Gnutella The routing protocol for sharing data among
![Gnutella [The routing protocol for sharing data among peers] By -: Pallav Paliwal 11185 Gnutella [The routing protocol for sharing data among peers] By -: Pallav Paliwal 11185](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-1.jpg)
![[Motivation] l l 2 According to ivkovic reserch paper on P 2 P applications. [Motivation] l l 2 According to ivkovic reserch paper on P 2 P applications.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-2.jpg)
![[Motivation] l l 3 Working on this had definitely helped us in enhancing and [Motivation] l l 3 Working on this had definitely helped us in enhancing and](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-3.jpg)
![[Data Sharing Scenario. Traditional Approach] l Client –Server Architecture Data is shared between two [Data Sharing Scenario. Traditional Approach] l Client –Server Architecture Data is shared between two](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-4.jpg)
![[Data sharing scenario-P 2 P] l l l 5 Peer to Peer Architecture : [Data sharing scenario-P 2 P] l l l 5 Peer to Peer Architecture :](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-5.jpg)
![[Data sharing scenario – P 2 P] l l l 6 Nodes have awareness [Data sharing scenario – P 2 P] l l l 6 Nodes have awareness](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-6.jpg)
![[Peer –to –Peer Architecture] • No central Administration • Direct Communications • Distributed resources [Peer –to –Peer Architecture] • No central Administration • Direct Communications • Distributed resources](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-7.jpg)
![[Types of P 2 P Architecture] l When it comes to P 2 P [Types of P 2 P Architecture] l When it comes to P 2 P](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-8.jpg)
![[Centralized P 2 P Model] l Used by well known applications like Nepster. - [Centralized P 2 P Model] l Used by well known applications like Nepster. -](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-9.jpg)
![[Centralized P 2 P Model] Required - Network infrastructure of servers. - Data storage. [Centralized P 2 P Model] Required - Network infrastructure of servers. - Data storage.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-10.jpg)
![[Centralized Server P 2 P] Join Central Index Get Answer File Query 11 2/12/2022 [Centralized Server P 2 P] Join Central Index Get Answer File Query 11 2/12/2022](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-11.jpg)
![[Centralized P 2 P Model] Search Response With user 2 information File download Server [Centralized P 2 P Model] Search Response With user 2 information File download Server](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-12.jpg)
![[Centralized P 2 P Model] l l 13 Server allows query of their databases. [Centralized P 2 P Model] l l 13 Server allows query of their databases.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-13.jpg)
![[Advantages of centralized P 2 P] l l l 14 The existence of a [Advantages of centralized P 2 P] l l l 14 The existence of a](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-14.jpg)
![[Key Disadvantages- centralized P 2 P] The single entry point l possibility of the [Key Disadvantages- centralized P 2 P] The single entry point l possibility of the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-15.jpg)
![[Solution – Decentralized P 2 P] l l 16 Multiple points of entry in [Solution – Decentralized P 2 P] l l 16 Multiple points of entry in](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-16.jpg)
![[What is Gnutella] 17 l Gnutella is a decentralized P 2 P file-sharing model. [What is Gnutella] 17 l Gnutella is a decentralized P 2 P file-sharing model.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-17.jpg)
![[Gnutella –Working] l User starts with a networked computer that runs one of the [Gnutella –Working] l User starts with a networked computer that runs one of the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-19.jpg)
