GDPR IT Challenges ico Who does the GDPR














- Slides: 23

GDPR – IT Challenges

ico. – Who does the GDPR apply to? The GDPR applies to ‘controllers’ and ‘processors’. A controller determines the purposes and means of processing personal data. A processor is responsible for processing personal data on behalf of a controller. If you are a processor, the GDPR places specific legal obligations on you; for example, you are required to maintain records of personal data and processing activities. You will have legal liability if you are responsible for a breach. However, if you are a controller, you are not relieved of your obligations where a processor is involved – the GDPR places further obligations on you to ensure your contracts with processors comply with the GDPR.

ico. – What information does the GDPR apply to? Personal data The GDPR applies to ‘personal data’ meaning any information relating to an identifiable person who can be directly or indirectly identified in particular by reference to an identifier. This definition provides for a wide range of personal identifiers to constitute personal data, including name, identification number, location data or online identifier, reflecting changes in technology and the way organisations collect information about people. The GDPR applies to both automated personal data and to manual filing systems where personal data are accessible according to specific criteria. This could include chronologically ordered sets of manual records containing personal data. Personal data that has been pseudonymised – eg key-coded – can fall within the scope of the GDPR depending on how difficult it is to attribute the pseudonym to a particular individual. Sensitive personal data The GDPR refers to sensitive personal data as “special categories of personal data” (see Article 9). The special categories specifically include genetic data, and biometric data where processed to uniquely identify an individual.

ico. – Article 5 of the GDPR requires that personal data shall be: a) processed lawfully, fairly and in a transparent manner in relation to individuals; b) collected for specified, explicit and legitimate purposes and not further processed in a manner that is incompatible with those purposes; further processing for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes shall not be considered to be incompatible with the initial purposes; c) adequate, relevant and limited to what is necessary in relation to the purposes for which they are processed; d) accurate and, where necessary, kept up to date; every reasonable step must be taken to ensure that personal data that are inaccurate, having regard to the purposes for which they are processed, are erased or rectified without delay; e) kept in a form which permits identification of data subjects for no longer than is necessary for the purposes for which the personal data are processed; personal data may be stored for longer periods insofar as the personal data will be processed solely for archiving purposes in the public interest, scientific or historical research purposes or statistical purposes subject to implementation of the appropriate technical and organisational measures required by the GDPR in order to safeguard the rights and freedoms of individuals; and f) processed in a manner that ensures appropriate security of the personal data, including protection against unauthorised or unlawful processing and against accidental loss, destruction or damage, using appropriate technical or organisational measures. Article 5(2) - the controller shall be responsible for, and be able to demonstrate, compliance with the principles.

ico. – rights for individuals: The right to be informed - The right to be informed encompasses your obligation to provide ‘fair processing information’, typically through a privacy notice. It emphasises the need for transparency over how you use personal data. The right of access - Individuals have the right to access their personal data and supplementary information. The right of access allows individuals to be aware of and verify the lawfulness of the processing. The right to rectification - The GDPR gives individuals the right to have personal data rectified. Personal data can be rectified if it is inaccurate or incomplete. The right to erase - The right to erasure is also known as ‘the right to be forgotten ’. The broad principle underpinning this right is to enable an individual to request the deletion or removal of personal data where there is no compelling reason for its continued processing. The right to restrict processing - Individuals have a right to ‘block’ or suppress processing of personal data. When processing is restricted, you are permitted to store the personal data, but not further process it. You can retain just enough information about the individual to ensure that the restriction is respected in future. The right to data portability - The right to data portability allows individuals to obtain and reuse their personal data for their own purposes across different services. It allows them to move, copy or transfer personal data easily from one IT environment to another in a safe and secure way, without hindrance to usability. The right to object - processing based on legitimate interests or the performance of a task in the public interest/exercise of official authority (including profiling); direct marketing (including profiling); and processing for purposes of scientific/historical research and statistics. Rights in relation to automated decision making and profiling. - The GDPR applies to all automated individual decision-making and profiling.

