Hacksim Hack Sim An Automation of Penetration Testing









- Slides: 24

Hacksim Hack. Sim : An Automation of Penetration Testing POSTECH HPC Lab. 이 승민 2004 -07 -29 Hack. Sim Project /15

Contents l Introduction l Tutorials for Two Issues • • Safe Pen-Test for Windows Remote Exploit Codes for Windows l Demo (? ) 2004 -07 -29 Hack. Sim Project 2


Safe Pen-Test for Windows 2004 -07 -29 Hack. Sim Project /15

Contents of Safe Pen-Test l Introduction l Using Kernel Service l Jump to the Shellcode • • Brute Force & Offline Attack Safe Jump l Conclusion l Future Works 2004 -07 -29 Hack. Sim Project 5

Introduction l Application Crash • • After attack, Application often ends with a crash. Such behavior may be easily notified and the attack may be detected. In some cases it may influence the whole system stability. In multithreaded application, the whole application is terminated. l Each stage must work correctly. • • Loading shellcode to the target host Jumping to the start address of shellcode Using kernel service Termination 2004 -07 -29 Hack. Sim Project 6

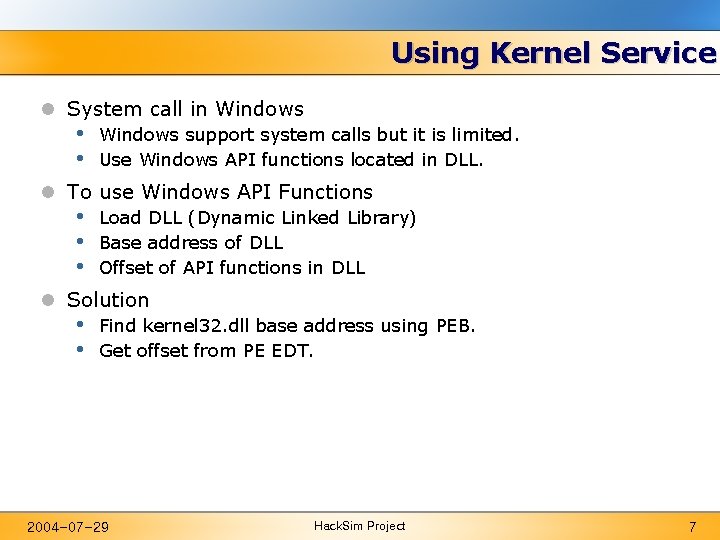
Using Kernel Service l System call in Windows • • Windows support system calls but it is limited. Use Windows API functions located in DLL. l To use Windows API Functions • • • Load DLL (Dynamic Linked Library) Base address of DLL Offset of API functions in DLL l Solution • • Find kernel 32. dll base address using PEB. Get offset from PE EDT. 2004 -07 -29 Hack. Sim Project 7

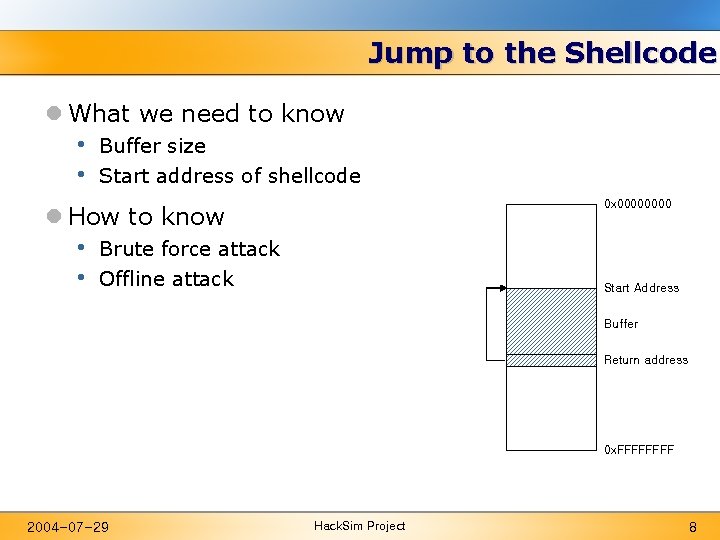
Jump to the Shellcode l What we need to know • • Buffer size Start address of shellcode 0 x 0000 l How to know • • Brute force attack Offline attack Start Address Buffer Return address 0 x. FFFF 2004 -07 -29 Hack. Sim Project 8

