Getting Connected Chapter 2 Part 1 Networking CS
















- Slides: 35

Getting Connected (Chapter 2 Part 1) Networking CS 3470, Section 1 Sarah Diesburg

Five Problems Encoding/decoding Framing Error Detection Error Correction Media Access

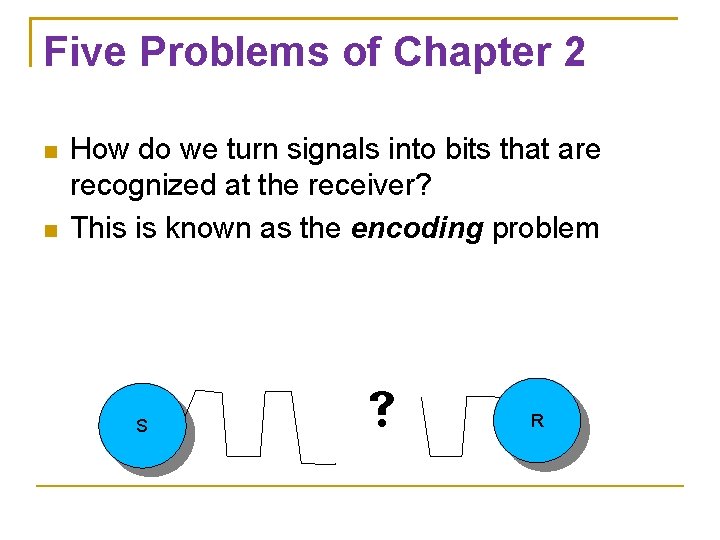
Five Problems of Chapter 2 How do we turn signals into bits that are recognized at the receiver? This is known as the encoding problem S R

Five Problems of Chapter 2 Delineating the sequence of bits into complete messages is called framing. When does a frame start? Byte-oriented Bit-oriented Clock-based

Five Problems of Chapter 2 Data verification Has the data been corrupted? If data has been corrupted, can we take the appropriate action? This is the error detection problem. CRC 2 -D parity Checksums

Five Problems of Chapter 2 Error Recovery Frames that are damaged will need to be retransmitted. This is the reliability problem ARQ Stop and wait Sliding window Concurrent channels

Five Problems of Chapter 2 How do you arbitrate, or self-regulate access to a shared link? This is the media-access problem Ethernet Token Ring Wireless

