Hardware Based XML Security Components Forum Systems Inc

Hardware Based XML Security Components Forum Systems, Inc. 95 Sawyer Road Waltham, MA 02453 781 -788 -4200 http: //www. forumsys. com Data. Power Technology, Inc. One Alewife Center Cambridge, MA 02140 617 -864 -0455 http: //www. datapower. com
Topics • XML web. Services Security • Enterprise Deployments for XML Security • Hardware-Based XML Security • Interoperability • XML Security and FEA
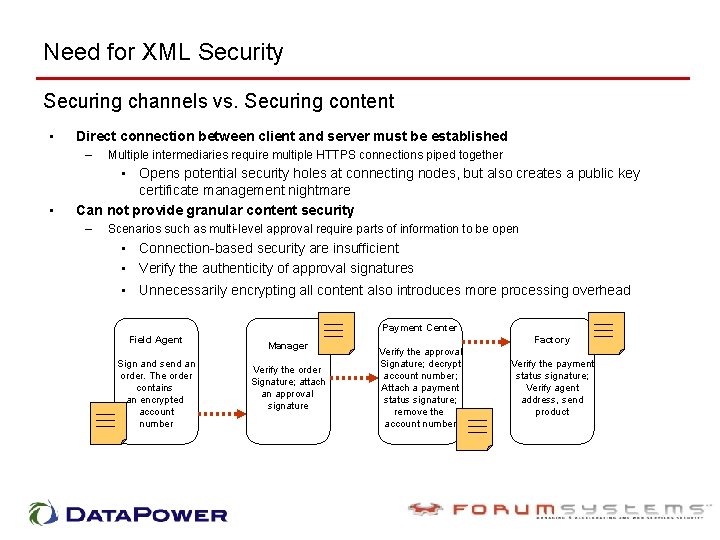
Need for XML Security Securing channels vs. Securing content • Direct connection between client and server must be established – • Multiple intermediaries require multiple HTTPS connections piped together • Opens potential security holes at connecting nodes, but also creates a public key certificate management nightmare Can not provide granular content security – Scenarios such as multi-level approval require parts of information to be open • Connection-based security are insufficient • Verify the authenticity of approval signatures • Unnecessarily encrypting all content also introduces more processing overhead Payment Center Field Agent Sign and send an order. The order contains an encrypted account number Manager Verify the order Signature; attach an approval signature Factory Verify the approval Signature; decrypt account number; Attach a payment status signature; remove the account number Verify the payment status signature; Verify agent address, send product
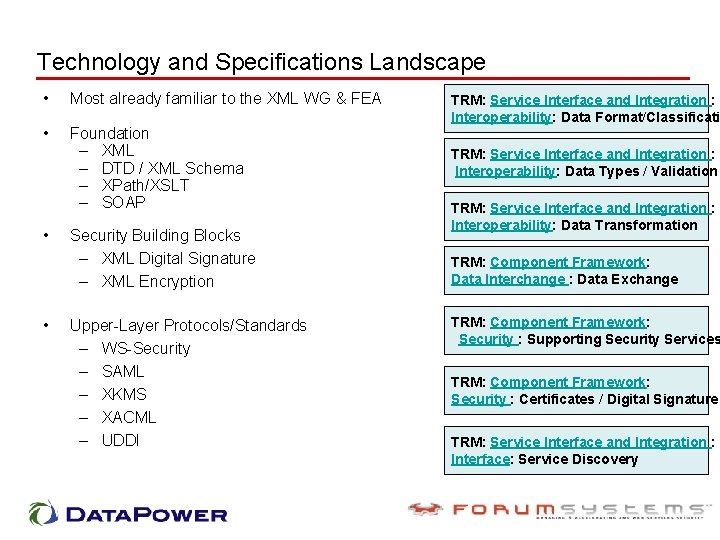
Technology and Specifications Landscape • Most already familiar to the XML WG & FEA • Foundation – XML – DTD / XML Schema – XPath/XSLT – SOAP • • Security Building Blocks – XML Digital Signature – XML Encryption Upper-Layer Protocols/Standards – WS-Security – SAML – XKMS – XACML – UDDI TRM: Service Interface and Integration : Interoperability: Data Format/Classificati TRM: Service Interface and Integration : Interoperability: Data Types / Validation TRM: Service Interface and Integration : Interoperability: Data Transformation TRM: Component Framework: Data Interchange : Data Exchange TRM: Component Framework: Security : Supporting Security Services TRM: Component Framework: Security : Certificates / Digital Signature TRM: Service Interface and Integration : Interface: Service Discovery
Sampling of XML Security Threats • Snooping – old problem made worse by human-readable formats • Tampering – alter invoice or PO – examples in semi-trusted environment • • Unauthorized action via valid interface Breach of memory space – buffer overwrite, HTTP overrun • Unintentionally exposed interface – methods not in public spec – automatic object marshalling to/from XML • XML Denial-of-Service (XDo. S) – attack at XML level – asymmetry of XML processing
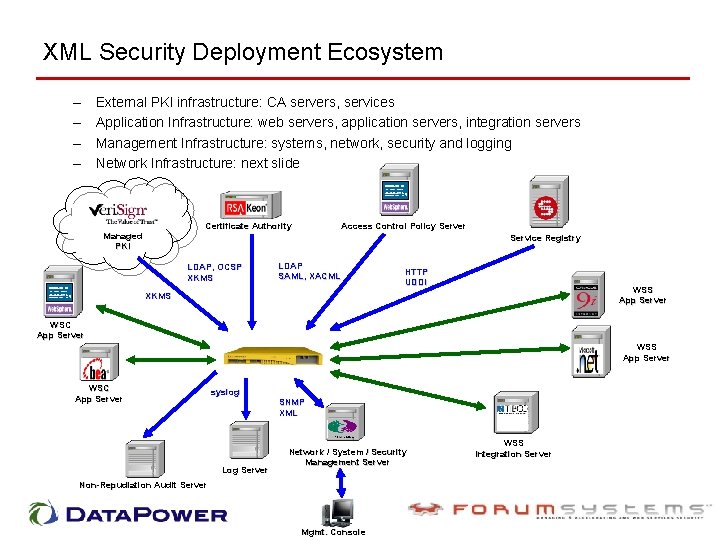
XML Security Deployment Ecosystem – – External PKI infrastructure: CA servers, services Application Infrastructure: web servers, application servers, integration servers Management Infrastructure: systems, network, security and logging Network Infrastructure: next slide Certificate Authority Managed PKI Access Control Policy Server Service Registry LDAP, OCSP XKMS LDAP SAML, XACML HTTP UDDI WSS App Server XKMS WSC App Server WSS App Server WSC App Server syslog SNMP XML Log Server Network / System / Security Management Server Non-Repudiation Audit Server Mgmt. Console WSS Integration Server
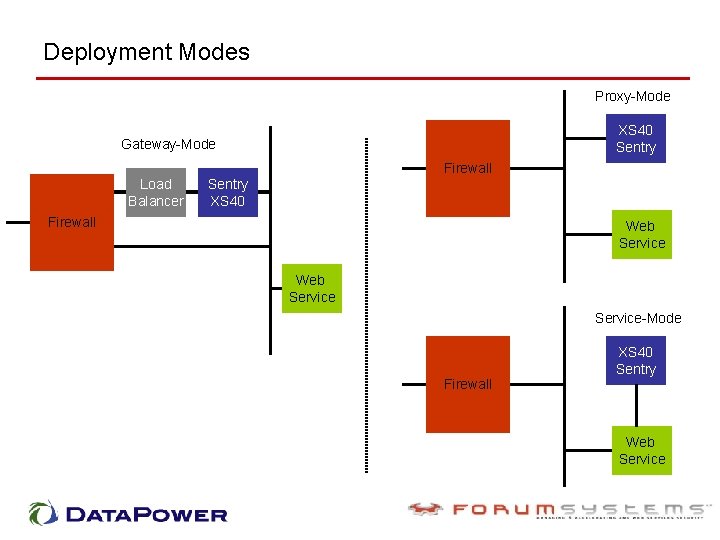
Deployment Modes Proxy-Mode XS 40 Sentry Gateway-Mode Load Balancer Firewall Sentry XS 40 Firewall Web Service-Mode Firewall XS 40 Sentry Web Service
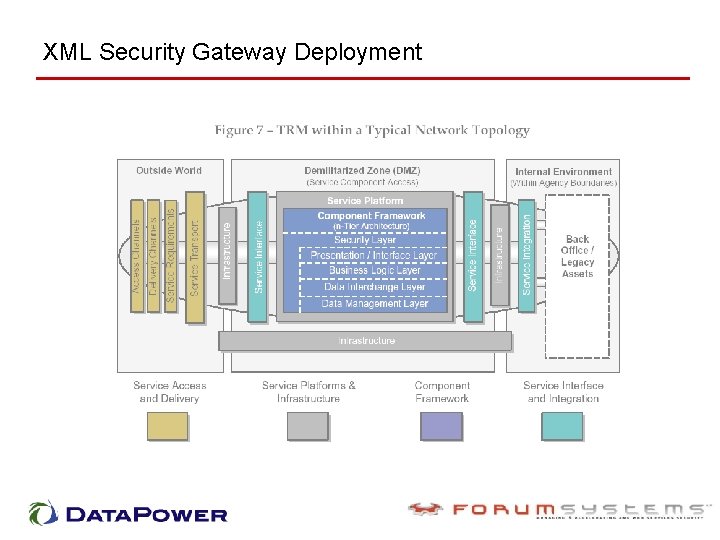
XML Security Gateway Deployment
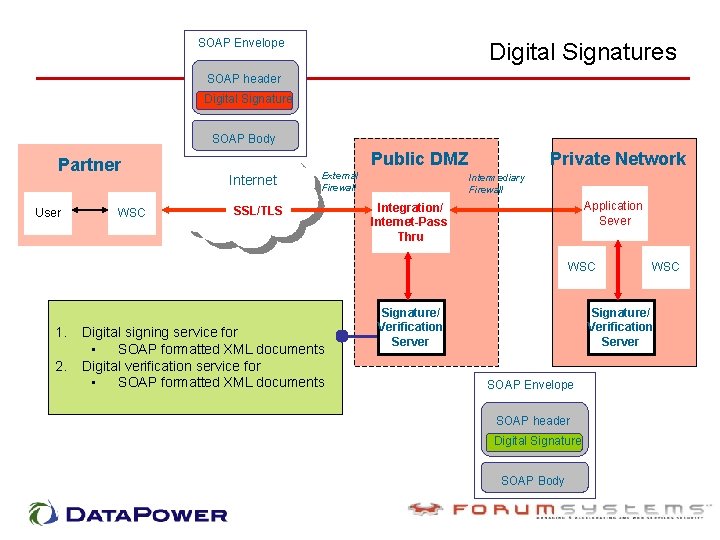