Jump to the Shellcode (2/4) Brute Force & Offline Attack l Windows do not allow Brute force attack. l Process or Thread creation uses Create. Process/Create. Thread function. • Internally calls Base. Process. Start/Base. Thread. STart in kernel 32. dll. VOID Base. Process. Start(PROCESS_START_ROUTINE pfn. Start. Addr) { __try { Exit. Thread((pfn. Start. Addr)()); } __except(Unhandled. Exception. Filter(Get. Exception. Information ())) { Exit. Process(Get. Exception. Code()); } } l Knowing buffer size is trivial in offline attack. l Knowing start address of buffer in memory • • Thread stack allocates consecutively in multithread. Start address dependes on versions of Windows and service packs. 2004 -07 -29 Hack. Sim Project 9

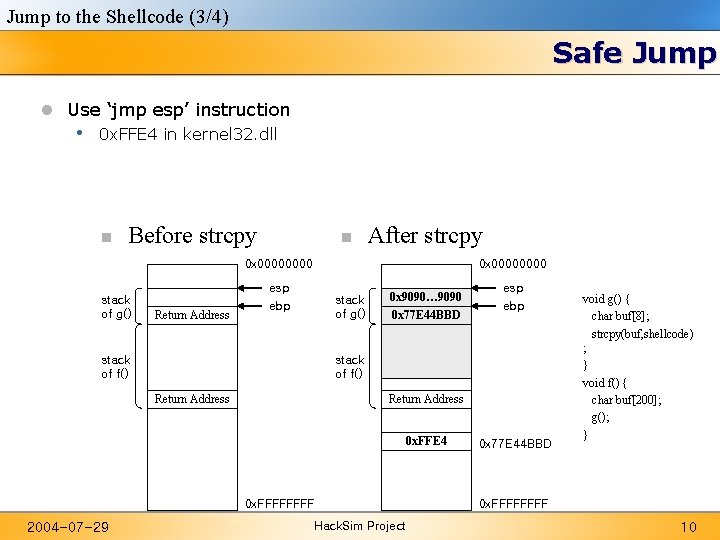
Jump to the Shellcode (3/4) Safe Jump l Use ‘jmp esp’ instruction • 0 x. FFE 4 in kernel 32. dll n Before strcpy n After strcpy 0 x 0000 stack of g() Return Address 0 x 0000 esp ebp stack of g() stack of f() 0 x 9090… 9090 0 x 77 E 44 BBD stack of f() Return Address 0 x. FFE 4 0 x. FFFF 2004 -07 -29 esp ebp Hack. Sim Project 0 x 77 E 44 BBD void g() { char buf[8]; strcpy(buf, shellcode) ; } void f() { char buf[200]; g(); } 0 x. FFFF 10

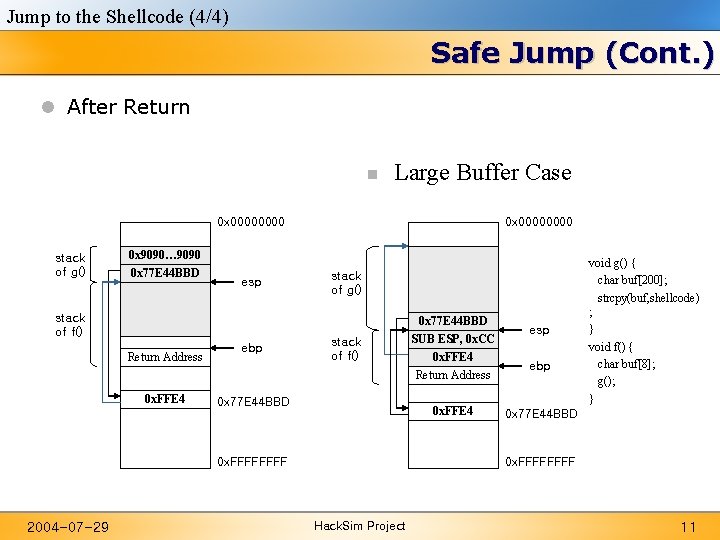
Jump to the Shellcode (4/4) Safe Jump (Cont. ) l After Return n Large Buffer Case 0 x 0000 stack of g() 0 x 9090… 9090 0 x 77 E 44 BBD esp stack of f() Return Address 0 x. FFE 4 ebp 0 x 0000 stack of g() stack of f() 0 x 77 E 44 BBD 0 x. FFE 4 esp ebp 0 x 77 E 44 BBD 0 x. FFFFFFFF 2004 -07 -29 0 x 77 E 44 BBD SUB ESP, 0 x. CC 0 x. FFE 4 Return Address void g() { char buf[200]; strcpy(buf, shellcode) ; } void f() { char buf[8]; g(); } Hack. Sim Project 11

