Hiding in Plain Sight Fileless Attacks and Covert

















- Slides: 27

"Hiding in Plain Sight: Fileless Attacks and Covert Communication Channels are Increasing Across all Industries. "




Terms Covert Channels Capability to transfer information between two hosts, which are not explicitly allowed to communicate Fileless Maware Attack technique that avoids downloading malicious, executable files, usually to disk, at one stage or another by using exploits, macros, scripts, or legitimate system tools instead. Steganography Concealing messages or information within other non-

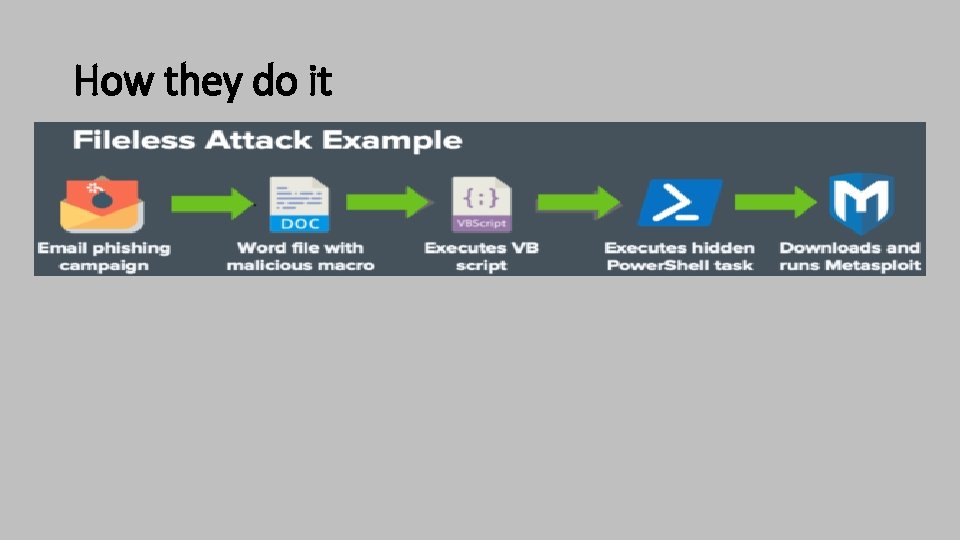
Fileless Malware • Most of these types of attacks are actually “semi-fileless • Once compromised, these attacks also abuse legitimate systems and admin tools and processes to gain persistence, elevate privileges, and spread laterally across the network. “ • Evade protection by traditional file-based or signature-based tools. So any technique designed to try to circumvent or evade detection by those tools really falls into the fileless attack category.

Why is this Method Effective? • Doesn’t trigger Anti-virus (file/signature-based) • Non-persistent (runs in memory) • “Lives off the Land” § Power. Shell § WMI § VBSCripts § Linux: Python, PERL, Bash scripts

