Git Flow Flow Revision Control for Software Defined




- Slides: 11

Git. Flow: Flow Revision Control for Software. Defined Networks Abhishek Dwaraki 1 Srini Seetharaman 2, Sriram Natarajan 3, Tilman Wolf 1 1. Department of Electrical and Computer Engineering, University of Massachusetts, Amherst, MA, USA 2. Infinera Inc. , San Francisco, CA, USA 3. Deutsche Telekom Inc. , Silicon Valley Innovation Center, Mountain View, CA, USA This material is based upon work supported by the National Science Foundation under Grant No. 1421448 Department of Electrical and Computer Engineering

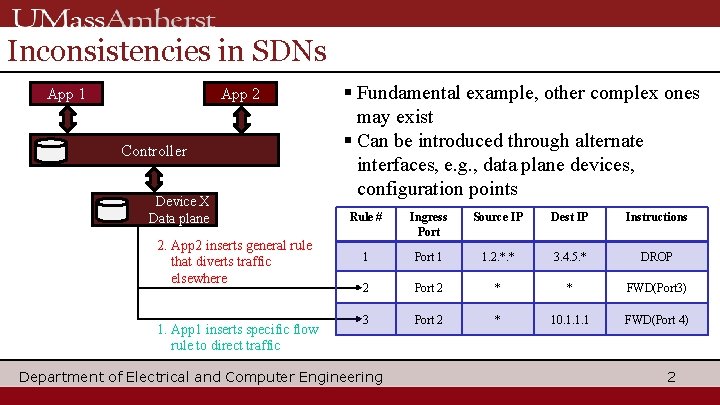
Inconsistencies in SDNs App 1 App 2 Controller Device X Data plane 2. App 2 inserts general rule that diverts traffic elsewhere 1. App 1 inserts specific flow rule to direct traffic § Fundamental example, other complex ones may exist § Can be introduced through alternate interfaces, e. g. , data plane devices, configuration points Rule # Ingress Port Source IP Dest IP Instructions 1 Port 1 1. 2. *. * 3. 4. 5. * DROP 2 Port 2 * * FWD(Port 3) 3 Port 2 * 10. 1. 1. 1 FWD(Port 4) Department of Electrical and Computer Engineering 2

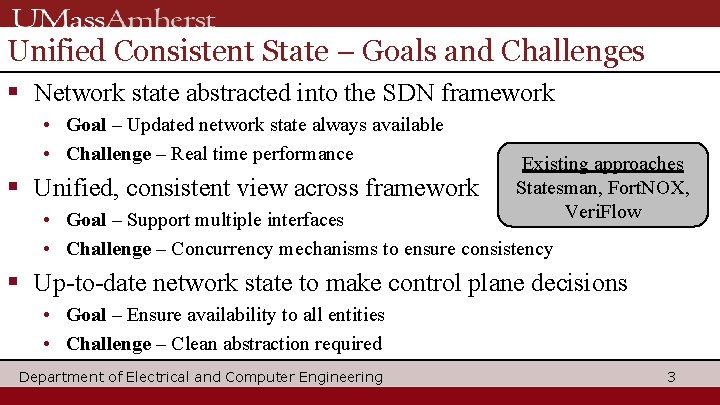
Unified Consistent State – Goals and Challenges § Network state abstracted into the SDN framework • Goal – Updated network state always available • Challenge – Real time performance § Unified, consistent view across framework Existing approaches Statesman, Fort. NOX, Veri. Flow • Goal – Support multiple interfaces • Challenge – Concurrency mechanisms to ensure consistency § Up-to-date network state to make control plane decisions • Goal – Ensure availability to all entities • Challenge – Clean abstraction required Department of Electrical and Computer Engineering 3

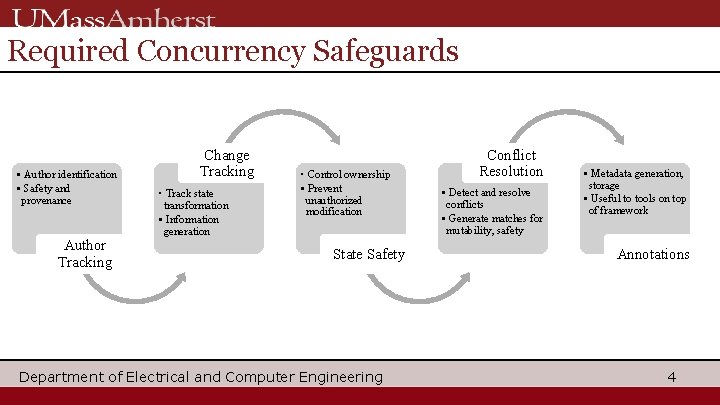
Required Concurrency Safeguards • Author identification • Safety and provenance Author Tracking Change Tracking • Track state transformation • Information generation • Control ownership • Prevent unauthorized modification State Safety Department of Electrical and Computer Engineering Conflict Resolution • Detect and resolve conflicts • Generate matches for mutability, safety • Metadata generation, storage • Useful to tools on top of framework Annotations 4

