GRID AND CLOUD COMPUTING Cloud Computing Hardware Software































- Slides: 54

GRID AND CLOUD COMPUTING Cloud Computing Hardware, Software and Data Security http: //web. uettaxila. edu. pk/CMS/FALL 2017/te. GNCCms/ Courtesy of Professor Ahmed Ezzat, Ph. D www. svuca. edu Courtesy: Dr Gnanasekaran Thangavel

UNIT 8: CLOUD AND SECURITY - Cloud Computing – Characteristics, Attributes, Terminology – Hardware: Data Center and Thin Client – Software: Virtualization and Services – Why now? What’s the challenge ahead? - Mobile Applications and Social Networking – How are they related to Cloud Computing? – Impact on Consumers and Enterprises - Cloud Security, IAM and Standardization 2/28/2021 2

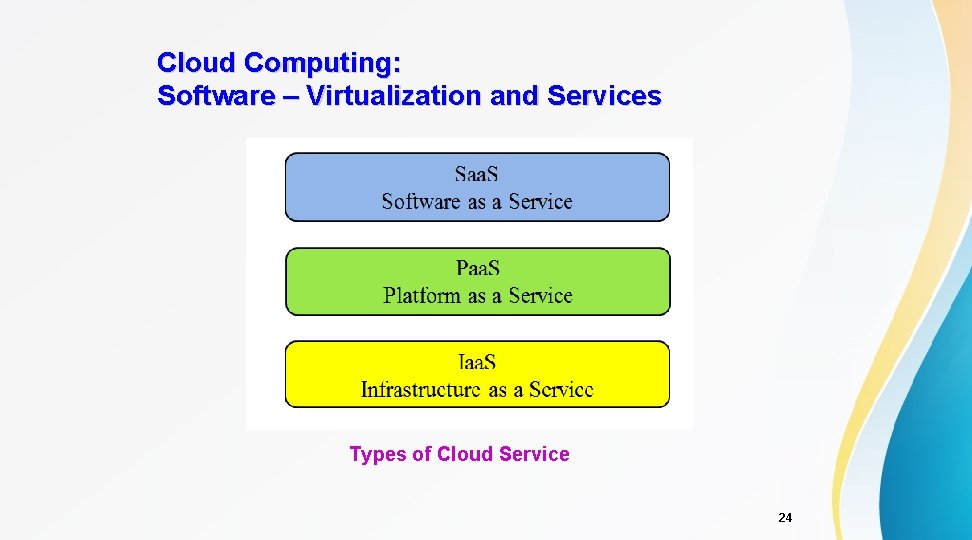
Background: Cloud Computing in a Nutshell • • • Cloud Computing – Applications delivered as services over the Internet – Hardware and systems software in the datacenters provide those services. Cloud: datacenter hardware and software Centralization of IT infrastructure made available to end users, software providers, and enterprises over the Internet Service Models: – Software as a Service (Saa. S, e. g. salesforce. com) – Platform as a Service (Paa. S, e. g. Google’s App Engine) – Infrastructure as a Service (Iaa. S, e. g. Amazon Web Service) Why? – Easier to manage and Larger economies of scale 3

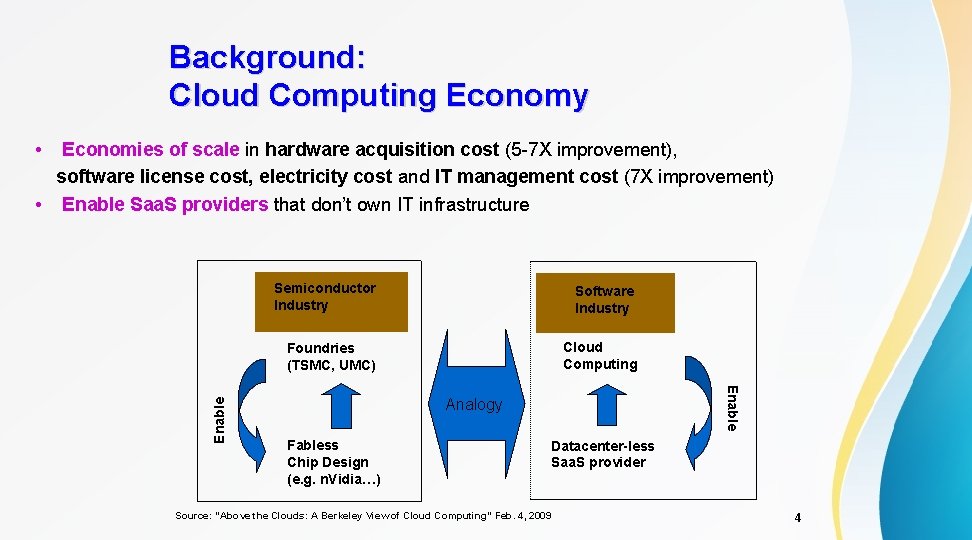
Background: Cloud Computing Economy • Semiconductor Industry Software Industry Foundries (TSMC, UMC) Cloud Computing Enable Economies of scale in hardware acquisition cost (5 -7 X improvement), software license cost, electricity cost and IT management cost (7 X improvement) • Enable Saa. S providers that don’t own IT infrastructure Analogy Fabless Chip Design (e. g. n. Vidia…) Datacenter-less Saa. S provider Source: “Above the Clouds: A Berkeley View of Cloud Computing” Feb. 4, 2009 4

