High Capacity Lossless Data Hiding in JPEG Bitstream

High Capacity Lossless Data Hiding in JPEG Bitstream Based on General VLC Mapping Source: IEEE TRANSACTIONS ON DEPENDABLE AND SECURE COMPUTING (DOI 10. 1109/TDSC. 2020. 3013326 ) Author: Yang Du, Zhaoxia Yin, and Xinpeng Zhang Speaker: Lin Li Date: 2021/04/29 1

Outline • Introduction • Related works • Proposed scheme • Experimental results • Conclusions 2

Introduction --JPEG image (1/10) The JPEG compression structure 3
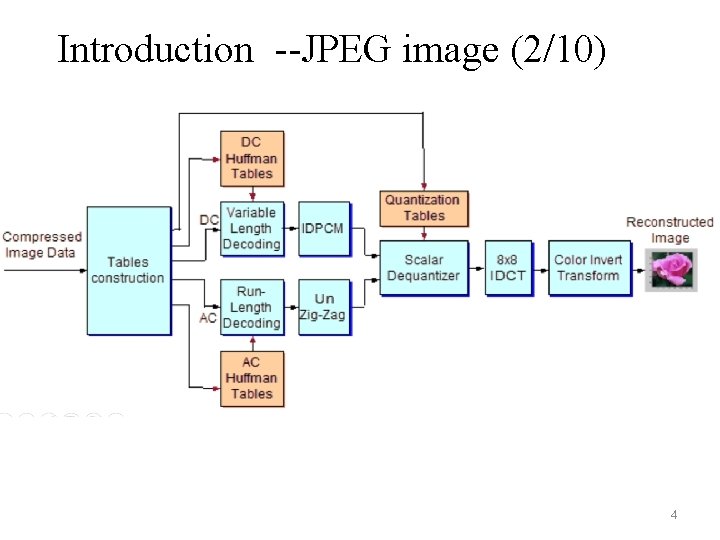
Introduction --JPEG image (2/10) 4

Introduction --JPEG image (3/10) 5
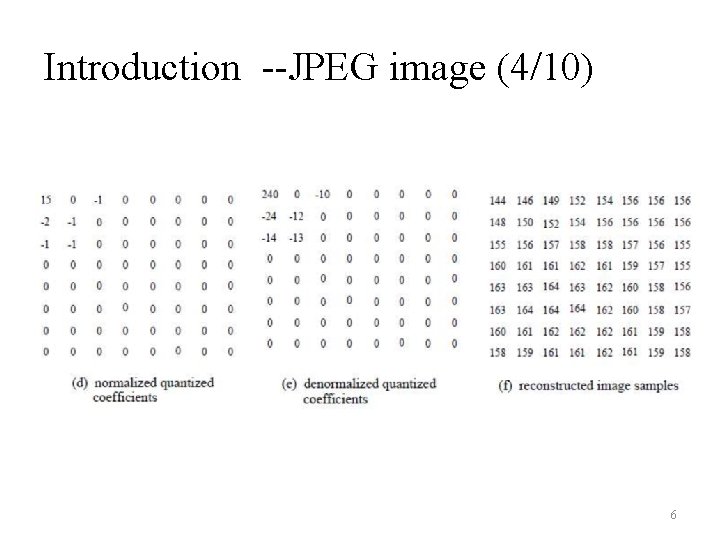
Introduction --JPEG image (4/10) 6

Introduction --JPEG image (5/10) DC(direct current ) The others are AC(alternating current ). Quantization 26 0 0 0 0 2 0 3 0 0 0 -1 0 0 0 0 0 0 0 0 0 0 0 0 DC DPCM (differentia l pulse code modulation DC Huffman coding JPEG file ) Entropy encoding AC RLC (Run Length Coding) AC Huffman coding 7 5
