Getting Ahead Integrating Development and Response for Improved










- Slides: 19

Getting Ahead: Integrating Development and Response for Improved Security Steven B. Lipner Director of Security Engineering Strategy Security Business and Technology Unit Microsoft Corporation

Engineering excellence Security development lifecycle Microsoft Security Response Center Sharing best practices with administrators and developers

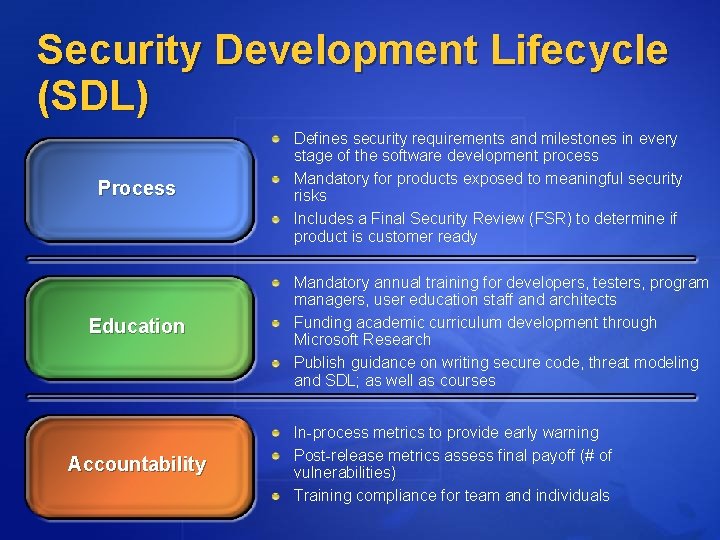
Security Development Lifecycle (SDL) Process Education Accountability Defines security requirements and milestones in every stage of the software development process Mandatory for products exposed to meaningful security risks Includes a Final Security Review (FSR) to determine if product is customer ready Mandatory annual training for developers, testers, program managers, user education staff and architects Funding academic curriculum development through Microsoft Research Publish guidance on writing secure code, threat modeling and SDL; as well as courses In-process metrics to provide early warning Post-release metrics assess final payoff (# of vulnerabilities) Training compliance for team and individuals


Final Security Review (FSR) “From a security viewpoint, is this software ready to deliver to customers? ” Two to six months prior to software completion, depending on the scope of the software. Software must be in a stable state with only minimal non-security changes expected prior to release FSR results: If the FSR finds a pattern of remaining vulnerabilities, the proper response is not just to fix the vulnerabilities found, but to revisit the earlier phases and take pointed actions to address root causes (e. g. , improve training, enhance tools)

Education for the SDL

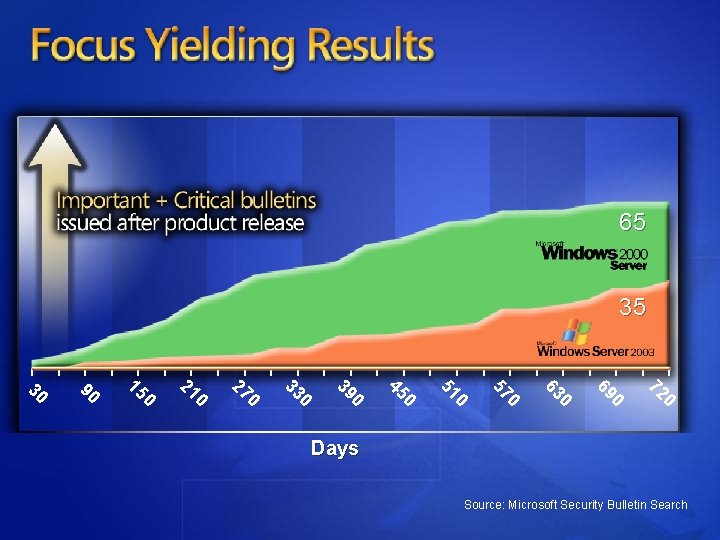
65 35 0 72 0 69 0 63 0 57 0 51 0 45 0 39 0 33 0 27 0 21 0 15 90 30 Days Source: Microsoft Security Bulletin Search

SQL Server 2000 2002 -2005 (YTD)