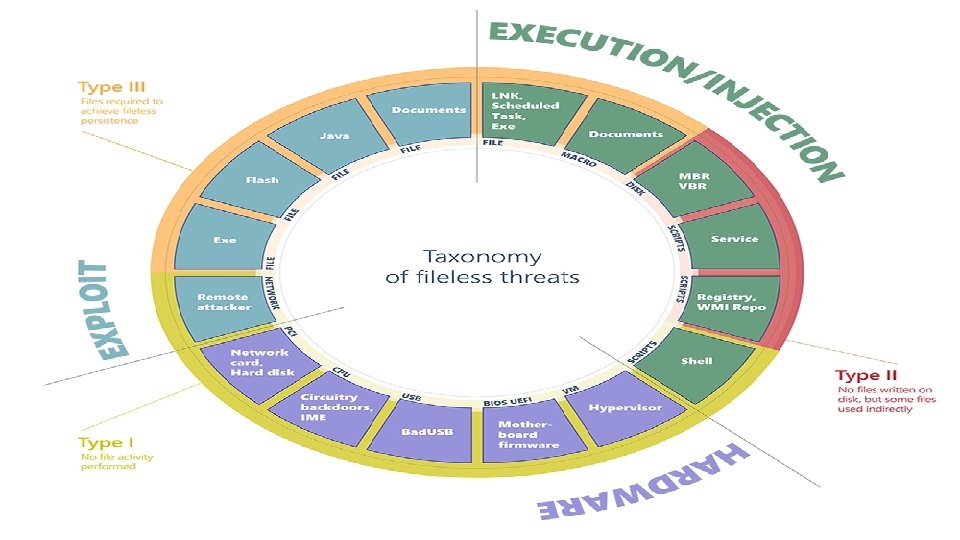
How they do it

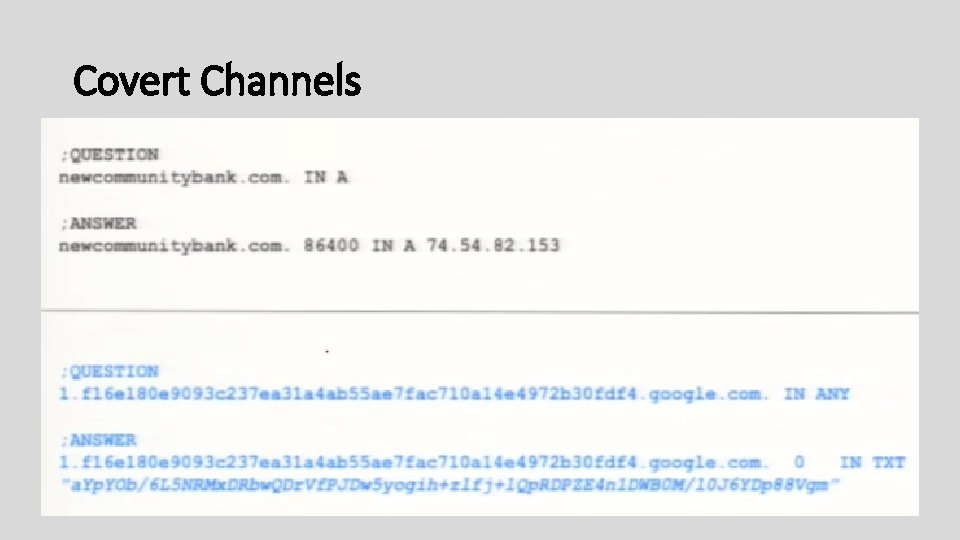
Covert Communication Channels • Receive commands • Send execution feedback (go/no-go) • Receive updates • Evade security defenses (IDS, AV, IR, Forensic Analysis) • Exfiltrate data

Covert Channels

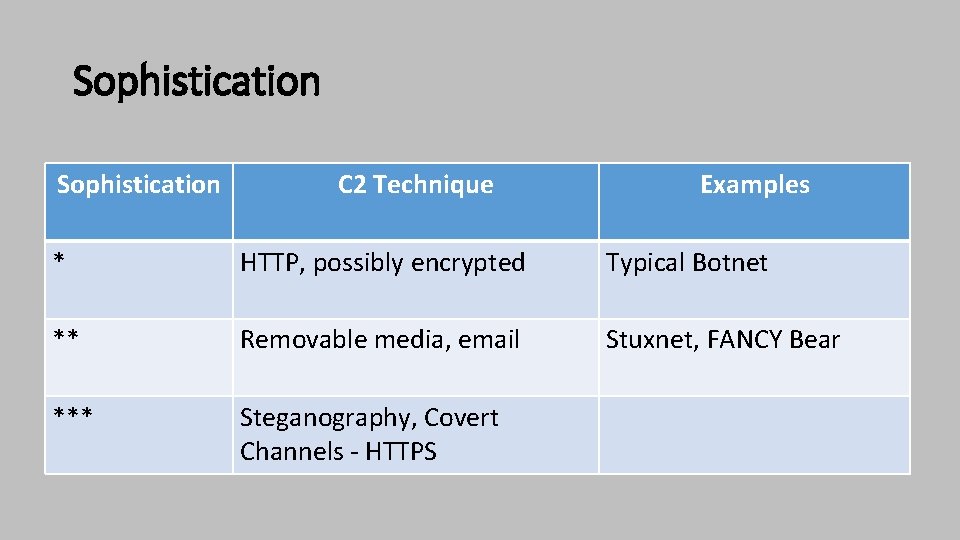
Sophistication C 2 Technique Examples * HTTP, possibly encrypted Typical Botnet ** Removable media, email Stuxnet, FANCY Bear *** Steganography, Covert Channels - HTTPS

