Hardware Trojans The Hidden Malicious Insider Cyber Security

Hardware Trojans: The Hidden Malicious Insider Cyber Security Forum 06 -07 Feb, 2018 – Amman, Jordan Malek Al-Zewairi © 2018

About the Presenter Malek Al-Zewairi ﻣﺎﻟﻚ ﺍﻟﺰﻭﻳﺮﻱ Education Ph. D. Computer Science at PSUT – Intelligence and Security Informatics (2015 -) MSc. Information Systems Security & Digital Criminology (2012 -2014) BSc. Computer Information Systems (2007 -2011) Professional Experience Senior Security Consultant and Professional Trainer – Precise Thinking TCT Head of Information Security – University of Jordan (2 Years) Information Security & Risk Administrator – Orange Telecom (+2 years) Certification 16+ Professional Security Certificates

What are Hardware Trojans Analogous to Software Trojan (i. e. malicious software masquerade as a benign application) Hardware Trojans are malicious modifications (malicious circuit) to the hardware design or implementation Stays dormant during normal operation Once triggered by internal or external event, it causes the hardware to Fail!!!

What are Hardware Trojans Injected by intelligent adversary Have very small probability of occurrence Have very small hardware overhead Extremely hard to detect IT IS NOT LIKE Meltdown or Spectre
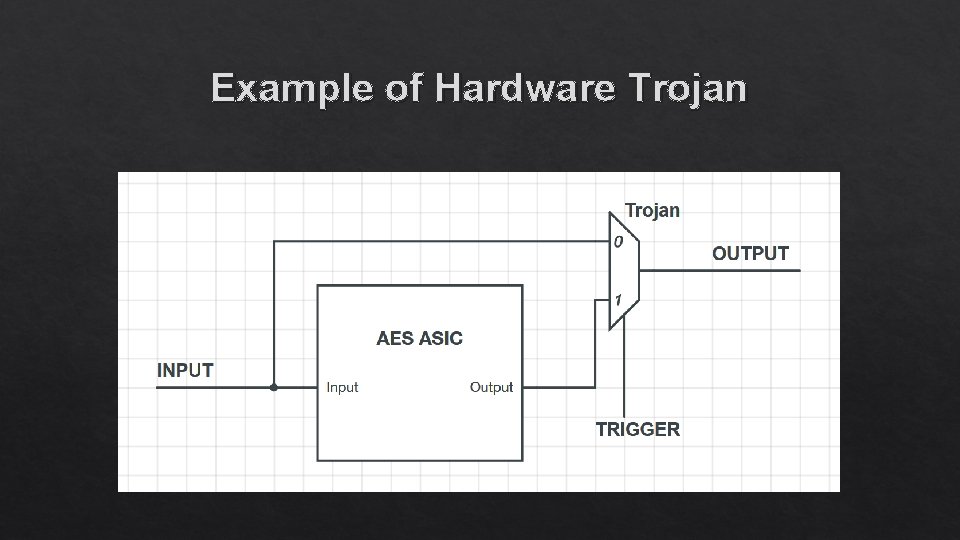
Example of Hardware Trojan

Main Targets of Hardware Trojans Military & Government Systems Critical Infrastructure (e. g. Power Grid, Nuclear Power Plant, …) Transportations (e. g. plans, trains, …) Telecommunication (e. g. Satellite, … ) Banking Systems

Real World Examples…

Case 1: Operation Orchard ( )ﻋﻤﻠﻴﺔ ﺍﻟﺒﺴﺘﺎﻥ On 5 th Sep 2007 at 23: 00, Ten Israeli F-15 fighters were tasked with a supposed emergency exercise At 23: 30 three jet fighters were called off the exercise, the remaining 7 fighters were ordered to change course to a new undisclosed coordination The Syrian Radar system in Tall al-Abuad ( ) ﺗﻞ ﺍﻷﺒﻴﺾ was deactivated by a secret built-in kill switch * Syria’s air defense systems, were showing a false sky-picture At 23: 58, Syria's al-Kibar ( )ﻣﻮﻗﻊ ﺍﻟﺑﺮ Nuclear Reactor was targeted with 17 tons of explosives using laser-guided bombs Syrian Radar systems So. Cs have been fabricated with Hardware Trojan * The Hunt for the Kill Switch, IEEE Spectrum, https: //spectrum. ieee. org/semiconductors/design/the-hunt-for-the-kill-switch/0