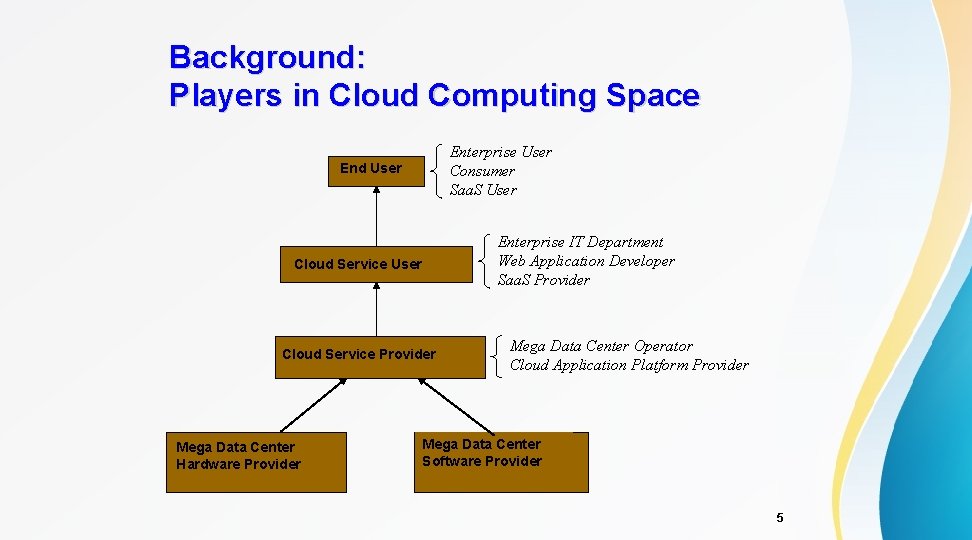
Background: Players in Cloud Computing Space Enterprise User Consumer Saa. S User End User Enterprise IT Department Web Application Developer Saa. S Provider Cloud Service User Cloud Service Provider Mega Data Center Hardware Provider Mega Data Center Operator Cloud Application Platform Provider Mega Data Center Software Provider 5

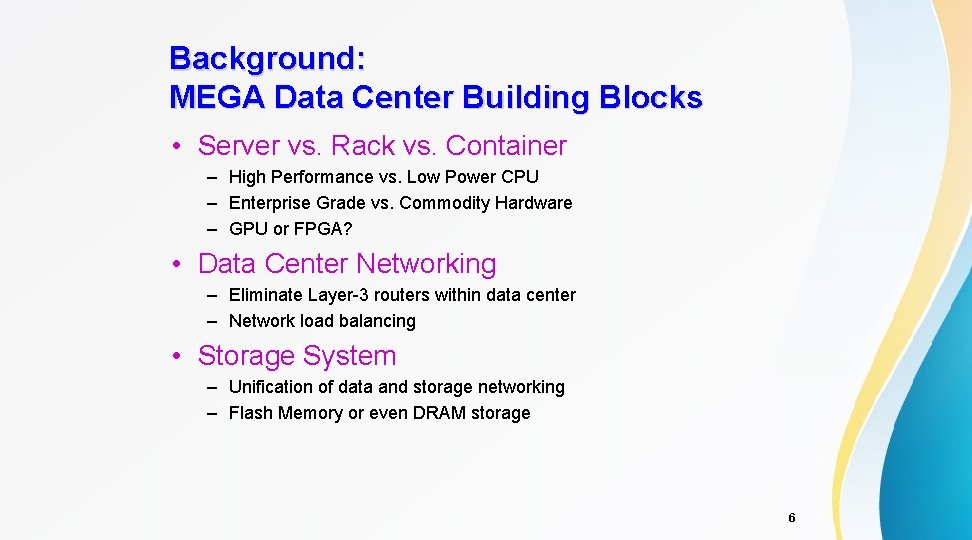
Background: MEGA Data Center Building Blocks • Server vs. Rack vs. Container – High Performance vs. Low Power CPU – Enterprise Grade vs. Commodity Hardware – GPU or FPGA? • Data Center Networking – Eliminate Layer-3 routers within data center – Network load balancing • Storage System – Unification of data and storage networking – Flash Memory or even DRAM storage 6