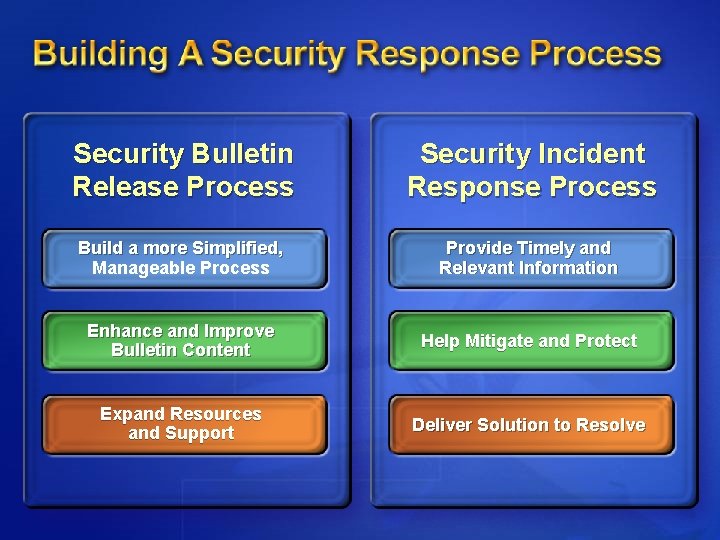
Security Bulletin Release Process Security Incident Response Process Build a more Simplified, Manageable Process Provide Timely and Relevant Information Enhance and Improve Bulletin Content Help Mitigate and Protect Expand Resources and Support Deliver Solution to Resolve

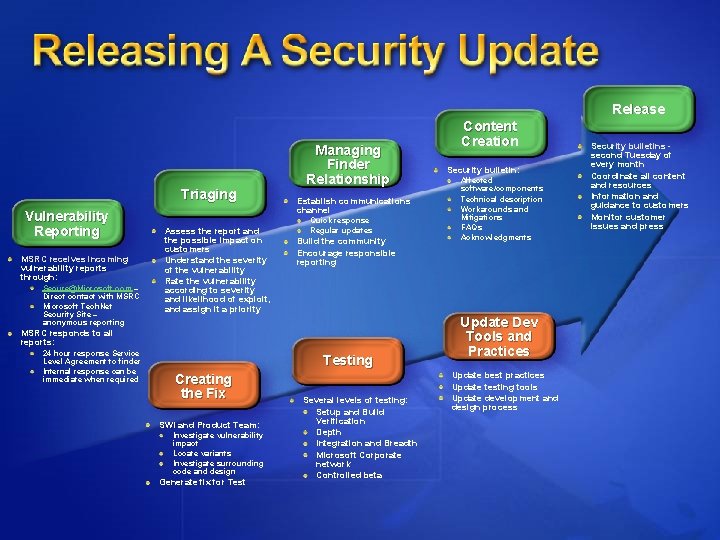
Release Triaging Vulnerability Reporting MSRC receives incoming vulnerability reports through: Secure@Microsoft. com – Direct contact with MSRC Microsoft Tech. Net Security Site – anonymous reporting Assess the report and the possible impact on customers Understand the severity of the vulnerability Rate the vulnerability according to severity and likelihood of exploit, and assign it a priority Managing Finder Relationship Establish communications channel Quick response Regular updates Build the community Encourage responsible reporting MSRC responds to all reports: 24 hour response Service Level Agreement to finder Internal response can be immediate when required Testing Creating the Fix SWI and Product Team: Investigate vulnerability impact Locate variants Investigate surrounding code and design Generate fix for Test Several levels of testing: Setup and Build Verification Depth Integration and Breadth Microsoft Corporate network Controlled beta Content Creation Security bulletin: Affected software/components Technical description Workarounds and Mitigations FAQs Acknowledgments Update Dev Tools and Practices Update best practices Update testing tools Update development and design process Security bulletins second Tuesday of every month Coordinate all content and resources Information and guidance to customers Monitor customer issues and press

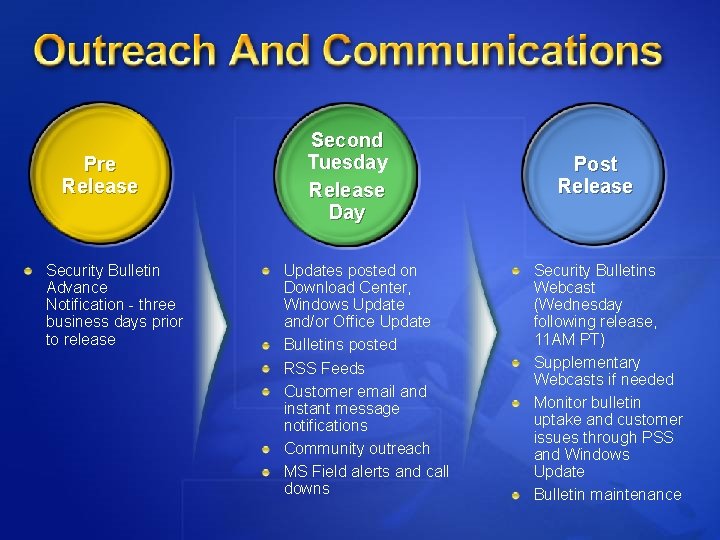
Pre Release Security Bulletin Advance Notification - three business days prior to release Second Tuesday Release Day Updates posted on Download Center, Windows Update and/or Office Update Bulletins posted RSS Feeds Customer email and instant message notifications Community outreach MS Field alerts and call downs Post Release Security Bulletins Webcast (Wednesday following release, 11 AM PT) Supplementary Webcasts if needed Monitor bulletin uptake and customer issues through PSS and Windows Update Bulletin maintenance

