Guided Fuzzing With AFL Agenda Lecture What is












- Slides: 22

Guided Fuzzing With AFL

Agenda • Lecture – What is “guided fuzzing” – All about AFL – Interesting AFL findings • Activity – Fuzzing a toy application with AFL – Fuzzing a real application with AFL

Prerequisite Knowledge • Basic C • Basic assembly • Linux command line navigation

Expected Outcomes • Understand. . . – The differences, and advantages of • Dumb fuzzing • Intelligent fuzzing • Guided fuzzing – How AFL improves on traditional fuzzing • Be able to. . . – Use AFL to fuzz open source software – Select and minimize good test files

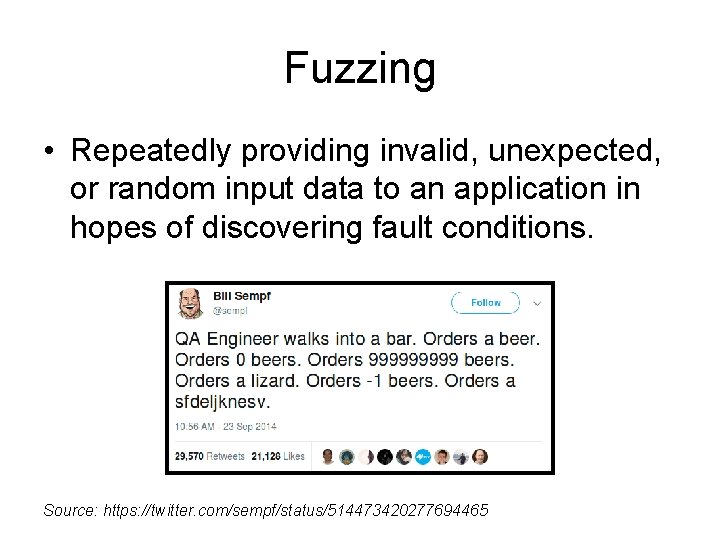
Fuzzing • Repeatedly providing invalid, unexpected, or random input data to an application in hopes of discovering fault conditions. Source: https: //twitter. com/sempf/status/514473420277694465

Traditional Fuzzing Strategies • “Dumb Fuzzing” – Randomly mutate data and watch for a crash • “Intelligent Fuzzing” – Provide the fuzzer some insight about the data structure and/or format so that it can target “interesting” elements with carefully crafted values

Code Coverage Problem • Consider the following code • Will a fuzzer find this? • Dumb fuzzing – Not a chance • Intelligent fuzzing – Highly unlikely – Maybe after 4. 2 b iterations

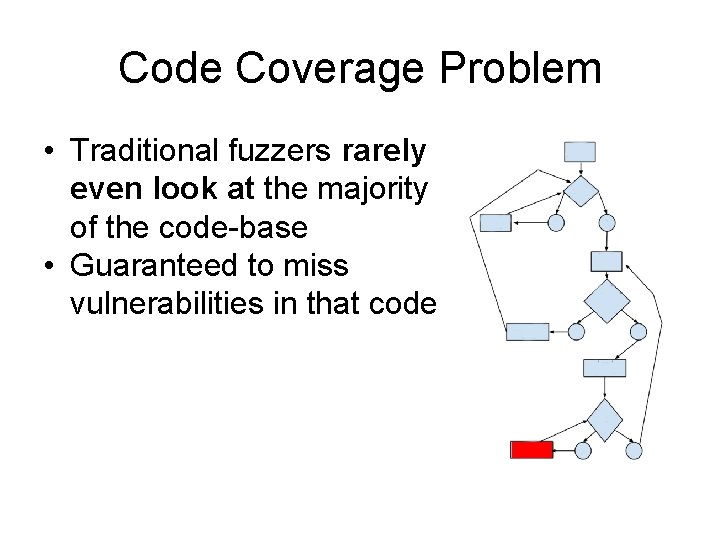
Code Coverage Problem • Traditional fuzzers rarely even look at the majority of the code-base • Guaranteed to miss vulnerabilities in that code

