Hardwarerooted Trust for Secure Key Management Transient Trust
- Slides: 1

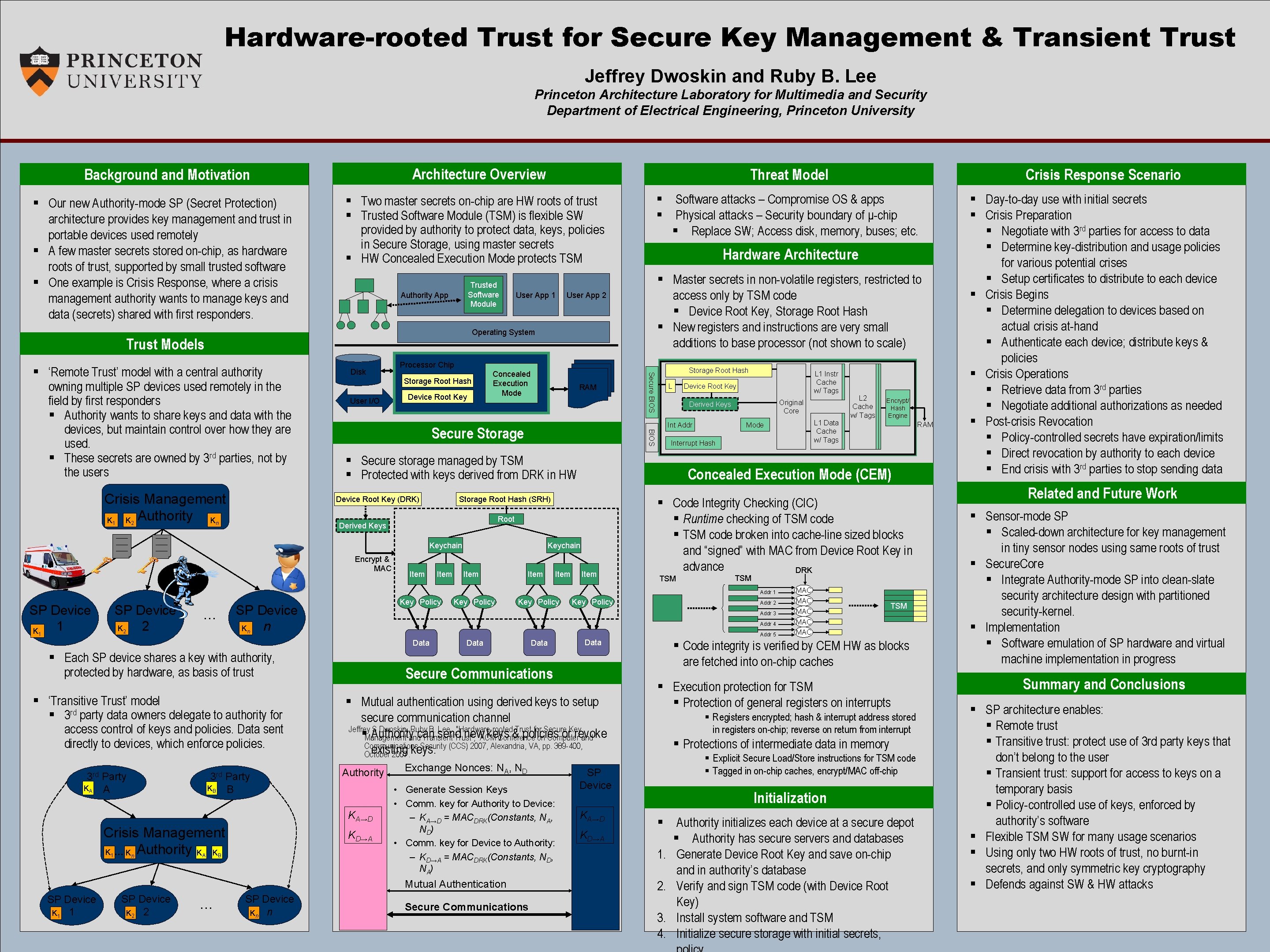
Hardware-rooted Trust for Secure Key Management & Transient Trust Jeffrey Dwoskin and Ruby B. Lee Princeton Architecture Laboratory for Multimedia and Security Department of Electrical Engineering, Princeton University Architecture Overview Background and Motivation § Our new Authority-mode SP (Secret Protection) architecture provides key management and trust in portable devices used remotely § A few master secrets stored on-chip, as hardware roots of trust, supported by small trusted software § One example is Crisis Response, where a crisis management authority wants to manage keys and data (secrets) shared with first responders. Threat Model § Software attacks – Compromise OS & apps § Physical attacks – Security boundary of μ-chip § Replace SW; Access disk, memory, buses; etc. § Two master secrets on-chip are HW roots of trust § Trusted Software Module (TSM) is flexible SW provided by authority to protect data, keys, policies in Secure Storage, using master secrets § HW Concealed Execution Mode protects TSM Trusted Software Module Authority App User App 1 Hardware Architecture § Master secrets in non-volatile registers, restricted to access only by TSM code § Device Root Key, Storage Root Hash § New registers and instructions are very small additions to base processor (not shown to scale) User App 2 Operating System Trust Models 1 2 ____ Storage Root Hash User I/O Device Root Key RAM Storage Root Hash L Storage Root Hash (SRH) Keychain Encrypt & MAC Item Item Interrupt Hash SP Device 1 K SP Device 2 K SP Device n K … 2 1 Item TSM n § ‘Transitive Trust’ model § 3 rd party data owners delegate to authority for access control of keys and policies. Data sent directly to devices, which enforce policies. Party A 3 rd KB Party B Crisis Management K … K Authority K K n A Data SP Device K 2 2 … SP Device Kn n Data § Mutual authentication using derived keys to setup secure communication channel Jeffrey S Dwoskin, Ruby B. Lee, "Hardware-rooted Trust for Secure Key §Management Authorityandcan send. Trust", new. ACM keys & policies or revoke Transient Conference on Computer and Communications Security (CCS) 2007, Alexandria, VA, pp. 389 -400, existing October 2007. keys. Authority Exchange Nonces: NA, ND • Generate Session Keys • Comm. key for Authority to Device: – KA→D = MACDRK(Constants, NA, N D) • Comm. key for Device to Authority: – KD→A = MACDRK(Constants, ND, NA ) Mutual Authentication SP Device K 1 1 Data Secure Communications KD→A B Addr 2 Addr 5 KA→D 1 Key Policy Addr 4 § Each SP device shares a key with authority, protected by hardware, as basis of trust KA Key Policy Secure Communications RAM TSM Addr 3 Data 3 rd Key Policy Encrypt/ Hash Engine § Code Integrity Checking (CIC) § Runtime checking of TSM code § TSM code broken into cache-line sized blocks and “signed” with MAC from Device Root Key in