GPRS Architecture with Viola Systems Arctic and M




- Slides: 15

GPRS Architecture with Viola Systems Arctic and M 2 M Gateway Products Jari Lahti, CTO

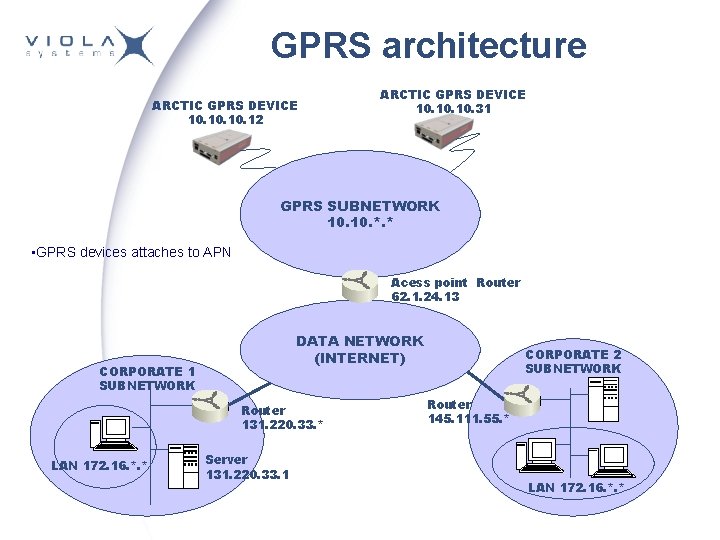
GPRS architecture ARCTIC GPRS DEVICE 10. 10. 12 ARCTIC GPRS DEVICE 10. 10. 31 GPRS SUBNETWORK 10. *. * • GPRS devices attaches to APN Acess point Router 62. 1. 24. 13 DATA NETWORK (INTERNET) CORPORATE 1 SUBNETWORK Router 131. 220. 33. * LAN 172. 16. *. * Server 131. 220. 33. 1 CORPORATE 2 SUBNETWORK Router 145. 111. 55. * LAN 172. 16. *. *

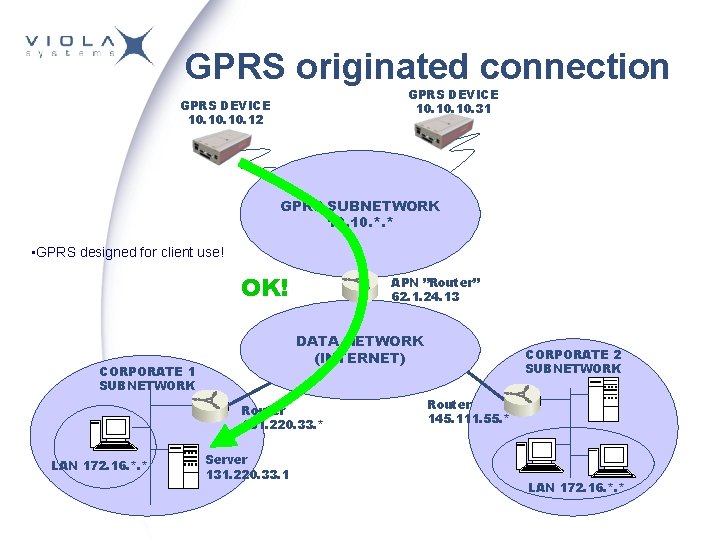
GPRS originated connection GPRS DEVICE 10. 10. 31 GPRS DEVICE 10. 10. 12 GPRS SUBNETWORK 10. *. * • GPRS designed for client use! OK! APN ”Router” 62. 1. 24. 13 DATA NETWORK (INTERNET) CORPORATE 1 SUBNETWORK Router 131. 220. 33. * LAN 172. 16. *. * Server 131. 220. 33. 1 CORPORATE 2 SUBNETWORK Router 145. 111. 55. * LAN 172. 16. *. *

