Guide to Operating System Security Chapter 3 Security
































- Slides: 50

Guide to Operating System Security Chapter 3 Security Through Authentication and Encryption

Objectives l l Explain encryption methods and how they are used Describe authentication methods and how they are used Explain and configure IP Security Discuss attacks on encryption and authentication methods Guide to Operating System Security 2

Encryption l l l Uses a secret code to disguise data Makes data unintelligible to everyone except intended recipients Protects data from attackers using a sniffer Uses cryptography Typically involves a key and an algorithm Guide to Operating System Security 3

Encryption Methods (Continued) l l l Stream cipher and block cipher Secret key Public key Hashing Data encryption standard (DES) RSA encryption Guide to Operating System Security 4

Encryption Methods (Continued) l l Pluggable authentication modules (PAMs) Microsoft Point-to-Point Encryption (MPPE) Encrypting File System (EFS) Cryptographic File System (CFS) Guide to Operating System Security 5

Stream Cipher and Block Cipher l Stream cipher u l Every bit in a stream of data is encrypted Block cipher Encrypts groupings of data in blocks u Typically has specific block and key sizes u Guide to Operating System Security 6

Secret Key l l Keeps encryption key secret from public access, particularly over a network connection Uses symmetrical encryption (same key to encrypt and decrypt) Guide to Operating System Security 7

Public Key l l Uses public key and private key combination (asymmetric encryption) Public key can be communicated over an unsecured connection Guide to Operating System Security 8

Hashing l Uses one-way function to mix up message contents Scrambles message u Associates it with a unique digital signature u Enables it to be picked out of a table u l l Often used to create a digital signature Hashing algorithms work on only one side of a two-way communication Guide to Operating System Security 9

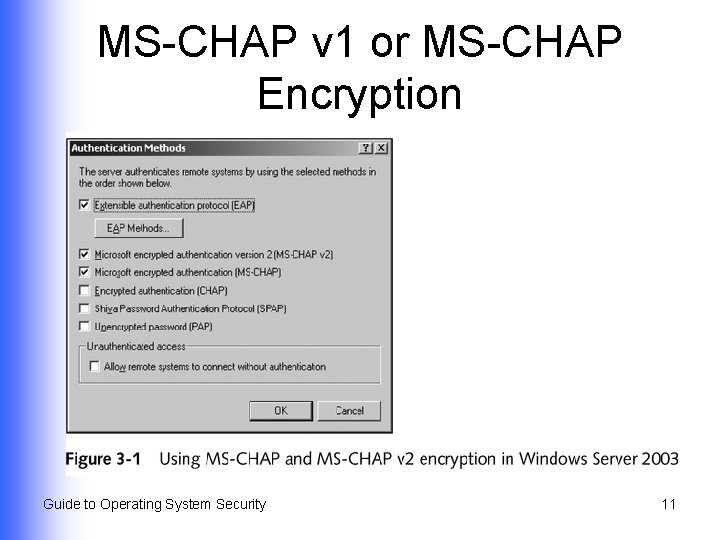
Typically Used Hashing Algorithms l l Message Digest 2 (MD 2) Message Digest 4 (MD 4) MS-CHAP v 1 u MS-CHAP in Windows Server 2003 u l l Message Digest 5 (MD 5) Secure Hash Algorithm 1 (SHA-1) Guide to Operating System Security 10

MS-CHAP v 1 or MS-CHAP Encryption Guide to Operating System Security 11

Data Encryption Standard l l l Developed by IBM; refined by the National Bureau of Standards Originally developed to use a 56 -bit encryption key New version: 3 DES (Triple DES) Hashes data three times u Uses a key of up to 168 bits in length u Guide to Operating System Security 12

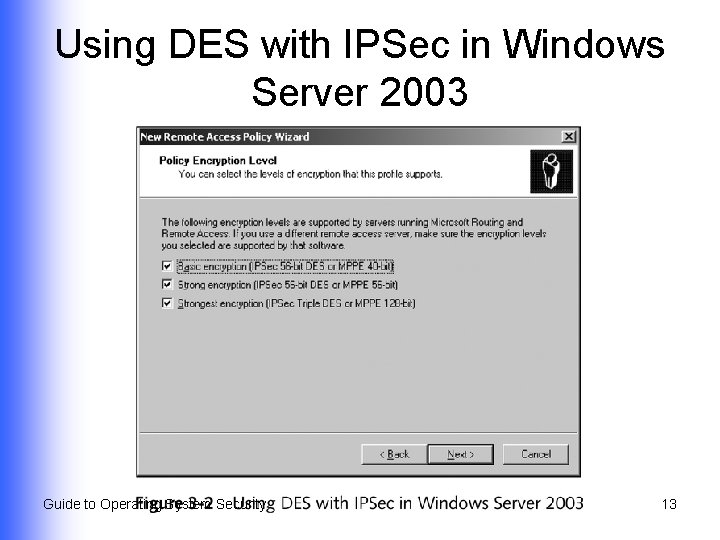
Using DES with IPSec in Windows Server 2003 Guide to Operating System Security 13

