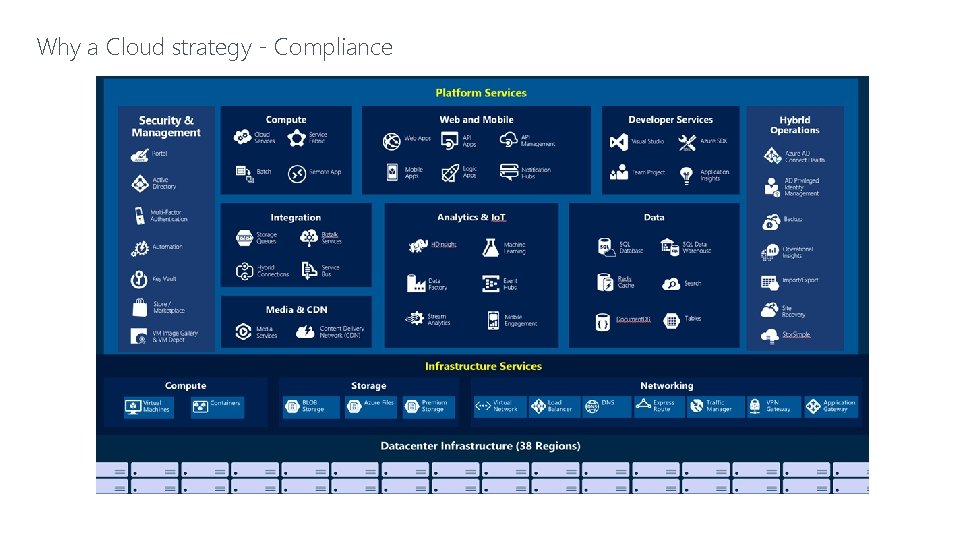
Why a Cloud strategy - Compliance COMPLIANC E

Why a Cloud strategy - Compliance Nov/Dec 2018

Why a Cloud strategy – Feature set FEATURE SET

Why a Cloud strategy - Compliance

Why a Cloud strategy – Feature set COST CONTROL SCALABILITY CONTINUITY COMPLIANC E FEATURE SET

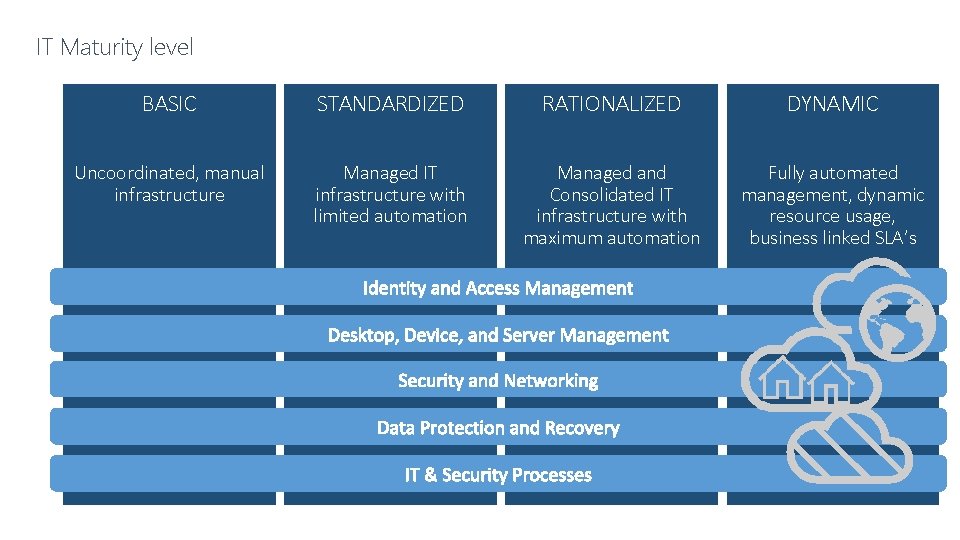
IT Maturity level BASIC STANDARDIZED RATIONALIZED DYNAMIC Uncoordinated, manual infrastructure Managed IT infrastructure with limited automation Managed and Consolidated IT infrastructure with maximum automation Fully automated management, dynamic resource usage, business linked SLA’s

The Modern Workplace enables Digital Transformation

Assuming a protected state!. . From cruising down the road….

Assuming bad-actors are targeting your organization. . To being ready to face any form of attack!

Assuming BREACH and actively responding to active threats within your organization. . to be in upside-down fighting mode!