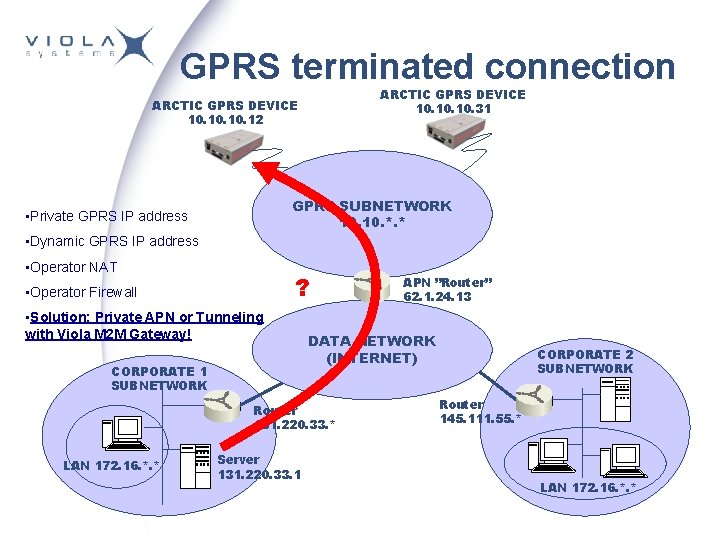
GPRS terminated connection ARCTIC GPRS DEVICE 10. 10. 31 ARCTIC GPRS DEVICE 10. 10. 12 GPRS SUBNETWORK 10. *. * • Private GPRS IP address • Dynamic GPRS IP address • Operator NAT ? • Operator Firewall • Solution: Private APN or Tunneling with Viola M 2 M Gateway! CORPORATE 1 SUBNETWORK DATA NETWORK (INTERNET) Router 131. 220. 33. * LAN 172. 16. *. * Server 131. 220. 33. 1 APN ”Router” 62. 1. 24. 13 CORPORATE 2 SUBNETWORK Router 145. 111. 55. * LAN 172. 16. *. *

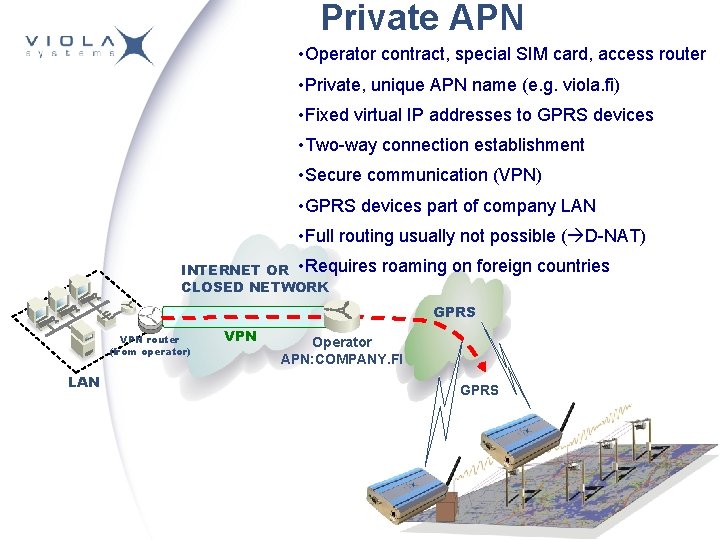
Private APN • Operator contract, special SIM card, access router • Private, unique APN name (e. g. viola. fi) • Fixed virtual IP addresses to GPRS devices • Two-way connection establishment • Secure communication (VPN) • GPRS devices part of company LAN • Full routing usually not possible ( D-NAT) INTERNET OR • Requires CLOSED NETWORK roaming on foreign countries GPRS VPN router (from operator) LAN VPN Operator APN: COMPANY. FI GPRS

