Handshake Protocols COEN 350 Threat Model n Passive





















- Slides: 23

Handshake Protocols COEN 350

Threat Model n Passive Sniffing n n Spoofing n n Malicious Mallory can read messages between Alice and Bob. Malicious Mallory can create messages that seem to come from either Alice or Bob. Standard Attack Modes: n n Breaking Cryptography Man-in-the-Middle Replay Attacks Reflection Attack (Open several connections)

Simple Password Protocol Alice: Hi, I am Alice. My password is “fiddlesticks”. Bob: Welcome, Alice. Vulnerable to sniffing and replay attack: Mallory sniffs the exchange. Mallory: Hi, I am Alice. My password is “fiddlesticks”. Bob: Welcome, Alice.

Shared Secret Alice and Bob share a secret key K. Alice: I am Alice. Bob: Encrypt random number R. Alice: EK(R) Bob (calculates EK(R) as well. ): Welcome Alice.

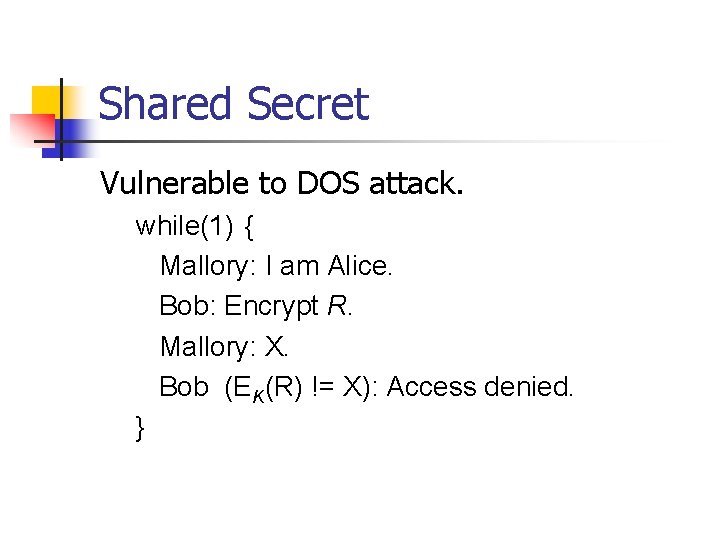
Shared Secret Vulnerable to DOS attack. while(1) { Mallory: I am Alice. Bob: Encrypt R. Mallory: X. Bob (EK(R) != X): Access denied. }

Shared Secret Vulnerable to sniffing and replay attack if R is not random or if R is repeated.

Shared Secret Use of Clock: Alice: I am Alice, EK(clock). Bob calculates clock, compares with his value: Welcome Alice. Problems with clock accuracy: Demand tight accuracy: drifting clocks can be bad. Otherwise: replay attack.

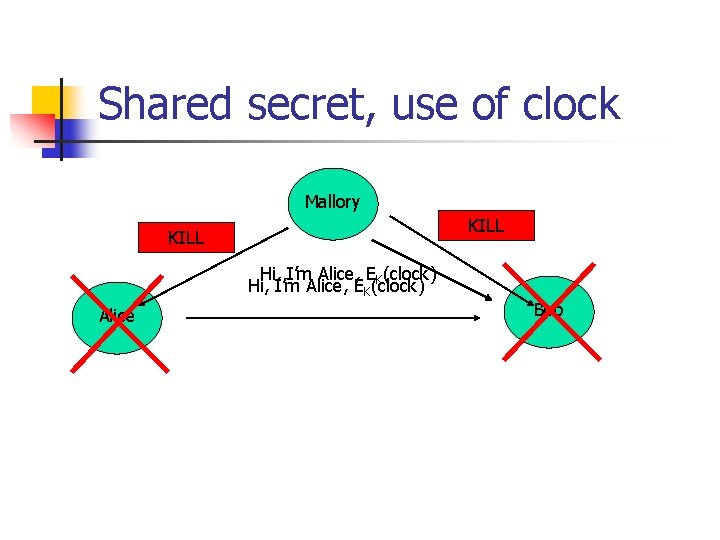
Shared secret, use of clock Sniffing + replay attack: Mallory to Bob: KILL, KILL. (Bob cannot receive messages because his message buffer is filled up. ) Alice: Hi, I’m Alice. EK(clock). Mallory to Alice: KILL, KILL. (Alice cannot receive messages because her message buffer is filled up. ) Mallory to Bob: Hi, I’m Alice. EK(clock). Bob: Hi, Alice.

