Grid Security for Site Authorization in EDG VOMS




- Slides: 18

Grid Security for Site Authorization in EDG VOMS, Java Security and LCMAPS David Groep, NIKHEF davidg@nikhef. nl EDG Security Coordination A. Frohner – CERN D. Kouril - CESNET F. Bonnassieux - CNRS R. Alfieri, R. Cecchini, V. Ciaschini, L. dell'Agnello, A. Gianoli , F. Spataro - INFN O. Mulmo – KDC D. L. Groep, M. Steenbakkers, W. Som de Cerff, O. Koeroo, G. Venekamp – NIKHEF L. Cornwall, D. Kelsey, J. Jensen – RAL A. Mc. Nab – University of Manchester P. Broadfoot, G. Lowe – University of Oxford http: //hep-project-grid-scg. web. cern. ch/ Data. Grid is a project funded by the European Union HEPi. X Conference Amsterdam 2003

Talk Outline u Introduction u Authorization requirements u VO Membership Service u Java Security for Hosted Environments u Native Mechanisms (LCAS, LCMAPS) u Conclusions HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 2

Authentication – only the first step u EDG security infrastructure based on X. 509 certificates (PKI) u Authentication n Needs “trusted third parties”: 16 national certification authorities n Policies and procedures mutual thrust n Users identified with “identity” certificates signed by a national CA See also next talk by Dave Kelsey… u Authorization n n Several entities involved s Resource Providers (e. g. computer centres, storage providers, NRENs) s Virtual Organizations (e. g. LHC experiments collaborations) Cannot decide Authorization for grid users only on local site basis HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 3

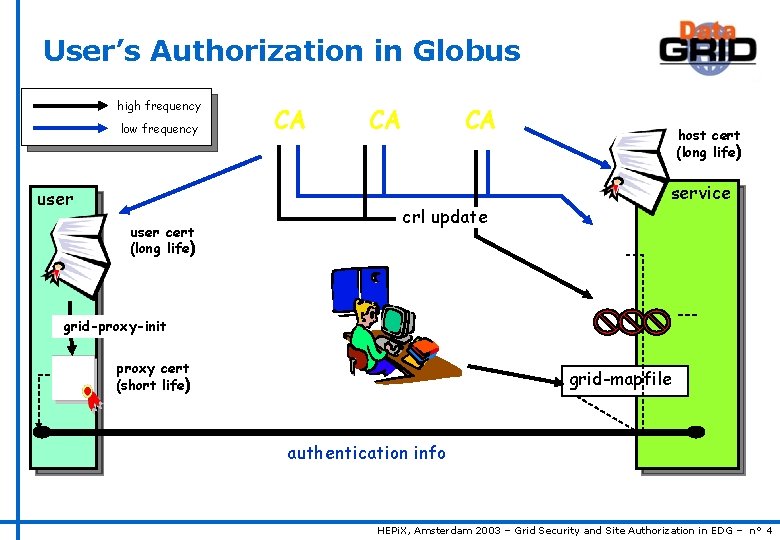
User’s Authorization in Globus high frequency low frequency user cert (long life) CA CA CA crl update host cert (long life) service grid-proxy-init proxy cert (short life) grid-mapfile authentication info HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 4

