GS Chapter 6 Using Java Cryptography for Authentication




![Message Digests in Java q byte[] digest () Completes the hash computation by performing Message Digests in Java q byte[] digest () Completes the hash computation by performing](https://slidetodoc.com/presentation_image_h2/0caf3e5be1dfdf6a0e58d17c71786aed/image-6.jpg)









- Slides: 24

GS: Chapter 6 Using Java Cryptography for Authentication csci 5233 Computer Security 1

Topics q Message digest (MD) q Password authentication for MD q Message Authentication Code (MAC) q Digital signatures & Identity authentication q Digital certificates, X. 509, certificate chaining q Keystores q Public Key Infrastructure (PKI) csci 5233 Computer Security 2

Dependencies • Review example programs and discussions in Chapter 3. csci 5233 Computer Security 3

Message Digests q message digest: a fingerprint of a piece of data q goal: data integrity (stored data, transmitted data, file copying, …) q message hashing algorithm digest q Java class: Message. Digest q Methods: get. Instance ( ), update ( ), digest ( ) q Algorithms: MD 5, SHA-1 csci 5233 Computer Security 4

Message Digests in Java q java. security Class Message. Digest Message digests are secure one-way hash functions that take arbitrarysized data and output a fixed-length hash value. A Message. Digest object starts out initialized. The data is processed through it using the update methods. At any point reset can be called to reset the digest. Once all the data to be updated has been updated, one of the digest methods should be called to complete the hash computation. After digest has been called, the Message. Digest object is reset to its initialized state. csci 5233 Computer Security 5
![Message Digests in Java q byte digest Completes the hash computation by performing Message Digests in Java q byte[] digest () Completes the hash computation by performing](https://slidetodoc.com/presentation_image_h2/0caf3e5be1dfdf6a0e58d17c71786aed/image-6.jpg)
Message Digests in Java q byte[] digest () Completes the hash computation by performing final operations such as padding. q byte[] digest (byte[] input) Performs a final update on the digest using the specified array of bytes, then completes the digest computation. q int digest (byte[] buf, int offset, int len) Completes the hash computation by performing final operations such as padding. csci 5233 Computer Security 6

Message Digests in Java q Computing a message digest on a file: Digest. File. java q Size of the output digest SHA-1: 20 bytes MD 5: 16 bytes q Exercise: Change the content of the input data file and compare the output digests. q Project: Write a program that gets a file, the MD algorithm, and the generated digest as the input, and then determine if the file has been corrupted. csci 5233 Computer Security 7

Message Digests in Java q Alternative classes for computing a message digest on a file: Digest. Input. Stream and Digest. Output. Stream q Digest. Input. Stream A transparent stream that updates the associated message digest using the bits going through the stream. To complete the message digest computation, call one of the digest methods on the associated message digest after your calls to one of this digest input stream's read methods. q Sample program: Digest. Stream. Example. java csci 5233 Computer Security 8

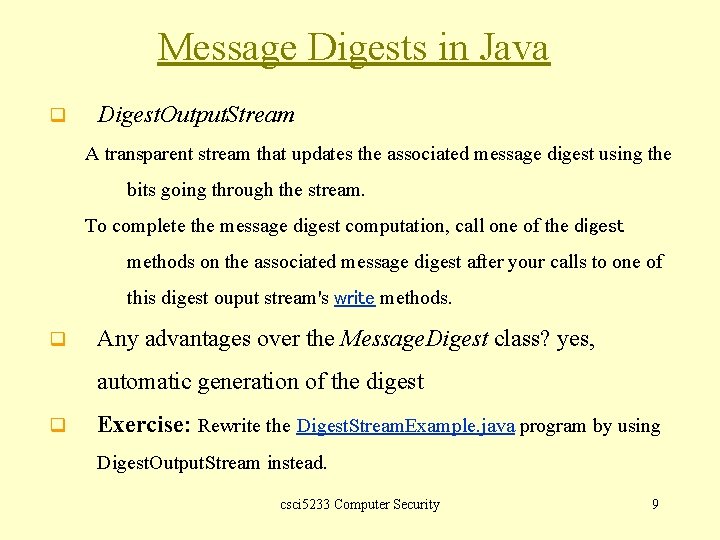
Message Digests in Java q Digest. Output. Stream A transparent stream that updates the associated message digest using the bits going through the stream. To complete the message digest computation, call one of the digest methods on the associated message digest after your calls to one of this digest ouput stream's write methods. q Any advantages over the Message. Digest class? yes, automatic generation of the digest q Exercise: Rewrite the Digest. Stream. Example. java program by using Digest. Output. Stream instead. csci 5233 Computer Security 9

Message Digests in Java q Another application of MD: Using message digests to store and authenticate passwords q Sample program: Password. Authenticator. java q Usages: -c password Create a password. -a password Authenticate the password. csci 5233 Computer Security 10