![[What is Gnutella] l Connect to another Gnutella-enabled networked computer. Node ‘B’ for example. [What is Gnutella] l Connect to another Gnutella-enabled networked computer. Node ‘B’ for example.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-20.jpg)
![[Gnutella – Working] l l l 21 Once the node A has announced its [Gnutella – Working] l l l 21 Once the node A has announced its](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-21.jpg)
![[Gnutella –Working] l l 22 when the Time- To-Live (TTL) packet information expires. At [Gnutella –Working] l l 22 when the Time- To-Live (TTL) packet information expires. At](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-22.jpg)
![[Gnutella- TTL (A closer look) ] TTL –Time to live, as in TCP/IP. l [Gnutella- TTL (A closer look) ] TTL –Time to live, as in TCP/IP. l](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-23.jpg)
![[Gnutella –TTL (A closer look) ] l l l 24 Low TTL means minimizing [Gnutella –TTL (A closer look) ] l l l 24 Low TTL means minimizing](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-24.jpg)
![[Gnutella Protocol Specifications] l l 25 All Gnutella communication happens on top of the [Gnutella Protocol Specifications] l l 25 All Gnutella communication happens on top of the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-25.jpg)
![[Gnutella Protocol Specifications] l l l 26 Any other response to the original connection [Gnutella Protocol Specifications] l l l 26 Any other response to the original connection](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-26.jpg)
![[Gnutella –Descriptors] l Ping: Used to actively discover hosts on the network. Servent receiving [Gnutella –Descriptors] l Ping: Used to actively discover hosts on the network. Servent receiving](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-27.jpg)
![[Gnutella –Descriptors] l l 28 Query hit The response to a Query, descriptor provides [Gnutella –Descriptors] l l 28 Query hit The response to a Query, descriptor provides](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-28.jpg)
![[Gnutella-Design] l The design consists of design of classes in the JAVA Environment. Why [Gnutella-Design] l The design consists of design of classes in the JAVA Environment. Why](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-29.jpg)
![[Gnutella-Design] There will be 4 main Classes 1. Node: For adding the node to [Gnutella-Design] There will be 4 main Classes 1. Node: For adding the node to](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-30.jpg)

![public static void main(String[] args) { System. out. println("<--- Monitor. Example running --->n"); if public static void main(String[] args) { System. out. println("<--- Monitor. Example running --->n"); if](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-34.jpg)
![[Gnutella-Design] l l l 38 The basic functionality of the Gnutella works on the [Gnutella-Design] l l l 38 The basic functionality of the Gnutella works on the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-38.jpg)
![[Gnutella-Design] l l l 39 Node class will take the port on which the [Gnutella-Design] l l l 39 Node class will take the port on which the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-39.jpg)
![[Gnutella-process model] 40 2/12/2022 [Gnutella-process model] 40 2/12/2022](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-40.jpg)
![[Gnutella-Design] l l 41 The various classes are used from this package which represents [Gnutella-Design] l l 41 The various classes are used from this package which represents](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-41.jpg)
![[Gnutella Design-DFD] Node IP/Port Host Existing Gnutella Network Web Cache Remote Host IP/Port Ping [Gnutella Design-DFD] Node IP/Port Host Existing Gnutella Network Web Cache Remote Host IP/Port Ping](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-42.jpg)
![[Gnutella Design-DFD] Search Keywords True/false File Server Query Hit Hash Table User 2 Download [Gnutella Design-DFD] Search Keywords True/false File Server Query Hit Hash Table User 2 Download](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-43.jpg)