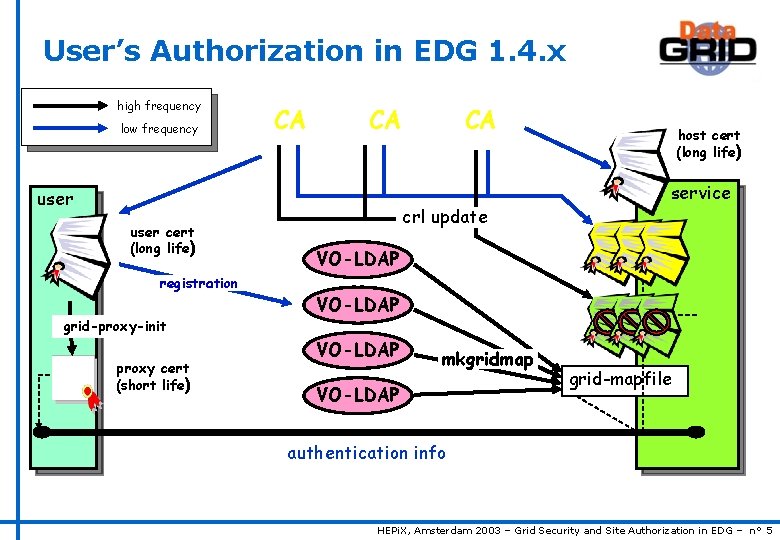
User’s Authorization in EDG 1. 4. x high frequency low frequency CA CA user cert (long life) registration grid-proxy-init proxy cert (short life) CA crl update host cert (long life) service VO-LDAP mkgridmap VO-LDAP grid-mapfile authentication info HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 5

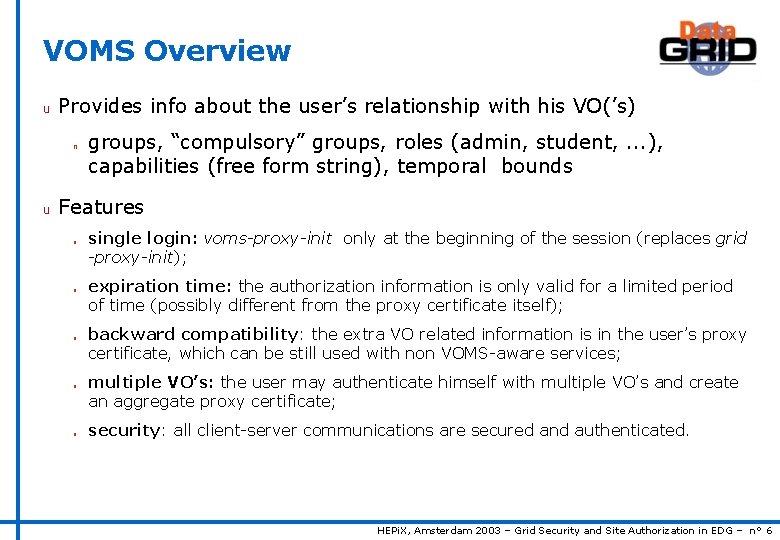
VOMS Overview u Provides info about the user’s relationship with his VO(’s) n u groups, “compulsory” groups, roles (admin, student, . . . ), capabilities (free form string), temporal bounds Features n n n single login: voms-proxy-init only at the beginning of the session (replaces grid -proxy-init); expiration time: the authorization information is only valid for a limited period of time (possibly different from the proxy certificate itself); backward compatibility: the extra VO related information is in the user’s proxy certificate, which can be still used with non VOMS-aware services; multiple VO’s: the user may authenticate himself with multiple VO’s and create an aggregate proxy certificate; security: all client-server communications are secured and authenticated. HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 6

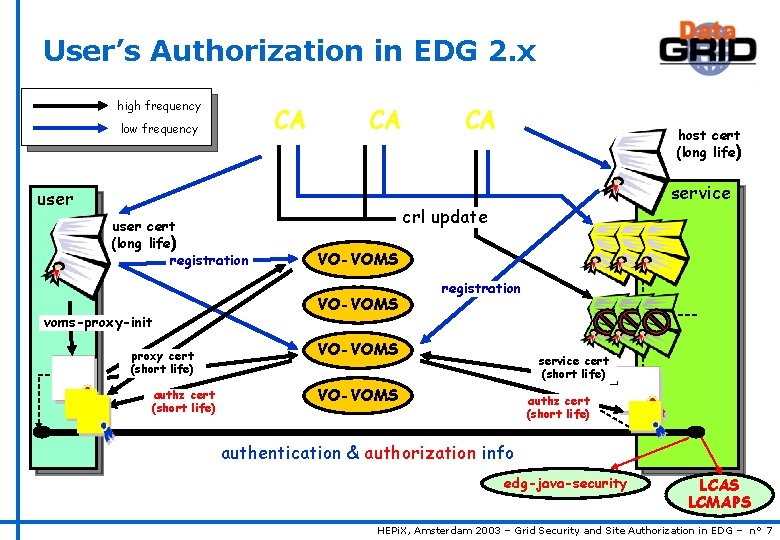
User’s Authorization in EDG 2. x high frequency CA low frequency CA user cert (long life) registration voms-proxy-init proxy cert (short life) authz cert (short life) CA host cert (long life) service crl update VO-VOMS registration VO-VOMS service cert (short life) VO-VOMS authz cert (short life) authentication & authorization info edg-java-security LCAS LCMAPS HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 7

