Hey Ferb I know what we are gonna

Hey Ferb, I know what we are gonna do today! Aims: To create a program that encodes messages using the Caesar Cipher. Objectives: ALL: Understand how the Caesar Cipher works. MOST: Reproduce the Scratch scripts to encode and decode messages using Caesar Cipher. SOME: Experiment with enciphering and deciphering messages with different shifts.
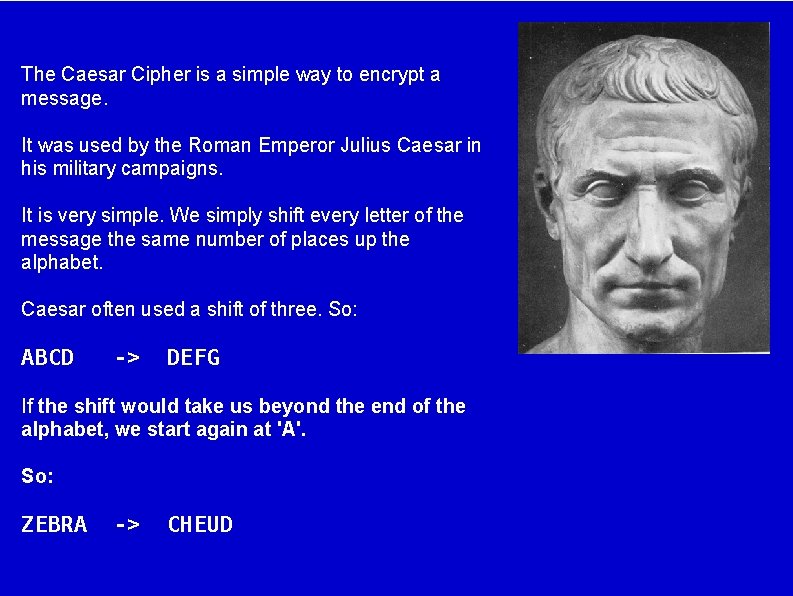
The Caesar Cipher is a simple way to encrypt a message. It was used by the Roman Emperor Julius Caesar in his military campaigns. It is very simple. We simply shift every letter of the message the same number of places up the alphabet. Caesar often used a shift of three. So: ABCD -> DEFG If the shift would take us beyond the end of the alphabet, we start again at 'A'. So: ZEBRA -> CHEUD
We need to come up with a script that will go through each letter in a string and change it for one a certain number of letters further on in the alphabet. We also need to make sure that if the shift takes us past 'Z', we start again at 'A'. First of all, we are going to ask the user for the shift they want to use. We will only accept whole numbers between -25 and 25. Have a go at writing a script that asks the user for a number and stores it in a variable called “shift” if it meets these criteria. Otherwise, the script should ask for another number. If you get stuck, you can see a sample solution on the next slide.
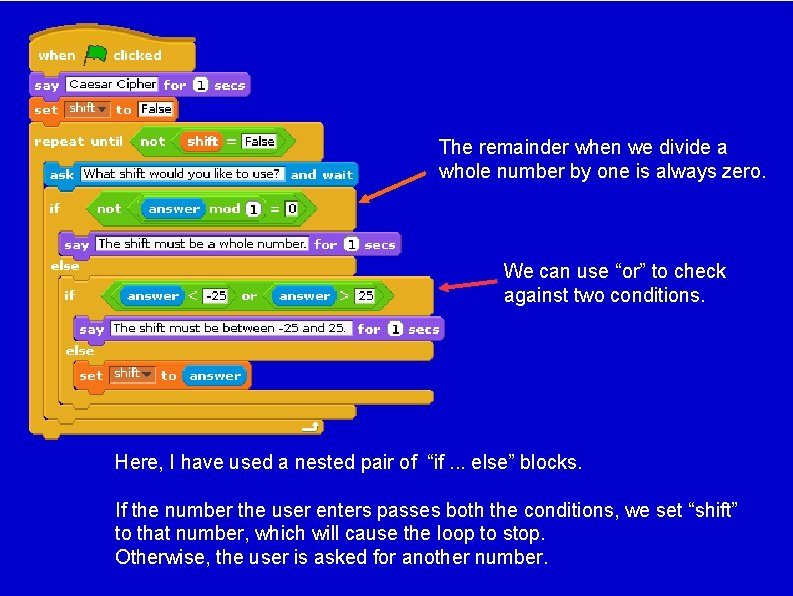
The remainder when we divide a whole number by one is always zero. We can use “or” to check against two conditions. Here, I have used a nested pair of “if. . . else” blocks. If the number the user enters passes both the conditions, we set “shift” to that number, which will cause the loop to stop. Otherwise, the user is asked for another number.