ico. – What is the accountability principle? The accountability principle in Article 5(2) requires you to demonstrate that you comply with the principles and states explicitly that this is your responsibility. How can I demonstrate that I comply? You must: implement appropriate technical and organisational measures that ensure and demonstrate that you comply. This may include internal data protection policies such as staff training, internal audits of processing activities, and reviews of internal HR policies; maintain relevant documentation on processing activities; where appropriate, appoint a data protection officer; implement measures that meet the principles of data protection by design and data protection by default. Measures could include: data minimisation; pseudonymisation; transparency; allowing individuals to monitor processing; and creating and improving security features on an ongoing basis. use data protection impact assessments where appropriate. You can also: adhere to approved codes of conduct and/or certification schemes. See the section on codes of conduct and certification for more detail.

ico. – Documentation of processing activities The GDPR contains explicit provisions about documenting your processing activities. You must maintain records on several things such as processing purposes, data sharing and retention. You may be required to make the records available to the ICO on request. Documentation can help you comply with other aspects of the GDPR and improve your data governance. Controllers and processors both have documentation obligations. You need to make sure that you have in place a record of your processing activities by 25 May 2018. Who needs to document their processing activities? Controllers and processors each have their own documentation obligations. If you have 250 or more employees, you must document all your processing activities.

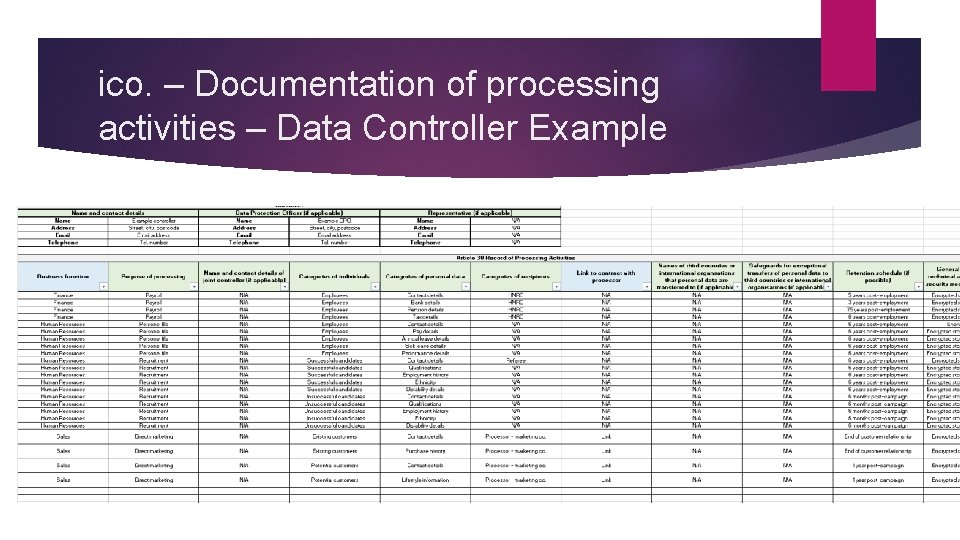
ico. – Documentation of processing activities – Data Controller Example

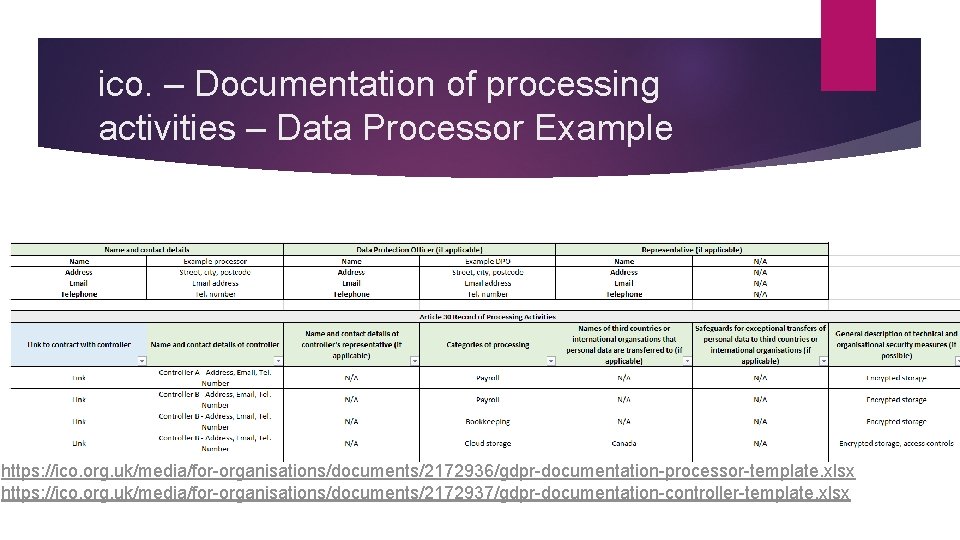
ico. – Documentation of processing activities – Data Processor Example https: //ico. org. uk/media/for-organisations/documents/2172936/gdpr-documentation-processor-template. xlsx https: //ico. org. uk/media/for-organisations/documents/2172937/gdpr-documentation-controller-template. xlsx