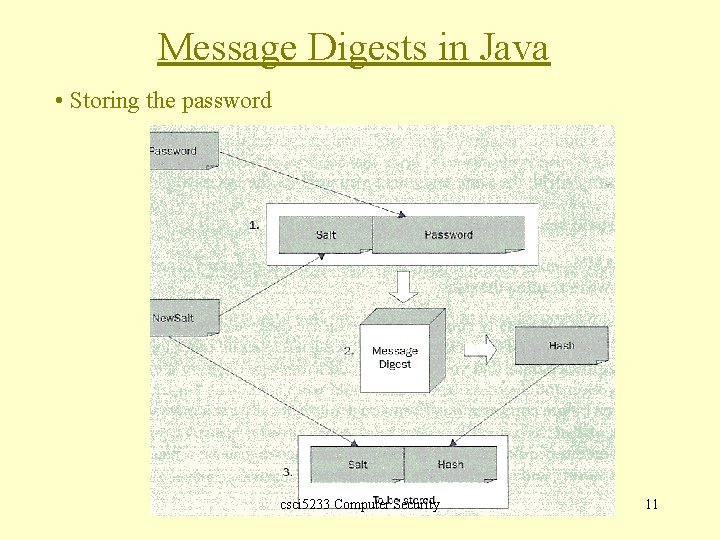
Message Digests in Java • Storing the password csci 5233 Computer Security 11

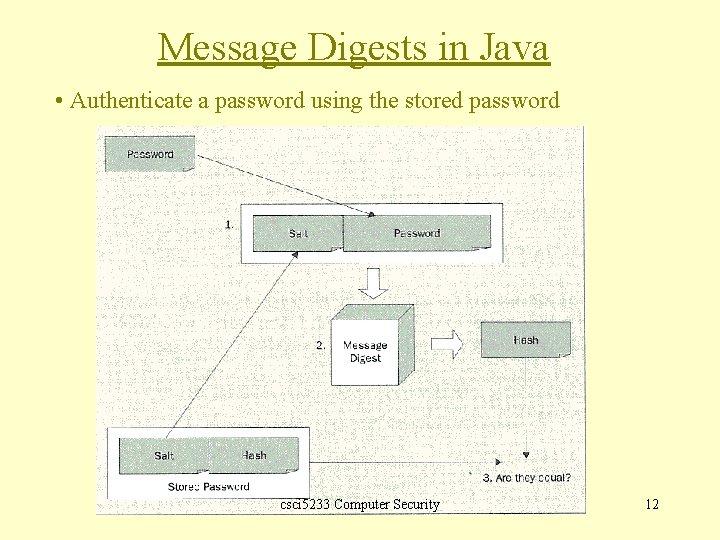
Message Digests in Java • Authenticate a password using the stored password csci 5233 Computer Security 12

Message Authentication Codes q A keyed message digest q Often used for authenticating data sent over an insecure network or stored in an insecure medium To prevent man-in-the-middle attack against keyless message digest q message + key MA algorithm MAC q Verification: The same key is used to produce MAC’, which is compared to MAC to determine if the message has been tampered. csci 5233 Computer Security 13

Using MAC in Java q HMAC (Hashed MAC) q HMAC functions supported by JCE: Hmac. MD 5 and Hmac. SHA 1 q javax. crypto Class Mac Methods: get. Instance( ), init( ), update( ), do. Final( ) q Sample program: MACExample. java q Drawback of MAC: The need to have a shared secret key Solution: Digital signatures csci 5233 Computer Security 14

Digital Signatures q Associates an individual with a particular piece of data, like a signed contract or an e-mail q is essentially a message digest signed by someone’s private key achieves both data integrity and source integrity (i. e. , authentication) q Review diagrams on p. 48, as well as on pp. 135 -136 csci 5233 Computer Security 15

Digital Signature Algorithm (DSA) q works similarly to RSA signing, but lack an encryption capability q c. f. , RSA DSA is faster at generating signatures; RSA is faster at validating signatures DSA was supported in older Java (v 1. 2); RSA is supported by JDK v 1. 3 and higher RSA is generally recommended if you have a choice. csci 5233 Computer Security 16

DSA and RSA q The signature algorithm can be, among others, DSA and SHA-1. The DSA algorithm using the SHA-1 message digest algorithm can be specified as SHA 1 with. DSA. q In the case of RSA, there are multiple choices for the message digest algorithm, so the signing algorithm could be specified as, for example, MD 2 with. RSA, MD 5 with. RSA, or SHA 1 with. RSA. q The algorithm name must be specified, as there is no default. csci 5233 Computer Security 17