Advanced Encryption Standard l l l Adopted by U. S. government to replace DES and 3 DES Employs private-key block-cipher form of encryption Employs an algorithm called Rijndael Guide to Operating System Security 14

RSA Encryption l l Uses asymmetrical public and private keys along with an algorithm that relies on factoring large prime numbers The algorithm uses a trapdoor function to manipulate prime numbers More secure than DES and 3 DES Used in Internet Explorer and Netscape Navigator Guide to Operating System Security 15

Pluggable Authentication Modules l l Can be installed in UNIX or Linux OS without rewriting and recompiling existing code Enable use of encryption techniques other than DES for passwords and communications on a network Guide to Operating System Security 16

Microsoft Point-to-Point Encryption l l Used by Microsoft operating systems for remote communications over PPP or PPTP Uses RSA encryption Basic encryption (40 -bit key) u Strong encryption (56 -bit key) u Strongest encryption (128 -bit key) u Guide to Operating System Security 17

Encrypting File System l l Set by an attribute of Windows OSs that use NTFS Protects folder/file contents on hard disk u l l Enables user to encrypt contents of folder/file so it can only be accessed via private key code by user who encrypted it Employs DES for encryption Uses a registered recovery agent Guide to Operating System Security 18

How to Configure EFS l l As an advanced folder attribute By using cipher command in Command Prompt window Guide to Operating System Security 19

Configuring EFS as an Advanced Folder Attribute Guide to Operating System Security 20

Cipher Command-Line Parameters Guide to Operating System Security 21

Cryptographic File System l l File system add-on available as open source software for UNIX and Linux systems Enables encryption of disk file systems and NFS files Guide to Operating System Security 22

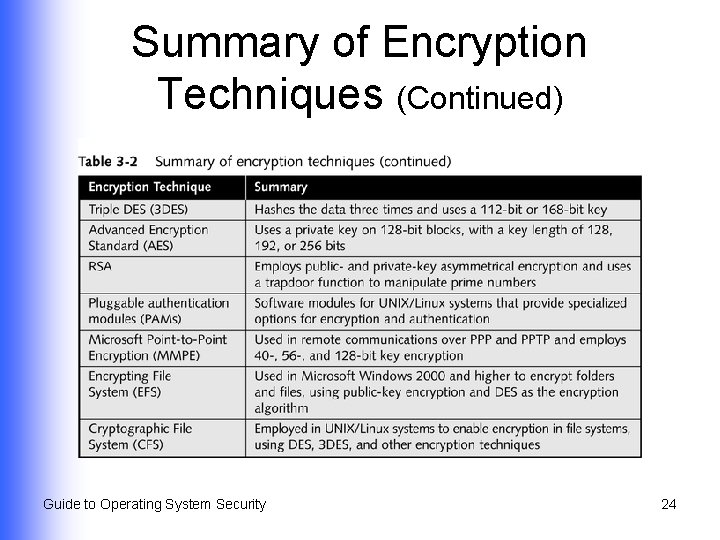
Summary of Encryption Techniques (Continued) Guide to Operating System Security continued… 23

Summary of Encryption Techniques (Continued) Guide to Operating System Security 24

Authentication l l Process of verifying that a user is authorized to access particular resources Typically associated with logon process Validates both user account name and password before giving access to resources Often uses encryption techniques to protect user names and passwords Guide to Operating System Security 25

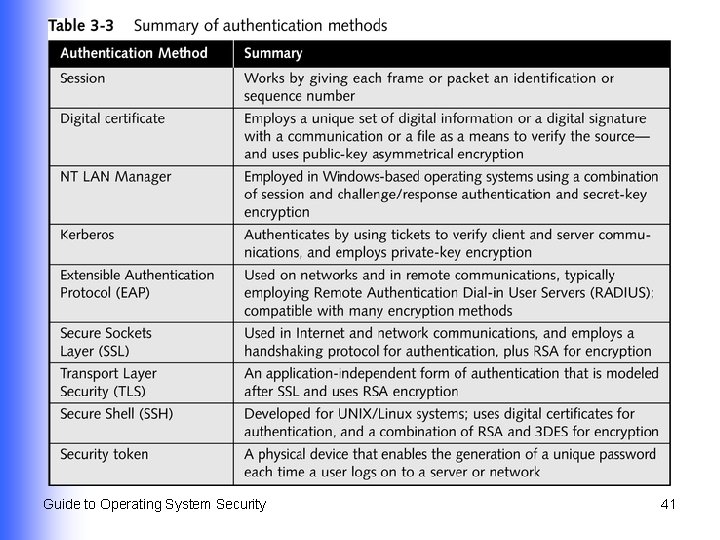
Authentication Methods (Continued) l l l Session authentication Digital certificates NT LAN Manager Kerberos Extensible Authentication Protocol (EAP) Secure Sockets Layer (SSL) Guide to Operating System Security 26