![[Gnutella-Future] l l 44 We have designed the Gnutella Servant but peculiarity is that [Gnutella-Future] l l 44 We have designed the Gnutella Servant but peculiarity is that](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-44.jpg)
![[References Used] l l 45 A. Ghosh, M. Fry, J. Crowcroft: “An architecture for [References Used] l l 45 A. Ghosh, M. Fry, J. Crowcroft: “An architecture for](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-45.jpg)
![[references used] l 46 Unix Network Programming Networking API: Sockets and XTI. By W. [references used] l 46 Unix Network Programming Networking API: Sockets and XTI. By W.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-46.jpg)
![[ Ongoing research Proposals] Security in Peer to Peer Networks. l Protocol Enhancement Ideas. [ Ongoing research Proposals] Security in Peer to Peer Networks. l Protocol Enhancement Ideas.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-47.jpg)

- Slides: 48
![Gnutella The routing protocol for sharing data among peers By Pallav Paliwal 11185 Gnutella [The routing protocol for sharing data among peers] By -: Pallav Paliwal 11185](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-1.jpg)
Gnutella [The routing protocol for sharing data among peers] By -: Pallav Paliwal 11185 Vikas Chauhan 11044 1 2/12/2022
![Motivation l l 2 According to ivkovic reserch paper on P 2 P applications [Motivation] l l 2 According to ivkovic reserch paper on P 2 P applications.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-2.jpg)
[Motivation] l l 2 According to ivkovic reserch paper on P 2 P applications. “It is said that P 2 P file sharing holds great potential for the future. In addition, P 2 P networking could change the structure of the Internet from the webcentric to the purely distributed data model by allowing users that are accessing data from a particular web site to retrieve the cached copy of the data from a geographically closest point to their location”. 2/12/2022
![Motivation l l 3 Working on this had definitely helped us in enhancing and [Motivation] l l 3 Working on this had definitely helped us in enhancing and](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-3.jpg)
[Motivation] l l 3 Working on this had definitely helped us in enhancing and given us the opportunity to learn the new concept. Gnutella is very hot topic in current R&D world, as many giants like Intel and Microsoft are working together on it. 2/12/2022
![Data Sharing Scenario Traditional Approach l Client Server Architecture Data is shared between two [Data Sharing Scenario. Traditional Approach] l Client –Server Architecture Data is shared between two](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-4.jpg)
[Data Sharing Scenario. Traditional Approach] l Client –Server Architecture Data is shared between two computers by Installing the special server - where client make the request and the server processes the requests. l l Goal: High availability for Reads and Writes. Challenges: Malfunctioning of server-Shut downs cost involved in installing the specialized servers 4 2/12/2022
![Data sharing scenarioP 2 P l l l 5 Peer to Peer Architecture [Data sharing scenario-P 2 P] l l l 5 Peer to Peer Architecture :](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-5.jpg)
[Data sharing scenario-P 2 P] l l l 5 Peer to Peer Architecture : Peer to peer networks allows computers to communicate directly with each other and to share data among them. Cost effective No need for specialized server Flexible 2/12/2022
![Data sharing scenario P 2 P l l l 6 Nodes have awareness [Data sharing scenario – P 2 P] l l l 6 Nodes have awareness](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-6.jpg)
[Data sharing scenario – P 2 P] l l l 6 Nodes have awareness of other nodes. Peers create a virtual network. Each node can both act as client and server. Clients can leave or join the network any time without interrupting the overall functionality of the network. Over all performance of system increases as more nodes are added to network. 2/12/2022