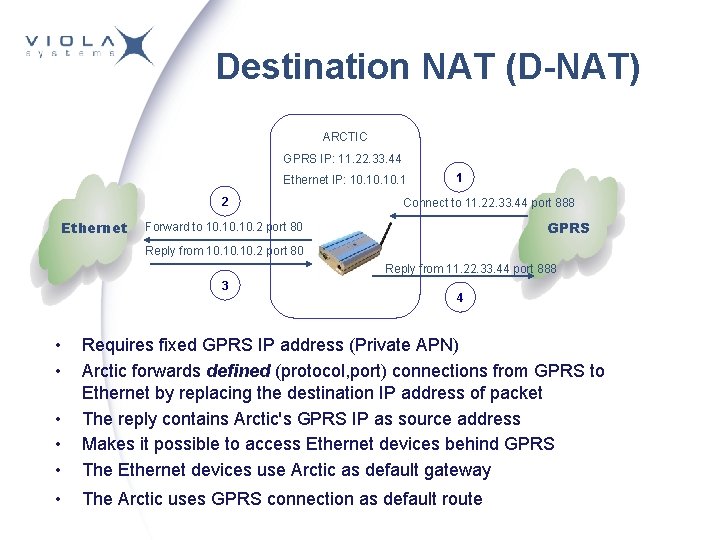
Destination NAT (D-NAT) ARCTIC GPRS IP: 11. 22. 33. 44 Ethernet IP: 10. 10. 1 2 Ethernet 1 Connect to 11. 22. 33. 44 port 888 GPRS Forward to 10. 10. 10. 2 port 80 Reply from 11. 22. 33. 44 port 888 3 • • 4 • • • Requires fixed GPRS IP address (Private APN) Arctic forwards defined (protocol, port) connections from GPRS to Ethernet by replacing the destination IP address of packet The reply contains Arctic's GPRS IP as source address Makes it possible to access Ethernet devices behind GPRS The Ethernet devices use Arctic as default gateway • The Arctic uses GPRS connection as default route

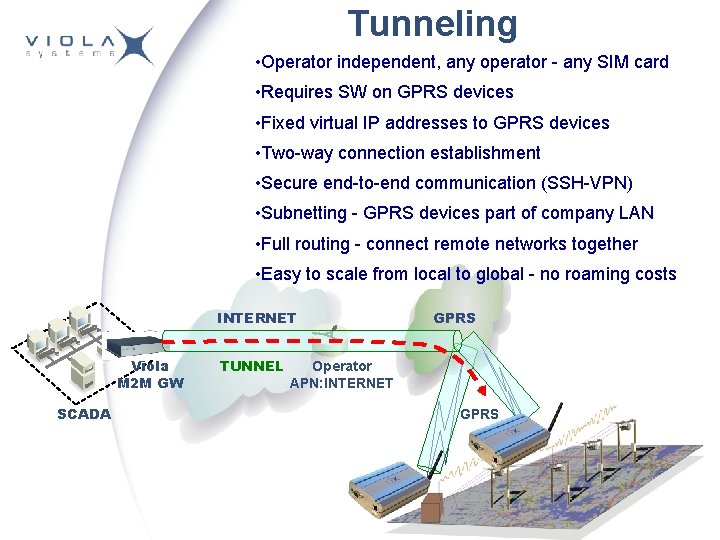
Tunneling • Operator independent, any operator - any SIM card • Requires SW on GPRS devices • Fixed virtual IP addresses to GPRS devices • Two-way connection establishment • Secure end-to-end communication (SSH-VPN) • Subnetting - GPRS devices part of company LAN • Full routing - connect remote networks together • Easy to scale from local to global - no roaming costs INTERNET Viola M 2 M GW SCADA TUNNEL GPRS Operator APN: INTERNET GPRS