The Modern Workplace enables Digital Transformation • Unlocks Creativity • Built for Collaboration • Integrated for Simplicity • Intelligent Security The Modern Desktop starts with Microsoft 365

Microsoft 365 - Security Why are we talking “security”? The growth of the number cyber attacks – (From our experience out of the field) Sophisticated attacks, spread quickly 100 million Identities a month are being attacked 50 K are compromised each month 2 types of organizations: • Organizations that have been breached and know about it • Organizations that have been breached and don’t know about it Amount of internet connected devices & the growing use of Cloud computing So, your perimeter-based security model is no longer good enough As, your network is where your users are, your network is where your devices are, and even, your network is where your data is

Microsoft 365 - Security Complexity is the absolute Enemy of Security! Larger organizations in most cases have a lot of security products, but they are not integrated, and they really require a lot of time, effort, energy from your sys/sec-admins We’ll have to “simplify” & integrate: Identity, Device, Information, Threats Therefore, we should think: “Built-in” vs. “Bolt-on” Microsoft –eq Security Company

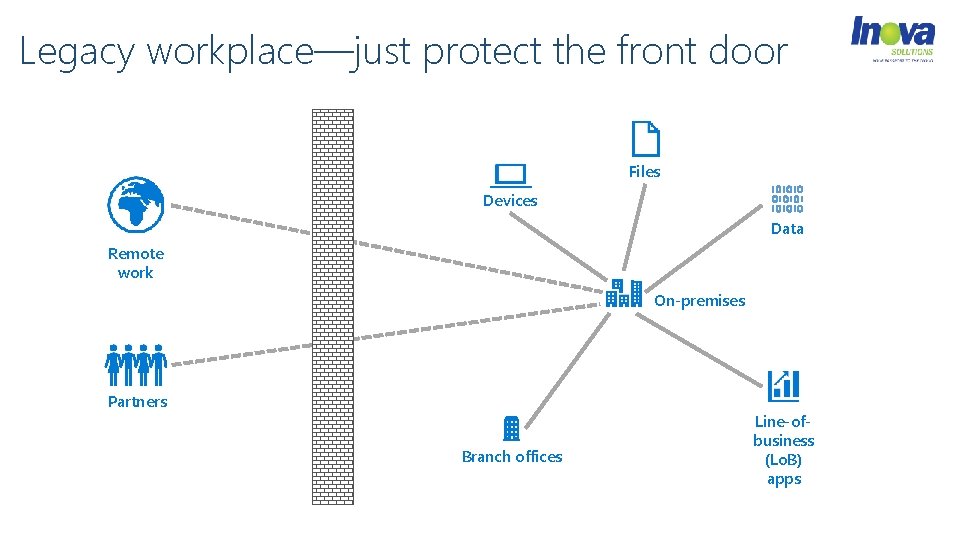
Legacy workplace—just protect the front door Files Devices Data Remote work On-premises Partners Branch offices Line-ofbusiness (Lo. B) apps

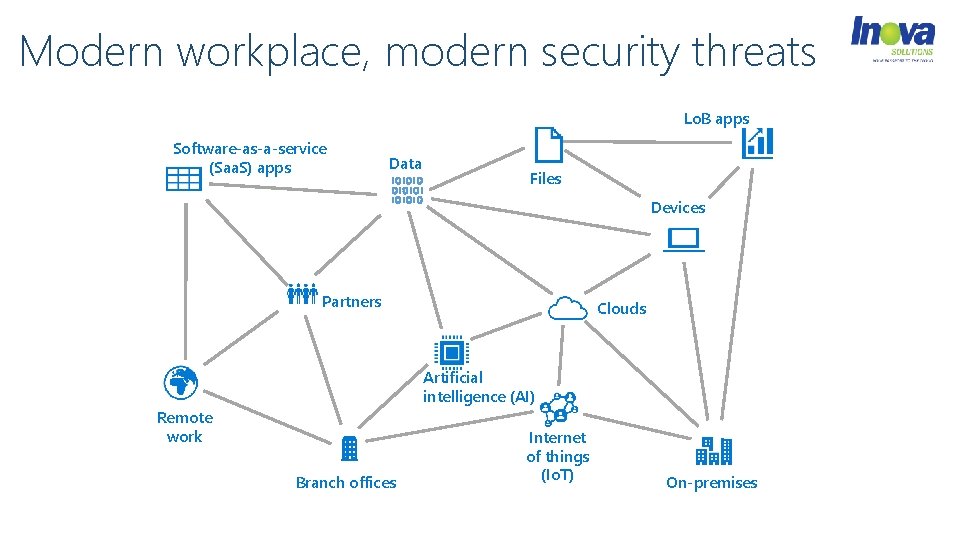
Modern workplace, modern security threats Lo. B apps Software-as-a-service (Saa. S) apps Data Files Devices Partners Clouds Artificial intelligence (AI) Remote work Branch offices Internet of things (Io. T) On-premises