Authentication Methods (Continued) l l l Transport Layer Security (TLS) Secure Shell (SSH) Security token Guide to Operating System Security 27

Session Authentication l l Ensures packets can be read in correct order Provides a way to encrypt the sequence order to discourage attackers Guide to Operating System Security 28

Digital Certificate l l Set of unique identification information typically put at the end of the file or associated with a computer communication Shows that the source of the file or communication is legitimate Typically encrypted by a private key and decrypted by a public key Issued by a certificate authority Guide to Operating System Security 29

Digital Certificate Contents l l l l Version Certificate serial number Signature algorithm identifier Name of issuer Validity period Subject name Subject public key information Guide to Operating System Security 30

NT LAN Manager l l Form of session authentication and challenge/response authentication compatible with all Microsoft Windows operating systems Challenge/response authentication Hashes an account’s password u Uses a secret key u Guide to Operating System Security 31

Kerberos l Employs private-key security and use of tickets that are exchanged between the client who requests logon and network services access and the server, application, or directory service that grants access Guide to Operating System Security 32

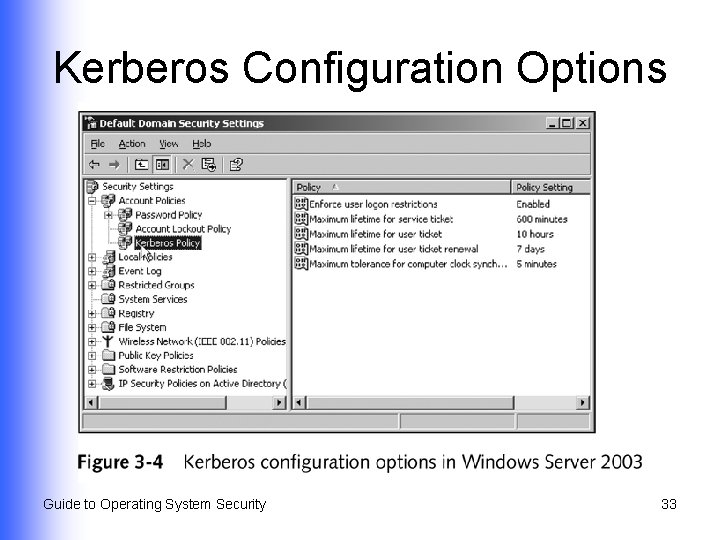
Kerberos Configuration Options Guide to Operating System Security 33

Extensible Authentication Protocol l Multipurpose authentication method used on networks and in remote communications Can employ many encryption methods (DES, 3 DES, public key encryption, smart cards, and certificates) Typically provides an authentication communication between a computer and a server used to authenticate computer’s access Guide to Operating System Security 34

Secure Sockets Layer l l Service-independent; broad uses for e-commerce, HTTPS, FTP, SMTP, and NNTP Developed by Netscape Uses RSA public-key encryption Most commonly used form of security for communications and transactions over the Web Guide to Operating System Security 35

Transport Layer Security l l Modeled after SSL Uses private-key symmetric data encryption and TLS Handshake Protocol Guide to Operating System Security 36

Secure Shell l Developed for UNIX/Linux systems to provide authentication security for TCP/IP applications, including FTP and Telnet Guide to Operating System Security 37

Using Secure Shell Guide to Operating System Security 38

Security Token l l Physical device, often resembling a credit card or keyfob, used for authentication Communicates with an authentication server to generate the password, using encryption for exchange of password-generating information Guide to Operating System Security 39

Advantages of Security Token l l User does not have to memorize password Value of password only lasts as long as the communications session; new password is created next time the security token is used Guide to Operating System Security 40