ico. – Data Protection Officers The GDPR makes it a requirement that organisations appoint a data protection officer (DPO) in some circumstances. The GDPR also contains provisions about the tasks a DPO should carry out and the duties of the employer in respect of the DPO. Any organisation is able to appoint a DPO. Regardless of whether the GDPR obliges you to appoint a DPO, you must ensure that your organisation has sufficient staff and skills to discharge your obligations under the GDPR.

ico. – Security / Data Breach The GDPR requires personal data to be processed in a manner that ensures its security. This includes protection against unauthorised or unlawful processing and against accidental loss, destruction or damage. It requires that appropriate technical or organisational measures are used. The GDPR will introduce a duty on all organisations to report certain types of data breach to the relevant supervisory authority. What is a personal data breach? A personal data breach means a breach of security leading to the destruction, loss, alteration, unauthorised disclosure of, or access to, personal data. This means that a breach is more than just losing personal data Example - An example of loss of personal data can include where a device containing a copy of a controller’s customer database has been lost or stolen. A further example of loss may be where the only copy of a set of personal data has been encrypted by ransomware, or has been encrypted by the controller using a key that is no longer in its possession

ico. – Security / Data Breach The GDPR only applies where there is a breach of personal data. The consequence of such a breach is that the controller will be unable to ensure compliance with the principles relating to the processing of personal data as outlined in Article 5 of the GDPR Example - Infection by ransomware (malicious software which encrypts the controller’s data until a ransom is paid) could lead to a temporary loss of availability if the data can be restored from backup. However, a network intrusion still occurred, and notification could be required if the incident is qualified as confidentiality breach (i. e. personal data is accessed by the attacker) and this presents a risk to the rights and freedoms of individuals. “In the case of a personal data breach, the controller shall without undue delay and, where feasible, not later than 72 hours after having become aware of it, notify the personal data breach to the supervisory authority competent in accordance with Article 55, unless the personal data breach is unlikely to result in a risk to the rights and freedoms of natural persons. Where the notification to the supervisory authority is not made within 72 hours, it shall be accompanied by reasons for the delay. ” http: //ec. europa. eu/newsroom/document. cfm? doc_id=47741