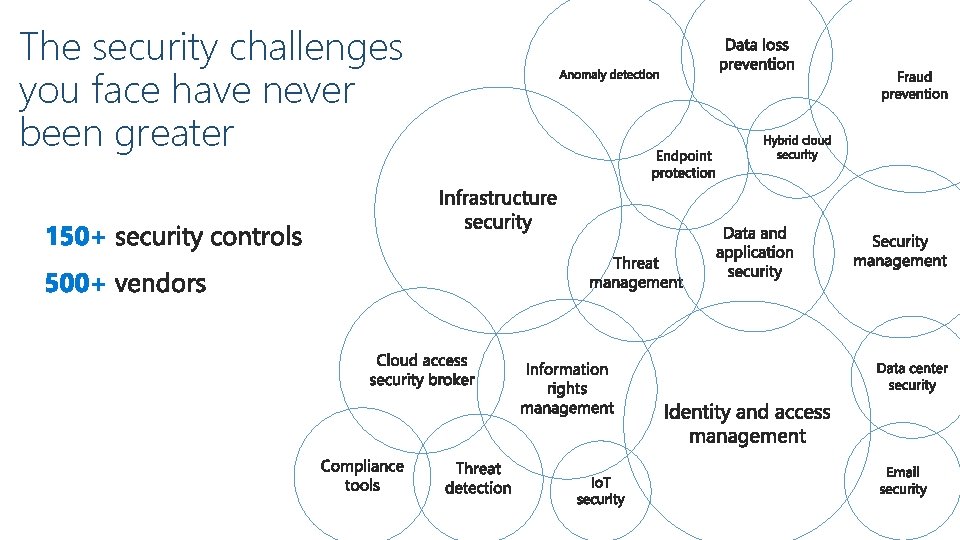
The security challenges you face have never been greater

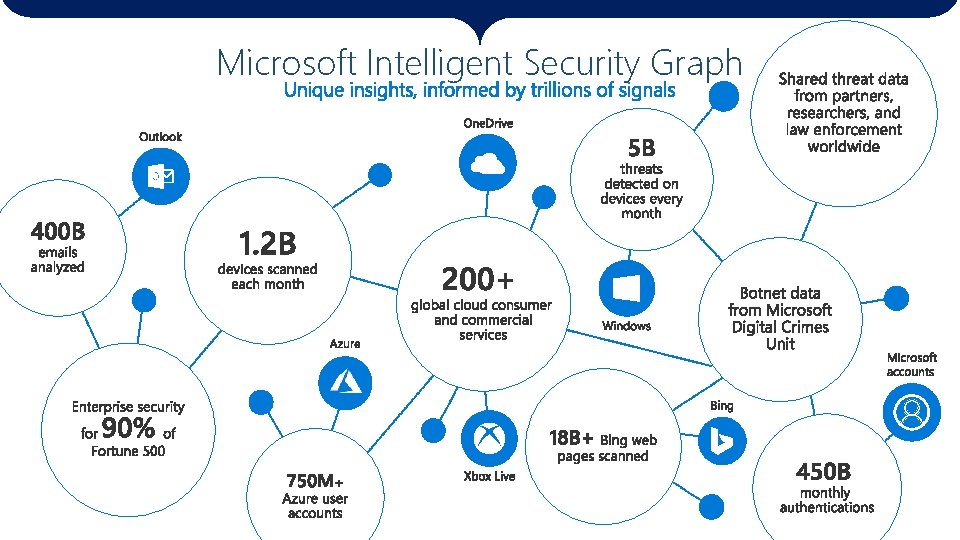
The threat landscape Identities Users and admins Endpoints User data Cloud apps Infrastructure Devices and sensors Email messages and documents Saa. S applications and data stores Servers, virtual machines, databases, networks Microsoft Intelligent Security Graph 6. 5 trillion signals per day