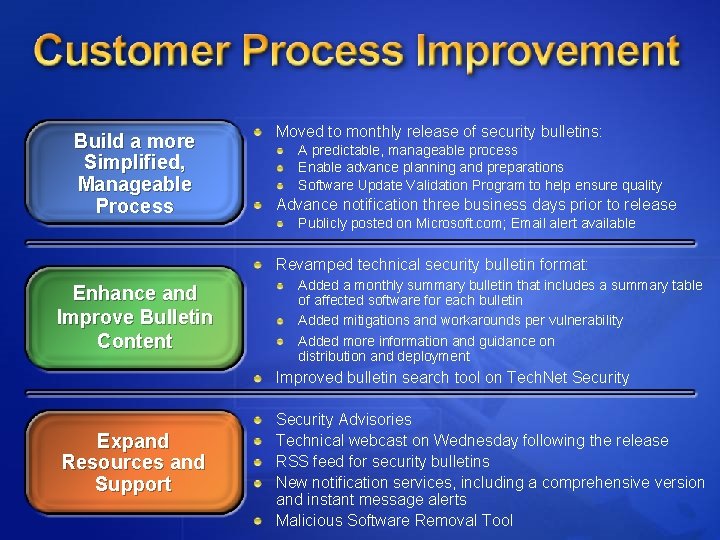
Build a more Simplified, Manageable Process Moved to monthly release of security bulletins: A predictable, manageable process Enable advance planning and preparations Software Update Validation Program to help ensure quality Advance notification three business days prior to release Publicly posted on Microsoft. com; Email alert available Revamped technical security bulletin format: Enhance and Improve Bulletin Content Added a monthly summary bulletin that includes a summary table of affected software for each bulletin Added mitigations and workarounds per vulnerability Added more information and guidance on distribution and deployment Improved bulletin search tool on Tech. Net Security Expand Resources and Support Security Advisories Technical webcast on Wednesday following the release RSS feed for security bulletins New notification services, including a comprehensive version and instant message alerts Malicious Software Removal Tool

Security Advisories Supplement Microsoft Security Bulletins Content More information Provide guidance and information about security related software changes or software updates Some examples of future topics may include: "Defense in Depth" security enhancements or changes unrelated to security vulnerabilities Guidance and mitigations that may be applicable for publicly disclosed vulnerabilities Top level summary detailing the reason for issuing the advisory Frequently asked questions Suggested actions May be updated any time we have new information Reference a unique Knowledge Base Article number for additional information Sign up for the Security Notification Service Comprehensive Edition at www. microsoft. com/technet/security/bulletin/notify. mspx www. microsoft. com/technet/security/advisory

SSIRP - Software Security Incident Response Plan Companywide process to deal with critical security threats Mobilize Microsoft resources worldwide Goals: Quickly gain a thorough understanding of the problem Provide customers with timely, relevant, consistent information Deliver tools, security updates and other assistance to restore normal operation

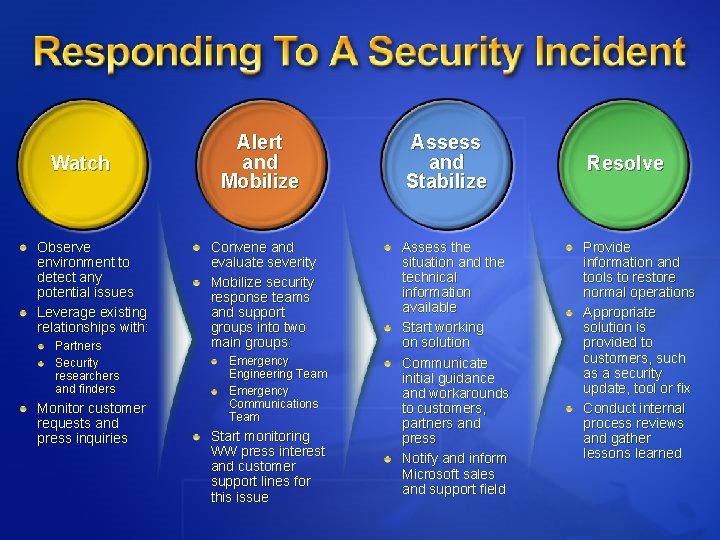
Watch Observe environment to detect any potential issues Leverage existing relationships with: Partners Security researchers and finders Monitor customer requests and press inquiries Alert and Mobilize Convene and evaluate severity Mobilize security response teams and support groups into two main groups: Emergency Engineering Team Emergency Communications Team Start monitoring WW press interest and customer support lines for this issue Assess and Stabilize Assess the situation and the technical information available Start working on solution Communicate initial guidance and workarounds to customers, partners and press Notify and inform Microsoft sales and support field Resolve Provide information and tools to restore normal operations Appropriate solution is provided to customers, such as a security update, tool or fix Conduct internal process reviews and gather lessons learned