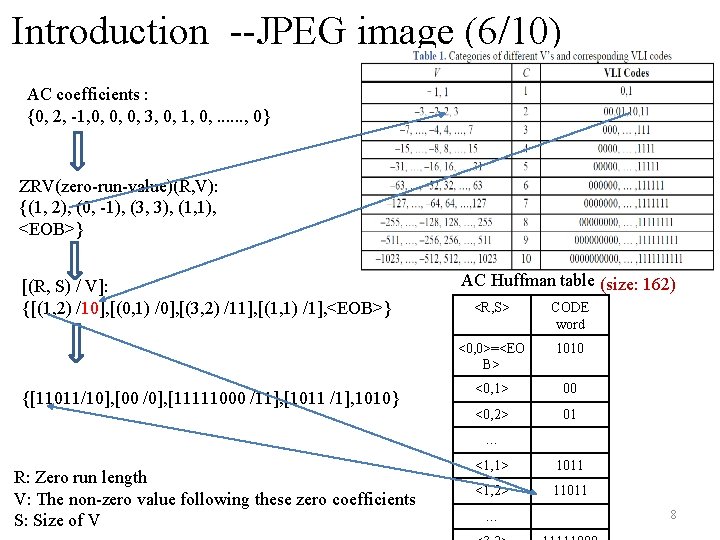
Introduction --JPEG image (6/10) AC coefficients : {0, 2, -1, 0, 0, 0, 3, 0, 1, 0, . . . , 0} ZRV(zero-run-value)(R, V): {(1, 2), (0, -1), (3, 3), (1, 1), <EOB>} [(R, S) / V]: {[(1, 2) /10], [(0, 1) /0], [(3, 2) /11], [(1, 1) /1], <EOB>} {[11011/10], [00 /0], [11111000 /11], [1011 /1], 1010} AC Huffman table (size: 162) <R, S> CODE word <0, 0>=<EO B> 1010 <0, 1> 00 <0, 2> 01 … R: Zero run length V: The non-zero value following these zero coefficients S: Size of V <1, 1> 1011 <1, 2> 11011 … 8 6