Microsoft Intelligent Security Graph

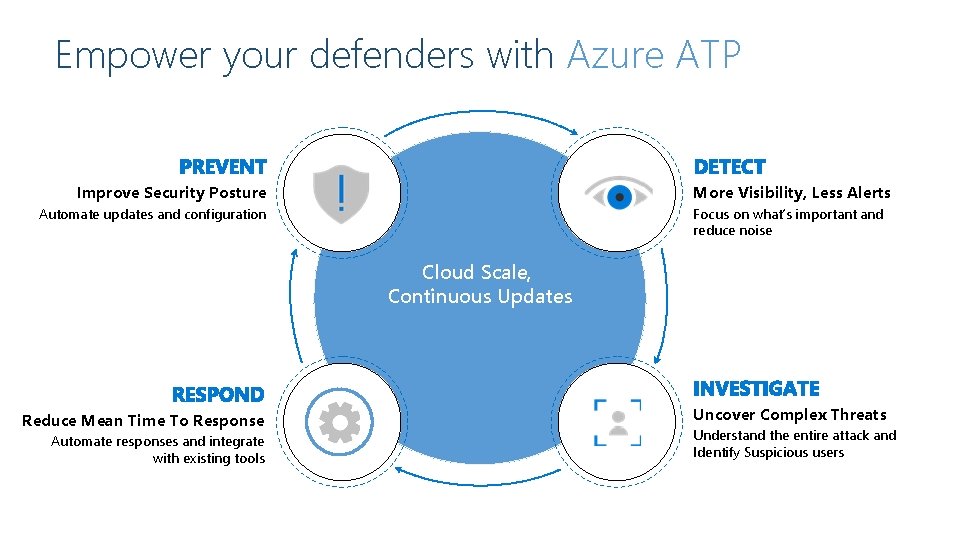
Empower your defenders with Azure ATP Improve Security Posture More Visibility, Less Alerts Automate updates and configuration Focus on what’s important and reduce noise Cloud Scale, Continuous Updates Reduce Mean Time To Response Automate responses and integrate with existing tools Uncover Complex Threats Understand the entire attack and Identify Suspicious users

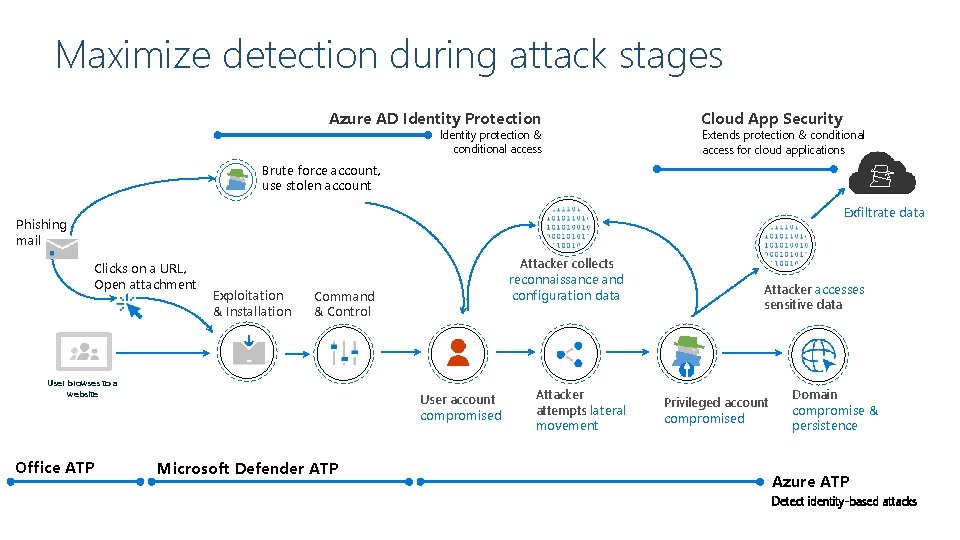
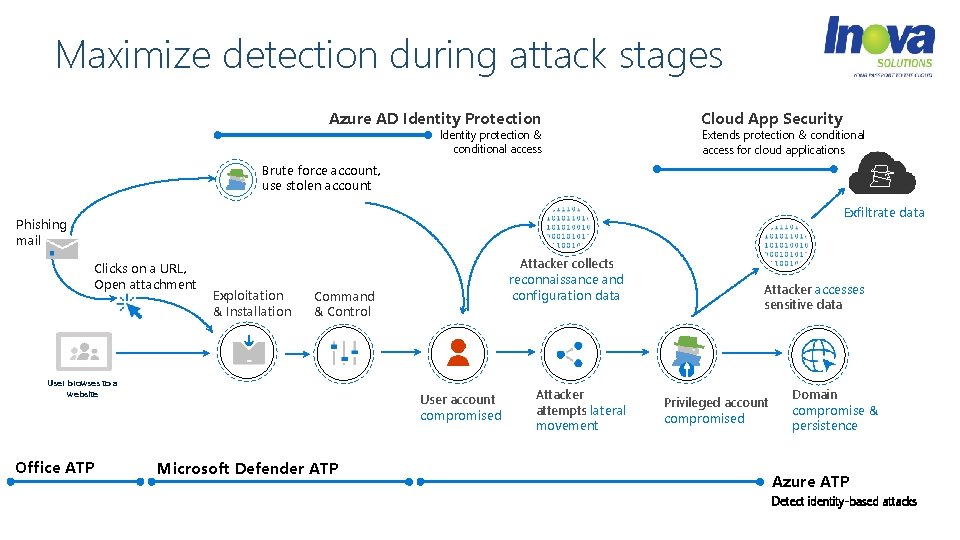
Maximize detection during attack stages Azure AD Identity Protection Identity protection & conditional access Cloud App Security Extends protection & conditional access for cloud applications Brute force account, use stolen account Exfiltrate data Phishing mail Clicks on a URL, Open attachment Exploitation & Installation Command & Control User browses to a website Office ATP Attacker collects reconnaissance and configuration data User account compromised Microsoft Defender ATP Attacker attempts lateral movement Attacker accesses sensitive data Privileged account compromised Domain compromise & persistence Azure ATP Detect identity-based attacks

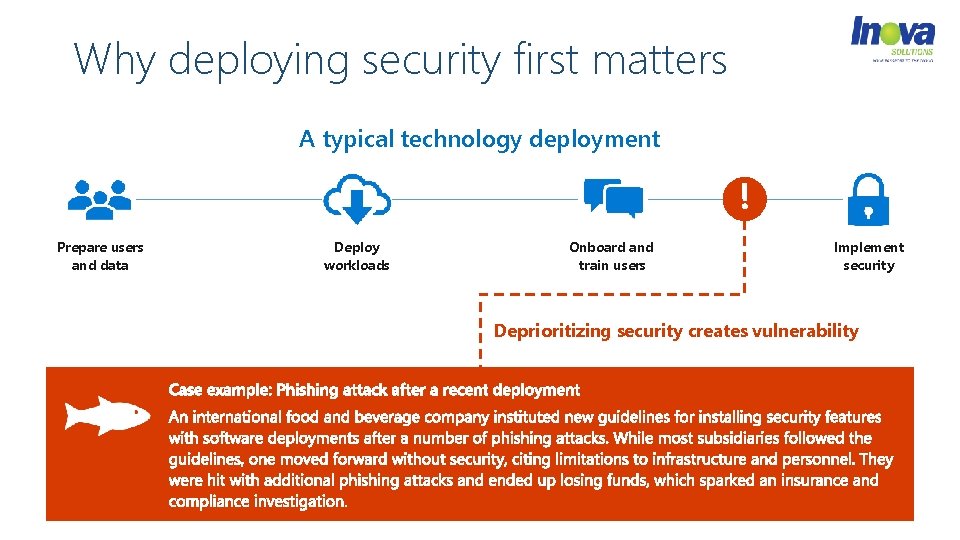
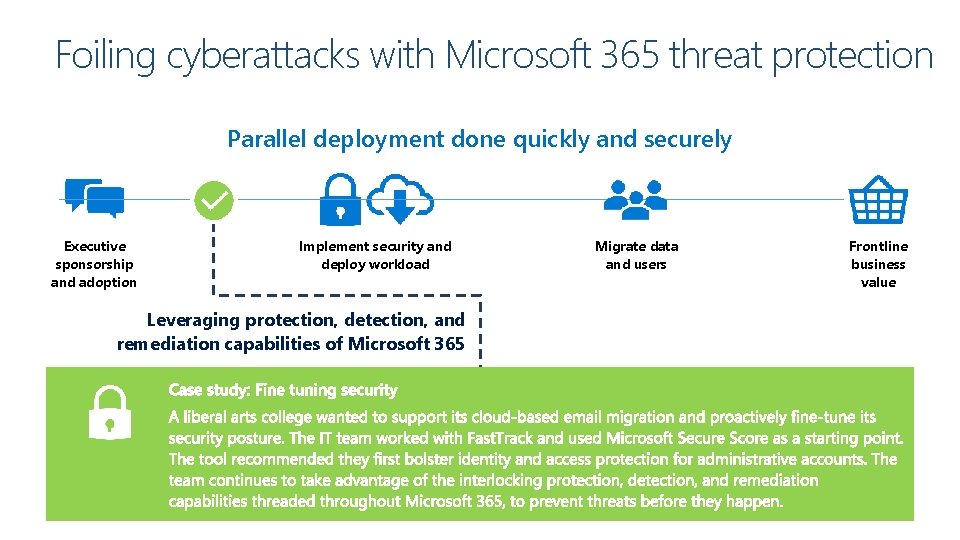
Why deploying security first matters A typical technology deployment Prepare users and data Deploy workloads Onboard and train users Implement security Deprioritizing security creates vulnerability

Foiling cyberattacks with Microsoft 365 threat protection Parallel deployment done quickly and securely Executive sponsorship and adoption Implement security and deploy workload Leveraging protection, detection, and remediation capabilities of Microsoft 365 Migrate data and users Frontline business value

Thank you!