Background: Challenge 1 - Power Efficiency • Why do you build Mega Data Centers at the scales of 100 k to one million machines? – Energy cost becomes critical – Cooling System – Think Green • New Metric: Amount of work done/joule • Intelligent Power Management – Centralized or distributed power source • Fine-granularity HW component turn on/off: memory bank, CPU core, CPU, disk, etc. • Modularity and Flexibility – Easily Expandable/Removable Systems – Physical Design Concerns 7

Background: Challenge 2 - Data Center Management • Design for manageability – Discovery: Establish dependencies among system components. If Switch 32 dies, how many services are affected? – Diagnosis: Identify the root cause behind a functionality or performance failure – Remediation: Take corrective actions to minimize the mean time to repair • Complexity of Managing of Real and Virtual Computing, Networking, Storage and Other Devices 8

Cloud Computing: Characteristics • Cloud Computing: is a style of computing in which dynamically scalable and often virtualized resources are provided as a service over the internet • Virtual: Software, databases, Web Servers, Operating Systems, Storage, and networking as virtual servers • On-demand: ability to add and subtract processors, memory, network bandwidth, storage as needed • Users need not have knowledge of, expertise in, or control over the technology infrastructure in the “cloud” that supports them 9

Cloud Computing: Attributes • Off-Premise: The service is hosted & delivered from a location that belongs to a service provider over the Internet • Elasticity: leverage the inherent scalability of service provider by providing elastic provisioning mechanism so that resources can be scaled up/down quickly as needed • Flexible Billing: Fine-grained metering of resource usage combined with on-demand service provisioning • Virtualization: Cloud services offered through an abstracted infrastructure • Service Delivery: Typically the service offers programmatic API in addition to user interface 10

Cloud Computing: Attributes • Universal Access (Resource Democratization): Pooled resources are available to anyone authorized to utilize them • Simplified Management: through automatic provisioning to meet scalability needs, user self-service, and programmatically accessible resources • Affordable Resources: cost is reduced dramatically because: (1) No capital cost. (2) Economy-of-scale • Multi-tenancy: mechanisms to isolate tenants (organizations) from each other while pooling resources across customers • Service-level Agreement (SLA): Sets the expectations with the customer 11

Cloud Computing: Terms • Service-Oriented Architecture (SOA): Decompose IT landscape of an Enterprise into unassociated and loosely coupled functional services. An enterprise that uses SOA is better positioned to leverage Cloud Computing • Grid Computing: Use of many interconnected computers to solve a problem through highly parallel computation • Web 2. 0: Is associated with Cloud Computing even though there are no intrinsic connections. Web 2. 0 refers to a class of services (platform for web-based collaborative communities) that may be delivered in many different ways, while Cloud Computing refers to a means of delivering the service 12

Cloud Computing: Since 1999 - “Web 2. 0” – Self publishing: Live. Journal/Blogger. com (1999), You. Tube (2005) – Metadata & feeds: RSS (1999), Atom (2003) – Collaboration: Wikipedia (2001), Google docs (2006) – Tagging: del. icio. us (2003), digg. com (2004), flickr (2004) – Ajax: Gmail (2004), Google Maps (2005) – Long Tail: Amazon (1994), Google Ad. Sense (2005) – API: Yahoo!, GData, Amazon… (who doesn't? ) – Aggregation: Google News (2002), Google Reader (2005) – Social: Linked. In (2003), My. Space (2003), Facebook (2004) – Microblogging: Twitter (2006), Plurk (2008) 13

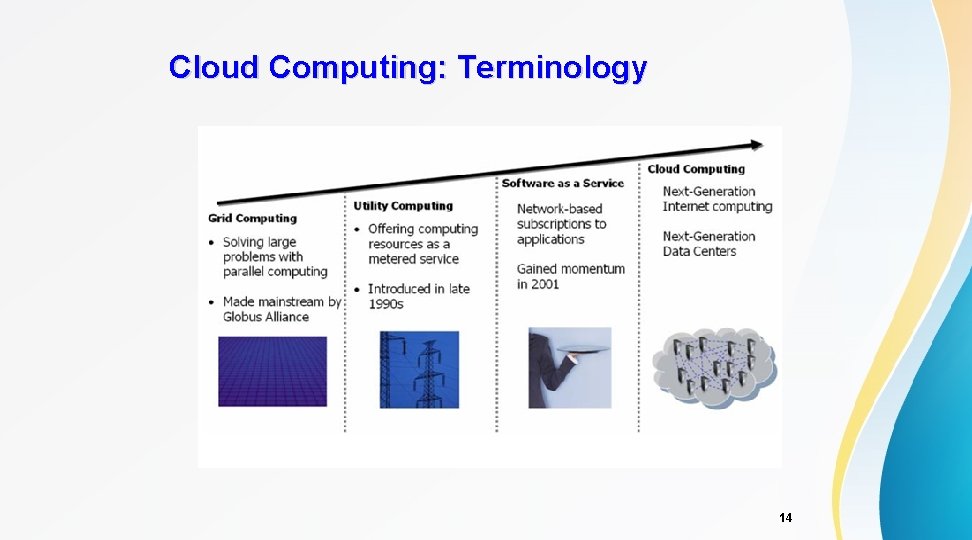
Cloud Computing: Terminology 14

Cloud Computing: Hardware – Datacenter & Thin Client • Cloud computing is the modern, if not ultimate, form of Server-Based Computing (SBC) • Thin client has been used successfully for the last 20 years • Thin client is typically web-based desktop management and support system, using HTTP or FTP, and as a result the administration of the thin client infrastructure can be outsources as a cloud service • With thin client and outsourcing IT to external service provider, client data are handled professionally and data availability is guaranteed (SLA) 15

Cloud Computing: Hardware – Datacenter Classification • Tier I datacenters: – – – Single path for power and cooling distribution Non-redundant components Expected availability of 99. 671% • Tier II: – – Adds redundant components to this design (N + 1), improving availability Expected availability of 99. 741% • Tier III: – – Multiple power and cooling distribution paths but only one active path. They also have redundant components and are concurrently maintainable, that is, they provide redundancy even during maintenance, usually with an N + 2 setup Concurrent maintainable infrastructure Expected availability of 99. 982% 16

Cloud Computing: Hardware – Datacenter Classification • Tier IV – – Meets or exceed tier 1, tier 2, and tier 3 requirements Two active power and cooling distribution paths, redundant components in each path Tolerate any single equipment failure without impacting the load Expected availability of 99. 995% 17

Cloud Computing: Hardware - Main Components • Power – UPS (Unintrupted Power Suply) – PDU (Power Distribution Unit) • Cooling • CRAC (Computer Room Air Conditioning) • Free Cooling (Heat exchange using water) http: //www. airedale. com/web/Products/Free-Cooling. htm • What about efficiency? • The amount of computational work performed divided by the total energy used in the process 18