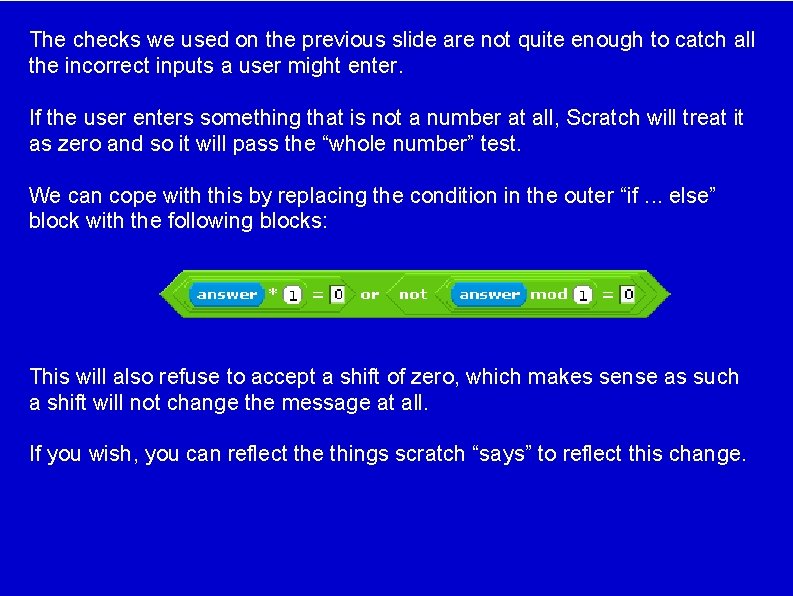
The checks we used on the previous slide are not quite enough to catch all the incorrect inputs a user might enter. If the user enters something that is not a number at all, Scratch will treat it as zero and so it will pass the “whole number” test. We can cope with this by replacing the condition in the outer “if. . . else” block with the following blocks: This will also refuse to accept a shift of zero, which makes sense as such a shift will not change the message at all. If you wish, you can reflect the things scratch “says” to reflect this change.
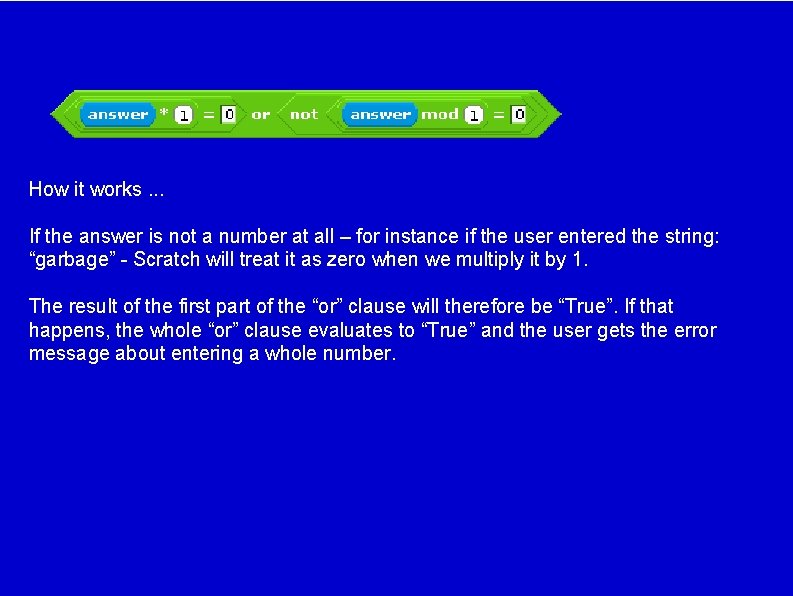
How it works. . . If the answer is not a number at all – for instance if the user entered the string: “garbage” - Scratch will treat it as zero when we multiply it by 1. The result of the first part of the “or” clause will therefore be “True”. If that happens, the whole “or” clause evaluates to “True” and the user gets the error message about entering a whole number.
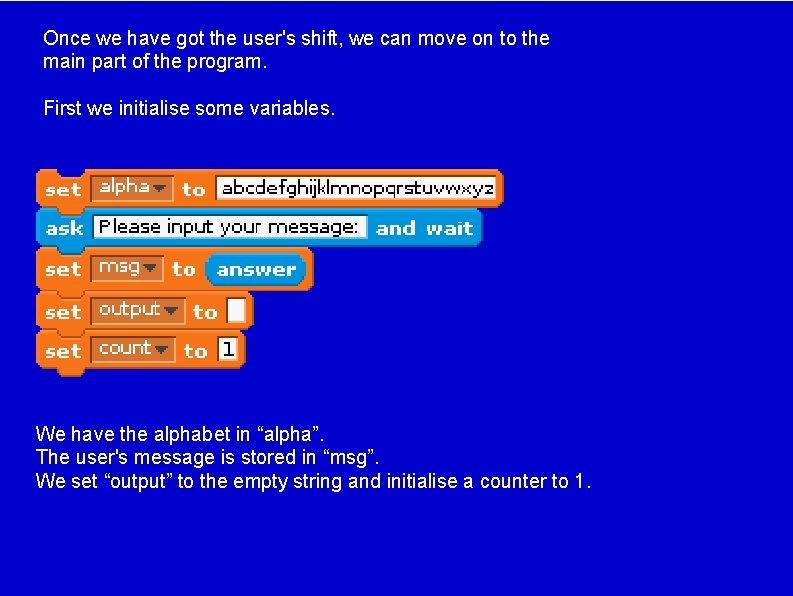
Once we have got the user's shift, we can move on to the main part of the program. First we initialise some variables. We have the alphabet in “alpha”. The user's message is stored in “msg”. We set “output” to the empty string and initialise a counter to 1.
