Genevas approach to Internet voting e Voting certification











- Slides: 18

Geneva's approach to Internet voting (e. Voting) certification towards certification, the way of trust building Council of Europe Workshop on certification of e-voting systems Strasbourg 26 -27 November 2009 SMSI e-voting - Cellule sécurité - DCTI

Summary 1. Context 2. Internet voting in Geneva 3. Homologation vs. Certification 4. Goals of the certification and the Information Security Management System (ISMS) 5. Project and ISMS e. Voting 6. Conclusion SMSI e-voting - Cellule sécurité - DCTI

1 a – Institutional context Geneva, an sovereign entity of 450'000 inhabitants and 45 municipalities • Its own government • Its own parliament • Its own laws Ø Switzerland = 26 cantons/sovereign entities • Works like the EU • One central government and parliament • A federal legislation that must be implemented by the 26 cantons Ø 676'000 citizens living abroad (418'000 in Europe) Life is not always simple !!! Ø SMSI e-voting - Cellule sécurité - DCTI 07/10/2020

1 b – Elections and referendums Ø Switzerland, the world champion for ballots from January 2001 to December 2009 • 29 federal ballots, as follows § National parliament elections: 2 § Referendums and initiatives: 75 in Geneva, Geneva cantonal and communal levels • 59 ballots, as follows § Elections: 23 § Referendums and initiatives: 119 Or, in Geneva: 7 ballots totaling 24 questions each year… SMSI e-voting - Cellule sécurité - DCTI 07/10/2020

1 c – Political will Favorable conditions Ø Convergence of reflections on the cantonal cyberadministration and the federal one Ø The e. Voting pilot project supported by the Confederation until the Geneva voters enshrine it in their Constitution (08. 02. 09 – 70% "yes") Ø There are full legal basis at every level, federal and cantonal Ø 14 binding e. Enabled ballots in Geneva from January 2003 to November 2009 SMSI e-voting - Cellule sécurité - DCTI

2 a – e. Voting in Geneva The process Ø Protecting the vote secrecy in a way similar to the other channels (postal voting and polling station voting) Ø Citizens' control: • Security tests and audits performed, results made public • Possibility to view the source code • The electoral commission controls the e. Voting process Ø Gradual change of the legal provisions to accompany the projects evolutions Ø Open to the citizens abroad (one system runs ballots conducted according to several cantonal laws) SMSI e-voting - Cellule sécurité - DCTI

2 b – e. Voting in Geneva A system Ø Fundamentally different from voting machines Ø Double nature: remote voting and electronic voting through Internet Ø Discontinued use: exploited for periods of 3 weeks each Ø Complement the other voting channels Ø Specific safety and security measures Ø Continually improved at the software and the architecture levels SMSI e-voting - Cellule sécurité - DCTI

2 c – 11 security requirements Ø The voter : • Must be protected against ID theft • Can only vote if he/she is registered • Has one and only one vote Ø The electronic ballot must not be • Intercepted, modified or hijacked • Known before the official ballot counting process • Linked to a voter Ø The IT system must • Resist to a Do. S attack • Be able to prove that a given voter has voted • Not accept votes outside of the voting periods • Be controlled by the authorities Ø The number of cast ballots must be the same as the number of counted ballots, any difference must be explained and corrected SMSI e-voting - Cellule sécurité - DCTI

2 d – Taking the e. Voting security into account Security has been integrated in the project from the start, with Ø Federal and cantonal legal basis Ø Formalization of security requirements Ø Description of the voting process Ø Mastering of the voting process Ø Audits and reports conducted by the Confederation and other stakeholders Ø Intrusion tests and security audits as normal procedure and conducted in the framework of each ballot Ø All external staff must sign an NDA Ø Implementation of a Security and information management system for the IT application (ISMS) Ø Compliance with Council of Europe recommendation Rec(2004)11 SMSI e-voting - Cellule sécurité - DCTI