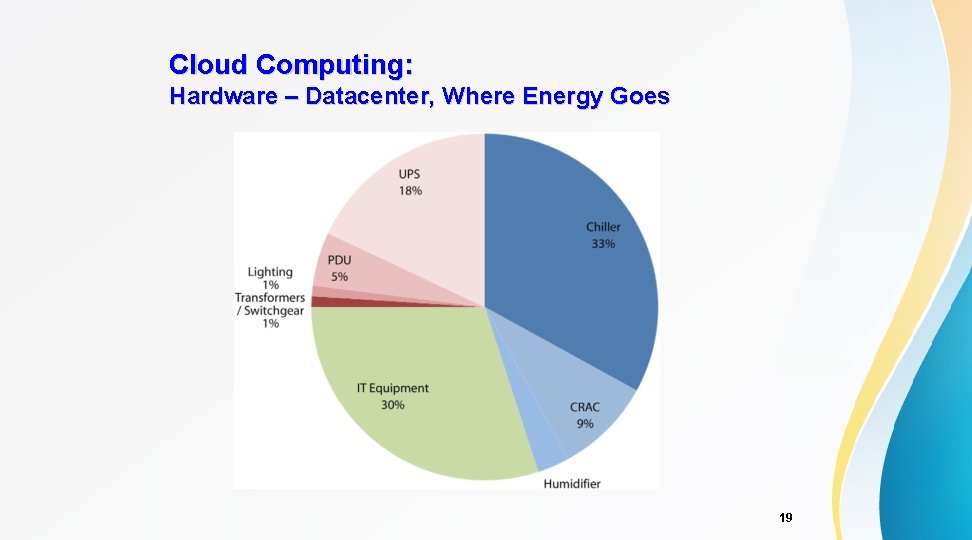
Cloud Computing: Hardware – Datacenter, Where Energy Goes 19

Cloud Computing: Hardware – Datacenters Tour • Google – http: //www. youtube. com/watch? v=vo. OK-1 DLr 00 – http: //www. youtube. com/watch? v=VCh. OEv. Kic. QQ – http: //www. youtube. com/watch? v=XZm. GGAb. Hqa 0 • Microsoft – http: //www. youtube. com/watch? v=h. Ox. A 1 l 1 p. QIw • HP – http: //www. youtube. com/watch? v=XB 0 c. Vd. NC 5 Y 8 • IBM – https: //www. youtube. com/watch? v=ymtrqig. TEXU • Facebook – http: //www. youtube. com/watch? v=4 A_A-Cmrqp. Q 20

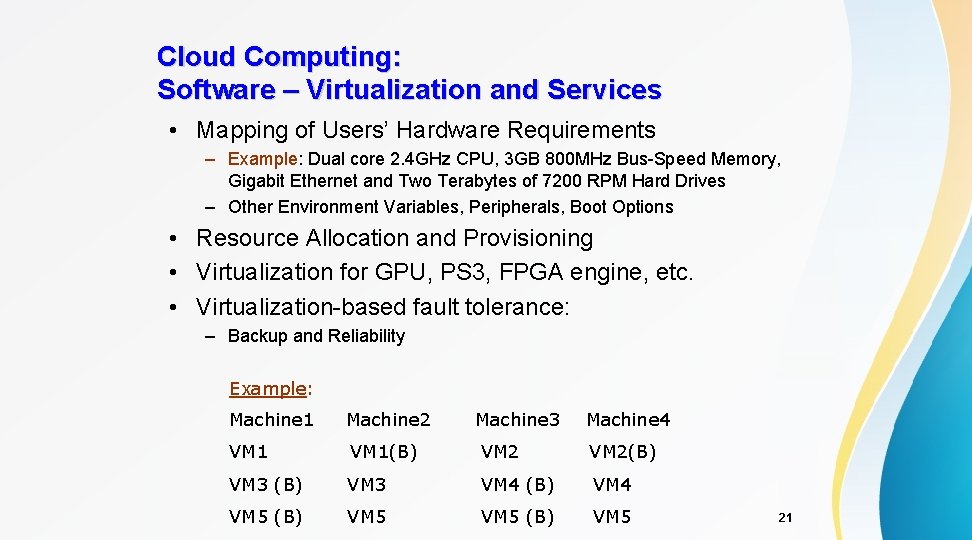
Cloud Computing: Software – Virtualization and Services • Mapping of Users’ Hardware Requirements – Example: Dual core 2. 4 GHz CPU, 3 GB 800 MHz Bus-Speed Memory, Gigabit Ethernet and Two Terabytes of 7200 RPM Hard Drives – Other Environment Variables, Peripherals, Boot Options • Resource Allocation and Provisioning • Virtualization for GPU, PS 3, FPGA engine, etc. • Virtualization-based fault tolerance: – Backup and Reliability Example: Machine 1 Machine 2 Machine 3 Machine 4 VM 1(B) VM 2(B) VM 3 VM 4 (B) VM 4 VM 5 (B) VM 5 21