![Peer to Peer Architecture No central Administration Direct Communications Distributed resources [Peer –to –Peer Architecture] • No central Administration • Direct Communications • Distributed resources](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-7.jpg)
[Peer –to –Peer Architecture] • No central Administration • Direct Communications • Distributed resources with different owners ->sites are autonomous. • In General : each peer has less resources then the server in the traditional Client-Server Model. 7 2/12/2022
![Types of P 2 P Architecture l When it comes to P 2 P [Types of P 2 P Architecture] l When it comes to P 2 P](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-8.jpg)
[Types of P 2 P Architecture] l When it comes to P 2 P - 2 types - Centralized P 2 P Model - Decentralized P 2 P Model 8 2/12/2022
![Centralized P 2 P Model l Used by well known applications like Nepster [Centralized P 2 P Model] l Used by well known applications like Nepster. -](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-9.jpg)
[Centralized P 2 P Model] l Used by well known applications like Nepster. - Nepster as a service allows the users to list the MP 3 –encoded music files they want to share. - Other users can download them through Nepster. 9 2/12/2022
![Centralized P 2 P Model Required Network infrastructure of servers Data storage [Centralized P 2 P Model] Required - Network infrastructure of servers. - Data storage.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-10.jpg)
[Centralized P 2 P Model] Required - Network infrastructure of servers. - Data storage. - corresponding bandwidth for allowing the large no. of user connections. l 10 2/12/2022
![Centralized Server P 2 P Join Central Index Get Answer File Query 11 2122022 [Centralized Server P 2 P] Join Central Index Get Answer File Query 11 2/12/2022](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-11.jpg)
[Centralized Server P 2 P] Join Central Index Get Answer File Query 11 2/12/2022
![Centralized P 2 P Model Search Response With user 2 information File download Server [Centralized P 2 P Model] Search Response With user 2 information File download Server](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-12.jpg)
[Centralized P 2 P Model] Search Response With user 2 information File download Server User 1 Search Query • uses central server – Directs traffic among users. • Maintains directories of data shared by the users. 12 2/12/2022 User 2
![Centralized P 2 P Model l l 13 Server allows query of their databases [Centralized P 2 P Model] l l 13 Server allows query of their databases.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-13.jpg)
[Centralized P 2 P Model] l l 13 Server allows query of their databases. Allows user to connect the other user who is actually sharing the file. Typically the connection is made by using the HTTP request –response mechanism. Actual transfer of data is done by users not by the server. 2/12/2022
![Advantages of centralized P 2 P l l l 14 The existence of a [Advantages of centralized P 2 P] l l l 14 The existence of a](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-14.jpg)
[Advantages of centralized P 2 P] l l l 14 The existence of a central index that allows users to search and find the desired files efficiently. The mandatory registration of all users of the system. Query reaches all users currently connected to the network. 2/12/2022
![Key Disadvantages centralized P 2 P The single entry point l possibility of the [Key Disadvantages- centralized P 2 P] The single entry point l possibility of the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-15.jpg)
[Key Disadvantages- centralized P 2 P] The single entry point l possibility of the entire network becoming incapacitated if main entry point is disabled (e. g. , Napster’s failure). l The invalid data in the database resulting from the periodical, not real time, refreshes of the data in the database. l 15 2/12/2022
![Solution Decentralized P 2 P l l 16 Multiple points of entry in [Solution – Decentralized P 2 P] l l 16 Multiple points of entry in](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-16.jpg)
[Solution – Decentralized P 2 P] l l 16 Multiple points of entry in the distributed model. No fear of failure of the system. Lack of registration in the decentralized network. Decreasing the breadth of data being queried. 2/12/2022
![What is Gnutella 17 l Gnutella is a decentralized P 2 P filesharing model [What is Gnutella] 17 l Gnutella is a decentralized P 2 P file-sharing model.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-17.jpg)
[What is Gnutella] 17 l Gnutella is a decentralized P 2 P file-sharing model. l Gnutella is simply is a routing protocol. To share files on the Gnutella –Network among peers in a Decentralized network environment. 2/12/2022

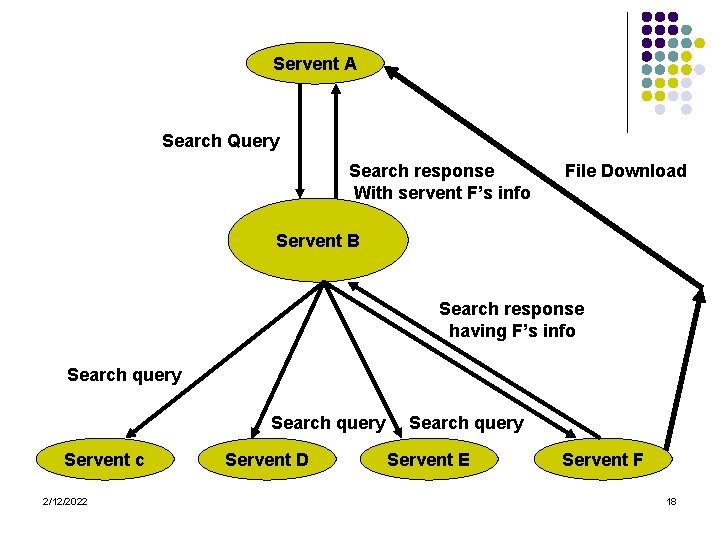
Servent A Search Query Search response With servent F’s info File Download Servent B Search response having F’s info Search query Servent c 2/12/2022 Servent D Search query Servent E Servent F 18
![Gnutella Working l User starts with a networked computer that runs one of the [Gnutella –Working] l User starts with a networked computer that runs one of the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-19.jpg)
[Gnutella –Working] l User starts with a networked computer that runs one of the Gnutella clients. (Node ‘A’ for example). 19 l This node will work both as a server and a client. l Generally referred to as a (Gnutella) “servant” (both a Server and a client). 2/12/2022
![What is Gnutella l Connect to another Gnutellaenabled networked computer Node B for example [What is Gnutella] l Connect to another Gnutella-enabled networked computer. Node ‘B’ for example.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-20.jpg)
[What is Gnutella] l Connect to another Gnutella-enabled networked computer. Node ‘B’ for example. l l l 20 ‘A’ will announce existence to ‘B’. Node ‘B’ will in turn announce to all its neighboring nodes. (nodes C, D, E, and F for example) ‘A’ is alive , pattern will continue recursively. 2/12/2022
![Gnutella Working l l l 21 Once the node A has announced its [Gnutella – Working] l l l 21 Once the node A has announced its](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-21.jpg)
[Gnutella – Working] l l l 21 Once the node A has announced its existence to the rest of the network user at this node can now query the contents of the data shared across the network. This announcement broadcasting ends - 2/12/2022
![Gnutella Working l l 22 when the Time ToLive TTL packet information expires At [Gnutella –Working] l l 22 when the Time- To-Live (TTL) packet information expires. At](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-22.jpg)
[Gnutella –Working] l l 22 when the Time- To-Live (TTL) packet information expires. At each level the TTL counter will be decreased by one from some initial value until it reaches zero. its broadcasting will stop. TTL is generally initialized by users. To prevent users from setting this initial TTL value too high, the majority of the Gnutella servents will refuse packets with excessively high TTL value. 2/12/2022
![Gnutella TTL A closer look TTL Time to live as in TCPIP l [Gnutella- TTL (A closer look) ] TTL –Time to live, as in TCP/IP. l](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-23.jpg)
[Gnutella- TTL (A closer look) ] TTL –Time to live, as in TCP/IP. l Signifies how much time the broadcasting of a message will occur. l Value should neither very low nor very high. l Servents should carefully scrutinize the TTL field of received descriptors and lower them as necessary. l Abuse of the TTL field will lead to an unnecessary amount of network traffic and poor network performance. l 23 2/12/2022
![Gnutella TTL A closer look l l l 24 Low TTL means minimizing [Gnutella –TTL (A closer look) ] l l l 24 Low TTL means minimizing](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-24.jpg)
[Gnutella –TTL (A closer look) ] l l l 24 Low TTL means minimizing the usage of the network resources. High TTL value means maximizing the Qo. S provided to the users of the network. The optimal TTL value would then (among others) depend on the network topology and traffic characteristics for a particular location and a particular time of the day. 2/12/2022
![Gnutella Protocol Specifications l l 25 All Gnutella communication happens on top of the [Gnutella Protocol Specifications] l l 25 All Gnutella communication happens on top of the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-25.jpg)
[Gnutella Protocol Specifications] l l 25 All Gnutella communication happens on top of the TCP/IP protocol. Once a TCP/IP connection is established between two servents. Servents send Gnutella connection string “GNUTELLA CONNECT/<protocol version string>nn”. The servent respond with a “GNUTELLA OKnn” message. 2/12/2022
![Gnutella Protocol Specifications l l l 26 Any other response to the original connection [Gnutella Protocol Specifications] l l l 26 Any other response to the original connection](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-26.jpg)
[Gnutella Protocol Specifications] l l l 26 Any other response to the original connection string taken as a communication-rejection by the initiator servent. After a connection is established- Two servents communicate by exchanging Gnutella protocol descriptors. Gnutella protocol also defines the rules for how these descriptors are exchanged between nodes. 2/12/2022
![Gnutella Descriptors l Ping Used to actively discover hosts on the network Servent receiving [Gnutella –Descriptors] l Ping: Used to actively discover hosts on the network. Servent receiving](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-27.jpg)
[Gnutella –Descriptors] l Ping: Used to actively discover hosts on the network. Servent receiving a Ping descriptor is expected to respond with one or more Pong descriptors. l Pong: The response to a Ping. Includes the address of a connected Gnutella servent. Information regarding the among of data it is making available to the network. l Query: The primary mechanism for searching the distributed network. A servent receiving a Query descriptor will respond with a Query. Hit if a match is found against its local data set. 27 2/12/2022
![Gnutella Descriptors l l 28 Query hit The response to a Query descriptor provides [Gnutella –Descriptors] l l 28 Query hit The response to a Query, descriptor provides](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-28.jpg)
[Gnutella –Descriptors] l l 28 Query hit The response to a Query, descriptor provides Recipient with enough information to acquire the data matching the corresponding Query Push A mechanism that allows a fire walled servent to contribute file-based data to the network. 2/12/2022
![GnutellaDesign l The design consists of design of classes in the JAVA Environment Why [Gnutella-Design] l The design consists of design of classes in the JAVA Environment. Why](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-29.jpg)
[Gnutella-Design] l The design consists of design of classes in the JAVA Environment. Why Java? -Good support for the Distributed Environment. -Socket programming is easy using java then in Unix. -Object oriented Structure -Reuse -The concepts of Java Beans etc make the code more portable. 29 2/12/2022
![GnutellaDesign There will be 4 main Classes 1 Node For adding the node to [Gnutella-Design] There will be 4 main Classes 1. Node: For adding the node to](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-30.jpg)
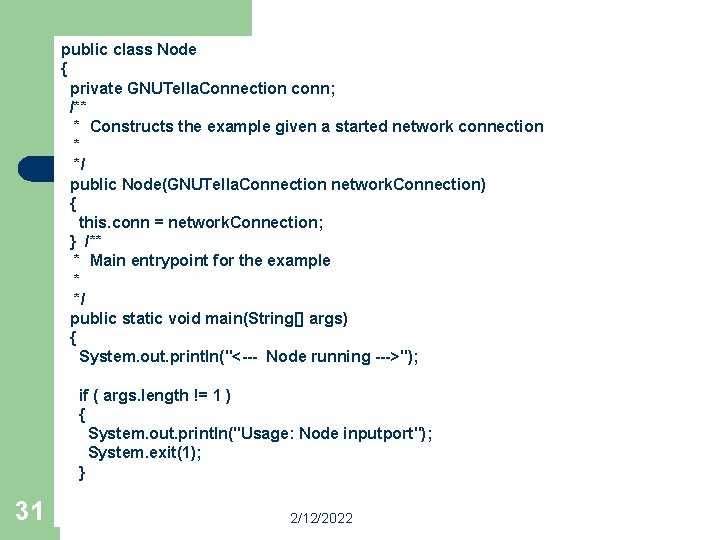
[Gnutella-Design] There will be 4 main Classes 1. Node: For adding the node to Gnutella Network 2. Monitor. Example For Monitoring the network like making connection exchanging the headers ping , pong etc. 3. File. Server. Example This is like the network share directory. 4. Search. Example For actually running the queries and queryhit if some match is found over the network. l 30 2/12/2022

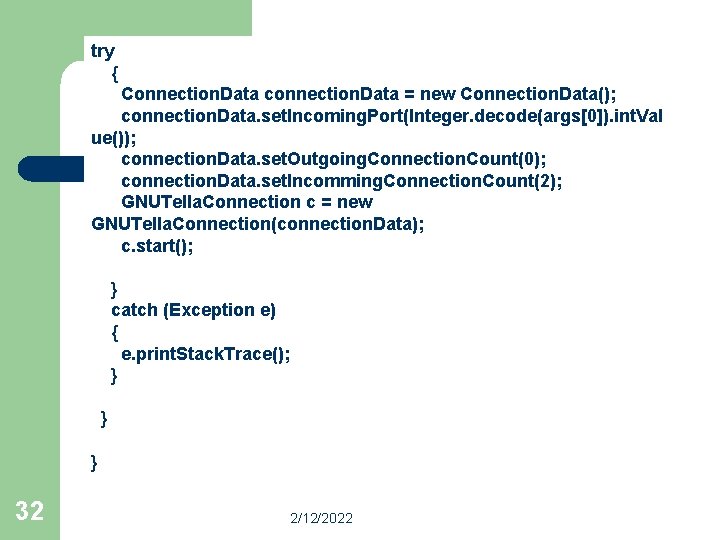
public class Node { private GNUTella. Connection conn; /** * Constructs the example given a started network connection * */ public Node(GNUTella. Connection network. Connection) { this. conn = network. Connection; } /** * Main entrypoint for the example * */ public static void main(String[] args) { System. out. println("<--- Node running --->"); if ( args. length != 1 ) { System. out. println("Usage: Node inputport"); System. exit(1); } 31 2/12/2022

try { Connection. Data connection. Data = new Connection. Data(); connection. Data. set. Incoming. Port(Integer. decode(args[0]). int. Val ue()); connection. Data. set. Outgoing. Connection. Count(0); connection. Data. set. Incomming. Connection. Count(2); GNUTella. Connection c = new GNUTella. Connection(connection. Data); c. start(); } catch (Exception e) { e. print. Stack. Trace(); } } } 32 2/12/2022

class for showing how to monitor search queries on the GNUTella network. The application expects two command ine parameters, the host name, and the port the servant is listening on public class Monitor. Example { private GNUTella. Connection conn; /** * Constructs the example given a started network connection * */ public Monitor. Example(GNUTella. Connection network. Connection) { this. conn = network. Connection; } /** * Main entrypoint for the example * */ 33 2/12/2022
![public static void mainString args System out println Monitor Example running n if public static void main(String[] args) { System. out. println("<--- Monitor. Example running --->n"); if](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-34.jpg)
public static void main(String[] args) { System. out. println("<--- Monitor. Example running --->n"); if (args. length != 2) { System. out. println("Usage: Monitor. Example host port"); System. exit(1); } try { System. out. println("Connecting to Gnutella Network. . . "); //------------------------------// Start a network connection and listen for succesful connection //------------------------------GNUTella. Connection c = new GNUTella. Connection(args[0], Integer. decode(args[1]). int. Value()); c. get. Search. Monitor. Session(new Test. Receiver()); c. start(); System. out. println("connected: "); 34 } 2/12/2022

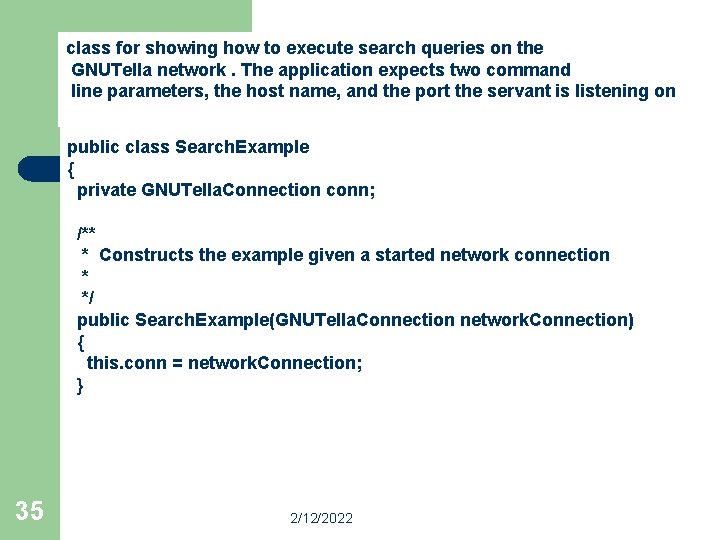
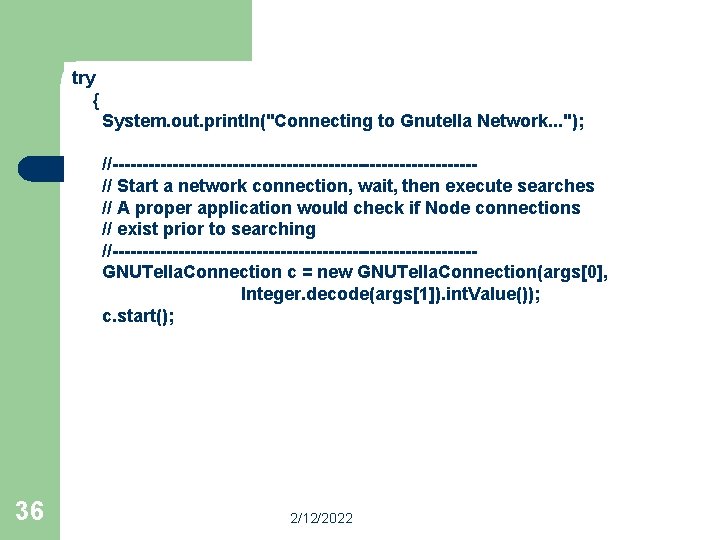
class for showing how to execute search queries on the GNUTella network. The application expects two command line parameters, the host name, and the port the servant is listening on public class Search. Example { private GNUTella. Connection conn; /** * Constructs the example given a started network connection * */ public Search. Example(GNUTella. Connection network. Connection) { this. conn = network. Connection; } 35 2/12/2022

try { System. out. println("Connecting to Gnutella Network. . . "); //------------------------------// Start a network connection, wait, then execute searches // A proper application would check if Node connections // exist prior to searching //------------------------------GNUTella. Connection c = new GNUTella. Connection(args[0], Integer. decode(args[1]). int. Value()); c. start(); 36 2/12/2022

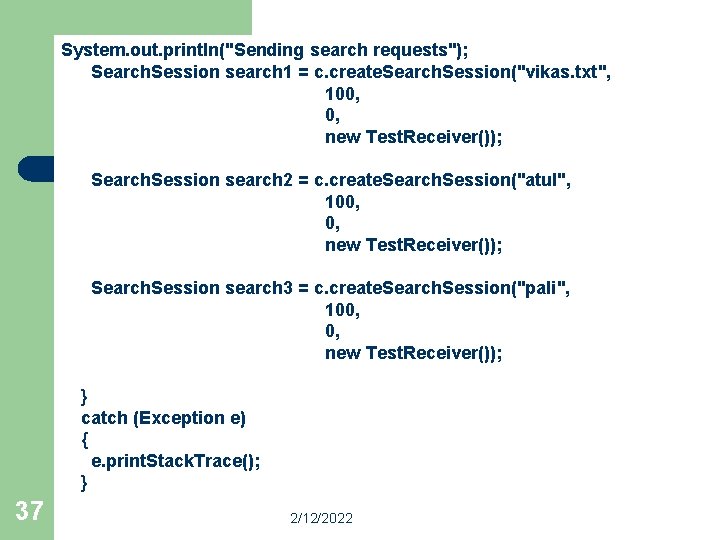
System. out. println("Sending search requests"); Search. Session search 1 = c. create. Search. Session("vikas. txt", 100, 0, new Test. Receiver()); Search. Session search 2 = c. create. Search. Session("atul", 100, 0, new Test. Receiver()); Search. Session search 3 = c. create. Search. Session("pali", 100, 0, new Test. Receiver()); } catch (Exception e) { e. print. Stack. Trace(); } 37 2/12/2022
![GnutellaDesign l l l 38 The basic functionality of the Gnutella works on the [Gnutella-Design] l l l 38 The basic functionality of the Gnutella works on the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-38.jpg)
[Gnutella-Design] l l l 38 The basic functionality of the Gnutella works on the top of TCP/IP and the Boot. Strapping. The boot strapping is the process in which we refer to GWeb. Cache for the list of known hosts which are connected to Gnutella Network at that point of time. These web caches are maintained over the Gnutella Supporting Societies like www. Gnutella. org Here we have to first fetch the list of known Gnutella servants then connect to network at a point like the address of known Gnutella Host. Then node class is run for declaring the existence of the node over the network. 2/12/2022