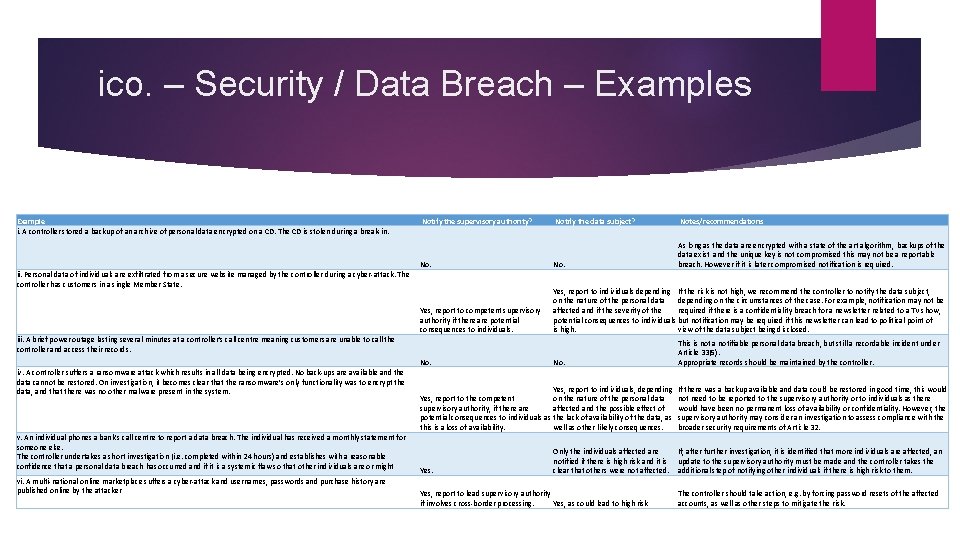
ico. – Security / Data Breach – Examples Example i. A controller stored a backup of an archive of personal data encrypted on a CD. The CD is stolen during a break-in. Notify the supervisory authority? Notify the data subject? Notes/recommendations No. As long as the data are encrypted with a state of the art algorithm, backups of the data exist and the unique key is not compromised this may not be a reportable breach. However if it is later compromised notification is required. Yes, report to competent supervisory authority if there are potential consequences to individuals. Yes, report to individuals depending If the risk is not high, we recommend the controller to notify the data subject, on the nature of the personal data depending on the circumstances of the case. For example, notification may not be affected and if the severity of the required if there is a confidentiality breach for a newsletter related to a TV show, potential consequences to individuals but notification may be required if this newsletter can lead to political point of is high. view of the data subject being disclosed. ii. Personal data of individuals are exfiltrated from a secure website managed by the controller during a cyber-attack. The controller has customers in a single Member State. iii. A brief power outage lasting several minutes at a controller’s call centre meaning customers are unable to call the controller and access their records. No. iv. A controller suffers a ransomware attack which results in all data being encrypted. No back-ups are available and the data cannot be restored. On investigation, it becomes clear that the ransomware’s only functionality was to encrypt the data, and that there was no other malware present in the system. v. An individual phones a bank’s call centre to report a data breach. The individual has received a monthly statement for someone else. The controller undertakes a short investigation (i. e. completed within 24 hours) and establishes with a reasonable confidence that a personal data breach has occurred and if it is a systemic flaw so that other individuals are or might vi. A multi-national online marketplace suffers a cyber-attack and usernames, passwords and purchase history are published online by the attacker No. Yes, report to individuals, depending Yes, report to the competent on the nature of the personal data supervisory authority, if there affected and the possible effect of potential consequences to individuals as the lack of availability of the data, as this is a loss of availability. well as other likely consequences. Yes. Only the individuals affected are notified if there is high risk and it is clear that others were not affected. Yes, report to lead supervisory authority if involves cross-border processing. Yes, as could lead to high risk This is not a notifiable personal data breach, but still a recordable incident under Article 33(5). Appropriate records should be maintained by the controller. If there was a backup available and data could be restored in good time, this would not need to be reported to the supervisory authority or to individuals as there would have been no permanent loss of availability or confidentiality. However, the supervisory authority may consider an investigation to assess compliance with the broader security requirements of Article 32. If, after further investigation, it is identified that more individuals are affected, an update to the supervisory authority must be made and the controller takes the additional step of notifying other individuals if there is high risk to them. The controller should take action, e. g. by forcing password resets of the affected accounts, as well as other steps to mitigate the risk.