Guided Fuzzing • Attempts to solve the coverage problem – Observe and track flow of execution – Find mutations that access new code paths – Continue fuzzing with those samples – Rinse, repeat until nothing new found

AFL (American Fuzzy Lop) • One of the first popular guided fuzzers • Written by Michał Zalewski (lcamtuf) Source: http: //lcamtuf. coredump. cx/afl/

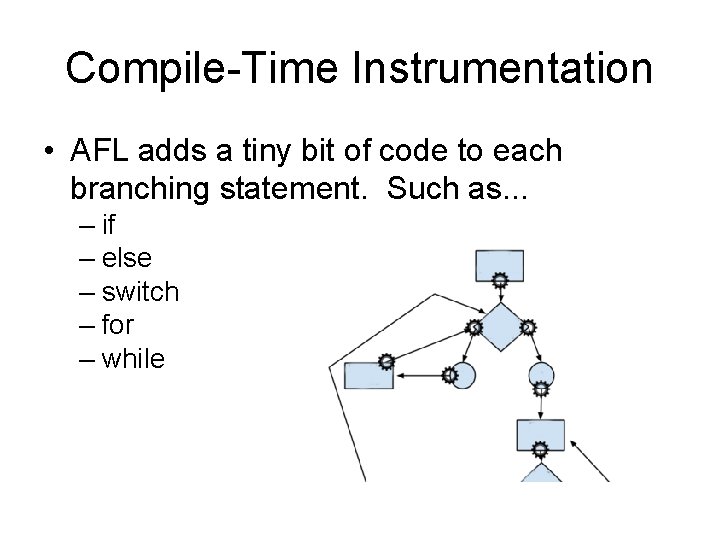
Compile-Time Instrumentation • AFL adds a tiny bit of code to each branching statement. Such as. . . – if – else – switch – for – while

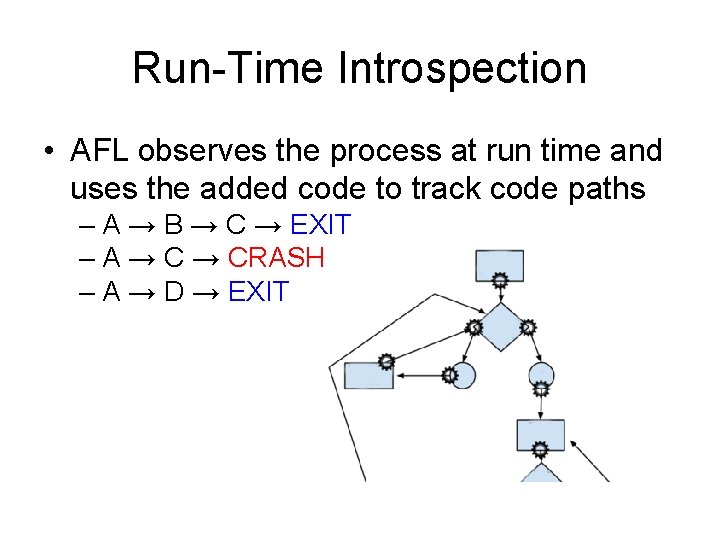
Run-Time Introspection • AFL observes the process at run time and uses the added code to track code paths – A → B → C → EXIT – A → CRASH – A → D → EXIT

AFL Features • • Excellent configuration by default Very easy to setup and use Compile-time instrumentation, FAST!!! Run-time instrumentation (blackbox) Parallelizable Data dictionary support Well documented and large user-base

AFL Additional Utilities • • Test case minimizer File format analyzer Crash explorer Custom “abusive” heap allocator

