FT DRA Security Operations Center SOC Vulnerability Management

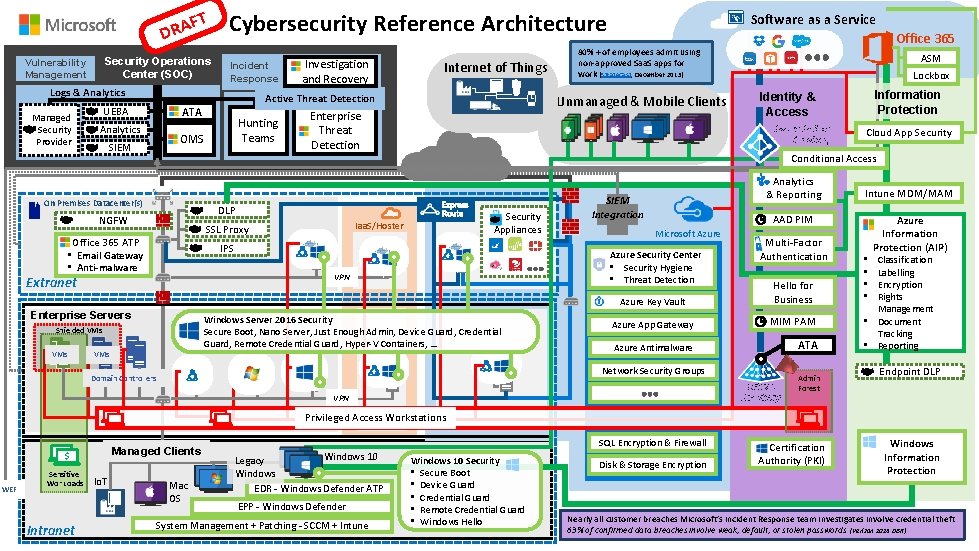
FT DRA Security Operations Center (SOC) Vulnerability Management Cybersecurity Reference Architecture Incident Response Logs & Analytics Managed Security Provider Analytics On Premises Datacenter(s) Enterprise Threat Detection Office 365 ATP • Email Gateway • Anti-malware Security Appliances Windows Server 2016 Security Secure Boot, Nano Server, Just Enough Admin, Device Guard, Credential Guard, Remote Credential Guard, Hyper-V Containers, … Shielded VMs Information Protection Identity & Access Analytics & Reporting SIEM Integration Cloud App Security Microsoft Azure Multi-Factor Authentication Azure Key Vault Hello for Business Azure App Gateway MIM PAM Azure Antimalware ATA Network Security Groups Domain Controllers Intune MDM/MAM AAD PIM Azure Security Center • Security Hygiene • Threat Detection VPN Enterprise Servers Lockbox Conditional Access IPS Extranet ASM Azure Active Directory Iaa. S/Hoster SSL Proxy Office 365 80% + of employees admit using non-approved Saa. S apps for work (Stratecast, December 2013) Unmanaged & Mobile Clients DLP NGFW VMs Hunting Teams OMS SIEM Internet of Things Active Threat Detection ATA UEBA Investigation and Recovery Software as a Service Active Directory VPN Admin Forest Azure Information Protection (AIP) Classification Labelling Encryption Rights Management • Document Tracking • Reporting • • Endpoint DLP Privileged Access Workstations Managed Clients $ WEF Sensitive Workloads Intranet Io. T Mac OS SQL Encryption & Firewall Windows 10 Legacy Windows EDR - Windows Defender ATP EPP - Windows Defender System Management + Patching - SCCM + Intune Windows 10 Security • Secure Boot • Device Guard • Credential Guard • Remote Credential Guard • Windows Hello Disk & Storage Encryption Certification Authority (PKI) Windows Information Protection Nearly all customer breaches Microsoft’s Incident Response team investigates involve credential theft 63% of confirmed data breaches involve weak, default, or stolen passwords (Verizon 2016 DBR)
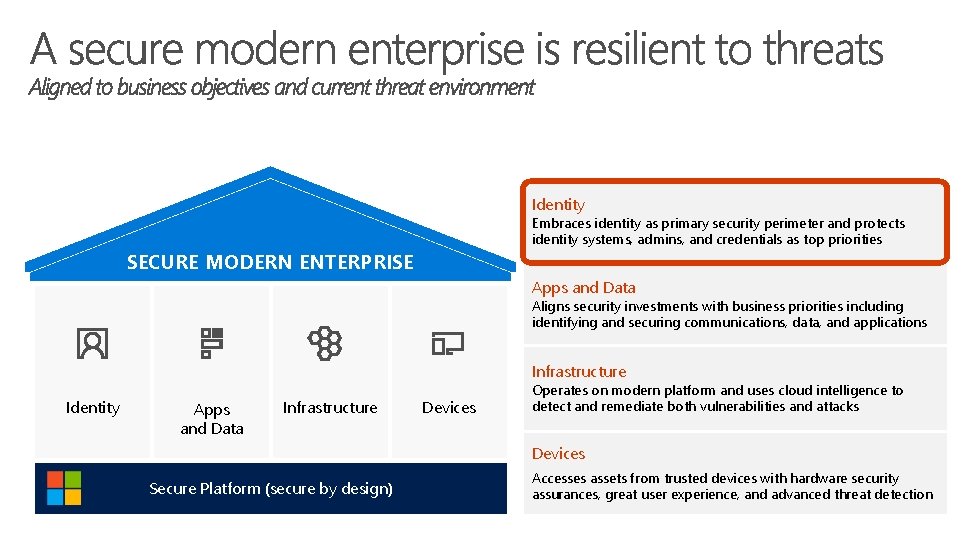