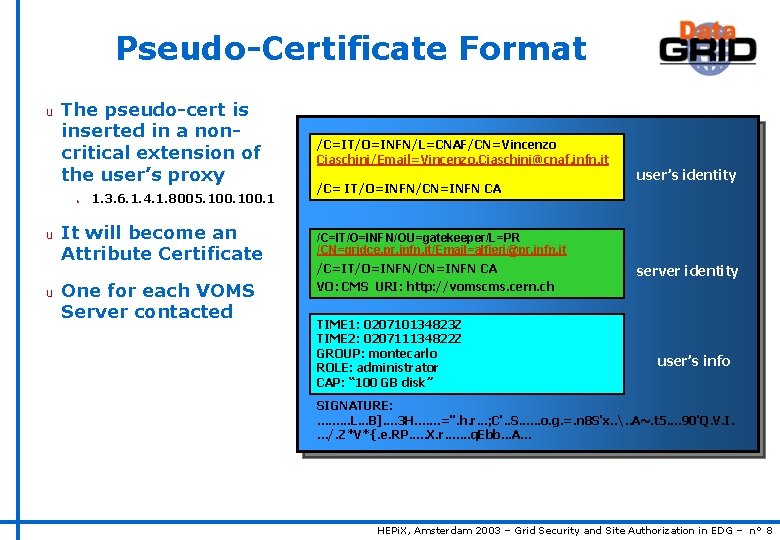
Pseudo-Certificate Format u The pseudo-cert is inserted in a noncritical extension of the user’s proxy n u u 1. 3. 6. 1. 4. 1. 8005. 100. 1 It will become an Attribute Certificate One for each VOMS Server contacted /C=IT/O=INFN/L=CNAF/CN=Vincenzo Ciaschini/Email=Vincenzo. Ciaschini@cnaf. infn. it /C= IT/O=INFN/CN=INFN CA user’s identity /C=IT/O=INFN/OU=gatekeeper/L=PR /CN=gridce. pr. infn. it/Email=alfieri@pr. infn. it /C=IT/O=INFN/CN=INFN CA server identity VO: CMS URI: http: //vomscms. cern. ch TIME 1: 020710134823 Z TIME 2: 020711134822 Z GROUP: montecarlo ROLE: administrator CAP: “ 100 GB disk” user’s info SIGNATURE: . . L. . . B]. . 3 H. . . . =". h. r. . . ; C'. . S. . . o. g. =. n 8 S'x. . . . A~. t 5. . 90'Q. V. I. . /. Z*V*{. e. RP. . . X. r. . . . q. Ebb. . . A. . . HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 8