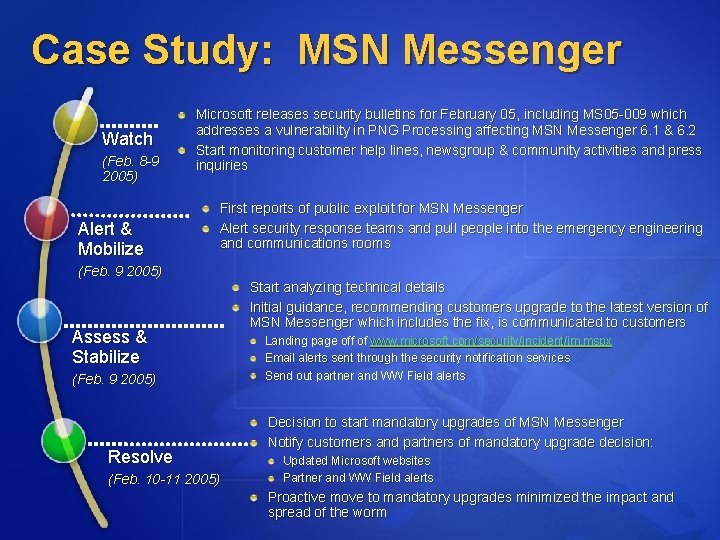
Case Study: MSN Messenger Watch (Feb. 8 -9 2005) Alert & Mobilize Microsoft releases security bulletins for February 05, including MS 05 -009 which addresses a vulnerability in PNG Processing affecting MSN Messenger 6. 1 & 6. 2 Start monitoring customer help lines, newsgroup & community activities and press inquiries First reports of public exploit for MSN Messenger Alert security response teams and pull people into the emergency engineering and communications rooms (Feb. 9 2005) Assess & Stabilize (Feb. 9 2005) Resolve (Feb. 10 -11 2005) Start analyzing technical details Initial guidance, recommending customers upgrade to the latest version of MSN Messenger which includes the fix, is communicated to customers Landing page off of www. microsoft. com/security/incident/im. mspx Email alerts sent through the security notification services Send out partner and WW Field alerts Decision to start mandatory upgrades of MSN Messenger Notify customers and partners of mandatory upgrade decision: Updated Microsoft websites Partner and WW Field alerts Proactive move to mandatory upgrades minimized the impact and spread of the worm

Sign up to receive security updates notifications via email, instant message, mobile devices or RSS Download and deploy security updates (Microsoft Download Center, Windows Update) Report security vulnerabilities through secure@microsoft. com Attend the monthly Tech. Net Security Bulletin Webcast Review information and guidelines on the Microsoft Tech. Net Security site Check out the MSRC Blog at http: //blogs. technet. com/msrc Review SDL for your development projects http: //msdn. microsoft. com/security/default. aspx? pull= /library/en-us/dnsecure/html/sdl. asp www. microsoft. com/technet/security/default. mspx

Microsoft Security Web sites: www. microsoft. com/security and www. microsoft. com/technet/security Sign up to receive notifications on security updates: www. microsoft. com/security/bulletins/alerts. mspx Sign up for the Security Bulletin Web cast: www. microsoft. com/technet/security/bulletin/summary. mspx RSS Feeds for Security Bulletins: www. microsoft. com/technet/security/bulletin/secrssinfo. mspx More from the Microsoft Security Response Center: Web site: www. microsoft. com/msrc Blog: http: //blogs. technet. com/msrc Security Bulletins Search: www. microsoft. com/technet/security/current. aspx Security Advisories: www. microsoft. com/technet/security/advisory Security Guidance Center for Enterprises: www. microsoft. com/security/guidance MSDN Security Developer Center http: //msdn. microsoft. com/security/ Protect Your PC: www. microsoft. com/protect

© 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY.