Grand Challenges for Enterprise Security Policies Nondisclosure policies







- Slides: 14

Grand Challenges for Enterprise Security Policies + Nondisclosure policies for distributed computations Arnon Rosenthal MITRE (visiting IBM Almaden) 1

Outline of Challenges Talk • Four big challenges – Security model for multi-model DBMSs – Compilation to heterogeneous enforcers – Mapping from abstract to implementation policies – Mapping between organizations’ policies • Brief comments on policy-related research in data privacy/security 3

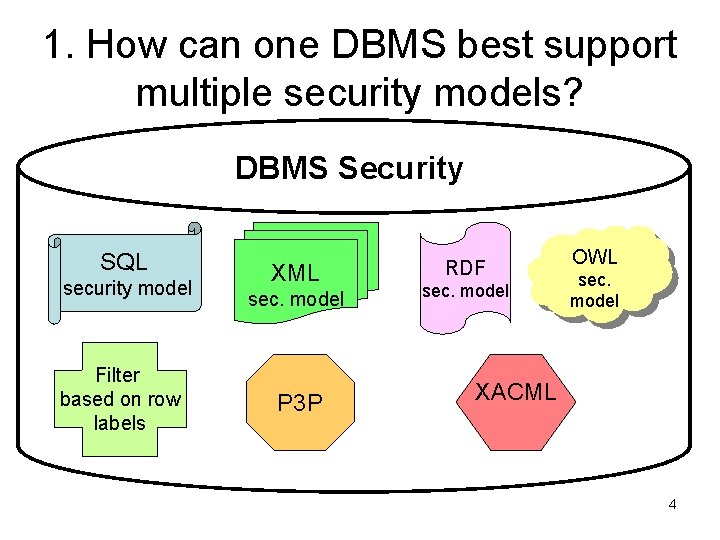
1. How can one DBMS best support multiple security models? DBMS Security SQL security model Filter based on row labels XML sec. model P 3 P RDF sec. model OWL sec. model XACML 4

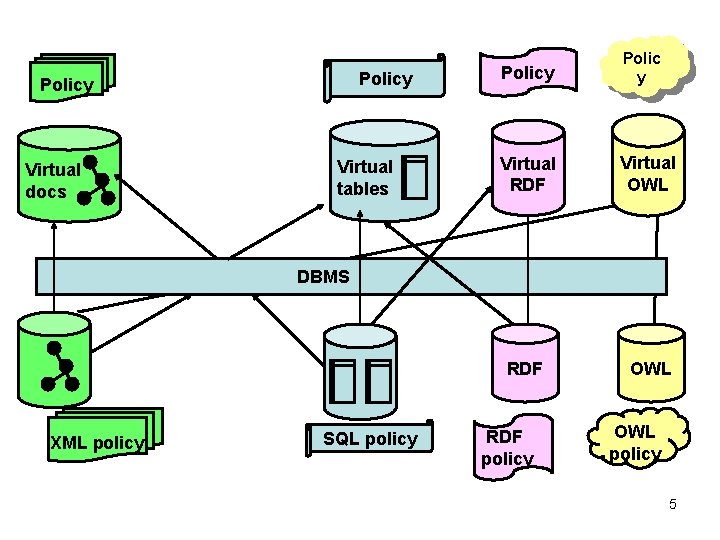
Policy Virtual docs Virtual tables Policy Polic y Virtual RDF Virtual OWL RDF OWL DBMS Add Tree graphic XML policy Add Table graphic SQL policy RDF policy OWL policy 5