3 – Homologation vs. Certification ØHomologation Ø Official third party recognition that an organization, a service or a process comply with predefined characteristics, a recognized norm, a rule or a legal requirement. ØCertification Ø Written confirmation, issued by an independent and authorized body, regarding a compliance verification process. § Staff certification § Hardware and software certification (ISO 15408, usually lengthy and costly!) § Certification regarding the implementation of management system (quality-ISO 9001, security-ISO 27001, etc. ) The federal law on data protection and the related ordinance on certifications foresee the possibility of certification for these two last points according to the above-mentioned ISO norms. SMSI e-voting - Cellule sécurité - DCTI

4 b – The State of Geneva ISMS aims Ø Developing a standardized and reproducible approach of security governance, in order to create a reasonable level of trust as well as bringing transparency into the internet voting process • Creating a system to manage the information security according to ISO 27001 norm and the PDCA model Tailored to the e. Voting domain, its challenges and the State context • The audit's approach: • "Say what we do and do as we say" Ø Anticipating interrogations and critics; communicating Ø Capitalizing on the acquired know how yet, our political framework is limiting certifications SMSI e-voting - Cellule sécurité - DCTI

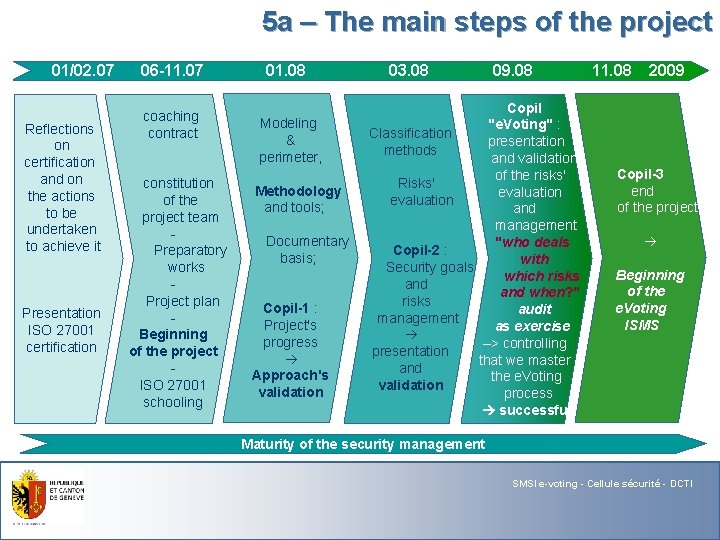
5 a – The main steps of the project 01/02. 07 Reflections on certification and on the actions to be undertaken to achieve it Presentation ISO 27001 certification 06 -11. 07 coaching contract constitution of the project team Preparatory works Project plan Beginning of the project ISO 27001 schooling 01. 08 Modeling & perimeter, Methodology and tools; Documentary basis; Copil-1 : Project's progress Approach's validation 03. 08 09. 08 Copil "e. Voting" : Classification presentation methods and validation of the risks' Risks' evaluation and management "who deals Copil-2 : with Security goals which risks and when? " risks audit management as exercise –> controlling presentation that we master and the e. Voting validation process successful 11. 08 2009 Copil-3 end of the project Beginning of the e. Voting ISMS Maturity of the security management SMSI e-voting - Cellule sécurité - DCTI