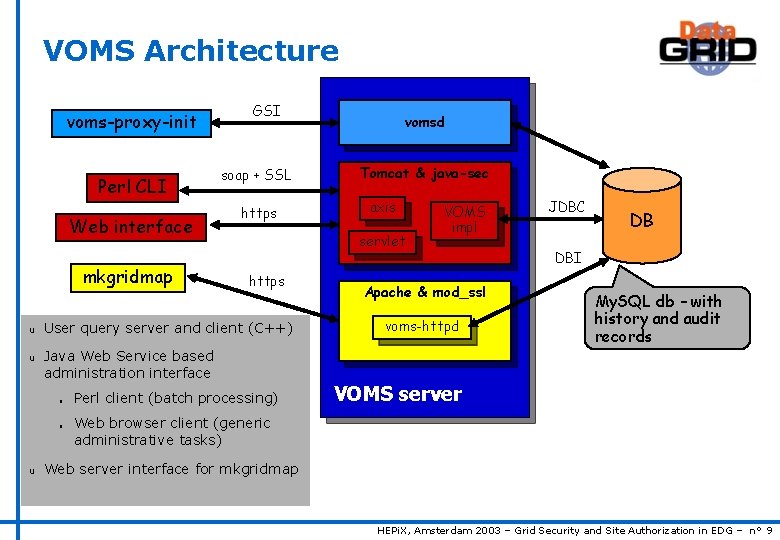
VOMS Architecture voms-proxy-init Perl CLI Web interface mkgridmap u u soap + SSL https vomsd Tomcat & java-sec axis servlet https User query server and client (C++) VOMS impl Apache & mod_ssl voms-httpd JDBC DB DBI My. SQL db – with history and audit records Java Web Service based administration interface n n u GSI Perl client (batch processing) VOMS server Web browser client (generic administrative tasks) Web server interface for mkgridmap HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 9

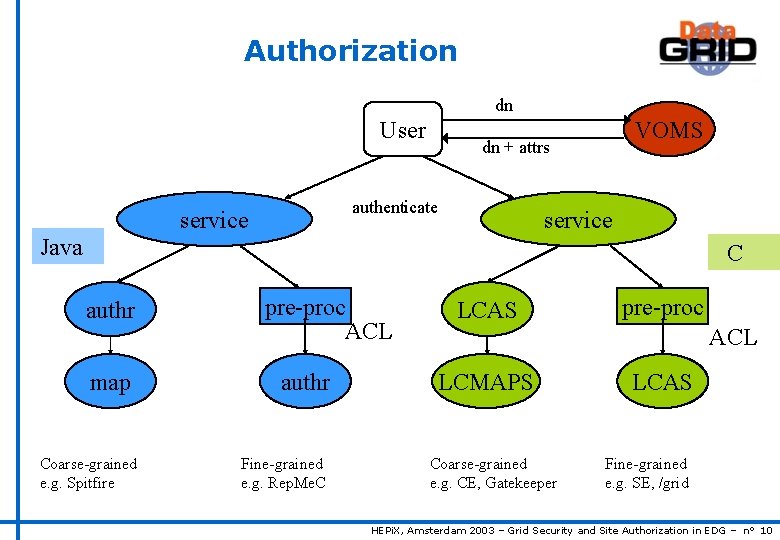
Authorization dn User dn + attrs authenticate service VOMS service Java C authr map Coarse-grained e. g. Spitfire pre-proc ACL authr Fine-grained e. g. Rep. Me. C LCAS pre-proc ACL LCMAPS Coarse-grained e. g. CE, Gatekeeper LCAS Fine-grained e. g. SE, /grid HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 10