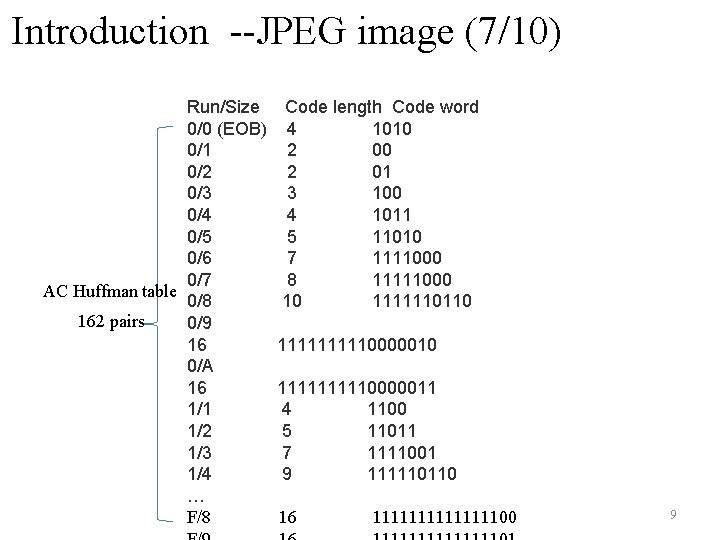
Introduction --JPEG image (7/10) Run/Size 0/0 (EOB) 0/1 0/2 0/3 0/4 0/5 0/6 0/7 AC Huffman table 0/8 162 pairs 0/9 16 0/A 16 1/1 1/2 1/3 1/4 … F/8 Code length Code word 4 1010 2 01 3 100 4 1011 5 11010 7 1111000 8 11111000 10 1111110110 1111111110000011 4 1100 5 11011 7 1111001 9 111110110 16 111111100 9 6
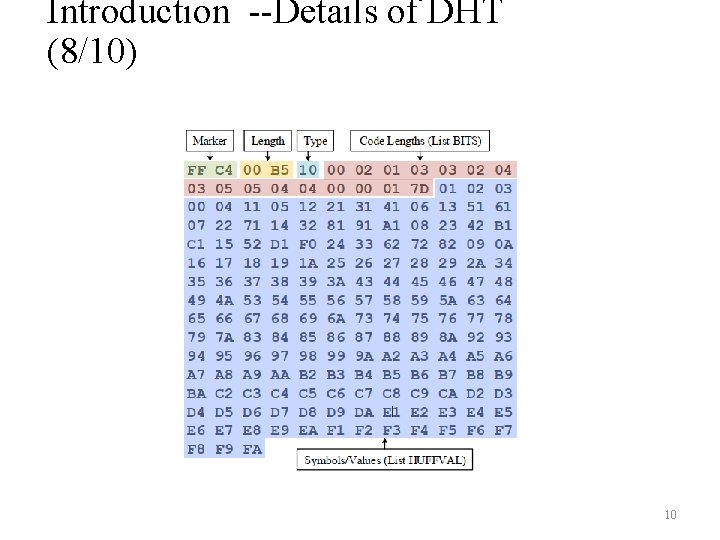
Introduction --Details of DHT (8/10) 10