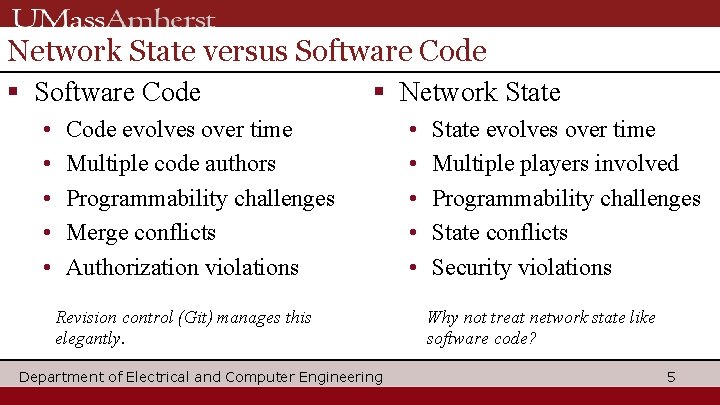
Network State versus Software Code § Software Code • • • § Network State Code evolves over time Multiple code authors Programmability challenges Merge conflicts Authorization violations Revision control (Git) manages this elegantly. Department of Electrical and Computer Engineering • • • State evolves over time Multiple players involved Programmability challenges State conflicts Security violations Why not treat network state like software code? 5

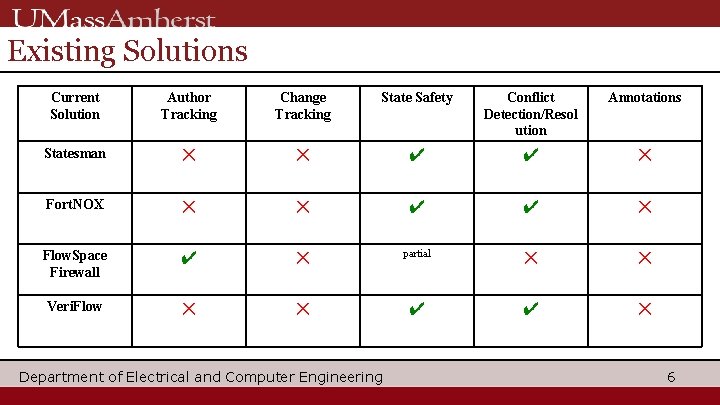
Existing Solutions Current Solution Author Tracking Change Tracking State Safety Conflict Detection/Resol ution Annotations Statesman ✕ ✕ ✔ ✔ ✕ Fort. NOX ✕ ✕ ✔ ✔ ✕ Flow. Space Firewall ✔ ✕ partial ✕ ✕ Veri. Flow ✕ ✕ ✔ ✔ ✕ Department of Electrical and Computer Engineering 6

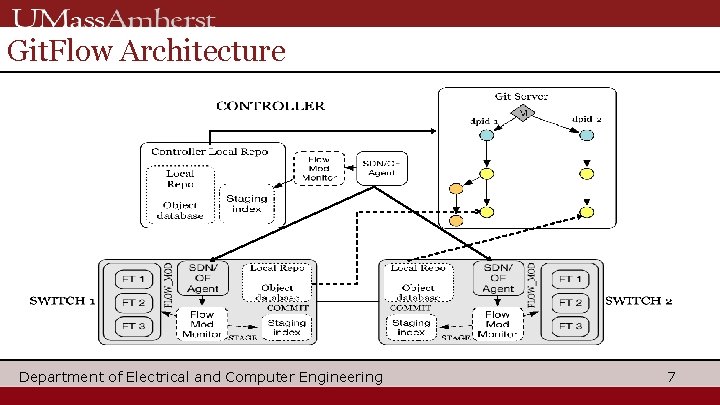
Git. Flow Architecture Department of Electrical and Computer Engineering 7

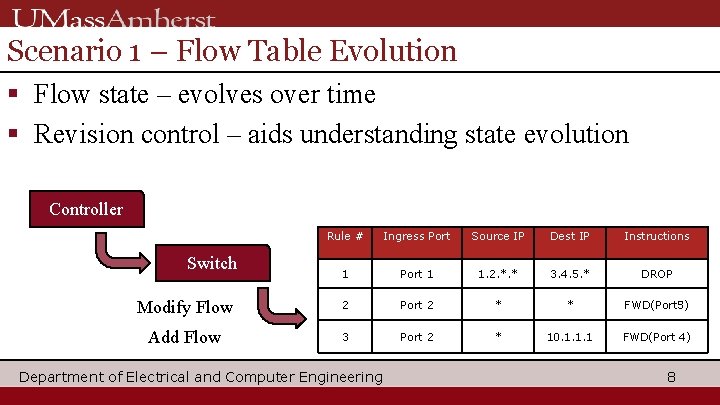
Scenario 1 – Flow Table Evolution § Flow state – evolves over time § Revision control – aids understanding state evolution Controller Rule # Ingress Port Source IP Dest IP Instructions 1 Port 1 1. 2. *. * 3. 4. 5. * DROP Modify Flow 2 Port 2 * * FWD(Port 3) FWD(Port 5) Add Flow 3 Port 2 * 10. 1. 1. 1 FWD(Port 4) Switch Department of Electrical and Computer Engineering 8

Scenario 2 – Identifying security violations § Malicious updates affect packet forwarding behavior § AAA – vets applications/bundles for malicious activity § Revision control + AAA = higher security • Revision control – can identify when what was changed and who authorized it • AAA – corrective measures to ensure secure operation in future Department of Electrical and Computer Engineering 9

Scenario 3 – Troubleshooting § Previous approaches - identify errant states, cannot prevent reoccurrence § Revision control – can avoid transitions to errant states using annotations § Networks as autonomous entities • What is important - Self-healing • How it is achieved - automated troubleshooting tools • How can revision control help - exercising more intricate level of inspection Department of Electrical and Computer Engineering 10

Summary § § § Inconsistencies exist in network state information Revision control is a comprehensive solution Treat network state like code/files revision and abstract Revision control provides required concurrency guarantees Very relevant use cases in state evolution, troubleshooting Please refer paper for more details Department of Electrical and Computer Engineering 11