Conclusion l Windows doesn’t allow brute force attack. l The image of ‘jmp esp’ makes it easy to guess the start address of shellcode in multithread envionment. • • Load shellcode in caller stack One more jump to the callee stack l It might work well in dynamic stack method. l But ‘jmp esp’ instruction locates different from versions of Windows and service packs. 2004 -07 -29 Hack. Sim Project 12

Future Works l Safe Jump • • Survey the image of ‘jmp esp/ebx’. Implement powerful OS Fingerprinting tools. l Safe Termination • • 2004 -07 -29 Exit. Thread function works well currently. We need to verify this method. Hack. Sim Project 13

Remote Exploit Codes for Windows 2004 -07 -29 Hack. Sim Project /15

Contents of Remote Exploit l Get the Remote Shell • Issues for Getting the Remote Shell l Get the Remote Exploit • • Public Exploit Codes Candidate § RPC DCOM § LSASS • Analysis Process l Future Work 2004 -07 -29 Hack. Sim Project 15

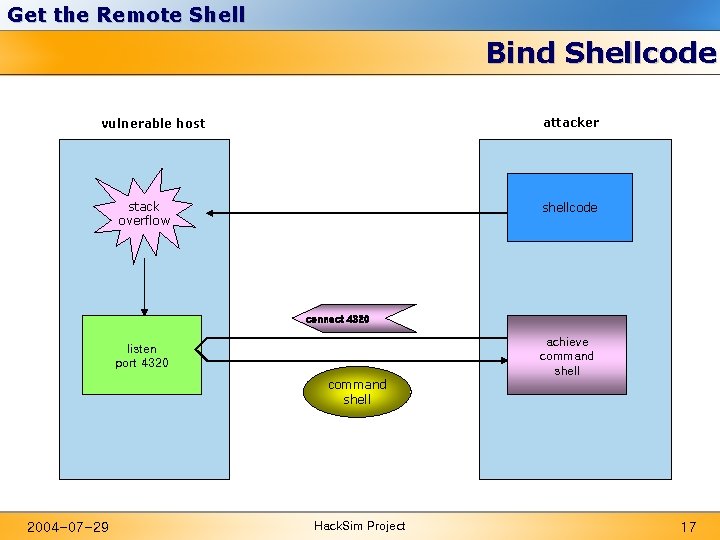
Get the Remote Shell Issues for Getting the Remote Shell l Loading ws 2_32. dll using Load. Library() • • Push the string “ws 2_32” to stack. Call Load. Library. A() function. l Redirecting standard input, output and error to socket • • Set the value of h. Std. Input, h. Std. Output, h. Std. Error to connected socket in STARTUPINFO struct. Set the value b. Inherit. Handles to true among arguments of Create. Process() function. l Implementation • • Bind Shellcode Reverse Shellcode 2004 -07 -29 Hack. Sim Project 16

Get the Remote Shell Bind Shellcode attacker vulnerable host stack overflow shellcode connect 4320 achieve command shell listen port 4320 command shell 2004 -07 -29 Hack. Sim Project 17

Get the Remote Shell Reverse Shellcode attacker vulnerable host 2004 -07 -29 stack overflow shellcode command shell listen port 4320 Hack. Sim Project 18