advance DRK Addr 1 Key Policy L 1 Data Cache w/ Tags Mode L 2 Cache w/ Tags Concealed Execution Mode (CEM) Root ____ Original Core Derived Keys § Secure storage managed by TSM § Protected with keys derived from DRK in HW Derived Keys L 1 Instr Cache w/ Tags Device Root Key Int Addr Secure Storage Device Root Key (DRK) n Concealed Execution Mode BIOS Crisis Management Authority K K Authority K Disk Processor Chip Secure BIOS § ‘Remote Trust’ model with a central authority owning multiple SP devices used remotely in the field by first responders § Authority wants to share keys and data with the devices, but maintain control over how they are used. § These secrets are owned by 3 rd parties, not by the users Crisis Response Scenario SP Device KA→D KD→A MAC MAC MAC TSM § Code integrity is verified by CEM HW as blocks are fetched into on-chip caches § Execution protection for TSM § Protection of general registers on interrupts § Registers encrypted; hash & interrupt address stored in registers on-chip; reverse on return from interrupt § Protections of intermediate data in memory § Explicit Secure Load/Store instructions for TSM code § Tagged in on-chip caches, encrypt/MAC off-chip Initialization § Authority initializes each device at a secure depot § Authority has secure servers and databases 1. Generate Device Root Key and save on-chip and in authority’s database 2. Verify and sign TSM code (with Device Root Key) 3. Install system software and TSM 4. Initialize secure storage with initial secrets, § Day-to-day use with initial secrets § Crisis Preparation § Negotiate with 3 rd parties for access to data § Determine key-distribution and usage policies for various potential crises § Setup certificates to distribute to each device § Crisis Begins § Determine delegation to devices based on actual crisis at-hand § Authenticate each device; distribute keys & policies § Crisis Operations § Retrieve data from 3 rd parties § Negotiate additional authorizations as needed § Post-crisis Revocation § Policy-controlled secrets have expiration/limits § Direct revocation by authority to each device § End crisis with 3 rd parties to stop sending data Related and Future Work § Sensor-mode SP § Scaled-down architecture for key management in tiny sensor nodes using same roots of trust § Secure. Core § Integrate Authority-mode SP into clean-slate security architecture design with partitioned security-kernel. § Implementation § Software emulation of SP hardware and virtual machine implementation in progress Summary and Conclusions § SP architecture enables: § Remote trust § Transitive trust: protect use of 3 rd party keys that don’t belong to the user § Transient trust: support for access to keys on a temporary basis § Policy-controlled use of keys, enforced by authority’s software § Flexible TSM SW for many usage scenarios § Using only two HW roots of trust, no burnt-in secrets, and only symmetric key cryptography § Defends against SW & HW attacks