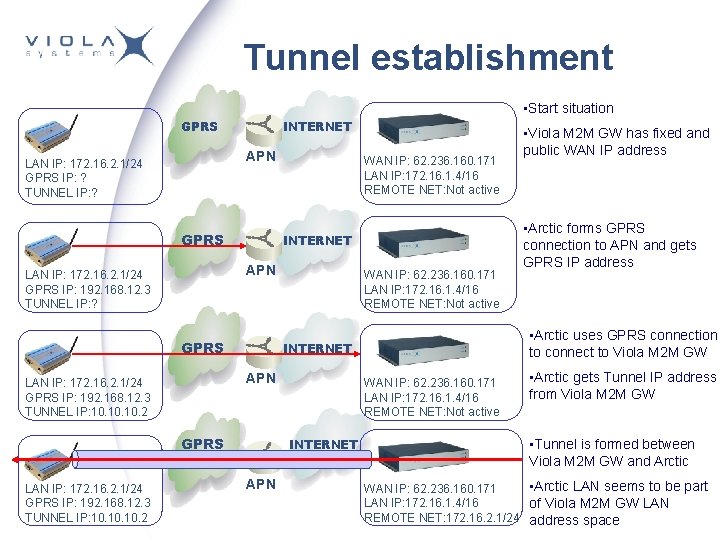
Tunnel establishment • Start situation GPRS INTERNET APN LAN IP: 172. 16. 2. 1/24 GPRS IP: ? TUNNEL IP: ? GPRS INTERNET APN LAN IP: 172. 16. 2. 1/24 GPRS IP: 192. 168. 12. 3 TUNNEL IP: ? GPRS WAN IP: 62. 236. 160. 171 LAN IP: 172. 16. 1. 4/16 REMOTE NET: Not active INTERNET APN • Arctic forms GPRS connection to APN and gets GPRS IP address • Arctic uses GPRS connection to connect to Viola M 2 M GW INTERNET APN LAN IP: 172. 16. 2. 1/24 GPRS IP: 192. 168. 12. 3 TUNNEL IP: 10. 10. 10. 2 WAN IP: 62. 236. 160. 171 LAN IP: 172. 16. 1. 4/16 REMOTE NET: Not active • Viola M 2 M GW has fixed and public WAN IP address • Arctic gets Tunnel IP address from Viola M 2 M GW • Tunnel is formed between Viola M 2 M GW and Arctic • Arctic LAN seems to be part WAN IP: 62. 236. 160. 171 LAN IP: 172. 16. 1. 4/16 of Viola M 2 M GW LAN REMOTE NET: 172. 16. 2. 1/24 address space

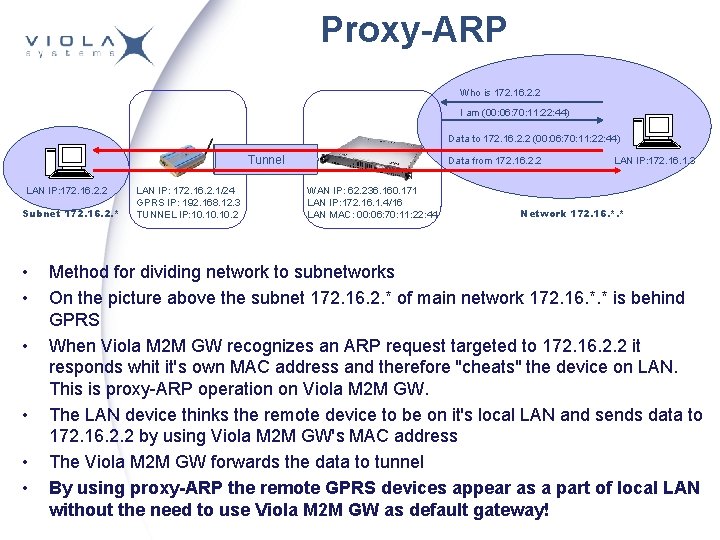
Proxy-ARP Who is 172. 16. 2. 2 I am (00: 06: 70: 11: 22: 44) Data to 172. 16. 2. 2 (00: 06: 70: 11: 22: 44) Tunnel LAN IP: 172. 16. 2. 2 Subnet 172. 16. 2. * • • • LAN IP: 172. 16. 2. 1/24 GPRS IP: 192. 168. 12. 3 TUNNEL IP: 10. 10. 2 Data from 172. 16. 2. 2 WAN IP: 62. 236. 160. 171 LAN IP: 172. 16. 1. 4/16 LAN MAC: 00: 06: 70: 11: 22: 44 LAN IP: 172. 16. 1. 3 Network 172. 16. *. * Method for dividing network to subnetworks On the picture above the subnet 172. 16. 2. * of main network 172. 16. *. * is behind GPRS When Viola M 2 M GW recognizes an ARP request targeted to 172. 16. 2. 2 it responds whit it's own MAC address and therefore "cheats" the device on LAN. This is proxy-ARP operation on Viola M 2 M GW. The LAN device thinks the remote device to be on it's local LAN and sends data to 172. 16. 2. 2 by using Viola M 2 M GW's MAC address The Viola M 2 M GW forwards the data to tunnel By using proxy-ARP the remote GPRS devices appear as a part of local LAN without the need to use Viola M 2 M GW as default gateway!