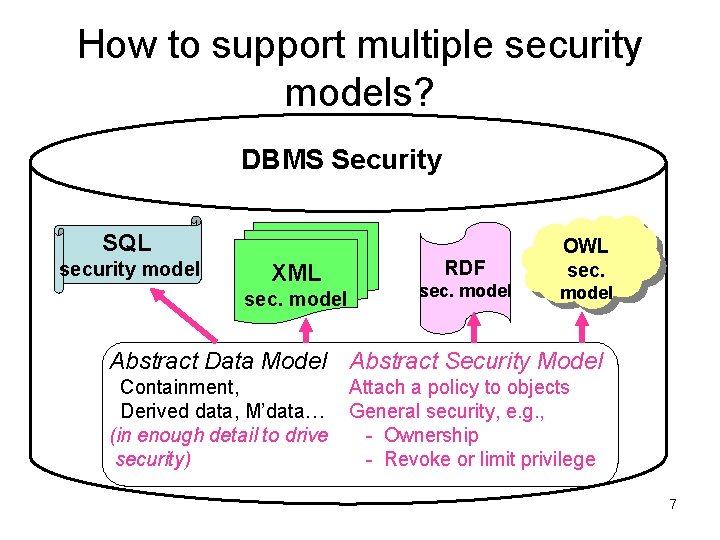
How to support multiple security models? DBMS Security SQL security model XML sec. model RDF sec. model OWL sec. model Abstract Data Model Abstract Security Model Containment, Derived data, M’data… (in enough detail to drive security) Attach a policy to objects General security, e. g. , - Ownership - Revoke or limit privilege 7

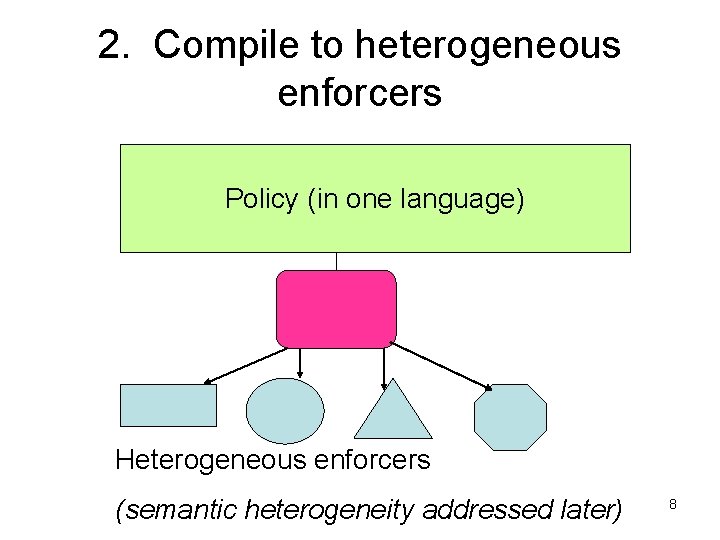
2. Compile to heterogeneous enforcers Policy (in one language) Heterogeneous enforcers (semantic heterogeneity addressed later) 8

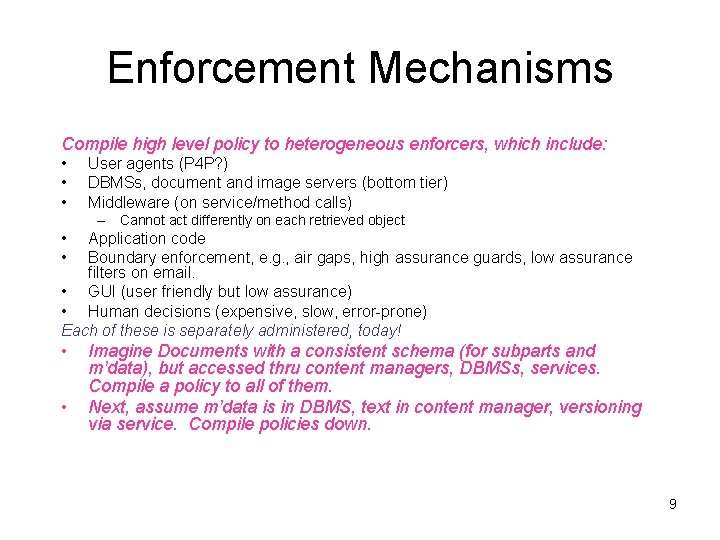
Enforcement Mechanisms Compile high level policy to heterogeneous enforcers, which include: • • • User agents (P 4 P? ) DBMSs, document and image servers (bottom tier) Middleware (on service/method calls) – Cannot act differently on each retrieved object • • Application code Boundary enforcement, e. g. , air gaps, high assurance guards, low assurance filters on email. • GUI (user friendly but low assurance) • Human decisions (expensive, slow, error-prone) Each of these is separately administered, today! • • Imagine Documents with a consistent schema (for subparts and m’data), but accessed thru content managers, DBMSs, services. Compile a policy to all of them. Next, assume m’data is in DBMS, text in content manager, versioning via service. Compile policies down. 9