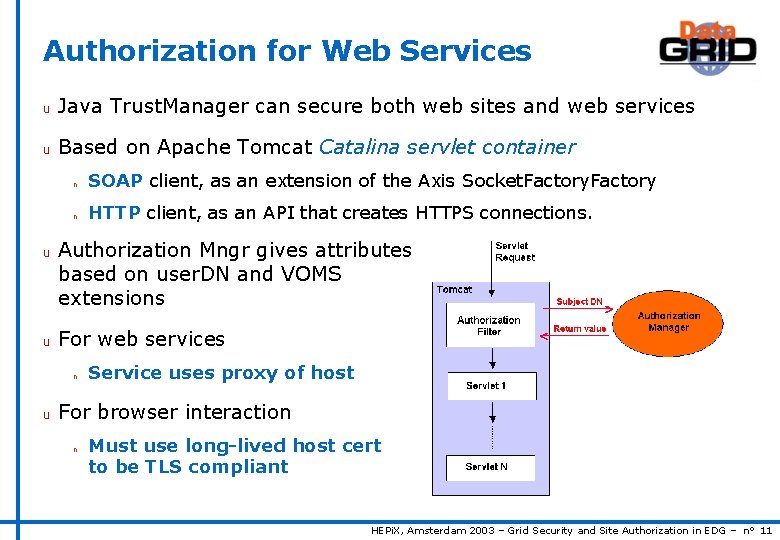
Authorization for Web Services u Java Trust. Manager can secure both web sites and web services u Based on Apache Tomcat Catalina servlet container u u n SOAP client, as an extension of the Axis Socket. Factory n HTTP client, as an API that creates HTTPS connections. Authorization Mngr gives attributes based on user. DN and VOMS extensions For web services n u Service uses proxy of host For browser interaction n Must use long-lived host cert to be TLS compliant HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 11

Services secured by EDG-Java-Sec u u u Spitfire uniform access to SQL database services (My. SQL, DB/2, Oracle) Replica Location Service, Rep. Me. C, Giggle – metadata and replica information services VOMS server R-GMA Relational Grid Monitoring Architecture – Information System Basis for new OGSA/Web. Services components HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 12

Authorization for Native Environments u All systems for running Grid jobs and storing files are UNIX based u Need for interface between Grid rights and local rights u Two-phase process u n Authorization of users: LCAS n Acquiring and enforcing local (UNIX-style) credentials: LCMAPS Why the split? n Authorization decisions may be applied for more than single resources n Credential mapping may be time-consuming and “heavy” n Internal service security credential mapping needs root privileges, authorization can do without HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 13

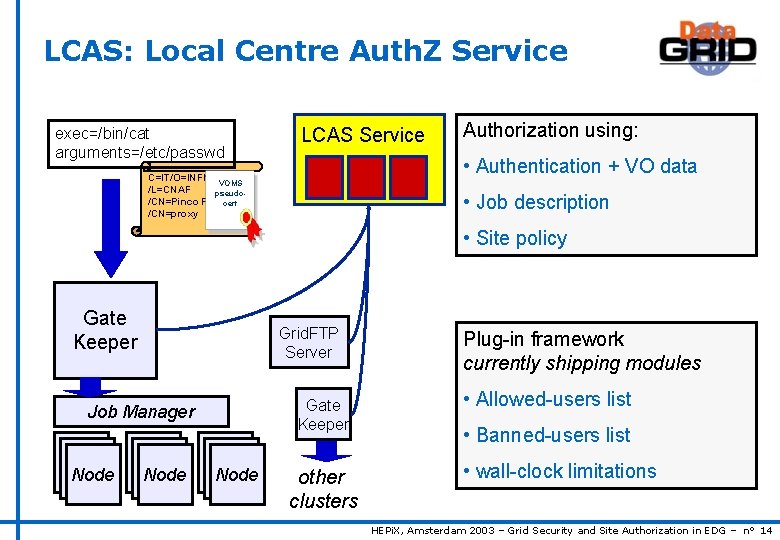
LCAS: Local Centre Auth. Z Service exec=/bin/cat arguments=/etc/passwd LCAS Service Authorization using: • Authentication + VO data C=IT/O=INFN VOMS /L=CNAF pseudo/CN=Pinco Pallacert /CN=proxy • Job description • Site policy Gate Keeper Job Manager Node Node Node Grid. FTP Server Gate Keeper other clusters Plug-in framework currently shipping modules • Allowed-users list • Banned-users list • wall-clock limitations HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 14