Guide to Operating System Security 41

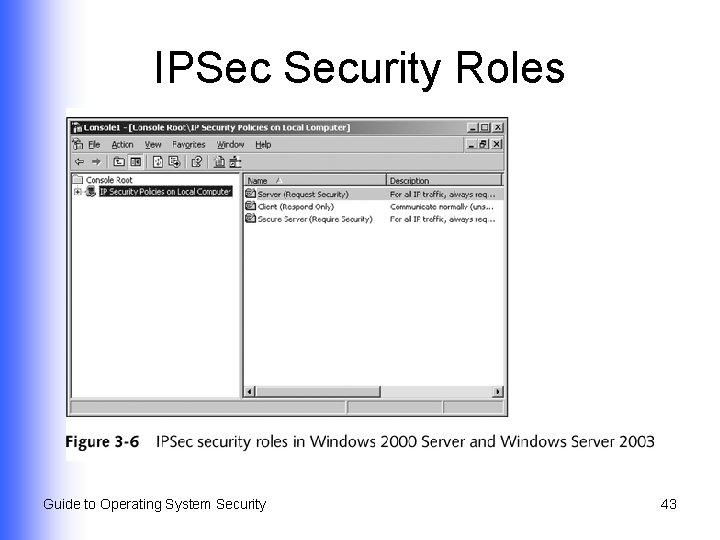
IP Security (IPSec) l l l Set of IP-based secure communications and encryption standards developed by the IETF Protect network communications through IP Elements that enable security measures Authentication header u Encapsulating Security Payload (ESP) u Guide to Operating System Security 42

IPSec Security Roles Guide to Operating System Security 43

Authentication Header (AH) l l Ensures integrity of a data transmission Ensures authentication of a packet by enabling verification of its source Guide to Operating System Security 44

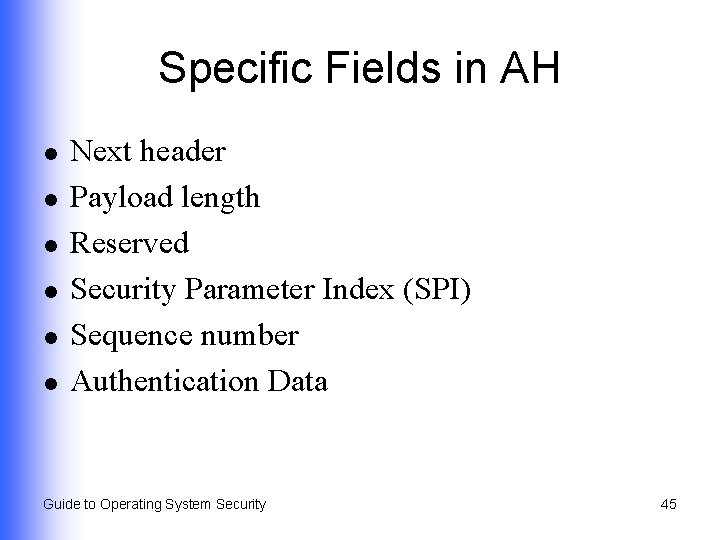
Specific Fields in AH l l l Next header Payload length Reserved Security Parameter Index (SPI) Sequence number Authentication Data Guide to Operating System Security 45

Encapsulating Security Payload (ESP) l l l Encrypts packet-based data Authenticates data Generally ensures security and confidentiality of network layer information and data within packet Guide to Operating System Security 46

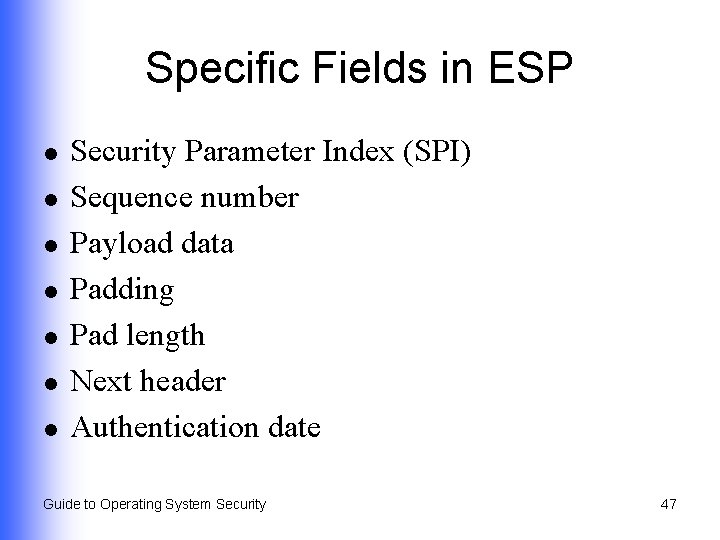
Specific Fields in ESP l l l l Security Parameter Index (SPI) Sequence number Payload data Padding Pad length Next header Authentication date Guide to Operating System Security 47

Attacks on Encryption and Authentication Guide to Operating System Security 48

Guidelines for Resisting Attacks l l l Use strong passwords Use strongest forms of authentication and encryption permitted by OS Use longest encryption keys possible Inventory encryption and authentication methods used by OS; close any holes Have administrators use personal accounts with administrative privileges (rather than use administrative account directly) Guide to Operating System Security 49

Summary l l l Encryption methods and how operating systems use them How systems authenticate one another How to configure Kerberos authentication logon security How to use IP security to keep your TCP/IP network secure Typical methods attackers use to defeat encryption and authentication Guide to Operating System Security 50