SOAP Envelope Digital Signatures SOAP header Digital Signature SOAP Body Partner User WSC Public DMZ Internet External Firewall SSL/TLS Private Network Intermediary Firewall Application Sever Integration/ Internet-Pass Thru WSC 1. 2. Digital signing service for • SOAP formatted XML documents Digital verification service for • SOAP formatted XML documents Signature/ Verification Server WSC Signature/ Verification Server SOAP Envelope SOAP header Digital Signature SOAP Body

Sign all outgoing messages • • • Protect against – Undetected message tempering – Liability of fake requests Recipient doesn’t have to be XML DSIG enabled Audit/verify transactions as originating from within own network Recipients can (but don’t have to) verify signatures for authentication Easy way to improve security – no reason not to start doing it today (except for maybe performance)
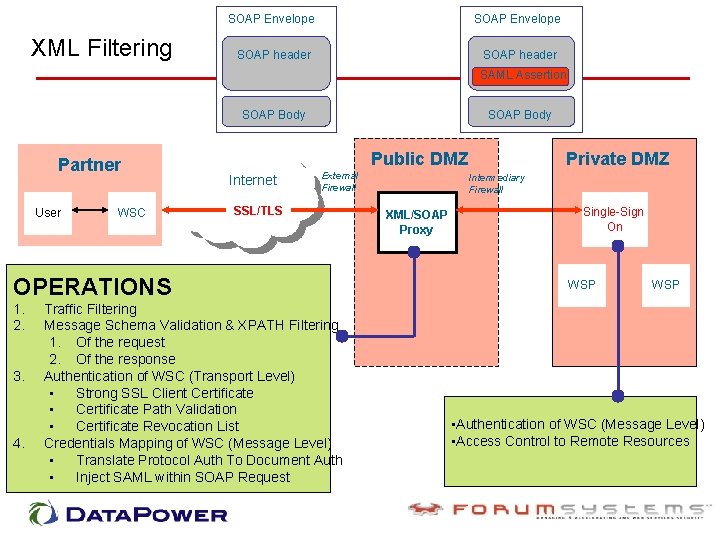
XML Filtering SOAP Envelope SOAP header SAML Assertion SOAP Body Partner User WSC SOAP Body Public DMZ Internet External Firewall SSL/TLS OPERATIONS 1. 2. 3. 4. Traffic Filtering Message Schema Validation & XPATH Filtering 1. Of the request 2. Of the response Authentication of WSC (Transport Level) • Strong SSL Client Certificate • Certificate Path Validation • Certificate Revocation List Credentials Mapping of WSC (Message Level) • Translate Protocol Auth To Document Auth • Inject SAML within SOAP Request Private DMZ Intermediary Firewall XML/SOAP Proxy Single-Sign On WSP • Authentication of WSC (Message Level) • Access Control to Remote Resources
The Need for Hardware Based XML Security • Hardware XML Security Reduces Complexity • Hardware XML Provides Hardened Security • Hardware XML Security Delivers superior Performance • Hardware XML Security Encourages Interoperability
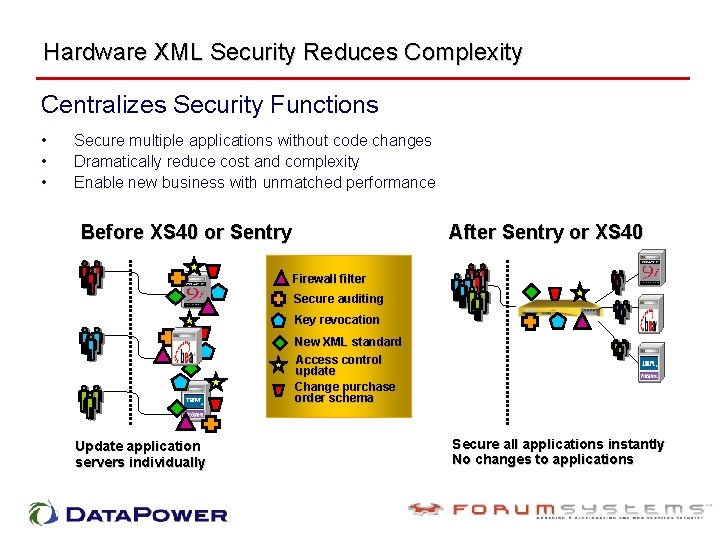