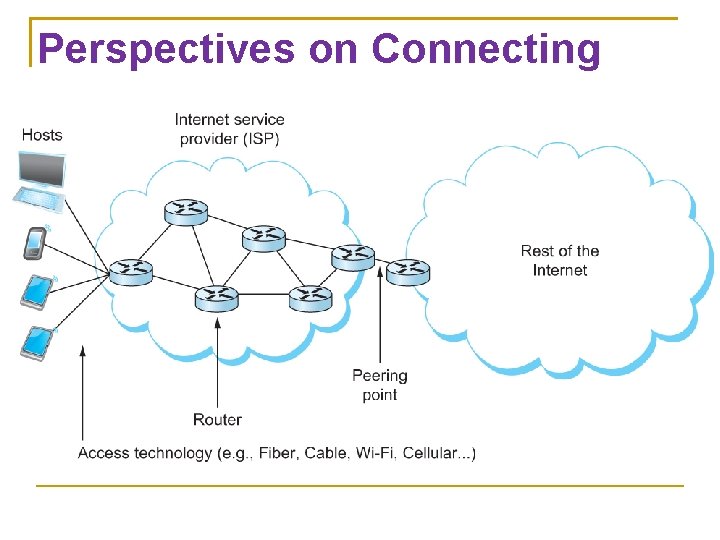
Perspectives on Connecting

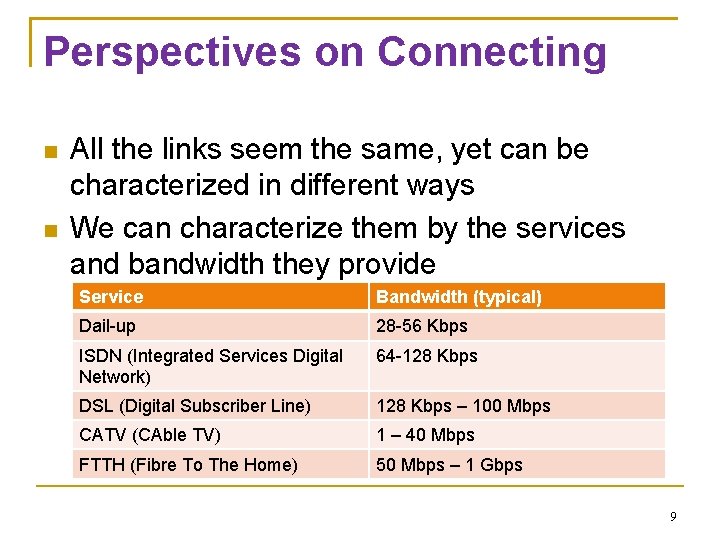
Perspectives on Connecting All the links seem the same, yet can be characterized in different ways We can characterize them by the services and bandwidth they provide Service Bandwidth (typical) Dail-up 28 -56 Kbps ISDN (Integrated Services Digital Network) 64 -128 Kbps DSL (Digital Subscriber Line) 128 Kbps – 100 Mbps CATV (CAble TV) 1 – 40 Mbps FTTH (Fibre To The Home) 50 Mbps – 1 Gbps 9

Perspectives on Connecting Another way to characterize links is by their physical makeup Copper – DSL, coaxial, cat 5 e/cat 6 cables Optical fiber – FTTH Air – Wireless 10

Links We care about electromagnetic waves These links provide the foundation to propagate binary information/bits (0’s and 1’s) – otherwise known as encoding 11

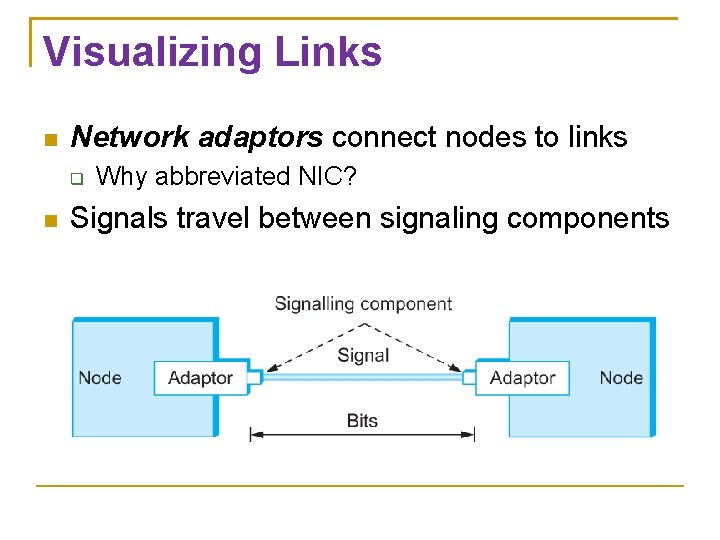
Visualizing Links Network adaptors connect nodes to links Why abbreviated NIC? Signals travel between signaling components