![GnutellaDesign l l l 39 Node class will take the port on which the [Gnutella-Design] l l l 39 Node class will take the port on which the](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-39.jpg)
[Gnutella-Design] l l l 39 Node class will take the port on which the node is listening the default port for Gnutella is 6346 or 6347. once the existence is declared the class Monitor. Example is run with the ip address and port as the command line input. This is the class where all the basics of connection making etc are done through the package proj. vikas. gnutella. 2/12/2022
![Gnutellaprocess model 40 2122022 [Gnutella-process model] 40 2/12/2022](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-40.jpg)
[Gnutella-process model] 40 2/12/2022
![GnutellaDesign l l 41 The various classes are used from this package which represents [Gnutella-Design] l l 41 The various classes are used from this package which represents](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-41.jpg)
[Gnutella-Design] l l 41 The various classes are used from this package which represents the inheritance in the object oriented model These are like connection class, connection data, ping, pong all the classes are made for modularity and ease for change in future. 2/12/2022
![Gnutella DesignDFD Node IPPort Host Existing Gnutella Network Web Cache Remote Host IPPort Ping [Gnutella Design-DFD] Node IP/Port Host Existing Gnutella Network Web Cache Remote Host IP/Port Ping](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-42.jpg)
[Gnutella Design-DFD] Node IP/Port Host Existing Gnutella Network Web Cache Remote Host IP/Port Ping User 1 User 2 Pong 42 2/12/2022 Add to list Host Alive
![Gnutella DesignDFD Search Keywords Truefalse File Server Query Hit Hash Table User 2 Download [Gnutella Design-DFD] Search Keywords True/false File Server Query Hit Hash Table User 2 Download](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-43.jpg)
[Gnutella Design-DFD] Search Keywords True/false File Server Query Hit Hash Table User 2 Download User 1 43 IP/Port user 2 Connection data 2/12/2022
![GnutellaFuture l l 44 We have designed the Gnutella Servant but peculiarity is that [Gnutella-Future] l l 44 We have designed the Gnutella Servant but peculiarity is that](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-44.jpg)
[Gnutella-Future] l l 44 We have designed the Gnutella Servant but peculiarity is that the functionality of the servant will depend over the various factors like Firewall, Proxies, GWeb. Cache avilability moreover more emphasis on the social acceptance. More research is can to be done on the field of security , authentication and the trust. 2/12/2022
![References Used l l 45 A Ghosh M Fry J Crowcroft An architecture for [References Used] l l 45 A. Ghosh, M. Fry, J. Crowcroft: “An architecture for](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-45.jpg)
[References Used] l l 45 A. Ghosh, M. Fry, J. Crowcroft: “An architecture for application layer routing”, Active Networks. Reserch paper on Peer-to-Peer Data Sharing Among Lab. VIEW Nodes. By Sadia Malik. WWW. aduni. org/courses. http: //www. rixsoft. com/Knowbuddy/gnutellafaq. html. 2/12/2022
![references used l 46 Unix Network Programming Networking API Sockets and XTI By W [references used] l 46 Unix Network Programming Networking API: Sockets and XTI. By W.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-46.jpg)
[references used] l 46 Unix Network Programming Networking API: Sockets and XTI. By W. Richard Stevens. volume 1, Second Edition. 2/12/2022
![Ongoing research Proposals Security in Peer to Peer Networks l Protocol Enhancement Ideas [ Ongoing research Proposals] Security in Peer to Peer Networks. l Protocol Enhancement Ideas.](https://slidetodoc.com/presentation_image_h2/b19c728cf03c9d6681cbd38a6442232b/image-47.jpg)
[ Ongoing research Proposals] Security in Peer to Peer Networks. l Protocol Enhancement Ideas. -Authentication and trust. -Using UDP instead of TCP/IP. l Gnutella Protocol Enhancements and security issues in the decentralized networks. l 47 2/12/2022

Thank you 48 2/12/2022