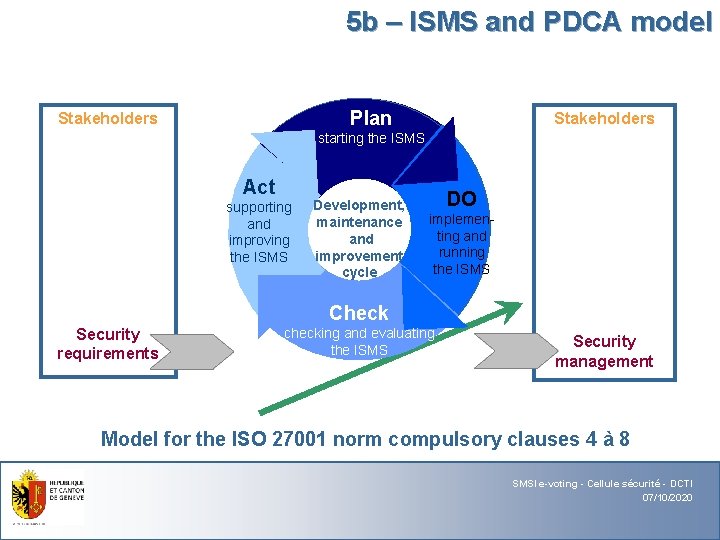
5 b – ISMS and PDCA model Plan Stakeholders starting the ISMS Act supporting and improving the ISMS Development, maintenance and improvement cycle DO implementing and running the ISMS Check Security requirements checking and evaluating the ISMS Security management Model for the ISO 27001 norm compulsory clauses 4 à 8 SMSI e-voting - Cellule sécurité - DCTI 07/10/2020

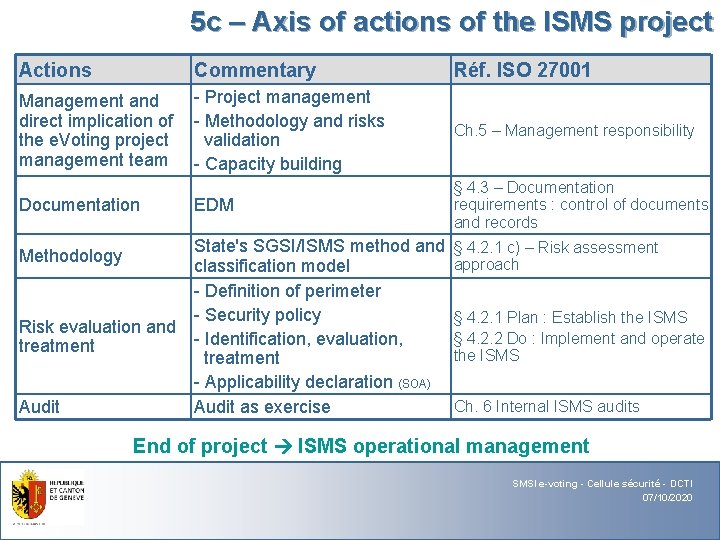
5 c – Axis of actions of the ISMS project Actions Commentary Réf. ISO 27001 Management and direct implication of the e. Voting project management team - Project management - Methodology and risks validation - Capacity building Ch. 5 – Management responsibility EDM § 4. 3 – Documentation requirements : control of documents and records Documentation Methodology Risk evaluation and treatment Audit State's SGSI/ISMS method and classification model - Definition of perimeter - Security policy - Identification, evaluation, treatment - Applicability declaration (SOA) Audit as exercise § 4. 2. 1 c) – Risk assessment approach § 4. 2. 1 Plan : Establish the ISMS § 4. 2. 2 Do : Implement and operate the ISMS Ch. 6 Internal ISMS audits End of project ISMS operational management SMSI e-voting - Cellule sécurité - DCTI 07/10/2020

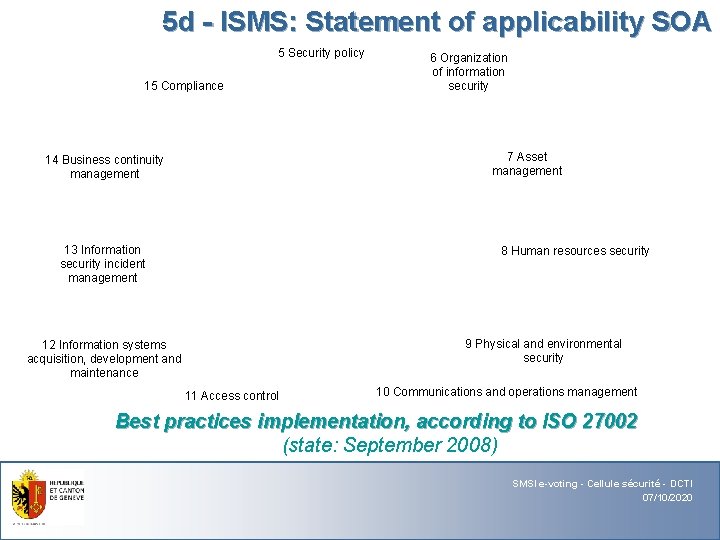
5 d - ISMS: Statement of applicability SOA 5 Security policy 15 Compliance 6 Organization of information security 7 Asset management 14 Business continuity management 13 Information security incident management 8 Human resources security 9 Physical and environmental security 12 Information systems acquisition, development and maintenance 11 Access control 10 Communications and operations management Best practices implementation, according to ISO 27002 (state: September 2008) SMSI e-voting - Cellule sécurité - DCTI 07/10/2020