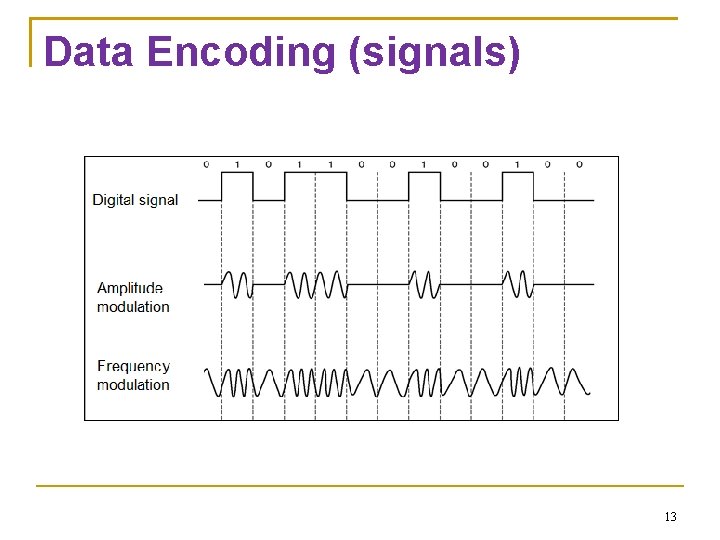
Data Encoding (signals) 13

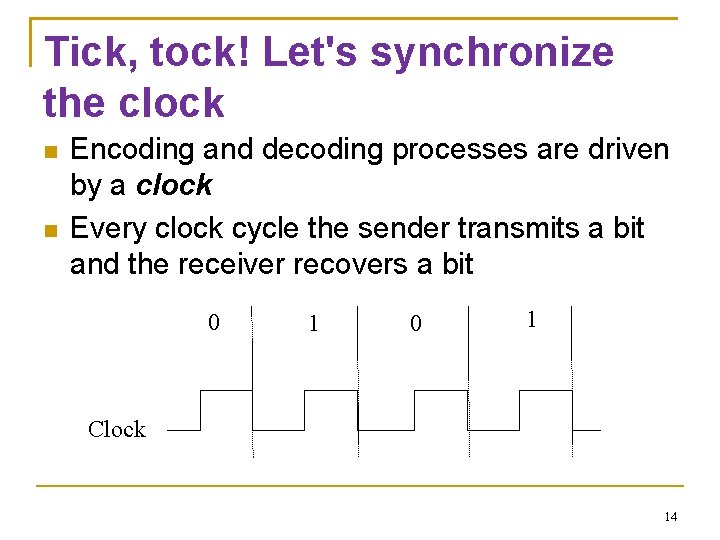
Tick, tock! Let's synchronize the clock Encoding and decoding processes are driven by a clock Every clock cycle the sender transmits a bit and the receiver recovers a bit 0 1 Clock 14

Encoding schemes NRZ (Non-return to zero) NRZI (Non-return to zero inverted) Manchester 4 B/5 B

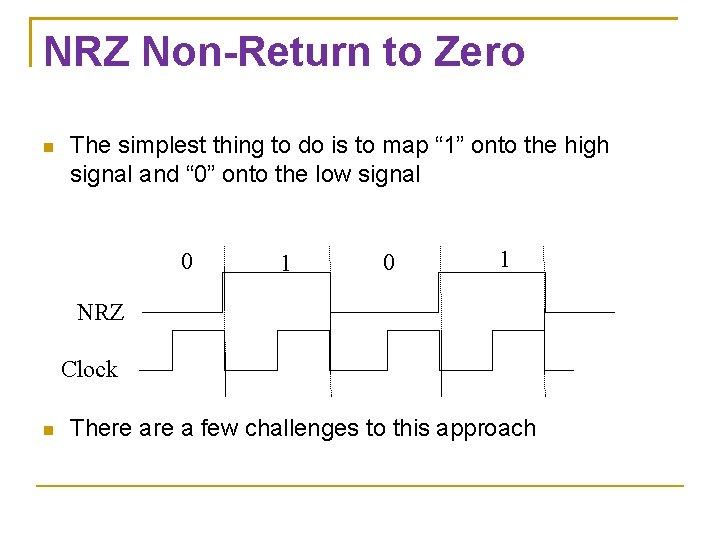
NRZ Non-Return to Zero The simplest thing to do is to map “ 1” onto the high signal and “ 0” onto the low signal 0 1 NRZ Clock There a few challenges to this approach

NRZ Non-Return to Zero Baseline Wander caused by signal averaging Receiver keeps average of signal it has received so far and uses average to distinguish highs and lows Problem occurs when to many consecutive 1’s or 0’s cause average to change 17

NRZ Non-Return to Zero Clock recovery required when signal remains constant too long Receiver uses high-low transitions to mark the clock boundaries What happens when we send a lot of consecutive 1’s or 0’s? 18

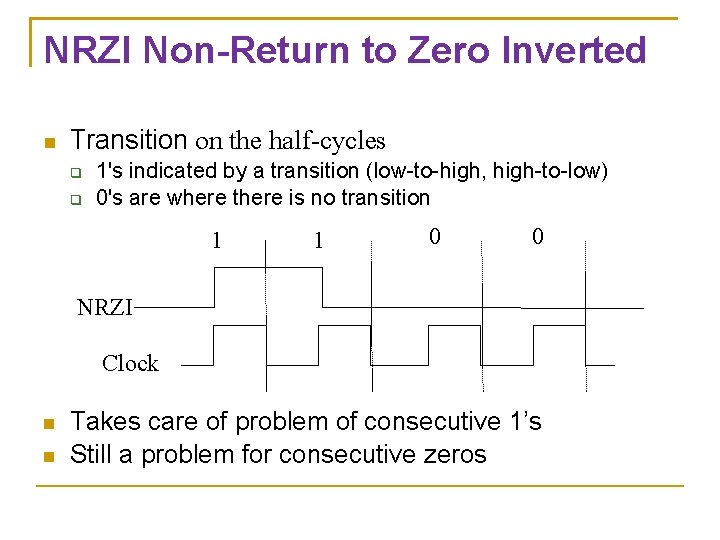
NRZI Non-Return to Zero Inverted Transition on the half-cycles 1's indicated by a transition (low-to-high, high-to-low) 0's are where there is no transition 1 1 0 0 NRZI Clock Takes care of problem of consecutive 1’s Still a problem for consecutive zeros

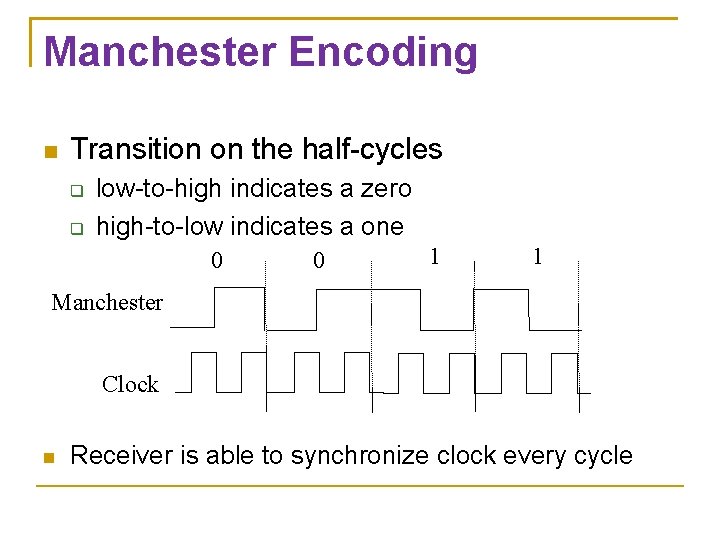
Manchester Encoding Transition on the half-cycles low-to-high indicates a zero high-to-low indicates a one 0 0 1 1 Manchester Clock Receiver is able to synchronize clock every cycle

Baud rate The baud rate is the rate at which the signal changes The bit rate is the rate at which you can transmit information For the same baud rate, NRZ and NRZI have twice the bit rate as Manchester.

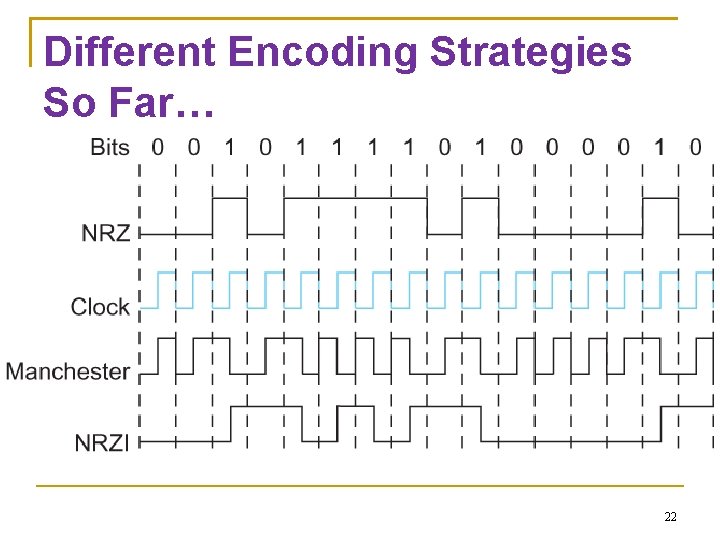
Different Encoding Strategies So Far… 22

4 B/5 B encoding 4 -bit payload in a 5 -bit gift box Goal is to improve upon Manchester (50% efficiency), but to avoid baseline wander and clock drift Insert extra bits into bit stream to break up long sequences of 0’s and 1’s 5 -bit codes selected such that there are never more than three consecutive zero's. Resulting codes transmitted through NRZI encoding

4 B/5 B 5 bits (32 patterns) to represent 4 bits (16 patterns) 5 -bit patterns with no more than 1 leading zero 5 -bit patterns with no more than 2 trailing zero's 16 leftovers 7 not valid Others control signals 11111 (idle) 00000 (dead) 00100 (bad)

Framing We know how to transmit bits on a link between two nodes Now we need to figure out how to send distinct messages in frames (Think packets at the link layer) Why would we want to break up messages into frames instead of just a bit stream? 25

Framing Protocols Bi-sync HDLC PPP SONET Framing Approaches Sentinel Approach Byte-counting approach

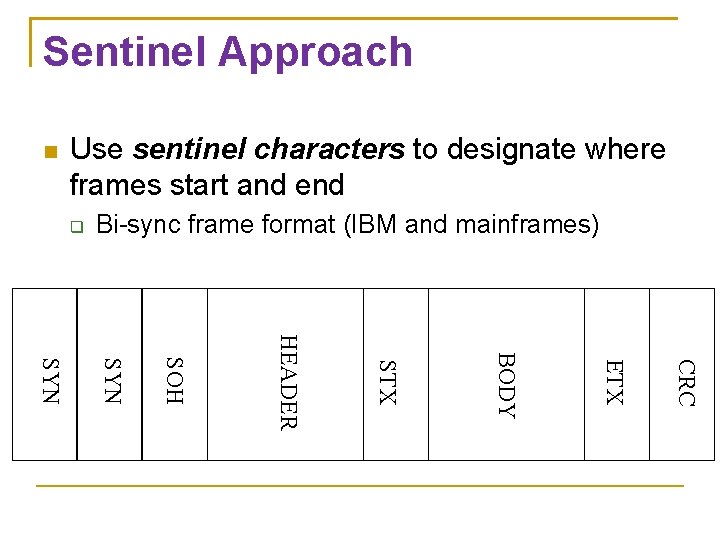
Sentinel Approach Use sentinel characters to designate where frames start and end Bi-sync frame format (IBM and mainframes) CRC ETX BODY STX HEADER SOH SYN

Sentinel Approach SYN STX End of Text SOH Start of Text ETX Synchronization Start of Header (Why no EOH? ) CRC Cyclic Redundancy Check

Character Stuffing How do you handle the situation where the body contains STX, ETX, SOH, etc? Escape out ETX with at Data Link Escape Character (DLE) Now, how do you deal with a body that has a DLE in it? Also known as character stuffing Examples in programming

Byte-counting Protocols Just like with C strings, we can detect the end of the string in two ways Special character An extra length field Same is true in framing In the byte-counting approach, we detect the end of the frame with an extra “Count” field 30

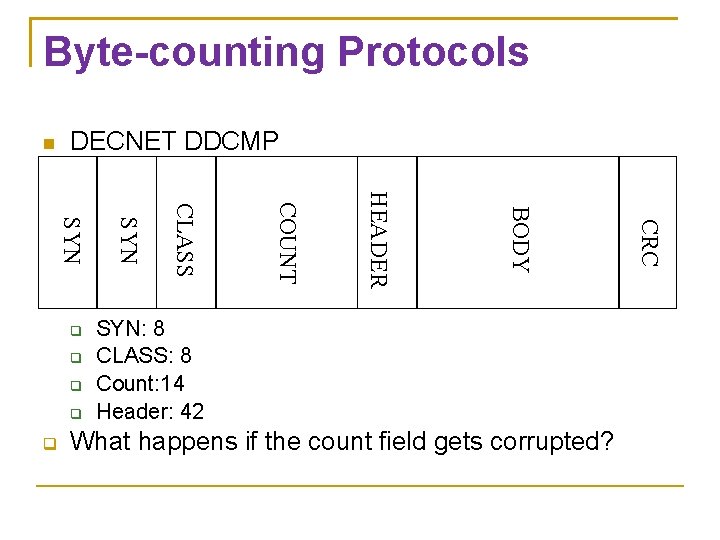
Byte-counting Protocols DECNET DDCMP SYN: 8 CLASS: 8 Count: 14 Header: 42 What happens if the count field gets corrupted? CRC BODY HEADER COUNT CLASS SYN

Bit-oriented Protocols Unlike byte-oriented protocols, these protocols don’t care about bytes Could be transmitting ASCII (7 -bits) Pixel values in an image … 32

Bit-oriented Protocols High-Level Data Link Control (HDLC) protocol Denotes beginning and end of a frame with the delimiter: 0 1 1 1 0 Also transmitted anytime link is idle to keep clocks synchronized Still has bit stuffing problem if special delimiter occurs in body 5 1's; zero ALWAYS follows in the body.

. . . and then there's Sonet Synchronous Optical Network standard Dominant standard for long-distance transmission of data over optical networks Every frame is exactly the same size! Has some special bit pattern to tell receiver where frame starts and ends, with no bit stuffing 34

Sonet How does the receiver know where each frame starts and ends? Receiver looks for it consistently (once every fixed number of bytes) Encoded using NRZ To combat NRZ clock recovery problem, XORs data to be transmitted to a well-known bit patten Can XOR encoded data with well-known bit pattern to decode 35