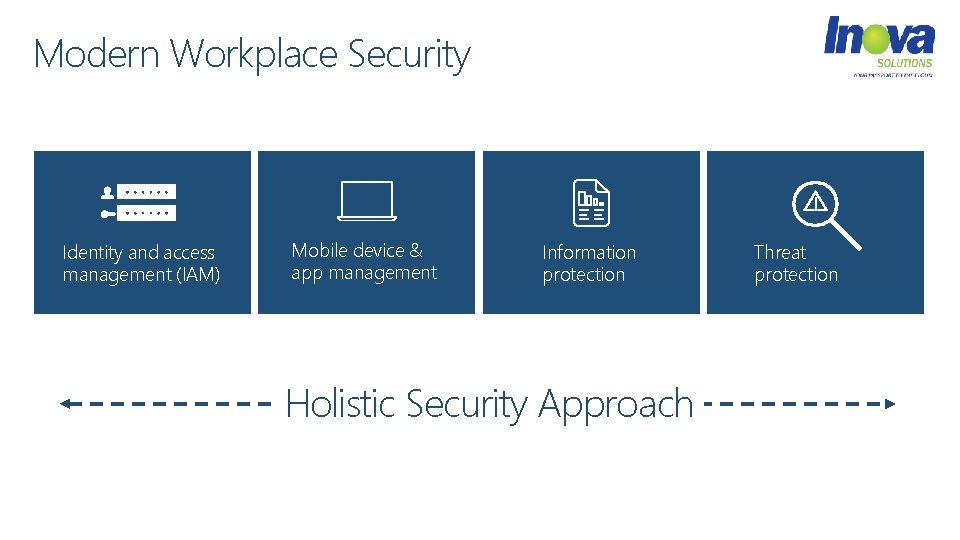
The Modern Workplace Security Quick Wins

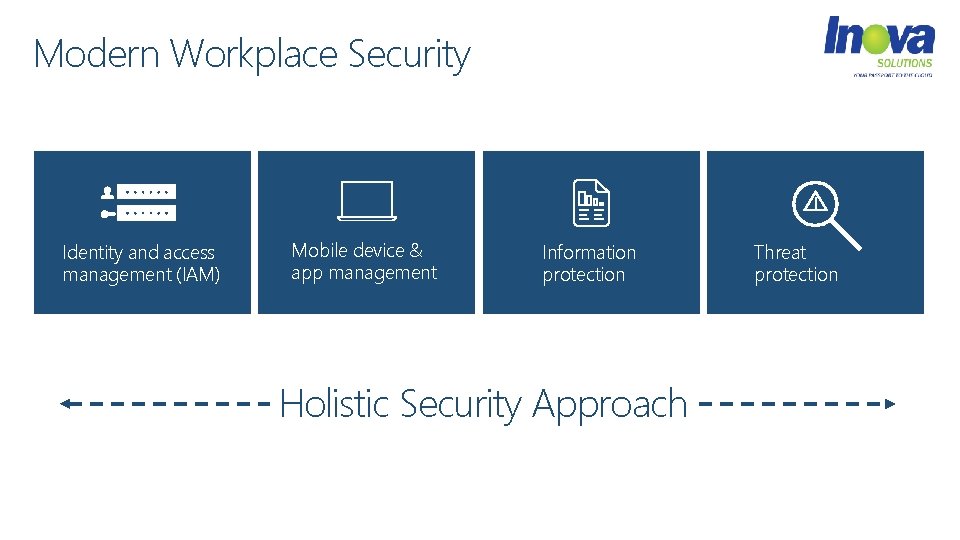
Modern Workplace Security Identity and access management (IAM) Mobile device & app management Information protection Holistic Security Approach Threat protection

Identity driven security What can go wrong? Identity and access management (IAM) 80% of breaches on accounts 32% of users will open email 12% of users click the link It takes only 2 ½ hours to hack an 8 -character password Assuming we are protected

Identity driven security What can we do? Identity and access management (IAM) “Assume breach” “Zero-Trust” QUICK WINS! • Named admin accounts – Required! • Implement Hybrid Identity (AD synchronization with Azure AD) • Enforce MFA on all admin accounts (privileged roles) - Required • Implement MFA for all Users (preferable conditional)* • Implement Office 365 Advanced Threat Protection (ATP)* • Portal Branding Next steps… • Implement PIM (Privileged Identity Management) • Implement Identity Protection (Behavioural analysis, AI, Risky sign-ins, leaked credentials, unfamiliar locations, etc. ) • Implement Azure Advanced Threat Protection * Conditional Access and Office 365 ATP will be covered in a bit