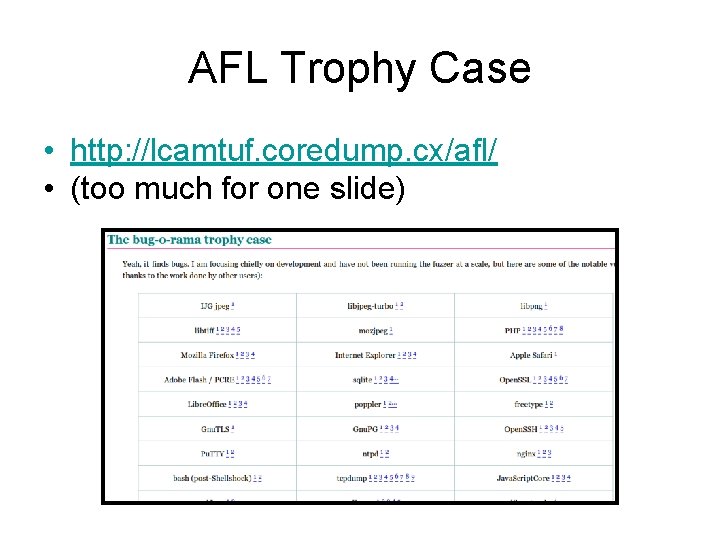
AFL Trophy Case • http: //lcamtuf. coredump. cx/afl/ • (too much for one slide)

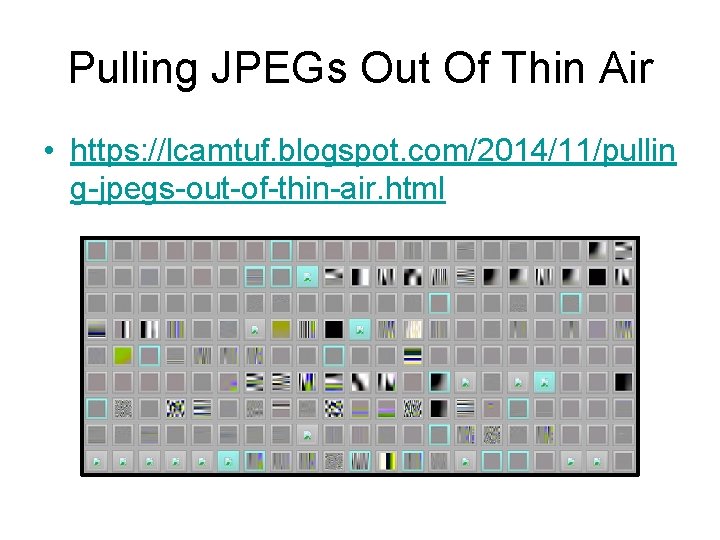
Pulling JPEGs Out Of Thin Air • https: //lcamtuf. blogspot. com/2014/11/pullin g-jpegs-out-of-thin-air. html

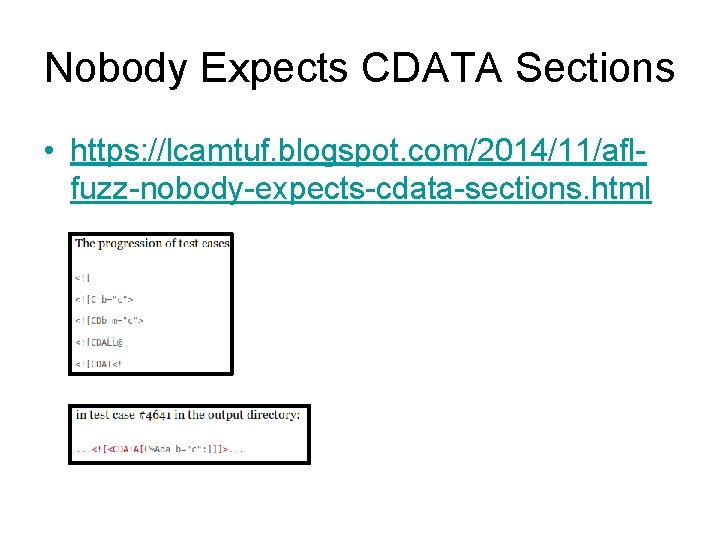
Nobody Expects CDATA Sections • https: //lcamtuf. blogspot. com/2014/11/aflfuzz-nobody-expects-cdata-sections. html

Choosing Good Samples • Minimize needless repetition • Maximize feature usage • GOOD – <html><a href=”b”>c</a></html> • BAD – <div>My first test case</div> – <div><div></div></div>