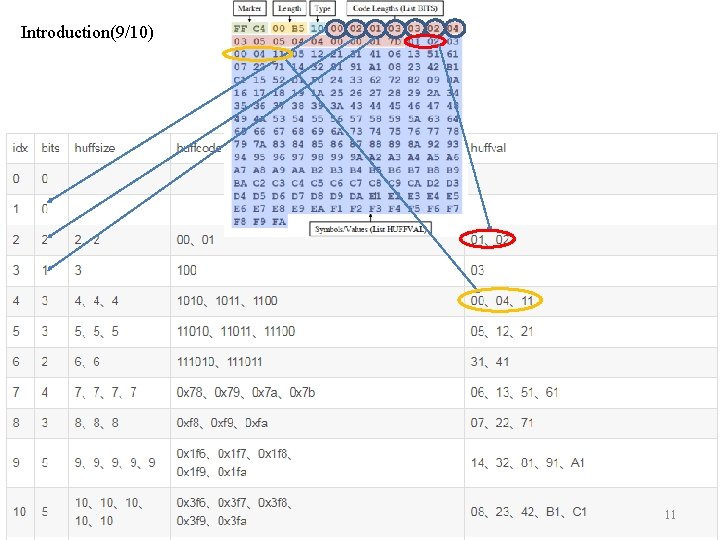
Introduction(9/10) 10 11
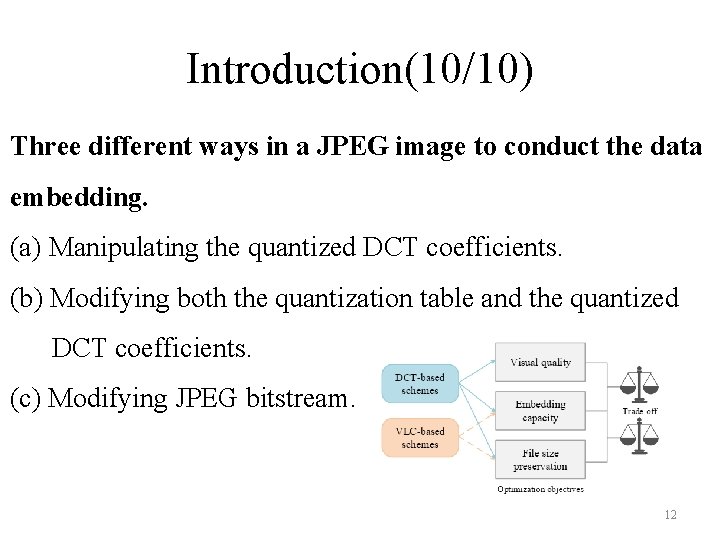
Introduction(10/10) Three different ways in a JPEG image to conduct the data embedding. (a) Manipulating the quantized DCT coefficients. (b) Modifying both the quantization table and the quantized DCT coefficients. (c) Modifying JPEG bitstream. 12
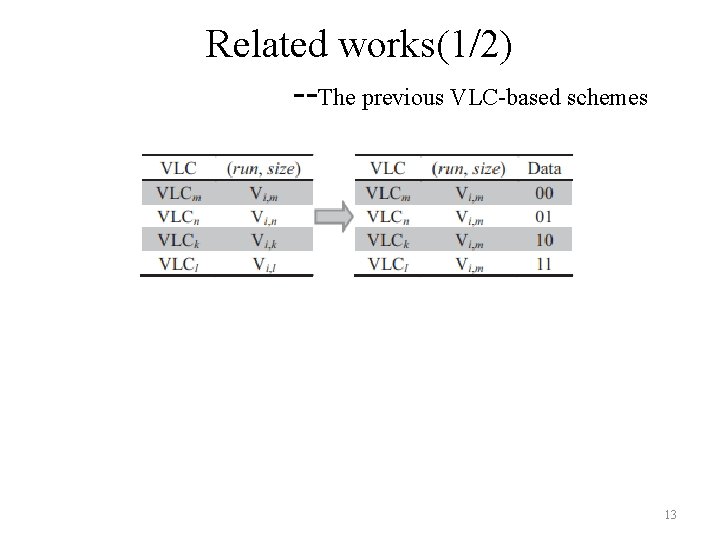
Related works(1/2) --The previous VLC-based schemes 13
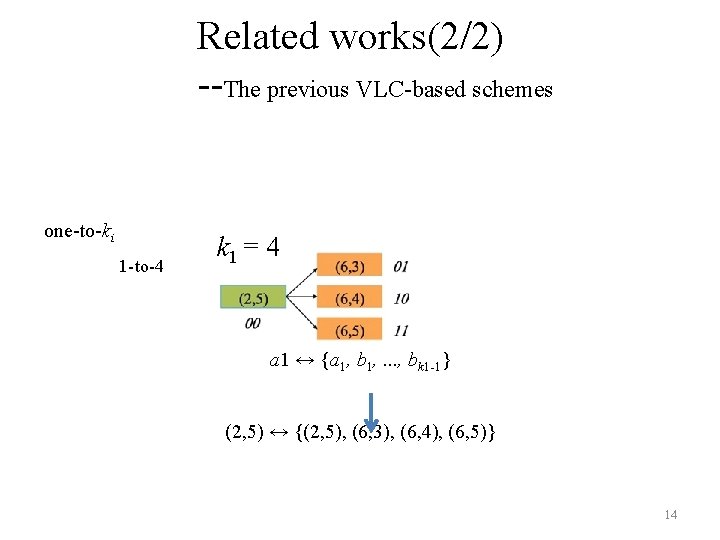