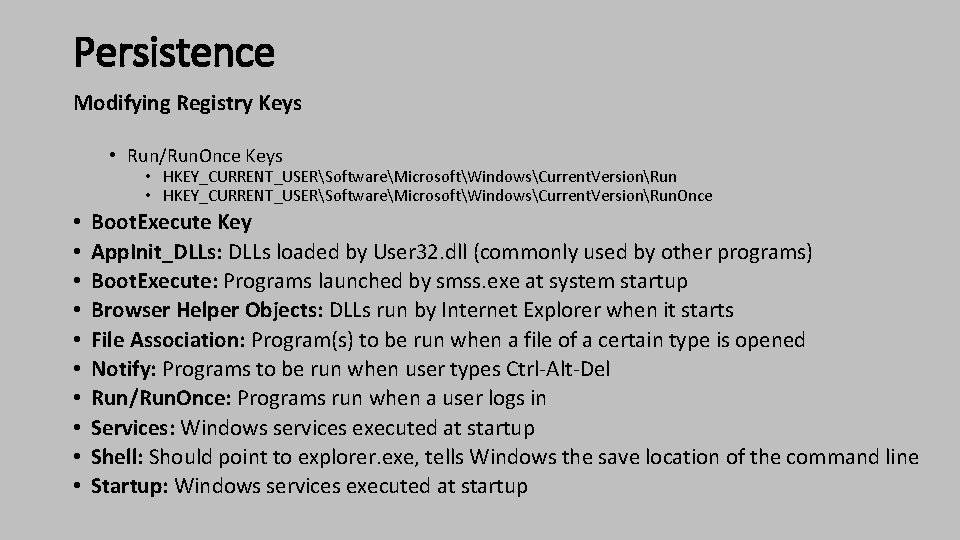
Persistence Modifying Registry Keys • Run/Run. Once Keys • HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrent. VersionRun. Once • • • Boot. Execute Key App. Init_DLLs: DLLs loaded by User 32. dll (commonly used by other programs) Boot. Execute: Programs launched by smss. exe at system startup Browser Helper Objects: DLLs run by Internet Explorer when it starts File Association: Program(s) to be run when a file of a certain type is opened Notify: Programs to be run when user types Ctrl-Alt-Del Run/Run. Once: Programs run when a user logs in Services: Windows services executed at startup Shell: Should point to explorer. exe, tells Windows the save location of the command line Startup: Windows services executed at startup

Persistence • Run/Run. Once Keys • HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrent. VersionRun. Once • Boot. Execute Key • Since smss. exe launches before windows subsystem loads, it calls configuration subsystem to load the hive present at • HKLMSYSTEMCurrent. Control. SetControlhivelist. • Also smss. exe will launch anything present in the Boot. Execute key at HKEY_LOCAL_MACHINESYSTEMControl. Set 002ControlSession Manager.

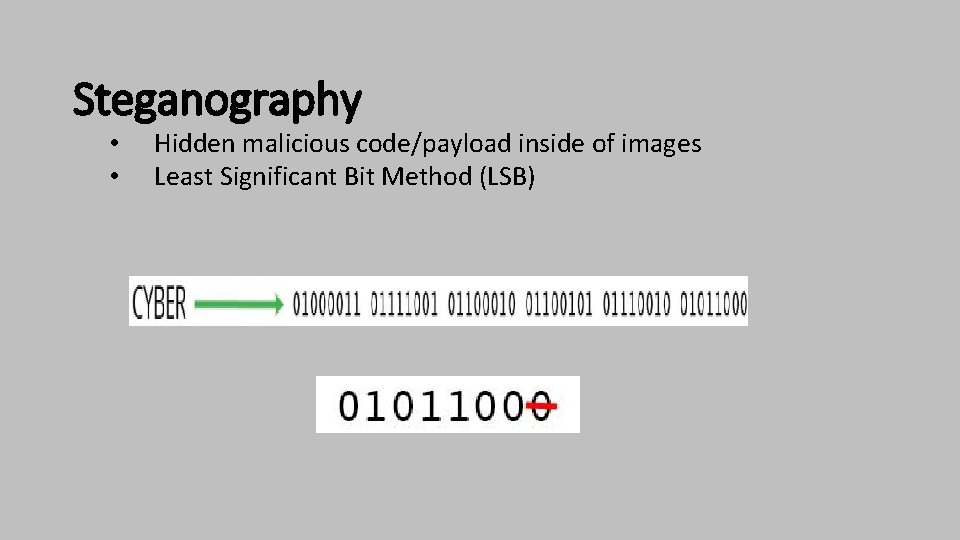
Steganography • • Hidden malicious code/payload inside of images Least Significant Bit Method (LSB)