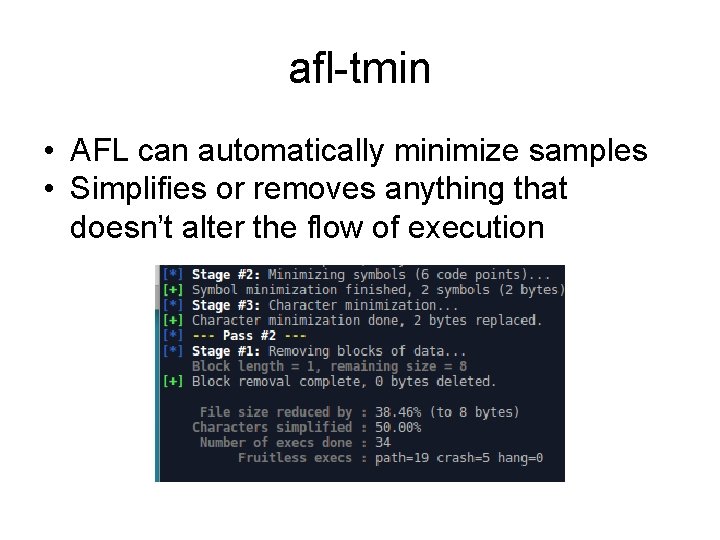
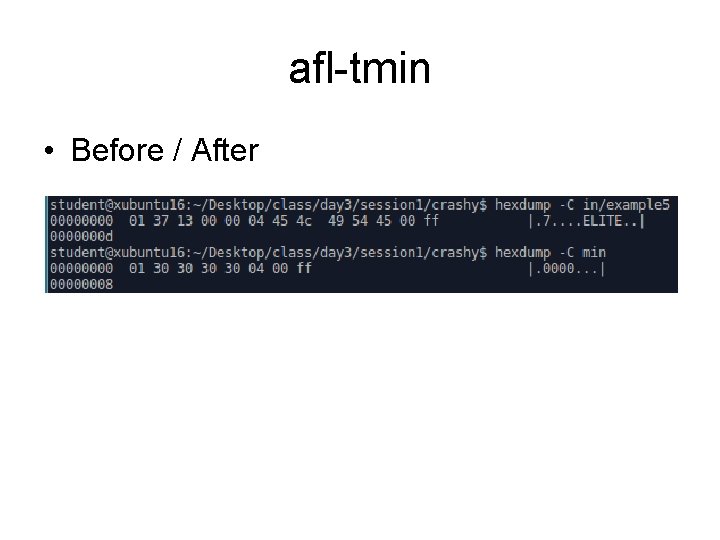
afl-tmin • AFL can automatically minimize samples • Simplifies or removes anything that doesn’t alter the flow of execution

afl-tmin • Before / After

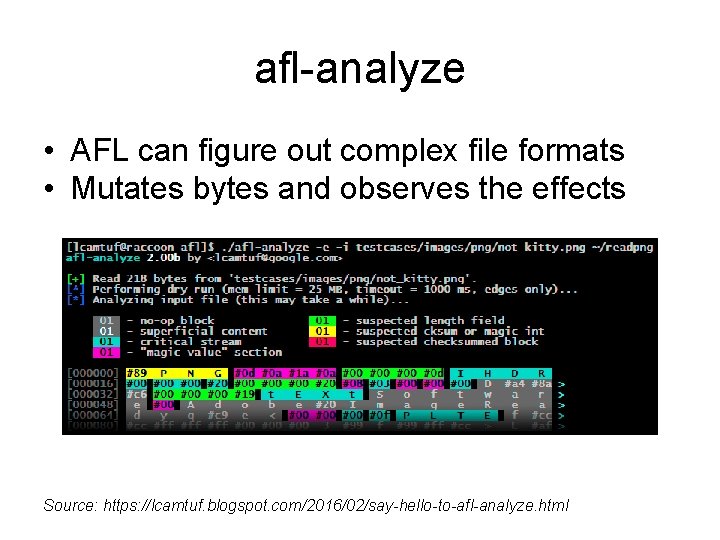
afl-analyze • AFL can figure out complex file formats • Mutates bytes and observes the effects Source: https: //lcamtuf. blogspot. com/2016/02/say-hello-to-afl-analyze. html

EOF • Questions?