Hardware XML Security Reduces Complexity Centralizes Security Functions • • • Secure multiple applications without code changes Dramatically reduce cost and complexity Enable new business with unmatched performance Before XS 40 or Sentry After Sentry or XS 40 Firewall filter Secure auditing Key revocation New XML standard Access control update Change purchase order schema Update application servers individually Secure all applications instantly No changes to applications
Hardware provides Hardened Security • Accountability: – OS upgrades – Security software upgrades – Hardware upgrades • Hardened OS – Eliminate generic processes, daemons or listeners. • Hardware-based crypto Algorithms – Prevent application developers from using weak crypto implementations • Separation of Security Policies from Applications
XML Cryptography & Security Performance • Crypto operations are resource-intensive • Public-key crypto operations are very expensive • Familiar example SSL – A couple RSA ops per connection, bulk encryption – Today, SSL hardware acceleration is well-accepted practice • XML example: WS-Security based XML message – Signed header(s) – Public-key encrypted symmetric key – Encrypted payload sections – Signed payload sections – 10+ public-key ops per message is quite likely • Multiple messages per connection • XML processing also significant
XML hardware encourages interoperability • Coupled to the other systems by Ethernet jack, not custom code • Separation of concerns • Network gear business model based on “out-of-the-box” interop • Large software vendors focused on creating XML-enabled platforms – Functionality and development tools benefit – Interop is necessarily secondary, standards wars looming • Network vendors architecturally unable to achieve “lock-in” • Focused on a concrete set of challenges – XML security performance – Interoperability.