5 e – Current actions Action Commentary Réf. ISO 27001 Implementation of safety measures - Ongoing Management of incidents - Continuous Management of steps; capacity building - Ongoing § 4. 2. 2 – Do ISMS control measures - Ongoing § 4. 2. 3 – Check : monitor and review ISMS Evaluation of the measures impact; reexamination of the risk assessment - Ongoing § 4. 2. 3 – Check - To be planned ISMS management and improvement § 4. 2. 3 – Check § 4. 2. 4 – Act : maintain (continuous improvement, corrective and improve ISMS and preventive actions) Ch. 8 ISMS improvement Revue de direction - To be planned § 4. 2. 3 – Check Ch. 7 Management revue of the ISMS Communication - To be planned § 4. 2. 4 – Act Responsibility of the owner of the e. Voting system SMSI e-voting - Cellule sécurité - DCTI 07/10/2020

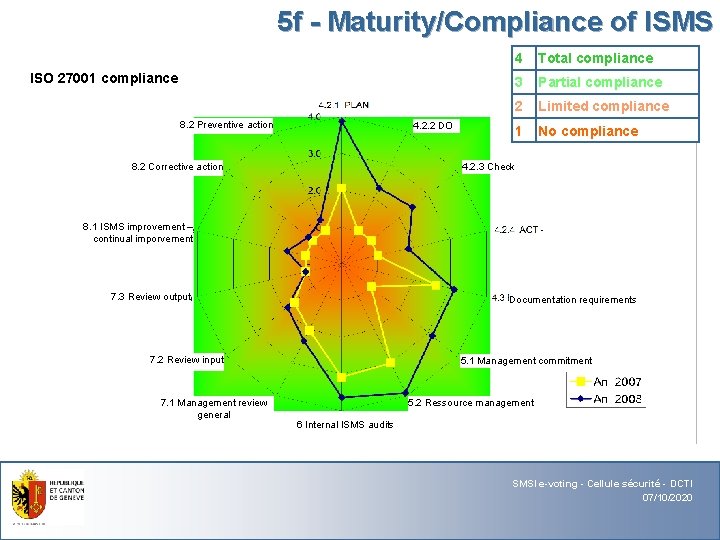
5 f - Maturity/Compliance of ISMS ISO 27001 compliance 8. 2 Preventive action 4. 2. 2 DO 8. 2 Corrective action 4 Total compliance 3 Partial compliance 2 Limited compliance 1 No compliance 4. 2. 3 Check 8. 1 ISMS improvement – continual imporvement 7. 3 Review output Documentation requirements 7. 2 Review input 7. 1 Management review general 5. 1 Management commitment 5. 2 Ressource management 6 Internal ISMS audits SMSI e-voting - Cellule sécurité - DCTI 07/10/2020

6 –Conclusion The way towards certification means Ø A commitment for means but not for results! Ø An approach that stimulates: Ø • The mastering of activities and the improvement of the maturity level of the security and risk management of the information system • The development of competencies and knowledge A tool for communication and understanding A path towards trust … certification has however no impact on the opinion of skeptics ("there will always be a black box somewhere in the system, no matter how hard you try to make it transparent") Ø SMSI e-voting - Cellule sécurité - DCTI