More Cases… Hardware Trojan was discovered on some Dell Edge. Power servers motherboards firmware ROM during testing, 2008 Operation Cisco Raider, USA, 2008 Hardware Trojan attack on Intel’s CSRNG reduces its entropy from 128 bits to 32 -bits, 2010 Spy-chips hidden in electric irons and kettles from China were discovered by Russian technician, 2013

A Hardware Trojans can be injected at Pre Silicon Post Silicon • Design, testing and debugging tools • Malicious IP design • Example: changing the thickness of wires, tampering with the clock speed • Add malicious circuits, reconnect wires • Fake or counterfeit chips • Example: adding a simple ring oscillator Trojan to cause power dissipation • Add malicious ICs in packaging • Malicious 3 rd party testers • Example: Dynamic Partial Reconfiguration (DPR) of FPGA
Does your organization have an active source-code review policy?
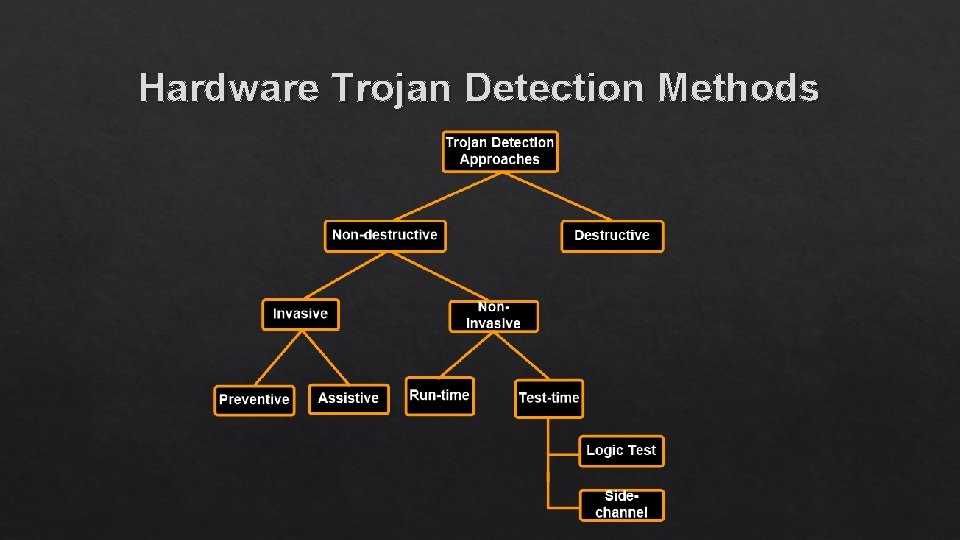
Hardware Trojan Detection Methods
Problem with current detection methods Lack of general detection techniques/frameworks Most proposed techniques cannot guarantee Trojan detection Destructive methods are not practical Searching for something that is Unknown! Test time is expensive (e. g. 2 billion States!!!) Trojans are designed to be stealthy

Q&A Thank You
References Hardware Trojan: Threats and Emerging Solutions, Chakraborty et al Understanding Integrated Circuit Security Threats, Asif Iqbal The Hunt for the Kill Switch, Sally Adee Stealthy Dopant-Level Hardware Trojans, Becker et al http: //www. homelandsecuritynewswire. com/dell-warns-hardware-trojan https: //archives. fbi. gov/archives/news/pressrel/press-releases/departments-of-justiceand-homeland-security-announce-30 -convictions-more-than-143 -million-in-seizuresfrom-initiative-targeting-traffickers-in-counterfeit-network-hardware http: //www. bbc. com/news/blogs-news-from-elsewhere-24707337
- Slides: 15