Hacking UnixLinux Footprinting Scanning Enumeration l Footprinting Similar




- Slides: 6

Hacking Unix/Linux

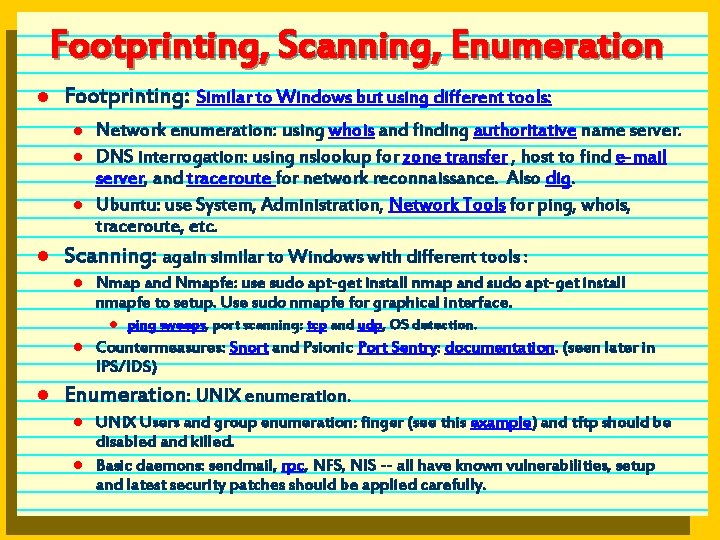
Footprinting, Scanning, Enumeration l Footprinting: Similar to Windows but using different tools: l l Network enumeration: using whois and finding authoritative name server. DNS interrogation: using nslookup for zone transfer , host to find e-mail server, and traceroute for network reconnaissance. Also dig. Ubuntu: use System, Administration, Network Tools for ping, whois, traceroute, etc. Scanning: again similar to Windows with different tools : l Nmap and Nmapfe: use sudo apt-get install nmap and sudo apt-get install nmapfe to setup. Use sudo nmapfe for graphical interface. l l l ping sweeps, port scanning: tcp and udp, OS detection. Countermeasures: Snort and Psionic Port Sentry: documentation. (seen later in IPS/IDS) Enumeration: UNIX enumeration. l l UNIX Users and group enumeration: finger (see this example) and tftp should be disabled and killed. Basic daemons: sendmail, rpc, NFS, NIS -- all have known vulnerabilities, setup and latest security patches should be applied carefully.

Getting started l Vulnerability mapping: identify specific software vulnerabilities (e. g. sendmail, telnet, ftp, NFS, apache). l Quest for root: root or nothing ? Su - root. l Remote access: gaining access via the network l l Local access: having access to a shell or login to the system l l l exploit a listening daemon/service a UNIX system performing routing with IP forwarding enabled user-initiated remote execution (hostile Web site, Trojan horses, etc) privilege escalation attacks (from login to root) once a remote access exploits a vulnerability it gains local shell access Brute force attacks: (we will see John the Ripper but not Hydra) l l l remote login programs: telnet, ftp, rlogin. rsh, ssh, http plus a tool to crack the username/password combination. The /etc/passwd file. You should use shadow passwords. Countermeasures: password education and software (e. g. checkpassd)

Remote access l Data driven attacks: sending data to an active service that causes unintended results, generally allowing access to the system l Buffer Overflow: same Windows vulnerabilities (C programs). Countermeasures: basically good programming practices, testing, auditing, safer compilers, etc. l Input Validation: failure in validating input and accepting extraneous input (hack code!!!). Produces similar results to buffer overflow and the countermeasure is the same: safe programming. l Shell access: after gaining access using a data driven attack the first objective is to open a shell window to enter commands. l Traditional shell access: telnet, rlogin, ssh (admins can close most). l Using X-Windows to run xterm in the remote (target) machine and display in the intruder machine, using its client/server features. l Reverse telnet and back channels: admins can remove X, then what? Run nc (netcat) in the intruder and run malicious code in the target creating a telnet connection from target to intruder. l Countermeasures: remove X (servers), chmod 750 telnet (Linux, root only), better yet only use ssh.

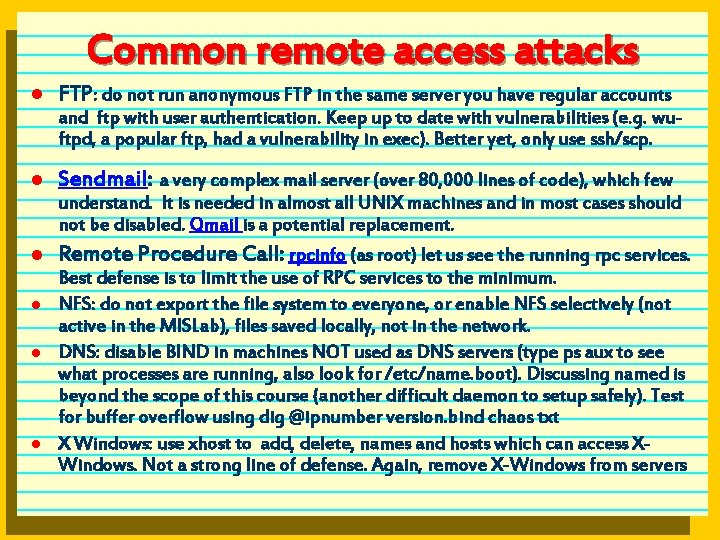
Common remote access attacks l FTP: do not run anonymous FTP in the same server you have regular accounts and ftp with user authentication. Keep up to date with vulnerabilities (e. g. wuftpd, a popular ftp, had a vulnerability in exec). Better yet, only use ssh/scp. l Sendmail: a very complex mail server (over 80, 000 lines of code), which few understand. It is needed in almost all UNIX machines and in most cases should not be disabled. Qmail is a potential replacement. l l Remote Procedure Call: rpcinfo (as root) let us see the running rpc services. Best defense is to limit the use of RPC services to the minimum. NFS: do not export the file system to everyone, or enable NFS selectively (not active in the MISLab), files saved locally, not in the network. DNS: disable BIND in machines NOT used as DNS servers (type ps aux to see what processes are running, also look for /etc/name. boot). Discussing named is beyond the scope of this course (another difficult daemon to setup safely). Test for buffer overflow using dig @ipnumber version. bind chaos txt X Windows: use xhost to add, delete, names and hosts which can access XWindows. Not a strong line of defense. Again, remove X-Windows from servers

Local access l Password cracking: We cannot decrypt a password, we use a dictionary, or other type of algorithm to generate passwords, encrypt them using the crypt function, DES, etc, and compare with hash in the passwd file. Crack 5 and John the Ripper are two of “the best of the breed. ” l l l Local buffer overflow: same problems and countermeasures. Symlinks: ln -s /this /that, when you cat this you see that. Signals in UNIX: you re-start, stop daemons sending signals: SIGXXX. Core dump: memory (core) dumps are snapshots of the memory when an error occurs. Delete it or it stays. ulimit set to 0 cancel core dumps. Shared libraries: replace a standard library file with a rogue one, granting privileges to the intruder, when used. Kernel problems: upgrades to the kernel may create security flaws, which will be found, patched, etc. Linux particularly vulnerable (growing). File and directory permissions: SUID files -- a necessary evil. Some applications need to run as root and be used by regular users (solution: SUID). The find command list these files, and there are many of them. World writable files are another problem.