Glenn Allison Michael Ehrenhofer Dan Hoadley Joe Mathew






- Slides: 14

Glenn Allison Michael Ehrenhofer Dan Hoadley Joe Mathew Bryan Tabiadon Raj Varma Secure Computing Network Team Excel

Key Objective • Goal Create a secure computing platform which enhances collaboration across the enterprise • Strategy Provide wired and wireless network connectivity which is secure and easy to use • Tactics People – security awareness training Process – on-boarding, troubleshooting, escalation Technology – NAC, VPN, LDAP, WPA

Business Requirements Business • Add visitor, customer, and competitor access • Use non-company laptops on corporate network for internet and internal application use • Visitor access to internet, VPN • Wireless access Security • • Protect corporate Intellectual Property Principle of least privilege Patch and anti-virus required Wireless access to internal network prohibited

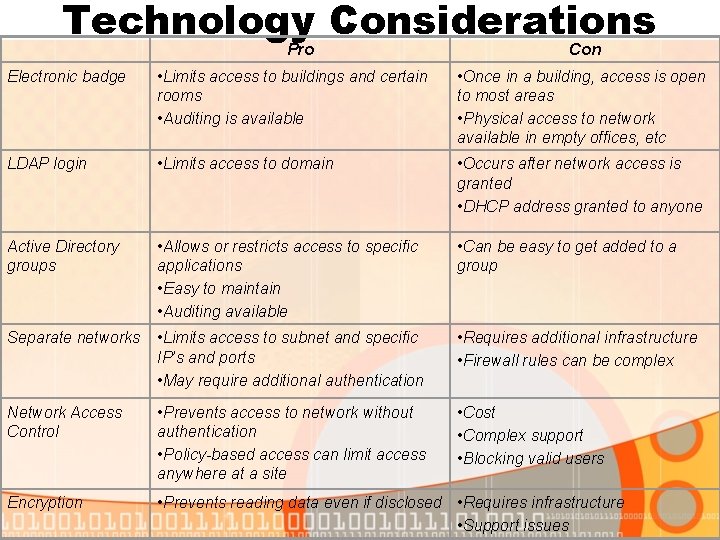
Technology Considerations Pro Con Electronic badge • Limits access to buildings and certain rooms • Auditing is available • Once in a building, access is open to most areas • Physical access to network available in empty offices, etc LDAP login • Limits access to domain • Occurs after network access is granted • DHCP address granted to anyone Active Directory groups • Allows or restricts access to specific applications • Easy to maintain • Auditing available • Can be easy to get added to a group Separate networks • Limits access to subnet and specific IP’s and ports • May require additional authentication • Requires additional infrastructure • Firewall rules can be complex Network Access Control • Prevents access to network without authentication • Policy-based access can limit access anywhere at a site • Cost • Complex support • Blocking valid users Encryption • Prevents reading data even if disclosed • Requires infrastructure • Support issues

Solution Overview • Physical security • Limit access via Electronic badge to single building • Active Directory Login (LDAP) • Required for Employee’s, Contractors, Customers • Not Required for Visitor access • Network Access Control • Implement at site level to prevent wandering • Use RADIUS authentication to integrate with Active Directory • Separate VLANs

Solution (cont. ) • Active Directory Groups • • Create Site Contractor groups Create Site Customer groups Use with NAC to limit access to network Use with Applications to limit access • Separate Visitors network for internet access • • Separate wireless physical infrastructure Eliminate network cables in conference rooms Employee’s VPN into Corporate network No login required

Solution (cont. ) • E-Mail Encryption • PKI certificates to support S/MIME • Encrypted 3 DES e-mail for secure internal communications and external communications when required • Policy • Documented and updated twice annually • Initial training required annual refresher • Procedures • Requires well documented troubleshooting steps • Help desk escalation • On and off-boarding must be accurate

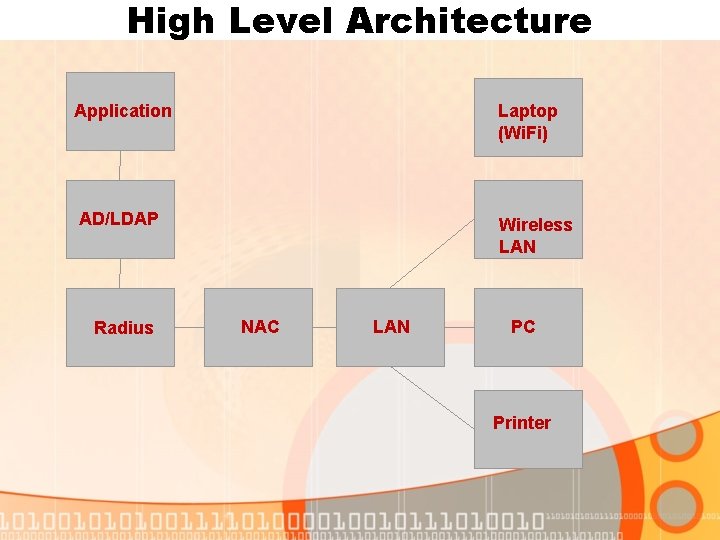
High Level Architecture Application Laptop (Wi. Fi) AD/LDAP Radius Wireless LAN NAC LAN PC Printer

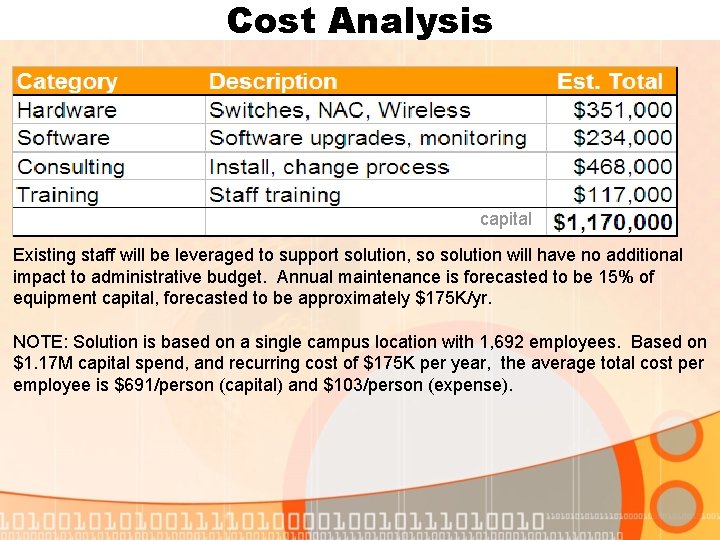
Cost Analysis capital Existing staff will be leveraged to support solution, so solution will have no additional impact to administrative budget. Annual maintenance is forecasted to be 15% of equipment capital, forecasted to be approximately $175 K/yr. NOTE: Solution is based on a single campus location with 1, 692 employees. Based on $1. 17 M capital spend, and recurring cost of $175 K per year, the average total cost per employee is $691/person (capital) and $103/person (expense).

Risks • Additional cost for infrastructure required • Complex environment supported by different groups • Never completely eliminated • Mitigation • • Implementation will require additional training Documentation, troubleshooting steps, escalation Senior level awareness Keep security top-of-mind awareness

Feasibility • People • Awareness training requirement • Change management • Process • Integration with existing process • Regular audits to validate compliance • Technology • Industry standard • Minimal customization

Compliance Key Driver is PCI Compliance, and ongoing SOX compliance • Monitoring Compliance • Internal audits • External audits • Change Control • All changes to infrastructure reviewed and measured with formal change control

Considerations • Solution can be adjusted for different level of risk industries • Confidentiality • Integrity • Availability • Authenticity

Questions?