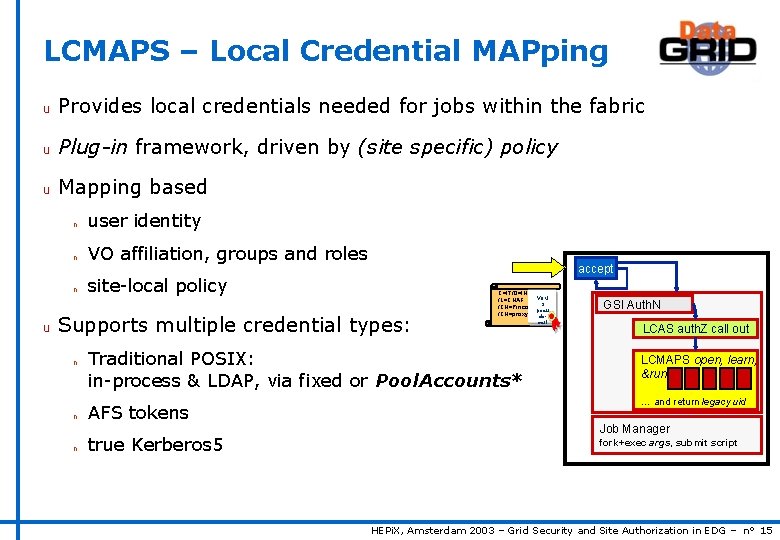
LCMAPS – Local Credential MAPping u Provides local credentials needed for jobs within the fabric u Plug-in framework, driven by (site specific) policy u Mapping based n user identity n VO affiliation, groups and roles n u accept site-local policy Supports multiple credential types: n n n C=IT/O=INFN VOM /L=CNAF S /CN=Pinco Palla pseu /CN=proxy do- Traditional POSIX: in-process & LDAP, via fixed or Pool. Accounts* AFS tokens true Kerberos 5 cert GSI Auth. N LCAS auth. Z call out LCMAPS open, learn, &run: … and return legacy uid Job Manager fork+exec args, submit script HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 15

LCMAPS – new functionality u Local UNIX groups based on VOMS group membership and roles u More than one VO and group/role per grid user u No pre-allocation of pool accounts to specific groups u New mechanisms: u n groups-on-demand n support for central user directories (primarily LDAP) Why do we continue to need LCAS? n Centralized site decisions on authorized users for multiple fabrics n Coordinated access control across multiple CEs and SEs n (and save on ‘expensive’ account allocation mechanisms in LCMAPS) HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 16

Conclusions u EDG provides extensive Grid authorization infrastructure today n LCAS* and Java-security already deployed n VOMS and LCMAPS ready for deployment (confirmed for June ’ 03) n Updates for various services in October ’ 03 User Side u Support for large, fast-changing user community u Roles and groups within the experiment VOs u Multiple affiliations and roles per user Resource Side u Minimal effort on resource provider side u More smooth integration in Grid computing at large u Retains tracability and auditability at all levels HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 17

More Information EDG Security Coordination Group Web site http: //hep-project-grid-scg. web. cern. ch/ VOMS Web site http: //grid-auth. infn. it/ CVS site http: //cvs. infn. it/cgi-bin/cvsweb. cgi/Auth/ Developers’ mailing list sec-grid@infn. it Pool. Accounts Web site http: //www. gridpp. ac. uk/authz/gridmapdir/ LCAS-LCMAPS Web site http: //www. dutchgrid. nl/Data. Grid/wp 4/ CVS site http: //datagrid. in 2 p 3. fr/cgi-bin/cvsweb. cgi/fabric_mgt/gridification/lcas/ Maillist http: //datagrid. in 2 p 3. fr/cgi-bin/cvsweb. cgi/fabric_mgt/gridification/lcmaps/ hep-proj-grid-fabric-gridify@cern. ch EDG Java Security Web site http: //edg-wp 2. web. cern. ch/edg-wp 2/security/ HEPi. X, Amsterdam 2003 – Grid Security and Site Authorization in EDG – n° 18