General Introduction of A Distributed Authorization Solution Group

General Introduction of A Distributed Authorization Solution Group Name: WG 4 Source: Wei Zhou, CATT, zhouwei@catt. cn Meeting Date: 2015 -03 -23 Agenda Item: <agenda item topic name>
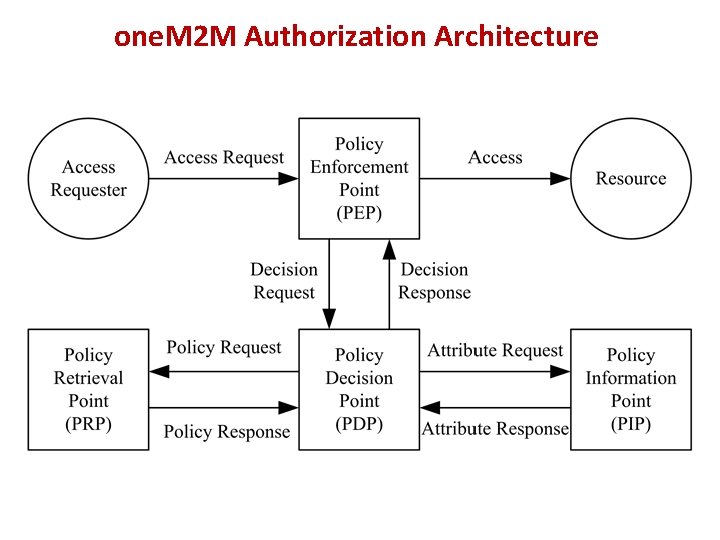
one. M 2 M Authorization Architecture
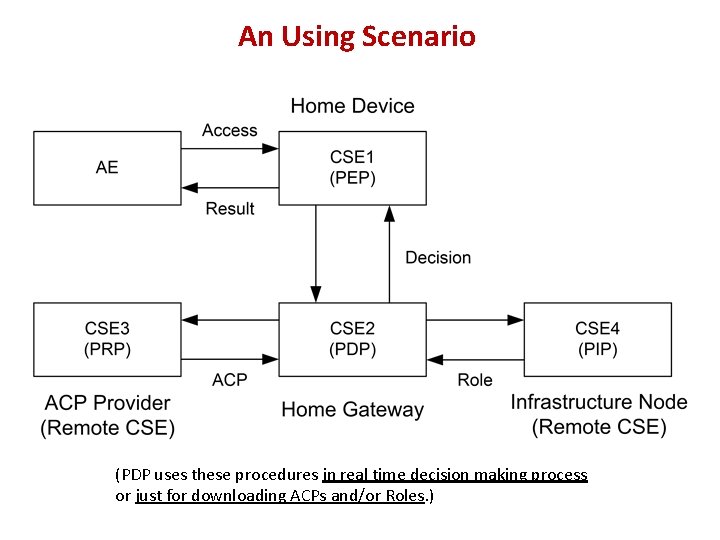
An Using Scenario (PDP uses these procedures in real time decision making process or just for downloading ACPs and/or Roles. )

Some Explanation about This Solution • Using virtual resources for triggering the processes of PDP, PRP and PIP (How to bind a process to a virtual resource is out of scope). • If a virtual resource is not bound to a process, then access (RETRIEVE) to this virtual resource cannot trigger a process. • These virtual resources are organized under the parent resource <access. Control> (possible renamed to <authorization>). • The PEP, PDP, PRP and PIP could be located in different CSEs. • Current the Multiplicity of the virtual resources is “ 1”. If the CREATE procedure supports virtual resource creation, the Multiplicity shall be “ 0. . 1” • The PEP sends a RETRIEVE Request to PDP, so the CSE hosting the PEP is the Originator, and the CSE hosting PDP is the Receiver; The PDP sends a RETRIEVE Request to PRP or PIP, so the CSE hosting the PDP is the Originator, and the CSE hosting PRP or PIP is the Receiver
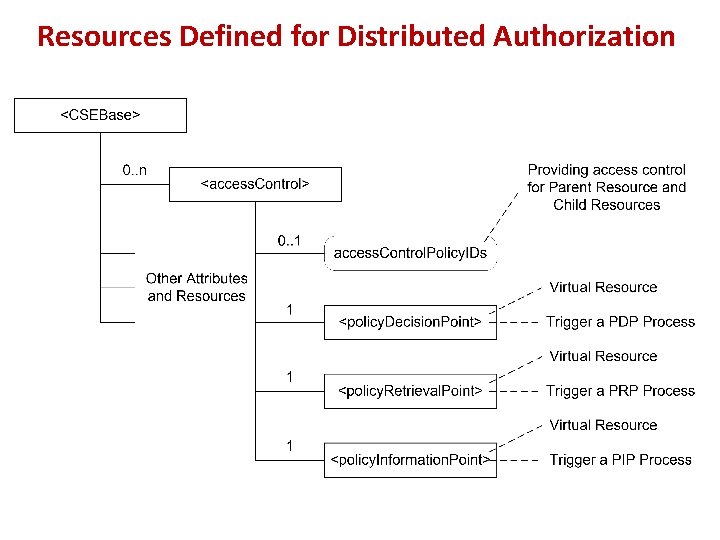
Resources Defined for Distributed Authorization

Create <access. Control> Resource and Its Virtual Child Resources
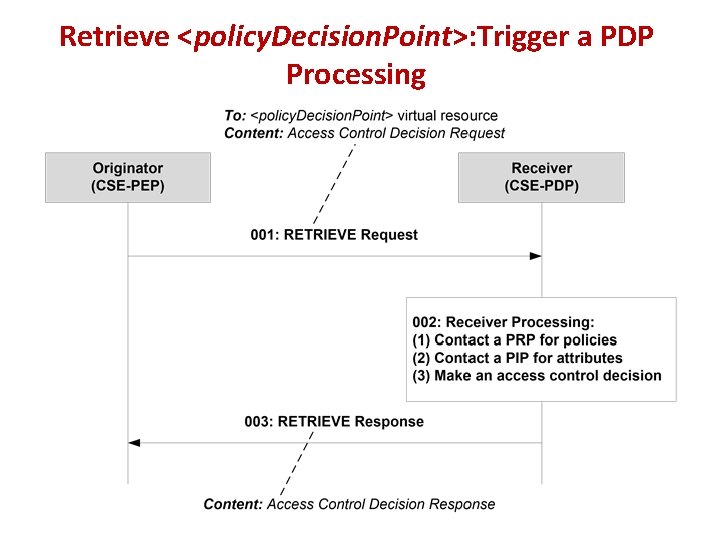
Retrieve <policy. Decision. Point>: Trigger a PDP Processing

Retrieve <policy. Retrieval. Point>: Trigger a PRP Processing

Retrieve <policy. Information. Point>: Trigger a PIP Processing

Contributions for Distributed Authorization • Resource Definitions see contribution: SEC-2015 -0492 -TR-00016_Resource_Definitions_for_Distributed_Authorization • Procedures on Parent Resource see contribution: SEC-2015 -0493 -TR 00016_Procedures_on_Parent_Resource_for_Distributed_Authorization • Procedures on Child Resources see contribution: SEC-2015 -0494 -TR 00016_Procedures_on_Child_Resources_for_Distributed_Authorization
- Slides: 10