Shared secret, use of clock Mallory KILL Hi, I’m Alice, EK(clock) Alice Bob

Public Key Alice: “I’m Alice. ” Bob: “R”. Alice: “EAlice(R)”. Bob calculates “DAlice. EAlice(R) == R”: Hi Alice.

Public Key Alice: “I’m Alice. ” Bob creates random challenge R: “EAlice(R)”. Alice: “R”. Bob checks “R == R”: Hi Alice.

Public Key: DOS attack Trudy: “I’m Alice. ” Bob: “R”. Trudy: “X” Bob calculates “DAlice. EAlice(X) != R: Access Denied. Bob spends much more time computing than Trudy!

Mutual Authentication: Shared Secret Alice: “I am Alice” Bob: “RB” Alice: EK(RB). RA. Bob calculates EK(RB) himself: EK(RA). Hi Alice calculates EK(RA) herself: Hi Bob.

Mutual Authentication with less messages? Alice: I am Alice. RA Bob: RB. EK(RA). Alice: Hi Bob. EK(RB). Bob: Hi Alice.

Mutual Authentication with less steps is vulnerable to the reflection attack Session Session 1 1 2 2 1 1 Trudy: I am Alice. RA. Bob: RB. EK(RA). Trudy: I am Alice. RB. Bob: RB’. EK(RB). Trudy: Hi Bob. EK(RB). Bob: Hi Alice.

Warning Signals n n n Requestor should authenticate herself first. Don’t have requestor and requestee do exactly the same thing. (E. g. use different key pairs. ) If you provide encryption service, you set yourself up for a key guessing attack.

Public Key: Simple Mutual Authentication Alice: “I am Alice. RA” Bob: “EBob(RA). RB” Alice DBob. EBob (RA)=RA: Hello Bob. EAlice(RB). Bob: DAlice. EAlice(RB) = RB: Hello Alice.

Key Distribution Centers n n Maintains a shared secret for each registered user. To set-up a connection requires the KDC to set up a session key.

Key Distribution Center Original Algorithm n n n Alice to KDC: Alice wants Bob. KDC to Alice: Here is your session key. KDC to Bob: Here is your session key. This needs to be modified.

Key Distribution Center: Needham Schroeder Protocol Alice to KDC: N 1, Alice wants Bob. KDC to Alice: KA(N 1, KS, Bob, Ticket), where Ticket=KB(KS, Alice). Alice to Bob: Ticket, KS(N 2). Bob to Alice: KS(N 2 -1, N 3). Alice to Bob: KS(N 3 -1). N 1, N 2, N 3 are nonces to prevent replay attacks.

Key Distribution Center: Needham Schroeder Protocol Variant Alice to KDC: N 1, Alice wants Bob. KDC to Alice: KA(N 1, KS, Bob, Ticket), where Ticket=KB(KS, Alice). Alice to Bob: Ticket, KS(N 2). Bob to Alice: KS(N 2 -1), KS(N 3). Alice to Bob: K(N 3 -1). N 1, N 2, N 3 are nonces to prevent replay attacks.

Replay attack on modified NS Alice to KDC: N 1, Alice wants Bob. KDC to Alice: KA(N 1, KS, Bob, Ticket), where Ticket=KB(KS, Alice). Alice to Bob: Ticket, KS(N 2). Bob to Alice: KS(N 2 -1), KS(N 3). Alice to Bob: KS(N 3 -1). Trudy as Alice to Bob: Ticket, KS(N 2) Bob to Alice, but intercepted by Trudy: KS(N 2 -1), KS(N 4) Trudy as Alice to Bob: Ticket, KS(N 4). Bob to Alice, but intercepted by Trudy. KS(N 4 -1), KS(N 5). Trudy as Alice to Bob: KS(N 4 -1).

Key Distribution Center n n n Assume that Alice’s key has become compromised. Trudy can now present herself as Alice to Bob with an old ticket. Tickets need to have an expiration date!!!!!!