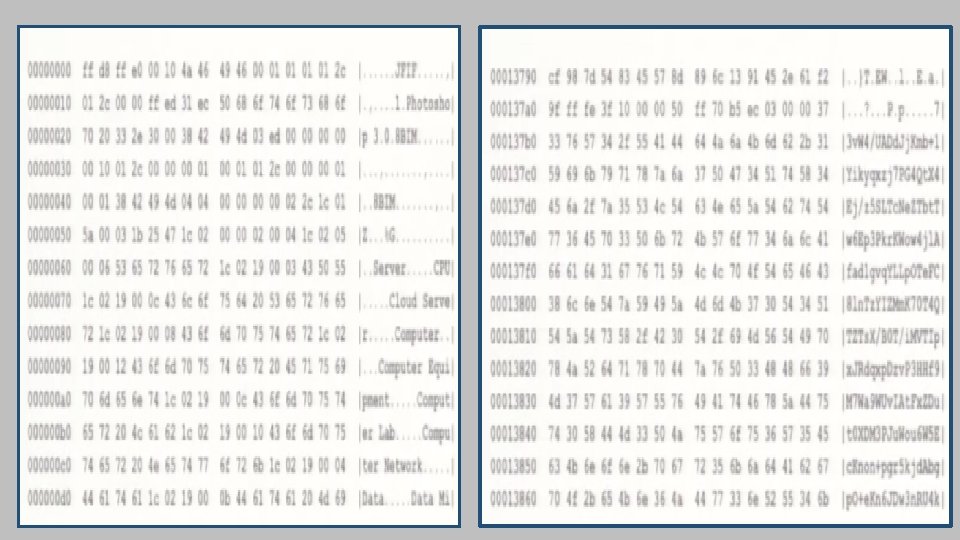
Simple. jpeg image right?