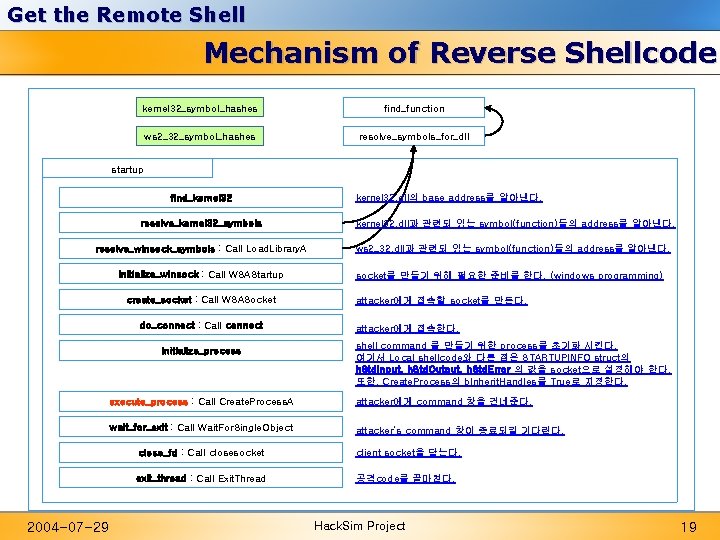
Get the Remote Shell Mechanism of Reverse Shellcode kernel 32_symbol_hashes find_function ws 2_32_symbol_hashes resolve_symbols_for_dll startup find_kernel 32. dll의 base address를 알아낸다. resolve_kernel 32_symbols kernel 32. dll과 관련되 있는 symbol(function)들의 address를 알아낸다. resolve_winsock_symbols : Call Load. Library. A ws 2_32. dll과 관련되 있는 symbol(function)들의 address를 알아낸다. initialize_winsock : Call WSAStartup create_socket : Call WSASocket do_connect : Call connect initialize_process 2004 -07 -29 socket를 만들기 위해 필요한 준비를 한다. (windows programming) attacker에게 접속할 socket를 만든다. attacker에게 접속한다. shell command 를 만들기 위한 process를 초기화 시킨다. 여기서 Local shellcode와 다른 점은 STARTUPINFO struct의 h. Std. Input, h. Std. Output, h. Std. Error 의 값을 socket으로 설정해야 한다. 또한, Create. Process의 b. Inherit. Handles를 True로 지정한다. execute_process : Call Create. Process. A attacker에게 command 창을 건네준다. wait_for_exit : Call Wait. For. Single. Object attacker’s command 창이 종료되길 기다린다. close_fd : Call closesocket client socket을 닫는다. exit_thread : Call Exit. Thread 공격code를 끝마친다. Hack. Sim Project 19

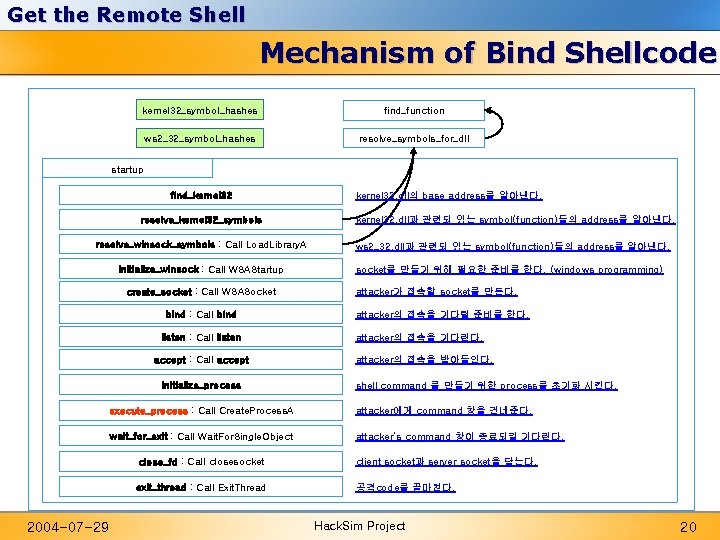
Get the Remote Shell Mechanism of Bind Shellcode kernel 32_symbol_hashes find_function ws 2_32_symbol_hashes resolve_symbols_for_dll startup find_kernel 32. dll의 base address를 알아낸다. resolve_kernel 32_symbols kernel 32. dll과 관련되 있는 symbol(function)들의 address를 알아낸다. resolve_winsock_symbols : Call Load. Library. A ws 2_32. dll과 관련되 있는 symbol(function)들의 address를 알아낸다. initialize_winsock : Call WSAStartup create_socket : Call WSASocket bind : Call bind listen : Call listen accept : Call accept initialize_process 2004 -07 -29 socket를 만들기 위해 필요한 준비를 한다. (windows programming) attacker가 접속할 socket를 만든다. attacker의 접속을 기다릴 준비를 한다. attacker의 접속을 기다린다. attacker의 접속을 받아들인다. shell command 를 만들기 위한 process를 초기화 시킨다. execute_process : Call Create. Process. A attacker에게 command 창을 건네준다. wait_for_exit : Call Wait. For. Single. Object attacker’s command 창이 종료되길 기다린다. close_fd : Call closesocket client socket과 server socket을 닫는다. exit_thread : Call Exit. Thread 공격code를 끝마친다. Hack. Sim Project 20