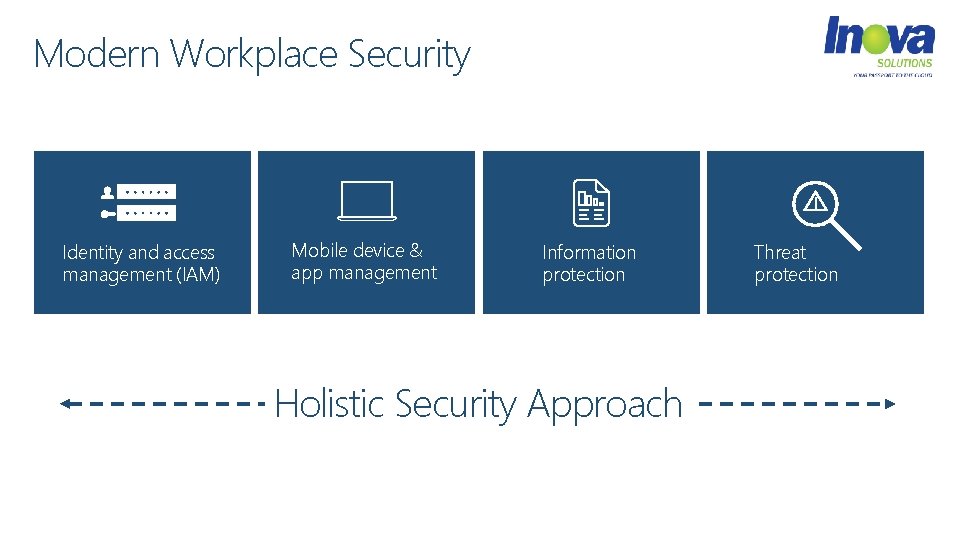
Modern Workplace Security Identity and access management (IAM) Mobile device & app management Information protection Holistic Security Approach Threat protection

Modern Workplace Security What can go wrong? Mobile device & app management Data is shared via non-corporate apps Data is stored locally on the device Mobile devices are commonly used careless Device gets stolen or is disposed in a careless way What else can we think off? We are not in control over managed, nor un-managed devices

Modern Workplace Security What can we do? Mobile device & app management Windows 7’s funeral was beautiful: QUICK WINS! • Enrol your devices; Windows 10, i. OS, and Android in Intune • Encrypt the disk with Bit. Locker – Required! • Implement App Protection Policies with DLP features • Implement Compliancy policy for your devices (insights) Next steps… • Implement advanced configuration policies and application deliveries • Make use of Windows 10 Enterprise features (Credential Guard, Application Guard, etc. ) • Combine Conditional Access with Device Compliancy (NAP) • Implement Windows Defender Advanced Threat Protection EPP (endpoint protection platform) – EDR (endpoint detection & response) • Configure One. Drive; Known Folder Move (KFM), Files on Demand • Implement Windows Information Protection (WIP)

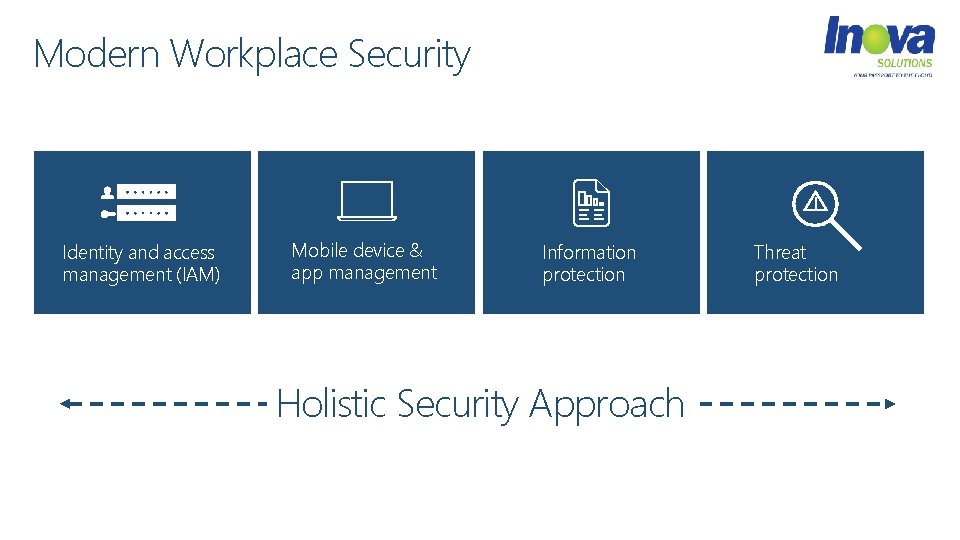
Modern Workplace Security Identity and access management (IAM) Mobile device & app management Information protection Holistic Security Approach Threat protection