L 2 TP Tunnel • Plain tunneling without strong authentication or encryption • • – Viola M 2 M Gateway authenticates the Arctic only by user/password combination – Data is not encrypted Very fast data transfer and small delays when compared to other tunnels Very fast tunnel establishment Suitable for bringing full routing to private-APN systems Suitable for applications not requiring strong security Extra GPRS data caused by L 2 TP Tunnel ~ 30 -40 bytes/packet Available on Arctic versions >= 4. 0 Currently available as add-on for M 2 M GW – standard feature on Series 5 release Q 1/2006

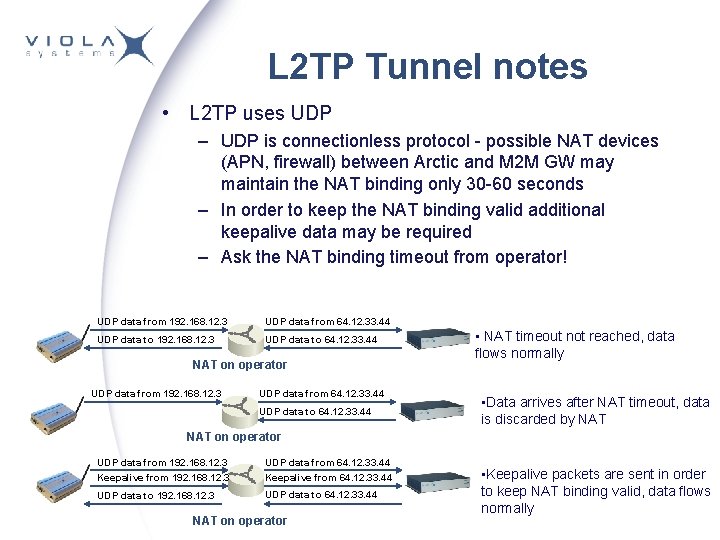
L 2 TP Tunnel notes • L 2 TP uses UDP – UDP is connectionless protocol - possible NAT devices (APN, firewall) between Arctic and M 2 M GW may maintain the NAT binding only 30 -60 seconds – In order to keep the NAT binding valid additional keepalive data may be required – Ask the NAT binding timeout from operator! UDP data from 192. 168. 12. 3 UDP data from 64. 12. 33. 44 UDP data to 192. 168. 12. 3 UDP data to 64. 12. 33. 44 NAT on operator UDP data from 192. 168. 12. 3 UDP data from 64. 12. 33. 44 UDP data to 64. 12. 33. 44 • NAT timeout not reached, data flows normally • Data arrives after NAT timeout, data is discarded by NAT on operator UDP data from 192. 168. 12. 3 UDP data from 64. 12. 33. 44 Keepalive from 192. 168. 12. 3 Keepalive from 64. 12. 33. 44 UDP data to 192. 168. 12. 3 UDP data to 64. 12. 33. 44 NAT on operator • Keepalive packets are sent in order to keep NAT binding valid, data flows normally

SSH-VPN • Secure and authenticated VPN tunnel – Uses SSH protocol – Authentication with 1024 bit RSA keys • Each device has two keys (asymmetric keypair) – private key (must be kept hidden) – public key (can be given to anyone) – Message crypted with a private key can be decrypted only with a public key of the same asymmetric keypair – Message crypted with a public key can be decrypted only with a private key of the same asymmetric keypair • Communicating parties must know each other's public keys in order to be able to authenticate • Extra GPRS data caused by SSH-VPN ~ 50 -60 bytes/packet