Challenge 2: The Official Policy is not in terms of implementation artifacts Individually identified medical data shall be available only to professionals treating the patient, (with confidence profile P 3) ? Lab message: Blood type Firewalls Physical DB schemas 10

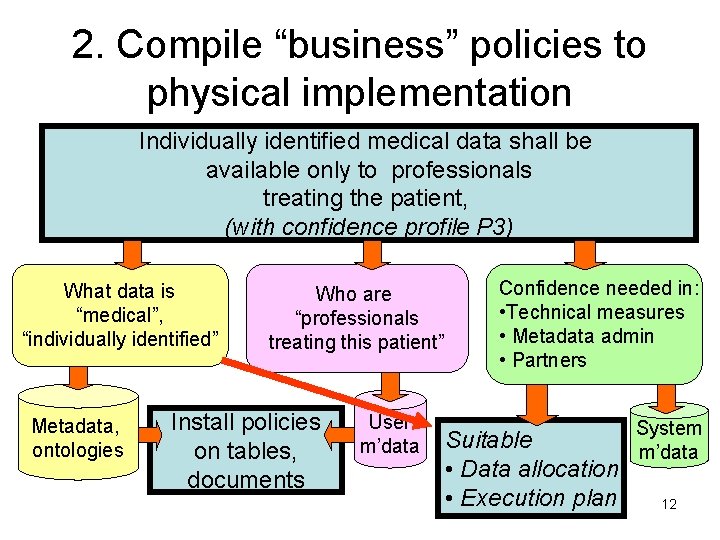
2. Compile “business” policies to physical implementation Individually identified medical data shall be available only to professionals treating the patient, (with confidence profile P 3) What data is “medical”, “individually identified” Metadata, ontologies Who are “professionals treating this patient” Install policies on tables, documents User m’data Confidence needed in: • Technical measures • Metadata admin • Partners Suitable • Data allocation • Execution plan System m’data 12

Translate and transfer policy across organizations and systems Aetna Travel Insurance Enforcement: Application server Policy applied: US (NY) Roles: Hi. PAA spec (Aetna version) Who are What data is • Medical • Indiv identified ? • Professionals • Treating this patient Insurance approver role only in US Confidence in • Technical measures • Metadata admin • Partners Paris Hospital Enforcement: DBMS Policy applied: France Roles: Hospital (Emergency Care) 13

Employing a research idea: Inference control • You have a full description of what the attacker knows • No collusion between requests from different User IDs • Administrators have identified all sensitive fields – Or it’s worthwhile to protect just a few • Efficiency – extra factor of 5 is OK • No updates Black bullets limit applicability. Not to zero, but is it a good place to invest scarce talent? 1 -2 probably can’t be removed by more research! Spend $$$$ for high certainty (locally), but partial solutions won’t give a large factor of protection 14

What’s different about privacy? • Millions of administrators, opting in and out • Human (Corporate? Animal? ) right 15

Privacy and Nondisclosure • Equating privacy with nondisclosure makes both terms less useful • Privacy involves – Rights – Notification, correctness, minimal collection and retention, … • Nondisclosure also applies to – Military plans, investigative reports – Lion King Video 16

An easily-applied categorization • Ask what stakeholder a policy protects – Privacy: The person (or entity) described – Enterprise secrecy: The entity controlling the database – Intellectual property: The provider of the info • Security usually adds integrity and availability (under attack) – Contrast with data quality, system availability which try to protect against Murphy’s Law 17
 Private securty
Private securty Industrial strategy grand challenges
Industrial strategy grand challenges Security program and policies principles and practices
Security program and policies principles and practices Database policy and procedures
Database policy and procedures Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Bell lapadula model
Bell lapadula model Security program and policies principles and practices
Security program and policies principles and practices Security program and policies principles and practices
Security program and policies principles and practices Sdn security challenges
Sdn security challenges Security and ethical challenges
Security and ethical challenges Theo dimitrakos
Theo dimitrakos Security and ethical challenges
Security and ethical challenges Putting the enterprise into the enterprise system
Putting the enterprise into the enterprise system Putting the enterprise into the enterprise system
Putting the enterprise into the enterprise system

