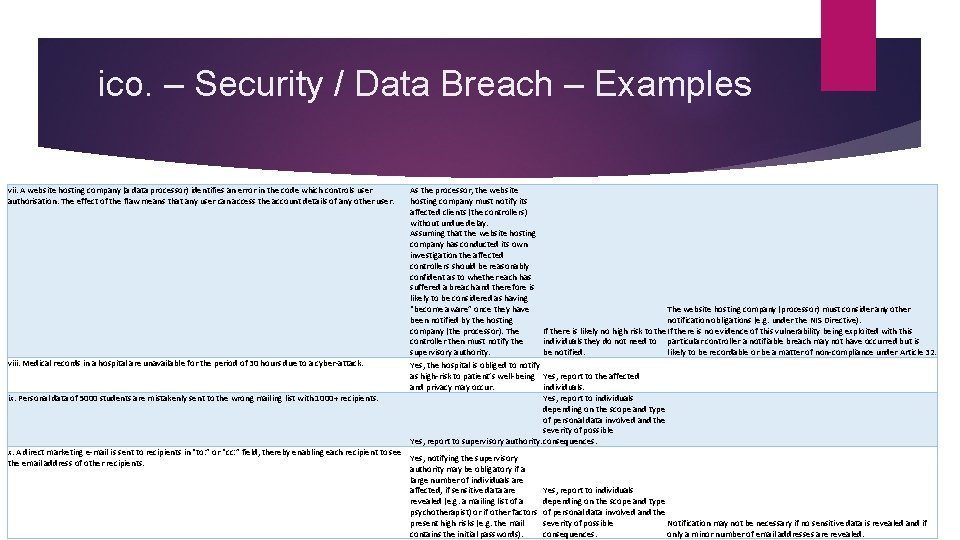
ico. – Security / Data Breach – Examples vii. A website hosting company (a data processor) identifies an error in the code which controls user authorisation. The effect of the flaw means that any user can access the account details of any other user. viii. Medical records in a hospital are unavailable for the period of 30 hours due to a cyber-attack. ix. Personal data of 5000 students are mistakenly sent to the wrong mailing list with 1000+ recipients. As the processor, the website hosting company must notify its affected clients (the controllers) without undue delay. Assuming that the website hosting company has conducted its own investigation the affected controllers should be reasonably confident as to whether each has suffered a breach and therefore is likely to be considered as having “become aware” once they have been notified by the hosting company (the processor). The controller then must notify the supervisory authority. Yes, the hospital is obliged to notify as high-risk to patient’s well-being and privacy may occur. The website hosting company (processor) must consider any other notification obligations (e. g. under the NIS Directive). If there is likely no high risk to the If there is no evidence of this vulnerability being exploited with this individuals they do not need to particular controller a notifiable breach may not have occurred but is likely to be recordable or be a matter of non-compliance under Article 32. be notified. Yes, report to the affected individuals. Yes, report to individuals depending on the scope and type of personal data involved and the severity of possible Yes, report to supervisory authority. consequences. x. A direct marketing e-mail is sent to recipients in “to: ” or “cc: ” field, thereby enabling each recipient to see Yes, notifying the supervisory the email address of other recipients. authority may be obligatory if a large number of individuals are affected, if sensitive data are revealed (e. g. a mailing list of a psychotherapist) or if other factors present high risks (e. g. the mail contains the initial passwords). Yes, report to individuals depending on the scope and type of personal data involved and the severity of possible Notification may not be necessary if no sensitive data is revealed and if consequences. only a minor number of email addresses are revealed.