Digital Signatures in Java q java. security Class Signature q refers to the object used to create and verify DS, but not the signatures, which are manipulated as byte arrays q Methods: get. Instance( ), init. Sign( ), init. Verify( ), update( ), sign( ), and verify( ) csci 5233 Computer Security 18

Digital Signatures in Java q There are three phases to the use of a Signature object: 1. Initialization, with either q a public key, which initializes the signature for verification (see init. Verify( ) ), or q a private key, which initializes the signature for signing (see init. Sign(Private. Key) and init. Sign(Private. Key, Secure. Random)). 2. Updating q Depending on the type of initialization, this will update the bytes to be signed or verified. See the update( ) methods. 3. Signing or Verifying a signature on all updated bytes. See the sign( ) methods and the verify( ) method. csci 5233 Computer Security 19

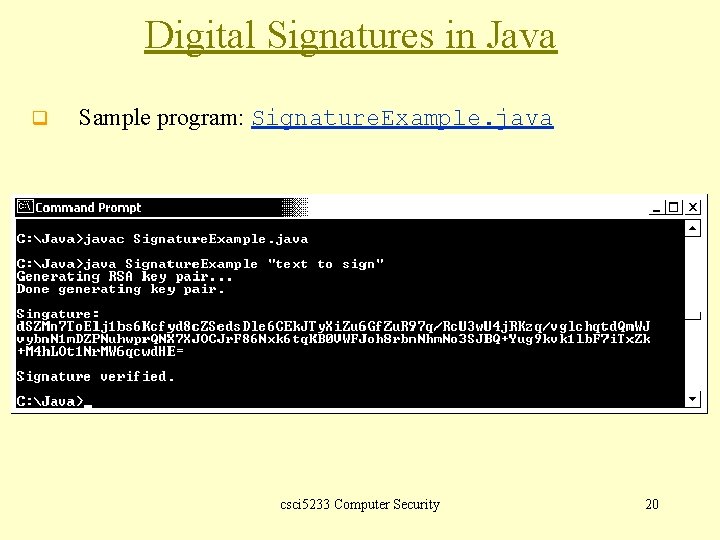
Digital Signatures in Java q Sample program: Signature. Example. java csci 5233 Computer Security 20

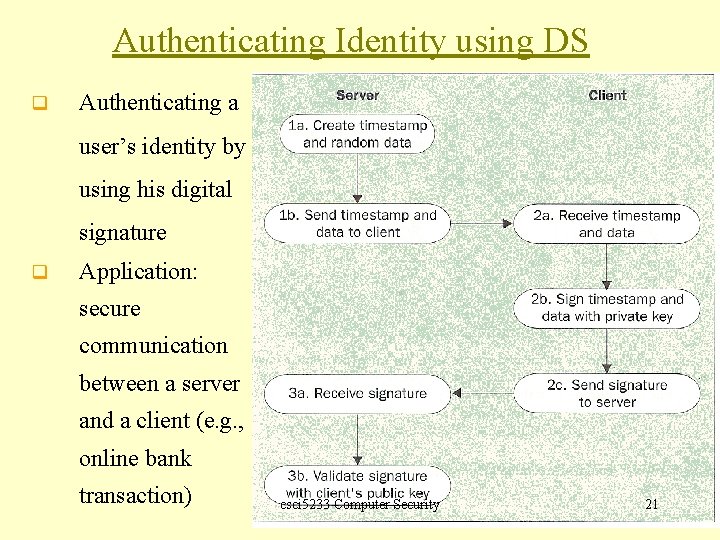
Authenticating Identity using DS q Authenticating a user’s identity by using his digital signature q Application: secure communication between a server and a client (e. g. , online bank transaction) csci 5233 Computer Security 21

Authenticating Identity using DS q Sample programs: Signature. Authentication. Client. java Signature. Authentication. Server. java q Advantage of this “nonce” approach: It allows the server to validate the client’s signature at the beginning of a communication session. q See pages 487 -488 (Appendix A) for further discussion of using a nonce. q See http: //en. wikipedia. org/wiki/Nonce for some discussion about the word ‘nonce’ (a ‘number used once’). q Drawback? requires secure communication, otherwise may suffer man-in-themiddle attack (e. g. , The session id may be stolen, and used by the hacker to launch a ‘rogue server’ or ‘session hijacking’ attack. ) q Solution? Encrypted communication (e. g. , tunneling) csci 5233 Computer Security 22

Authenticating Identity using DS q c. f. , Server-initiated authentication The server encrypts some random data with the client’s public key and sends the result to the client. If the client can decrypt the ciphertext, his identity is authenticated. Trade-offs? q c. f. , The “full-blown” DS approach, in which the client sign every message. Trade-offs? csci 5233 Computer Security 23

Next q Digital certificates, X. 509, certificate chaining q Keystores q Public Key Infrastructure (PKI) csci 5233 Computer Security 24