Modern Workplace Security What can go wrong? Information protection 58% of workers have accidentally shared sensitive data to the wrong person Users are unaware of the “gold” they have in their hands We don’t know where our data travels

Modern Workplace Security What can we do? Information protection is a responsibility of the Business! IT facilitates QUICK WINS! • Implement Office message encryption • Start with classification labels (without policy) • Discuss information compliancy regulations – Retention • Implement basic retention policies • Create user awareness sessions Next steps… • Implement policies on specific classification labels • Retention based • Sensitivity based • Create DLP (Data Loss Prevention) policies • Configure Access Reviews • Start the review for automatic labelling of specific information

Modern Workplace Security Identity and access management (IAM) Mobile device & app management Information protection Holistic Security Approach Threat protection

Modern Workplace Security What can go wrong? Threat protection 91% of cyberattacks and the resulting data breach begin with a spear phishing email Patient-Zero/ Zero-Day, is not tackled on Day-Zero We are hold ransom for our own data! We are unaware of threats currently happening

Modern Workplace Security What can we do? Threat protection QUICK WINS! • Finish the quick wins of Identity Access Management • Finish the quick wins of Device Next steps… • Run through the reports generated now from your Office 365 ATP implementations • Dive deeper into the Secure Score actions • Implement Azure Sentinel (Advanced SIEM) and connect the M 365 + ATP products to Sentinel • Implement Azure ATP for behavioural analysis on your identities onpremises and in the Cloud

Recap - Modern Workplace Security Protect at the front door Protect your data anywhere Microsoft 365 Detect & remediate attacks

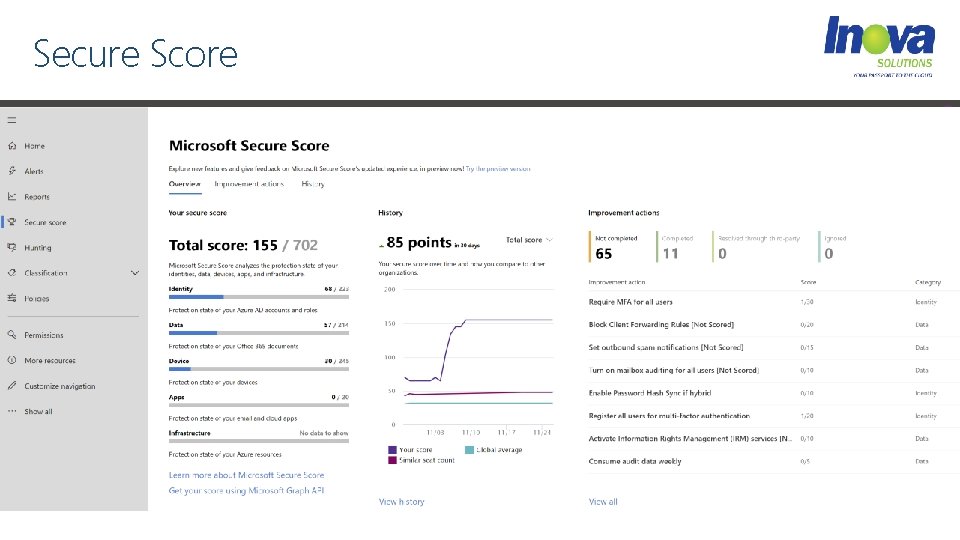
Secure Score

Real-life Experiences What happened – Case 1 What happened – Case 2 Organization lost a lot of money, by being tricked into sending money towards a new bank account Organization lost a lot of Personal Identification Information (PII) of her customers Compromised Credentials!!! We MUST switch to an Identity driven security approach

Maximize detection during attack stages Azure AD Identity Protection Identity protection & conditional access Cloud App Security Extends protection & conditional access for cloud applications Brute force account, use stolen account Exfiltrate data Phishing mail Clicks on a URL, Open attachment Exploitation & Installation Command & Control User browses to a website Office ATP Attacker collects reconnaissance and configuration data User account compromised Microsoft Defender ATP Attacker attempts lateral movement Attacker accesses sensitive data Privileged account compromised Domain compromise & persistence Azure ATP Detect identity-based attacks


Thank you!