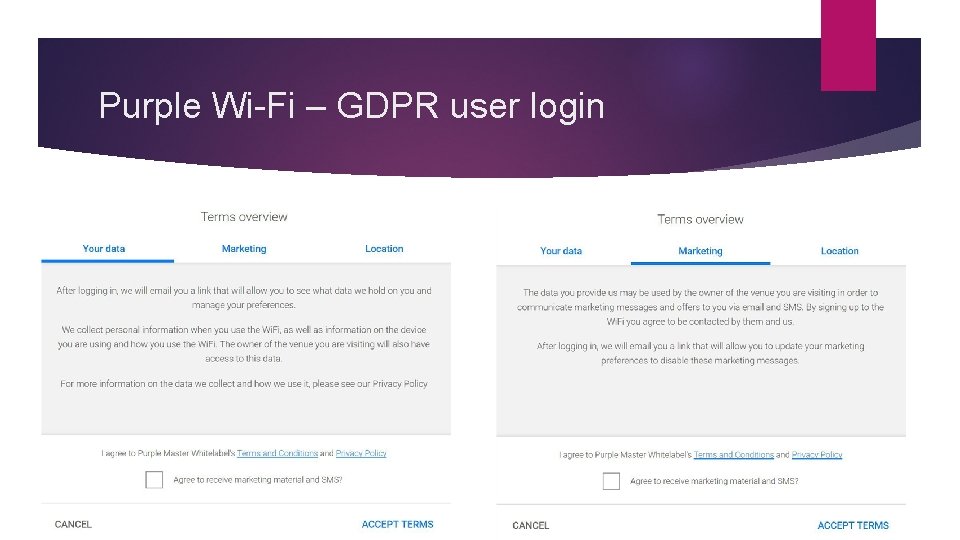
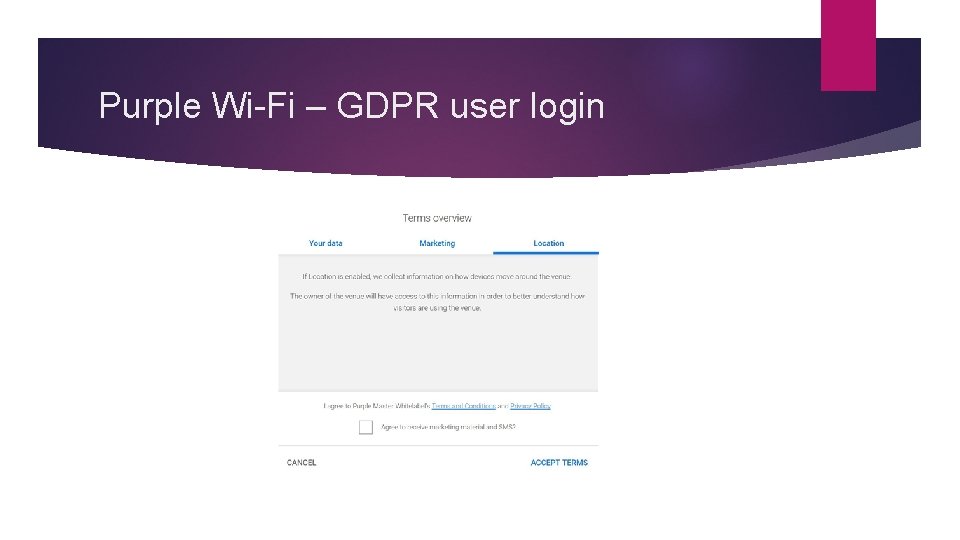
Purple Wi-Fi – GDPR Access Journey One of the key terms to come from GDPR is the idea of “unambiguous consent”. What this means is that when a user agrees to a Privacy Policy, or Terms and Conditions, they are aware of what they are agreeing to, and they have clearly agreed to the principles of what data a company will collect and what they will do with that data. In order to attain this “unambiguous consent” we have made a number of changes to the access journey. When a customer ticks the consent box on the Wi. Fi splash page, they will be presented with a further screen that provides a “Terms Overview”. This screen provides 2 tabs which then break down information on the data that is collected (Your data) and how the data is used for marketing purposes (Marketing).

Purple Wi-Fi – GDPR user login

Purple Wi-Fi – GDPR user login

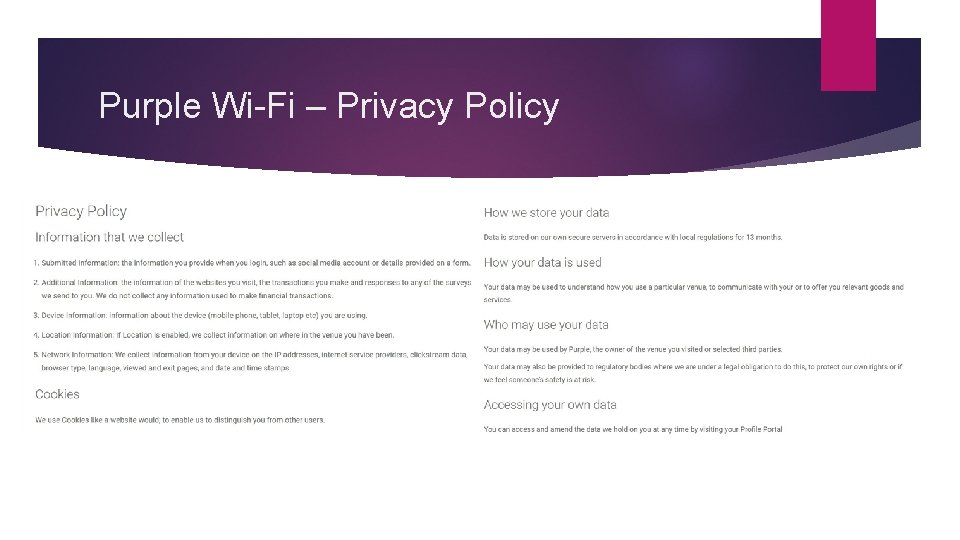
Purple Wi-Fi – Privacy Policy Many Privacy Policies are lengthy and often designed as a legal document, which results in them being difficult to understand often ignored. Many users will blindly agree to terms and conditions rather than take the time to read through them. In response to this, we’ve shortened our own Privacy Policy from 1600 words to 260 words, and made it very easy to understand. We’ve used the type of language that people use in their everyday life. Our hope is that when a user is presented with the Privacy Policy it is clear enough for them to be confident in the knowledge of what data we collect, why we collect it and what we do with the data.