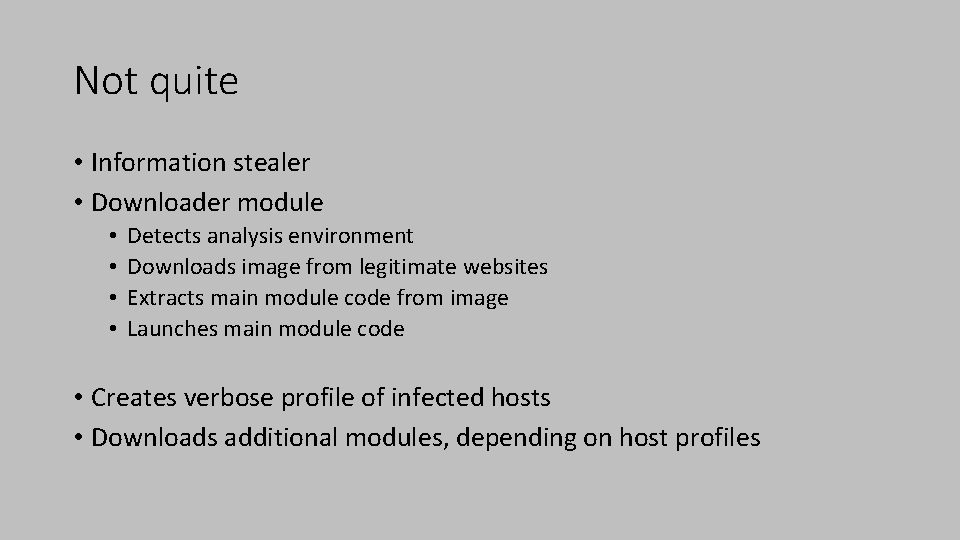
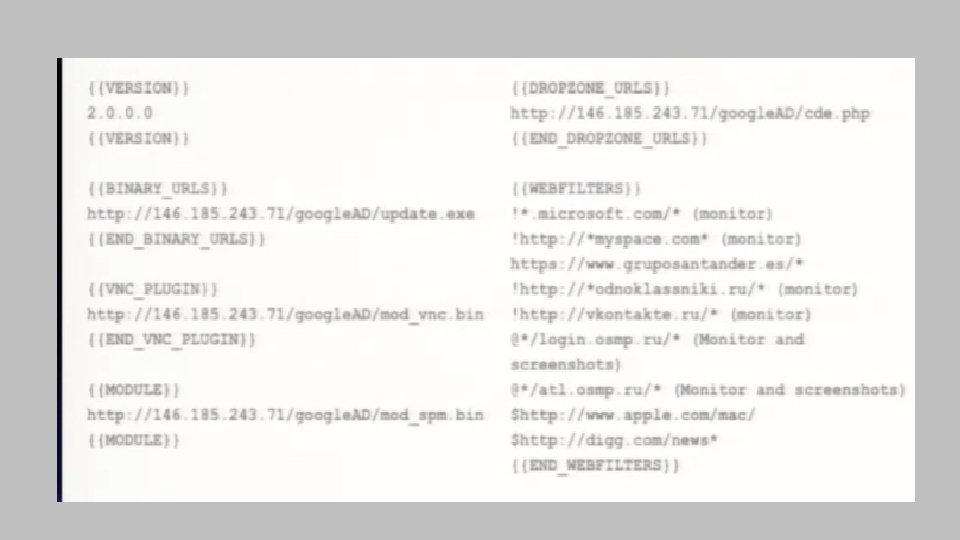
Not quite • Information stealer • Downloader module • • Detects analysis environment Downloads image from legitimate websites Extracts main module code from image Launches main module code • Creates verbose profile of infected hosts • Downloads additional modules, depending on host profiles



Prevention Detection Correction

Prevention User training Ø Formal, user friendly, updated at least annually Ø Initial & Annual requirement Ø Testing (phishing) Prevention Technologies ($$$) Ø Secure Email Gateway Ø Secure Web Gateway Ø Nextgen endpoint protection (advanced threat prevention, heuristics) Ø MFA/2 FA for remote access and down to some endpoints Technical Policy Controls (“Free”) Ø Block risky email attachments (. exe, . bat, . doc, . dll, . js, . vbs, . ps 1, . cmd, . msi, . inf, . sh) Ø Browser extensions - whitelist (group policy) Ø Remove local admin privileges Ø Secure usae of EA/DA accounts Ø Patching

Detection • Alert rules for anomalous behavior: • Processes executing shell commands • Suspicious commands executed by listening processes. • Excessive network communications from processes that are somewhat abnormal/anomalous • SSL Decryption at the edge • Limited persistence and privilege escalation • Sandbox file detonation

Detection cont’d. • Power. Shell event 4014 (Script Block Logging) contains a ton of data • Event 4688: Power. Shell via Ps. Exec • Power. Shell via WMIC or Ps. Exec • Suspicious service creation • User creation and users added to Local/Global Admin group

Correction Incident Response Plan ØPlaybook ØTested – practice “cyber fire drills” ØUpdated System Recovery/Backups ØVSS ØVM Snapshots ØOnsite & off-site Third-Party Response Retainer


Impacts/Consequences § Temporary or permanent loss of sensitive or proprietary information § Disruption to business operations § Financial losses: restore systems and files, fines, lawsuits § Potential harm to an organization’s reputation

Resources • MITRE ATT&CK • NSA’s Spotting the Adversary with Windows Event Log Monitoring • Internet Storm Center Daily Podcast • US-CERT Alerts & Advisories • Microsoft Security Response Center (MSRC)

Questions?