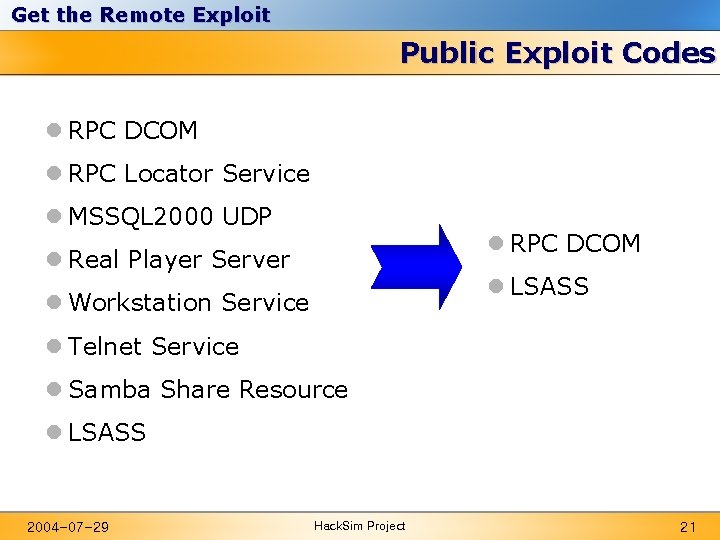
Get the Remote Exploit Public Exploit Codes l RPC DCOM l RPC Locator Service l MSSQL 2000 UDP l RPC DCOM l Real Player Server l LSASS l Workstation Service l Telnet Service l Samba Share Resource l LSASS 2004 -07 -29 Hack. Sim Project 21

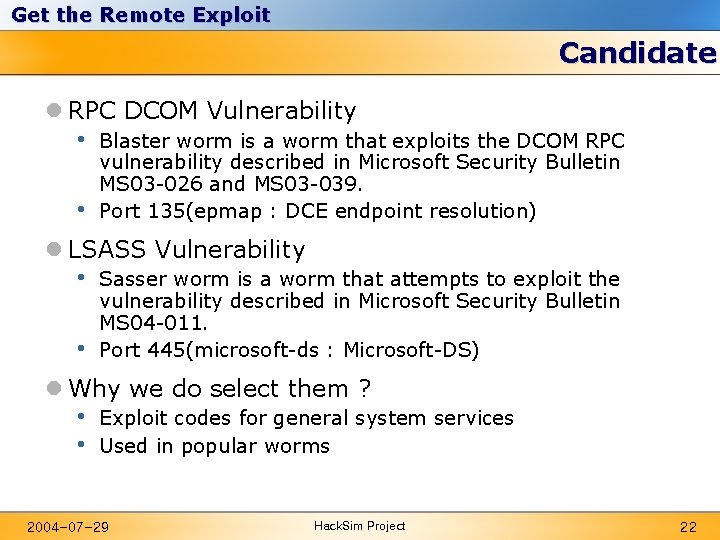
Get the Remote Exploit Candidate l RPC DCOM Vulnerability • • Blaster worm is a worm that exploits the DCOM RPC vulnerability described in Microsoft Security Bulletin MS 03 -026 and MS 03 -039. Port 135(epmap : DCE endpoint resolution) l LSASS Vulnerability • • Sasser worm is a worm that attempts to exploit the vulnerability described in Microsoft Security Bulletin MS 04 -011. Port 445(microsoft-ds : Microsoft-DS) l Why we do select them ? • • Exploit codes for general system services Used in popular worms 2004 -07 -29 Hack. Sim Project 22

Get the Remote Exploit Analysis Process l Checkpoint • • shellcode return address l DCOM exploit • • It operated for english windows XP. We found the image of return address in english windows. We got the address of the image in korean windows. Using the address, it operates for korean windows. l LSASS exploit • • The image is “jmp esp” or “jmp ebx” in kernel 32. dll, etc. We used the address of them as a return address. 2004 -07 -29 Hack. Sim Project 23

Future Work l Survey more vulnerabilities. l Analyze & modularize selected exploit codes. • • RPC DCOM LSASS l Propose a pen-testing framework for windows. l Adapt exploit codes in linux environments. 2004 -07 -29 Hack. Sim Project 24