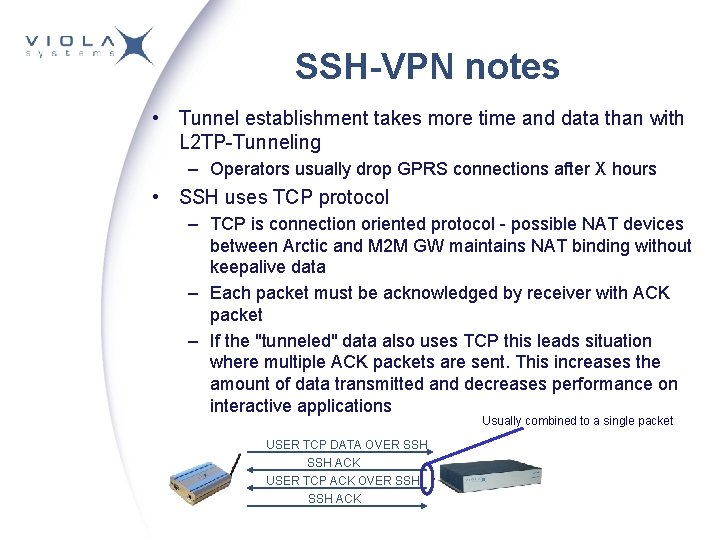
SSH-VPN notes • Tunnel establishment takes more time and data than with L 2 TP-Tunneling – Operators usually drop GPRS connections after X hours • SSH uses TCP protocol – TCP is connection oriented protocol - possible NAT devices between Arctic and M 2 M GW maintains NAT binding without keepalive data – Each packet must be acknowledged by receiver with ACK packet – If the "tunneled" data also uses TCP this leads situation where multiple ACK packets are sent. This increases the amount of data transmitted and decreases performance on interactive applications Usually combined to a single packet USER TCP DATA OVER SSH ACK USER TCP ACK OVER SSH ACK

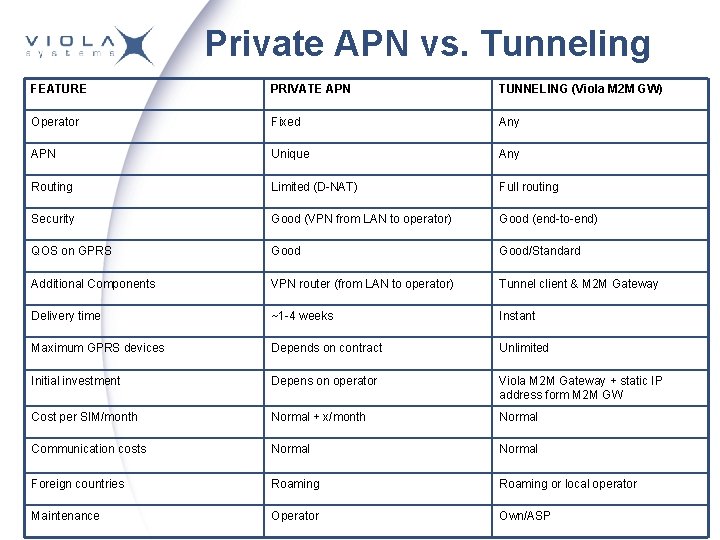
Private APN vs. Tunneling FEATURE PRIVATE APN TUNNELING (Viola M 2 M GW) Operator Fixed Any APN Unique Any Routing Limited (D-NAT) Full routing Security Good (VPN from LAN to operator) Good (end-to-end) QOS on GPRS Good/Standard Additional Components VPN router (from LAN to operator) Tunnel client & M 2 M Gateway Delivery time ~1 -4 weeks Instant Maximum GPRS devices Depends on contract Unlimited Initial investment Depens on operator Viola M 2 M Gateway + static IP address form M 2 M GW Cost per SIM/month Normal + x/month Normal Communication costs Normal Foreign countries Roaming or local operator Maintenance Operator Own/ASP