Purple Wi-Fi – Privacy Policy

Purple Wi-Fi – My Activity App In reaction to the EU General Data Protection Regulation (GDPR) which will come into force next year, we have unveiled our brand new Profile Portal and revised privacy policy to give end users complete transparency into the data collected about them. The Profile Portal provides end users with ongoing access to all of the information collected about them and our Privacy Policy has been dramatically shortened to ensure they are simple and unambiguous. These developments have cemented our position as the first GDPR compliant Wi. Fi provider, eased the pressures of GDPR for our European customers and made end users feel reassured that their data is in safe hands. The Profile Portal and privacy policy will not only benefit European partners, customers and Wi. Fi users, but will prove beneficial worldwide as pressure mounts for businesses to manage data responsibly.

G 5 – GDPR A change in the law for providers of free Wi-Fi The EU General Data Protection Regulation (GDPR) comes into effect on the 25 th May 2018. This regulation is complex but in a nutshell, if you currently provide Free Wi-Fi, you must only collect personal data for providing a service that your client has both requested and given consent to their data being used for its intended purpose. In other words, users must consent to their personal data being used for marketing purposes (personal data can include name, address, location data, IP address and much more). Regardless of Brexit, the UK still needs to comply and fines can be up to 5% of your turnover if you don’t. What does this mean? The terms & conditions for your Wi-Fi service need to be very clear on what data you are collecting, the reasons why, your intended usage of such data and the ability for the public to optin for any marketing, as well as providing them clear instructions on how they can opt-out at any time. G 5 Zone Wi-Fi includes our standard T&Cs that are currently compliant with the proposed GDPR framework.

G 5 – Guest Wi-Fi - Your Responsibilities Not only can poor Wi-Fi provision be the cause of many customer complaints but there also various laws and regulations that apply to the operation of public Wi-Fi. Legal Compliance The regulations are going to change on 25 th May 2018. To avoid a hefty fine of up to 5% of your turnover, you will need an effective management system in place that can not only ensure compliance with the law but also manage your bandwidth, users and provide the following functions: If your current system is unable to do this then it is time to upgrade. Discourage illegal downloading - The Digital Economy Act 2010 is designed to implement steps to reduce online copyright infringement by end users such as illegal downloading of copyright material and illegal file sharing. Discourage criminal activity - Under the Anti-Terrorism, Crime and Security Act 2001 you need to be able to identify who is using your network. GDPR and Data Protection - The EU General Data Protection Regulation (GDPR) comes into effect on the 25 th May 2018. This regulation is complex but if you currently provide Free Wi-Fi you must only collect personal data for providing a service that your client has both requested and given consent to their data being used for its intended purpose.

Backup Tapes – Veritas You may very well have hundreds if not thousands of backup tapes, some you keep onsite in a fireproof safe, but most are safely kept offsite in your disaster recovery location. The target file (or files) that you have been asked to delete can be on any of these backup tapes. So … how do you find the backup tape that stores your target file? Now … your files aren’t actually individually copied to your backup tapes. Your backup tapes store backup images and each image may contain multiple files. This means that you first must identify the backup image that contains your target file before you can determine which backup tape you must retrieve. Next … how do you delete your target file from the backup tape? Unfortunately, you cannot selectively destroy a backup image on a backup tape. You have to destroy everything else on that backup tape too. This doesn’t sound a viable approach – at least not to me. You may end up having first to duplicate out all the other backup images from the backup tape except for the backup image that contains the target file, and then perform (long) erasure of the backup tape. And – adding some more time consuming joy - if the backup image also contains other files that must be kept, then you first need to restore that backup image, delete the file, and then backup the rest again. Finally … depending on your data retention policies you are likely to have to repeat these steps for several more backup tapes. The good news is that you have just under two-years left to go 'tapeless '. (Published 2016)