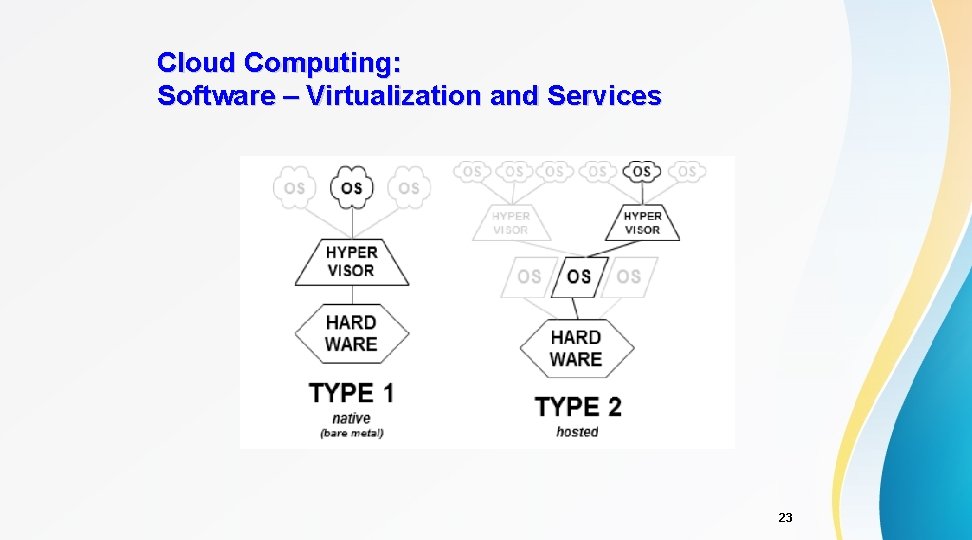
Cloud Computing: Software – Virtualization and Services • Hypervisor, Virtual Machine Manager - VMM, is one popular technique allowing multiple Operating Systems, guest OS, to run concurrently on a host computer • Hypervisor describes the interface provided by the cloud computing functionality known as Iaa. S • There are two types of hypervisors: – Type-1 (bare metal) hypervisors: run directly on the host hardware. It controls both the hardware as well as the guest OS – Type-2 (hosted) hypervisors: run within the conventional OS as a distinct 2 nd layer, and the guest OS runs as a 3 rd layer 22

Cloud Computing: Software – Virtualization and Services 23

Cloud Computing: Software – Virtualization and Services Types of Cloud Service 24

Cloud Computing: Why Cloud Computing Now? (1) • Market Pull – Software on the premise -> Saa. S • Information technology (IT) on the premise -> IT service as a rented utility (Electricity) – IT should not and will not be a core competence for most corporations – Paa. S and Iaa. S • Lowering up-front and day-to-day IT cost: – Pay only as much as actual resource usage – Total Cost of Ownership including SW maintenance 25

Cloud Computing: Why Cloud Computing Now? (2) • Technology Push – Broadband network connectivity getting faster and more reliable – Low Cost Powerful Processors and Advanced Virtualization Software • Sufficient trust in infrastructure providers • Google is already a critical service for most of the world, and it is in the cloud! • Comparison: – Mainframe systems 26

Mobile Apps & Social Networking: Innovative Apps of Cloud Computing • Mobile Applications and Social Networking are greatly empowered and enriched by Cloud Computing. • Popular mobile devices have to be low power, low priced, thus need to shift most computing tasks to the cloud. • Cloud-backed consumer device: – Thin phone + desktop virtualization – Mobile Internet Device (MID) – E-Books and other Gadgets Sentio Desktop (Android 4 -6) https: //play. google. com/store/apps/details? id=com. andromium. os&hl=en https: //www. androidauthority. com/install-ubuntu-on-your-android-smartphone-765408/ 27

Mobile Apps & Social Networking: Social Networking • Facebook, Twitter, Orkut, Linked-In – Viral Effect and Stickiness – Attract huge investment from big players • Online Gaming and Wireless Access – Solution by Cloud Computing • Global Movement and Reach – Kaixin Business Model – Virtual Economy and Social Issues – China Health Ministry to treat 'Net addiction as disorder 28

Mobile Apps & Social Networking: Social Networking in Enterprises • Cisco Systems – The Human Effect Networking Campaign – Acquisition of Five Across, Pure Digital • IBM – Lotus Connections - Social software for business – Home page, Blogs, Profiles, Wikis, Communities. . . • Google and Others – Performance review based on network circles – Development of Social Networking style Corporate Communications Tools 29

Interesting Projects towards future Mobile use • Maru. OS – https: //maruos. com 2/28/2021 https: //www. bostondynamics. com/robots 30

Cloud Computing Data Security for 1. Data in transit (transmission) 2. Data at rest (storage) 3. Processing of data including multitenancy (multiuser) 4. Data Lineage (traversal) 5. Data Provenance (origin) 6. Data remanance (residual) • Solutions include encryption, identity management, sanitation (removal of residual data) 2/28/2021 31

Cloud Service Provider: Data and its Security • What data does the provider collect – e. g. , metadata, and how can this data be secured? 1. Data security issues 2. Access control, • Key management for encrypting • Confidentiality, Integrity and Availability are objectives of data security in the cloud 2/28/2021 32

Identity and Access Management (IAM) in the Cloud Trust Boundaries and IAM • In a traditional environment, trust boundary is within the control of the organization • This includes the governance of the networks, servers, services, and applications • In a cloud environment, the trust boundary is dynamic and moves within the control of the service provider as well as organizations • Identity federation is an emerging industry best practice for dealing with dynamic and loosely coupled trust relationships in the collaboration model of an organization • Core of the architecture is the directory service which is the repository for the identity, credentials and user attributes 2/28/2021 33

Why Identity and Access Management (IAM)? • Improves operational efficiency and regulatory compliance management • IAM enables organizations to achieve access control and operational security • Cloud use cases that need IAM – Organization employees accessing Saa. S service using identity federation – IT admin access CSP management console to provision resources and access for users using a corporate identity – Developers creating accounts for partner users in Paa. S – End users access storage service in a cloud – Applications residing in a cloud serviced provider access storage from another cloud service 2/28/2021 34

IAM Challenges • Provisioning resources to users rapidly to accommodate their changing roles • Disparate features e. g. identities, access rights • Need standards and protocols that address the IAM challenges IAM Definitions • Authentication • Verifying the identity of a user, system or service • Authorization • Privileges that a user or system or service has after being authenticated (e. g. , access control) • Auditing Exam what actions the user, system or service has carried out • Check for compliance • 2/28/2021 35

IAM Practice • Identity and Access Management (IAM) process consists of the following: – User management (for managing identity life cycles), – Authentication management, – Authorization management, – Access management, – Application management and provisioning, – Monitoring and auditing, – Credential and attribute management, – Entitlement management, – Identity federation management, – Centralization of authentication and authorization, – Compliance management, 2/28/2021 36

Getting Ready for the Cloud • Organization using a cloud must plan for user account provisioning – How can a user be authenticated in a cloud • Organization can use cloud based solutions from a vendor for IAM – Identity Management as a Service • Industry standards for federated identity management – SAML, WS-Federation, Liberty Alliance https: //solutionsreview. com/identity-management-solutions-directory/ 2/28/2021 37

Relevant IAM Standards and Protocols for Cloud � IAM Standards and Specifications for Organizations • SAML (Security Assertion Markup Language) • SPML (Service Provisioning Markup Language) • XACML (e. Xtensible Access Control Markup Language) • OAuth (Open Authentication) – cloud service X accessing data in cloud service Y without disclosing credentials � IAM Standards and Specifications for Consumers • Open. ID • Information Cards • Open Authenticate (OAUTH) • Open Authentication API (Open. Auth) 2/28/2021 38

IAM Practices in the Cloud • Cloud Identity Administration • Life cycle management of user identities in the cloud • Federated Identity (SSO) • Enterprise an enterprise Identity provider within an Organization perimeter • Cloud-based Identity provider Cloud Authorization Management • • XACML is the preferred model for authorization RBAC (Role-Based Access Control) is being explored Dual roles: Administrator and User IAM support for compliance management 2/28/2021 39

Cloud Service Provider and IAM Practice • What is the responsibility of the CSP and the responsibility of the organization/enterprise? • Enterprise IAM requirements • Provisioning of cloud service accounts to users • Provisioning of cloud services for service to service integration • SSO support for users based on federation standards • Support for international and regulatory policy requirements • User activity monitoring • How can enterprises expand their IAM requirements to Saa. S, Paa. S and Iaa. S 2/28/2021 40

Security Management in the Cloud • Security Management Standards • Security Management in the Cloud • Availability Management • Access Control Management • Security Vulnerability, Patch and Configuration Management Security Management Standards • Security Management has to be carried out in the cloud • Standards include ITIL (Information Technology Infrastructure Library) and ISO 27001/27002 • What are the policies, procedures, processes and work instruction for managing security 2/28/2021 41

Security Management in the Cloud • Availability Management (ITIL) • Access Control (ISIO, ITIL) • Vulnerability Management (ISO, IEC) • Patch Management (ITIL) • Configuration Management (ITIL) • Incident Response (ISO/IEC) • System use and Access Monitoring (ISO 27001) 2/28/2021 42

Availability Management Saa. S availability • Customer responsibility: Customer must understand SLA and communication methods • Saa. S health monitoring • Paa. S availability • Customer responsibility • Paa. S health monitoring • Iaa. S availability • Customer responsibility • Iaa. S health monitoring • 2/28/2021 43

Access Control Management in the Cloud • • Who should have access and why How is a resources accessed How is the access monitored Impact of access control of Saa. S, Paa. S and Iaa. S Security Vulnerability, Patch and Configuration (VPC) Management • • How can security vulnerability, patch and configuration management for an organization be extended to a cloud environment What is the impact of VPS on Saa. S, Paa. S and Iaa. S 2/28/2021 44

Privacy • Privacy and Data Life Cycle • Key Privacy Concerns in the Cloud • Who is Responsible for Privacy • Privacy Risk Management and Compliance ion the Cloud • Legal and Regulatory Requirements Privacy and Data Life Cycle Privacy: Accountability of organizations to data subjects as well as the transparency to an organization’s practice around personal information • Data Life Cycle • Generation, Use, Transfer, Transformation, Storage, Archival, Destruction • Need policies • 2/28/2021 45

Legal and Regulatory Requirements � US Regulations • Federal Rules of Civil Procedure • US Patriot Act • Electronic Communications Privacy Act • FISMA • GLBA • HIPAA • HITECH Act � International regulations • EU Directive • APEC Privacy Framework 2/28/2021 46

Audit and Compliance • Internal Policy Compliance • Governance, Risk and Compliance (GRC) • Control Objectives • Regulatory/External Compliance • Cloud Security Alliance • Auditing for Compliance 2/28/2021 47

Regulatory/External Compliance • Sarbanes-Oxley Act • PCI DSS • HIPAA • COBIT • What is the impact of Cloud computing on the above regulations? 2/28/2021 48

Auditing for Compliance • Internal and External Audits • Audit Framework • • SAS 70 • Sys. Trust • Web. Trust • ISO 27001 certification Relevance to Cloud 2/28/2021 49

Cloud Service Providers 1. Amazon Web Services (Iaa. S) 2. Google (Saa. S, Paa. S) 3. Microsoft Azure (Saa. S, Iaa. S) 4. Proofpoint (Saa. S, Iaa. S) 5. Right. Scale (Saa. S) 6. Salesforce. com (Saa. S, Paa. S) 7. Sun Open Cloud Platform 8. Workday (Saa. S) 2/28/2021 50

Directions • Analysts predict that cloud computing will be a huge growth area • Cloud growth will be much higher than traditional IT growth • Will likely revolutionize IT • Need to examine how traditional solutions for IAM, Governance, Risk Assessment etc will work for Cloud • Technologies will be enhanced (Iaa. S, Paa. S, Saa. S) • Security will continue o be a major concern 2/28/2021 51

References 1. Kai Hwang, Geoffery C. Fox and Jack J. Dongarra, “Distributed and Cloud Computing: Clusters, Grids, Clouds and the Future of Internet”, First Edition, Morgan Kaufman Publisher, an Imprint of Elsevier, 2012. 2. www. nesc. ac. uk/action/esi/download. cfm%3 Findex=3882 3. www. cse. cuhk. edu. hk/~lyu/seminar/04 spring/Woodas. ppt 4. www. utdallas. edu/~bxt 043000/Teaching/CS 6301/Developing. . . cloud. . . /Lecture 5. ppt 5. http: //dl. ifip. org/db/conf/ifip 11 -4/inetsec 2010/Velev. Z 10. pdf 2/28/2021 52

Assignment #7 • In Slides 16 and 17, by using %age uptime availability of Tier-1, Tier-III and Tier-IV Data. Centers calculate their dowtime per day, week, month and year using https: //uptime. is/ 2/28/2021 53

Thank You Questions and Comments? http: //web. uettaxila. edu. pk/CMS/FALL 2017/te. GNCCms/ 2/28/2021 54