GoMoku and ThreadSpace Search Introduction n n Expert










- Slides: 17

Go-Moku and Thread-Space Search

Introduction n n Expert Knowledge Threat-space search Result of Threat-space search Result

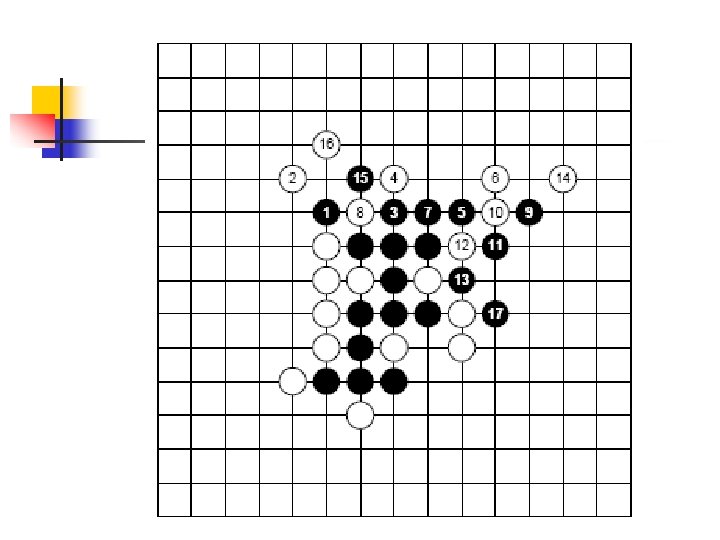
Expert Knowledge n n n Definitions and thread sequences Human expert analysis Computer programs’ strategies

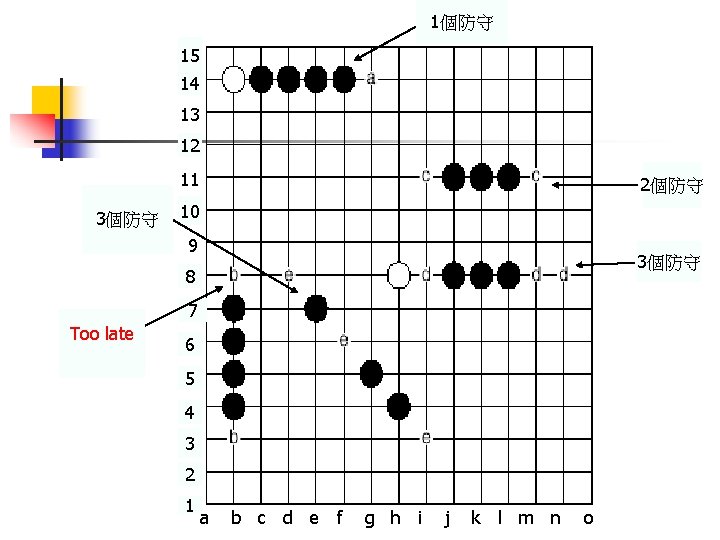
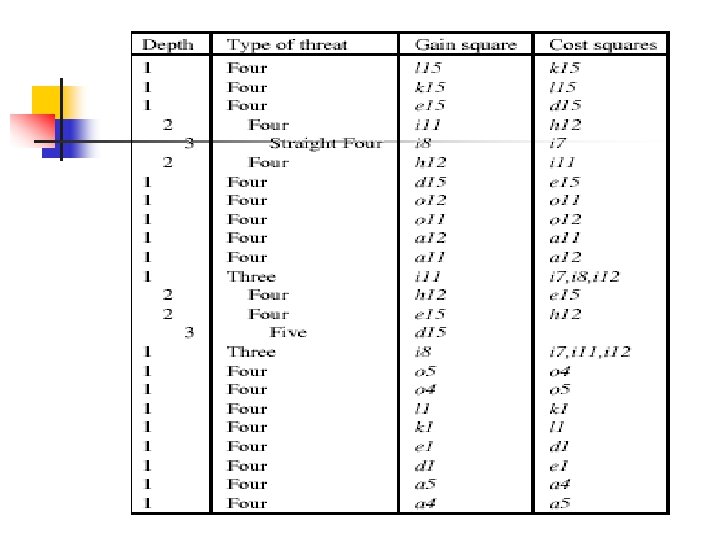
Definitions and thread sequences n n Threat Name: four(a) ; straight four(b); three(c, d) ; broken -three(e) To win: Creat a “double threat” Threat sequence Winning threat sequence: lead to double threat 必勝


1個防守 15 14 13 12 11 3個防守 2個防守 10 9 3個防守 8 7 Too late 6 5 4 3 2 1 a b c d e f g h i j k l m n o

Human expert analysis 1. Favorable place for attacking player & where? Based on feeling(long experience) 2. Defensive moves by opponent are disregarded 3. Try to find double threat sequence 4. The threat is failure to find other threat

Human expert analysis 5. When winning threat sequence appear, we can almost ignore defensive moves but “to care defensive four “

Computer programs’ strategies n n The strongest Gomoku program use The difference program: Poly: 20~30 ply depath search until n-ply using heuristic Vertex: Search depath of 16 ply + extended openning book

Threat-space search n n Several Notions Principle

Threat-space search n Several Notions: 1. gain square, cost square, rest sqaure 2. Threat A is dependent on threat B if rest square of A is gain square of B 3. Two dependency tree P&Q are in conflict

Threat-space search Principle: 1. Threat A& Threat B can’t be in the same tree (it mean that they can’t appear together) 2. Threat space search only include threat of attacker. When the threat can’t work , find another threat to attack. n

Threat-space search 15 14 13 12 11 10 9 8 7 6 5 4 3 2 1 a b c d e f g h i j k l m n o


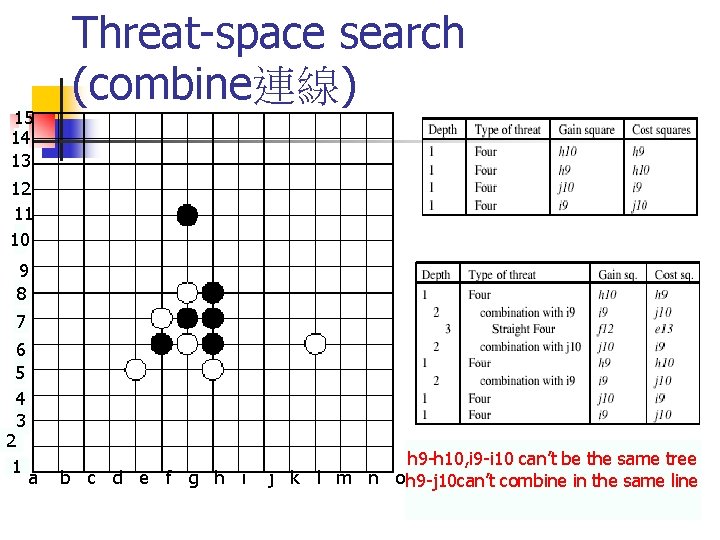
15 14 13 Threat-space search (combine連線) 12 11 10 9 8 7 6 5 4 3 2 1 a b c d e f g h i h 9 -h 10, i 9 -i 10 can’t be the same tree j k l m n oh 9 -j 10 can’t combine in the same line

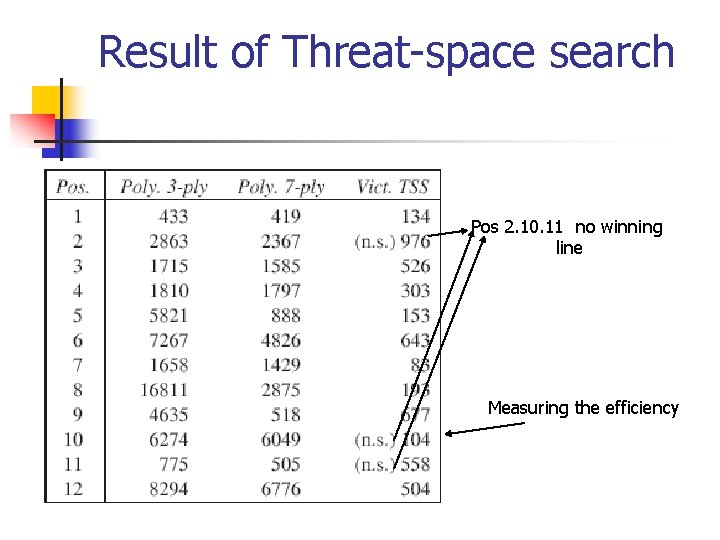
Result of Threat-space search Pos 2. 10. 11 no winning line Measuring the efficiency

Result n n Tree is split in few hundred subtree Stored in database All solution are in tree Solution are completeness in the tree