Related works(2/2) --The previous VLC-based schemes one-to-ki 1 -to-4 k 1 = 4 a 1 ↔ {a 1, b 1, . . . , bk 1 -1} (2, 5) ↔ {(2, 5), (6, 3), (6, 4), (6, 5)} 14
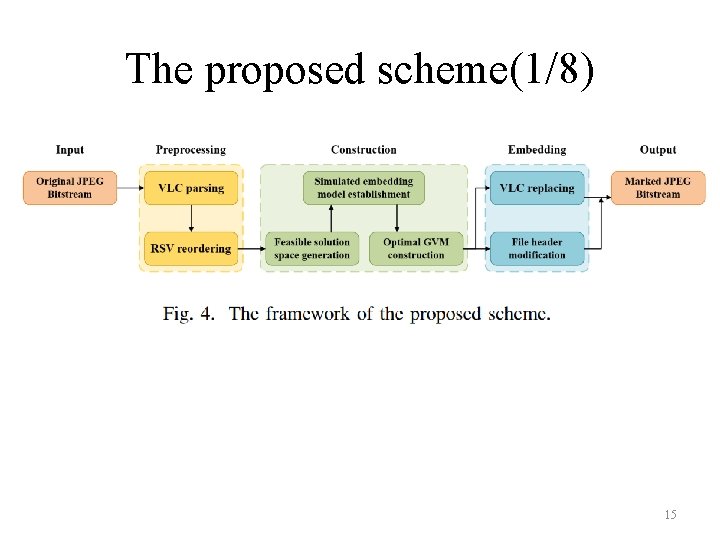
The proposed scheme(1/8) 15
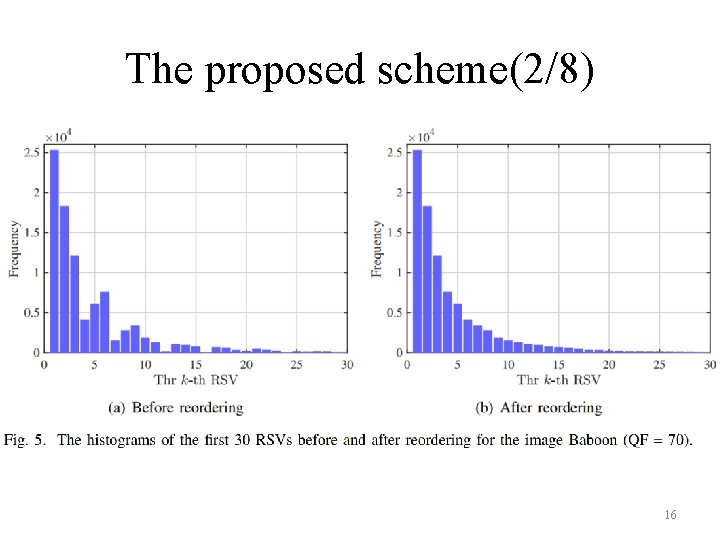
The proposed scheme(2/8) 16
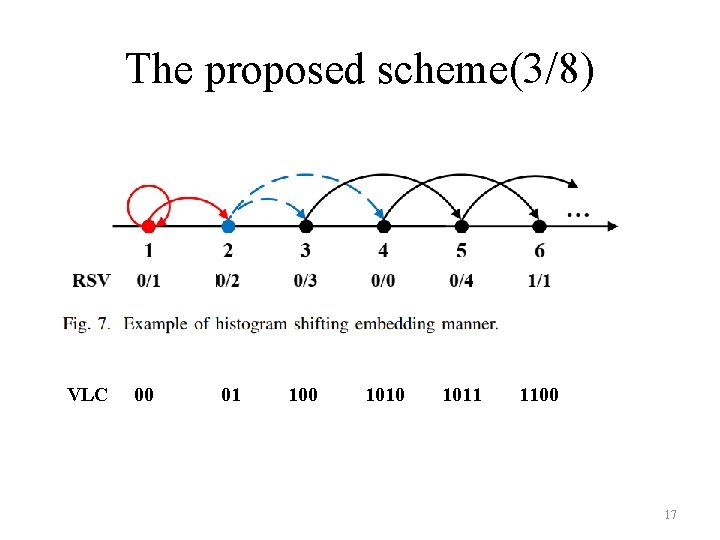
The proposed scheme(3/8) VLC 00 01 100 1011 1100 17
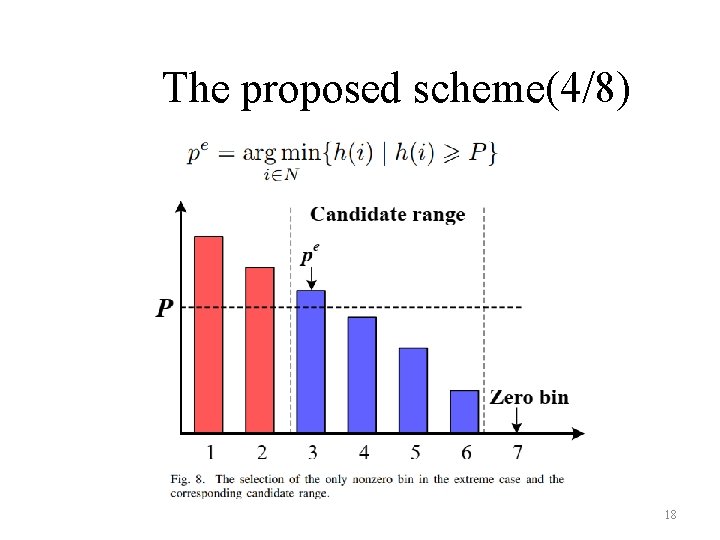
The proposed scheme(4/8) 18
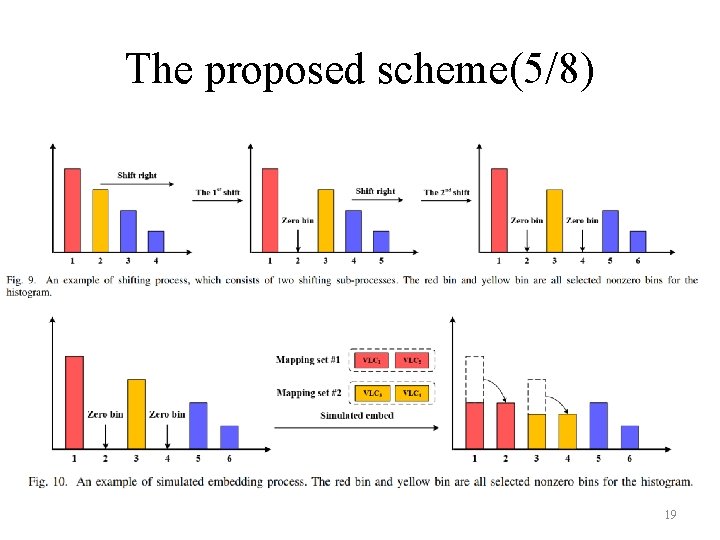
The proposed scheme(5/8) 19
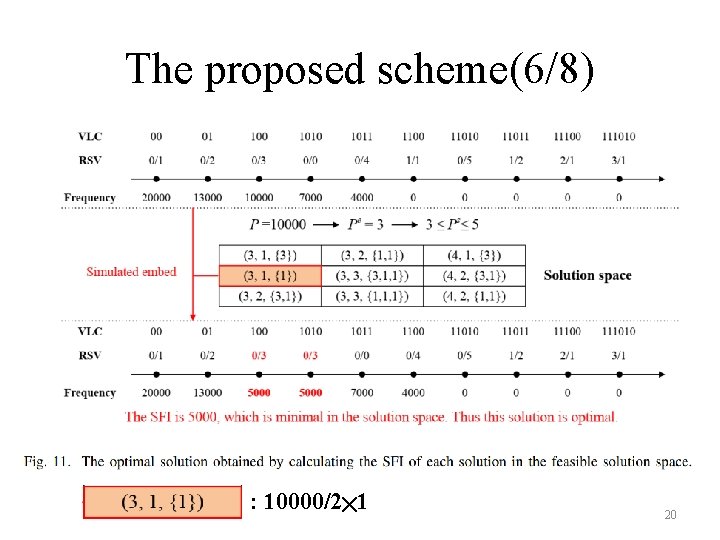
The proposed scheme(6/8) : 10000/2╳ 1 20
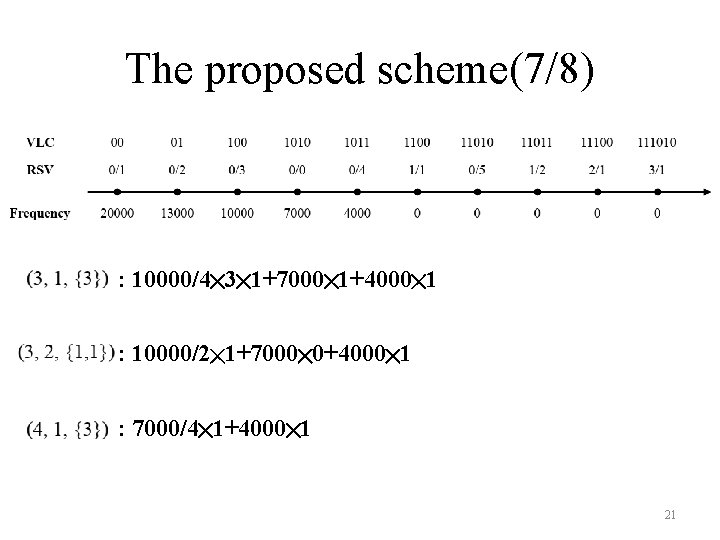
The proposed scheme(7/8) : 10000/4╳ 3╳ 1+7000╳ 1+4000╳ 1 : 10000/2╳ 1+7000╳ 0+4000╳ 1 : 7000/4╳ 1+4000╳ 1 21
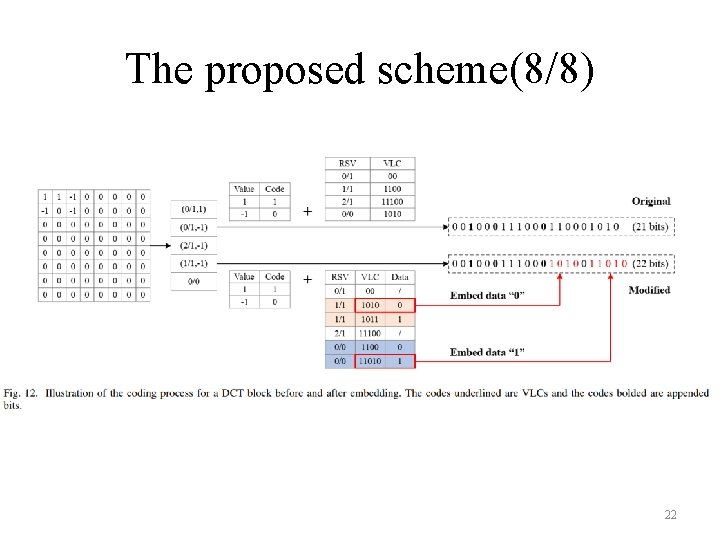
The proposed scheme(8/8) 22
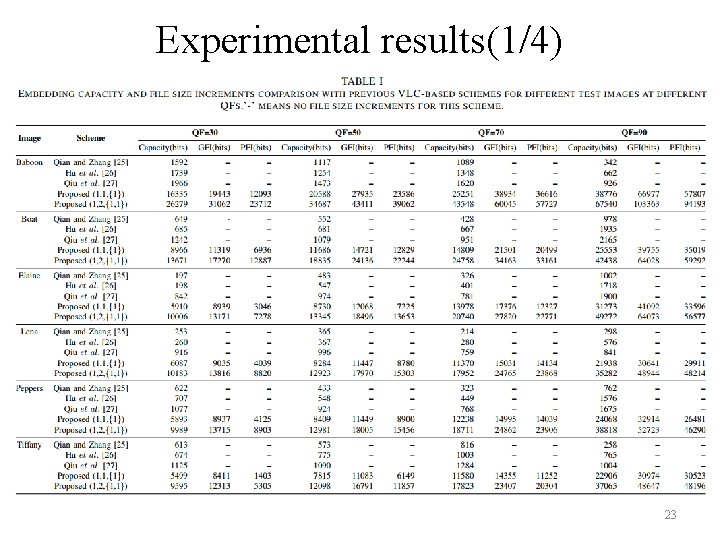
Experimental results(1/4) 23
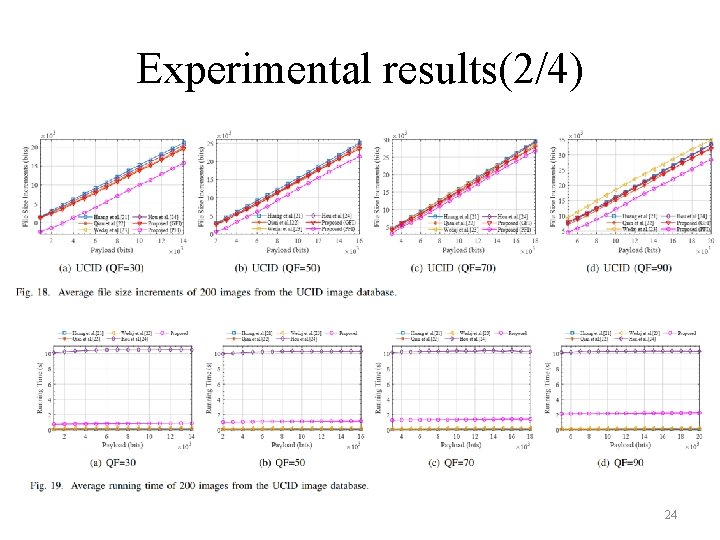
Experimental results(2/4) 24
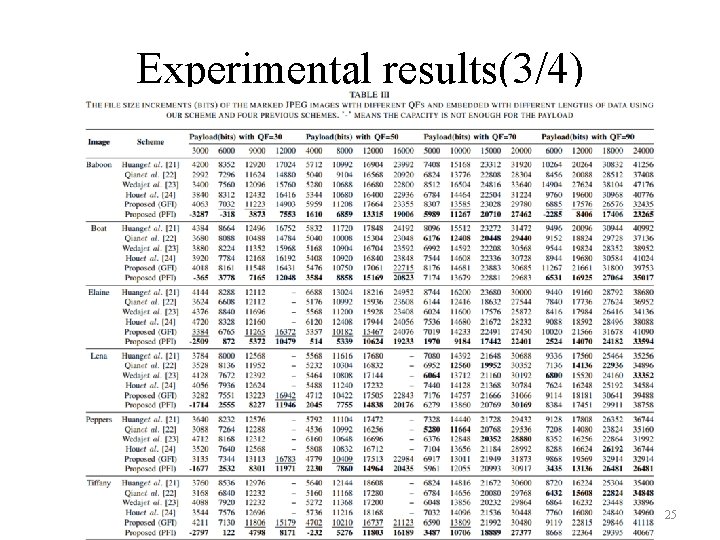
Experimental results(3/4) 25
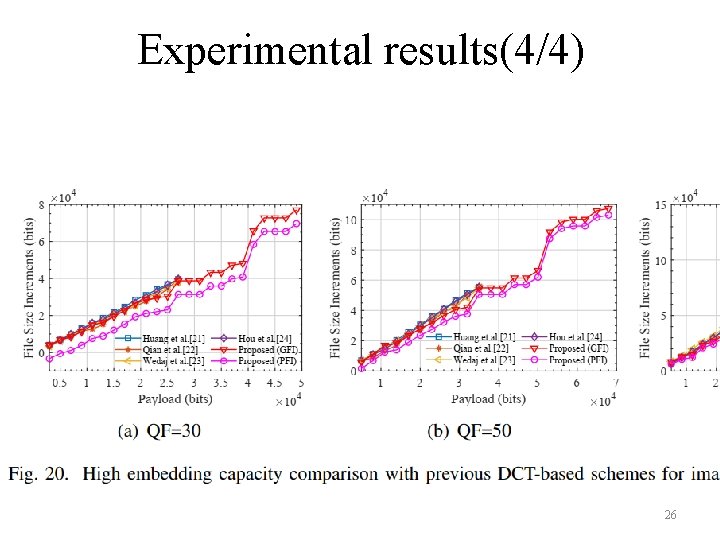
Experimental results(4/4) 26

References 27

Conclusions l The file size increments caused by the proposed scheme is smaller than the previous RDH schemes under the identical payload. l The visual quality of the marked JPEG image is preserved. l The upper bound of the embedding capacity of our proposed scheme is also much larger than state-of-the-arts works. Thanks for your listening! 28
- Slides: 28