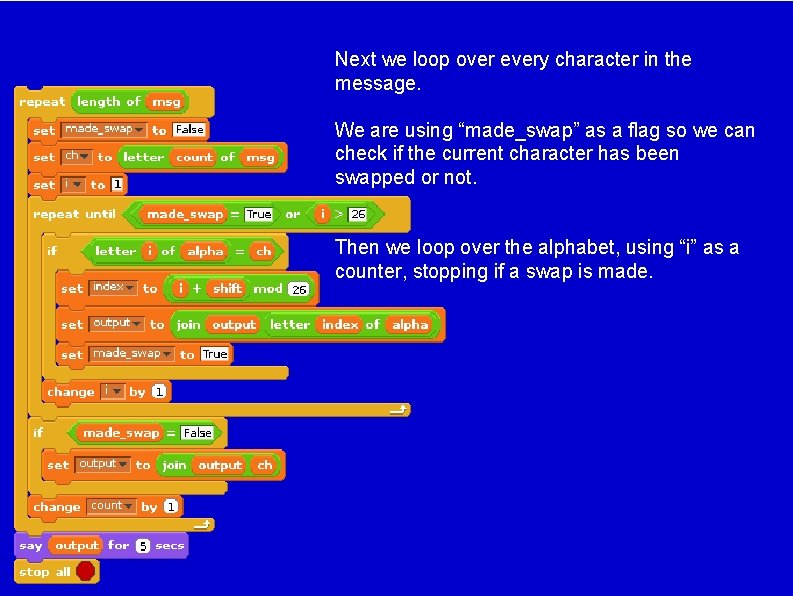
Next we loop over every character in the message. We are using “made_swap” as a flag so we can check if the current character has been swapped or not. Then we loop over the alphabet, using “i” as a counter, stopping if a swap is made.
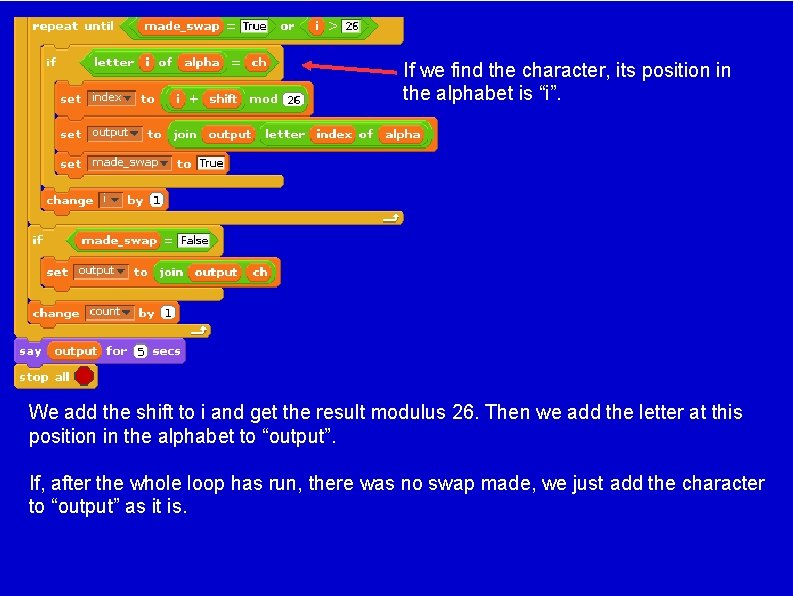
If we find the character, its position in the alphabet is “i”. We add the shift to i and get the result modulus 26. Then we add the letter at this position in the alphabet to “output”. If, after the whole loop has run, there was no swap made, we just add the character to “output” as it is.
Here's a sample run of the program. As you can see, Scratch treats lower and upper case letters as the same, so the whole message gets output as lower case. Numbers and punctuation come through unchanged.
Tasks 1: What number would you have to select as the shift if you wanted to decipher the message we just used to test our program? 2: Try sending an encrypted message to one of your classmates. Let them know what shift you used (keep it secret from everyone else!). 3: Can you use the Caesar Cipher script to encrypt and decrypt messages? 4: It would make the encryption more secure if we left out spaces, punctuation and numbers. Adapt the program to do this.
Extra Credit: Use the technique we used in the Bubble. Sort program for loading data from a text file. When you “import” a message into a list from a text file, each line in the file will become an item in the list. You'll need to loop over the list and process each item according to the shift the user specified. It would be nice to make a new list made up of the enciphered message. Then the user can “export” the output from the program into a new text file.
- Slides: 12