Overview of Hardware XML Security Market • A lot of vendors, large and small, claim to provide “XML security” or • This is natural, but can make selection confusing • Web services management vs. web services security • Most relatively small companies • Hardware model gaining traction • Recent inrush of pure-software vendors with “server appliances” • Standards support key to value “secure web services”
Interoperability promoted through Standards Bodies • Interoperability is hard work, but much more likely – WSI promotes web. Services Interoperability. • The WS-I testing tools are designed to help developers determine whether their Web services are conformant with Profile Guidelines. – “SOAP Specifications Assertions and Test Collection” • A SOAP 1. 2 implementation that passes all of the tests specified in this document may claim to conform to the SOAP 1. 2 • Baseline Standards have matured, for example: – SOAP 1. 1 – May 2000 – XML DSIG – Feb 2002 – SAML 1. 0 – November 2002 – WS-Security – April 2002 • Integration with CA’s, policy stores, schema repositories, service repository registries • Interoperability in a heterogeneous environment with application servers, in-house software, hardware devices from other vendors
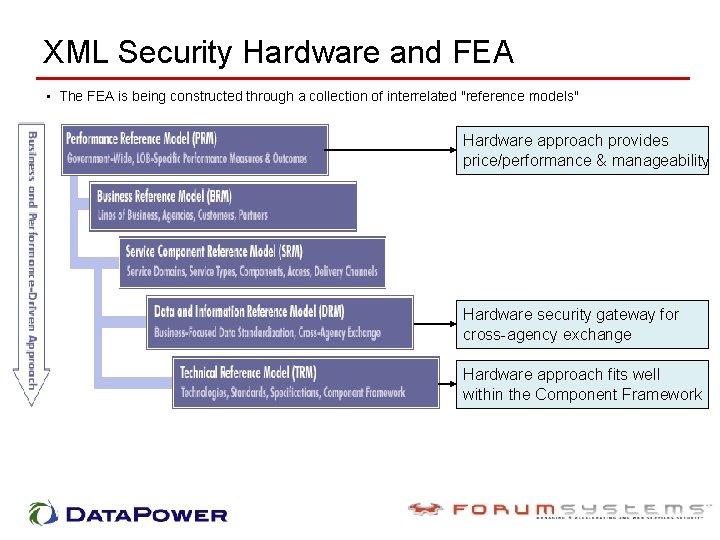
XML Security Hardware and FEA • The FEA is being constructed through a collection of interrelated "reference models" Hardware approach provides price/performance & manageability Hardware security gateway for cross-agency exchange Hardware approach fits well within the Component Framework
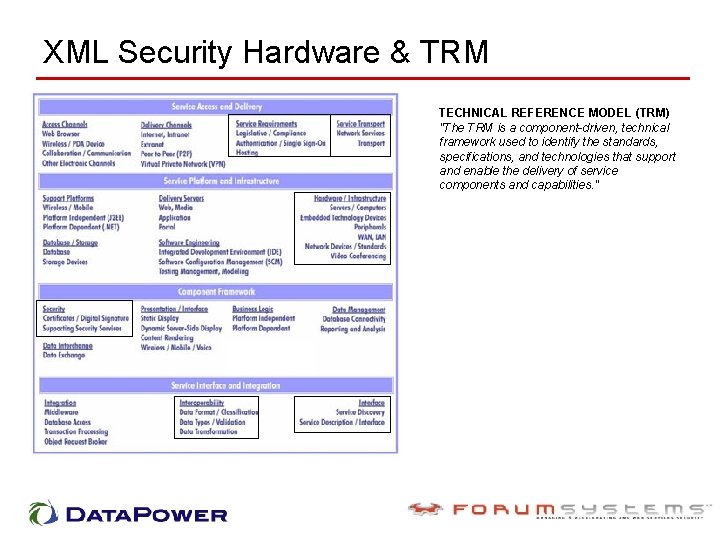
XML Security Hardware & TRM TECHNICAL REFERENCE MODEL (TRM) "The TRM is a component-driven, technical framework used to identify the standards, specifications, and technologies that support and enable the delivery of service components and capabilities. "
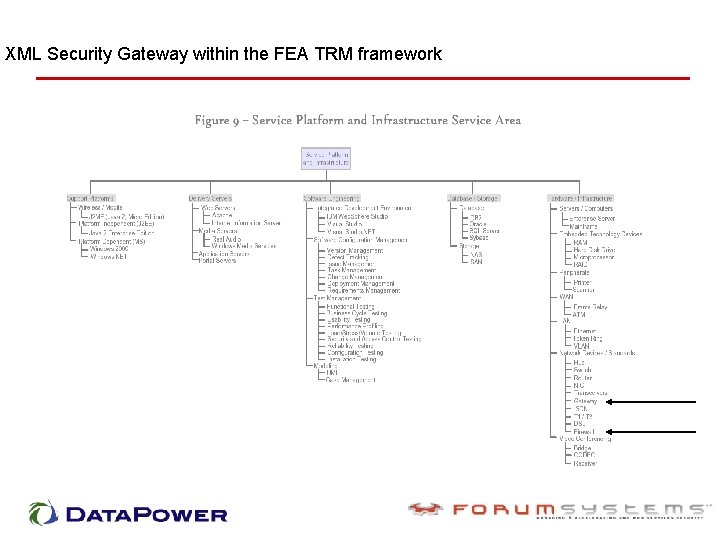
XML Security Gateway within the FEA TRM framework
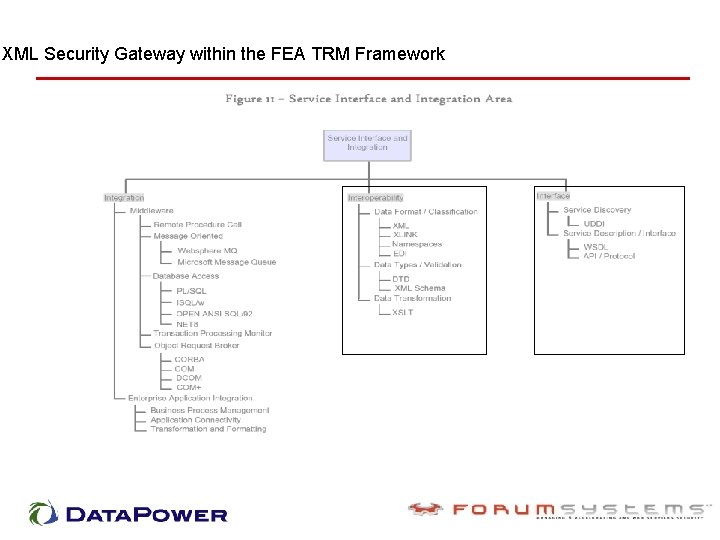
XML Security Gateway within the FEA TRM Framework
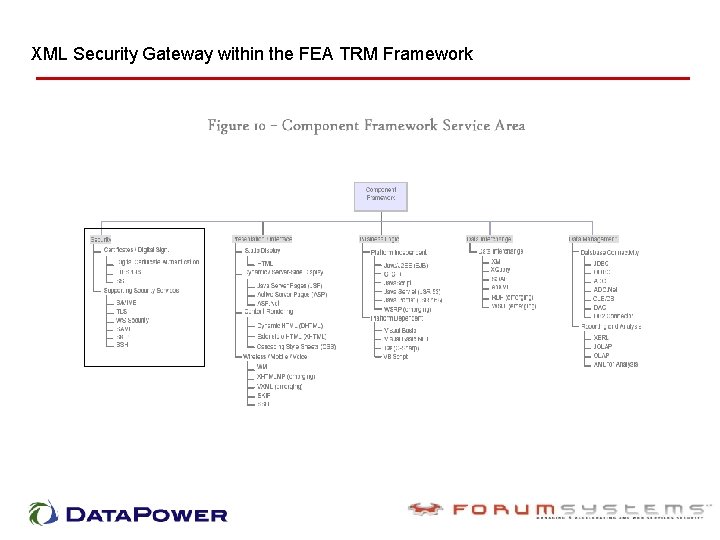
XML Security Gateway within the FEA TRM Framework
Q&A Mamoon Yunus Forum Systems, Inc. 95 Sawyer Road Waltham, MA 02453 781 -788 -4200 http: //www. forumsys. com Eugene Kuznetsov Data. Power Technology, Inc. One Alewife Center Cambridge, MA 02140 (617)864 -0455 http: //www. datapower. com
- Slides: 24