Identity Embraces identity as primary security perimeter and protects identity systems, admins, and credentials as top priorities SECURE MODERN ENTERPRISE Apps and Data Aligns security investments with business priorities including identifying and securing communications, data, and applications Infrastructure Identity Apps and Data Infrastructure Devices Operates on modern platform and uses cloud intelligence to detect and remediate both vulnerabilities and attacks Devices Secure Platform (secure by design) Accesses assets from trusted devices with hardware security assurances, great user experience, and advanced threat detection
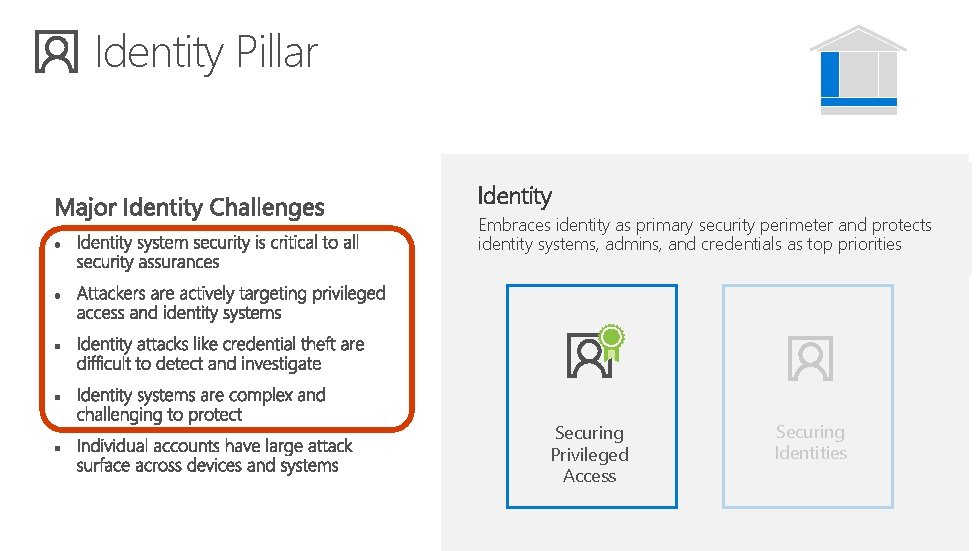
Identity Pillar Identity Embraces identity as primary security perimeter and protects identity systems, admins, and credentials as top priorities Securing Privileged Access Securing Identities
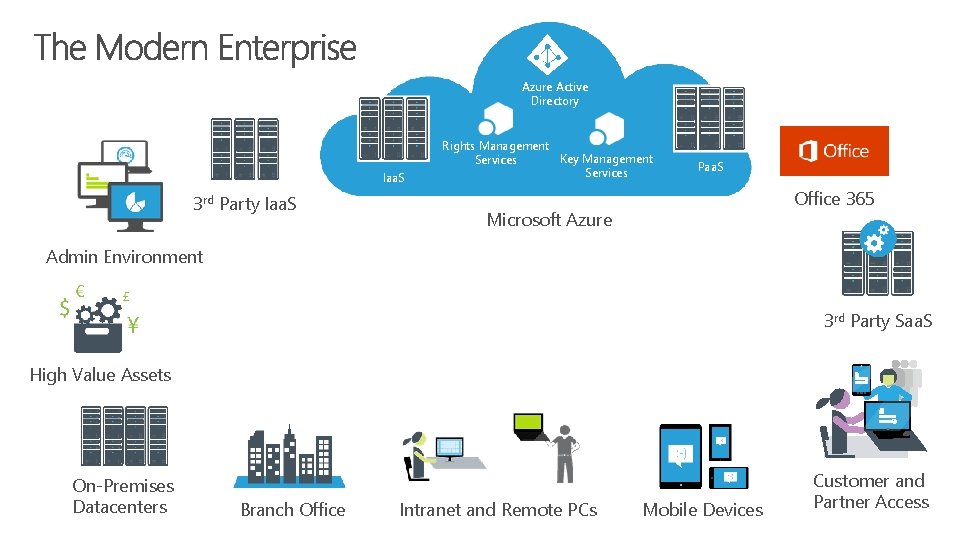
Azure Active Directory Iaa. S 3 rd Party Iaa. S Rights Management Key Management Services Paa. S Office 365 Microsoft Azure Admin Environment 3 rd Party Saa. S High Value Assets On-Premises Datacenters Branch Office Intranet and Remote PCs Mobile Devices Customer and Partner Access
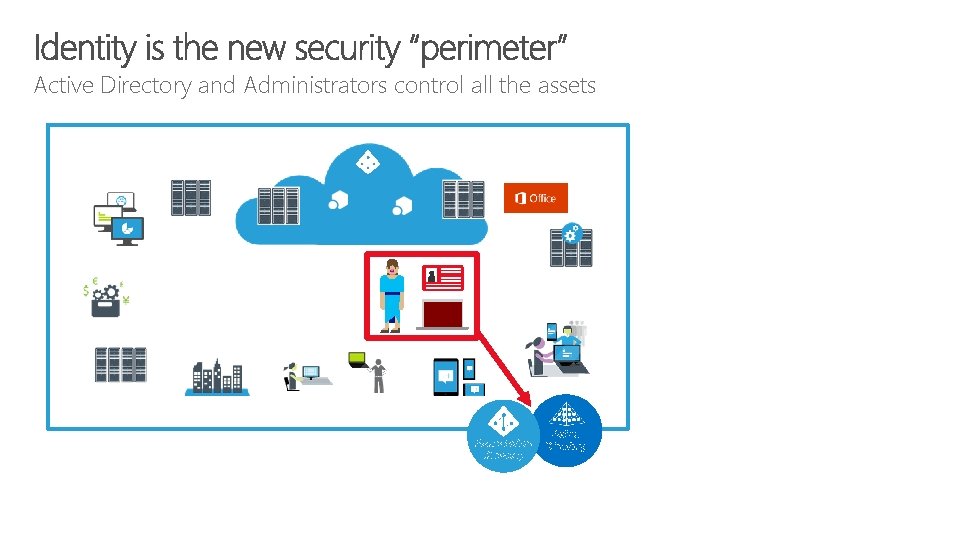
Active Directory and Administrators control all the assets Azure Active Directory
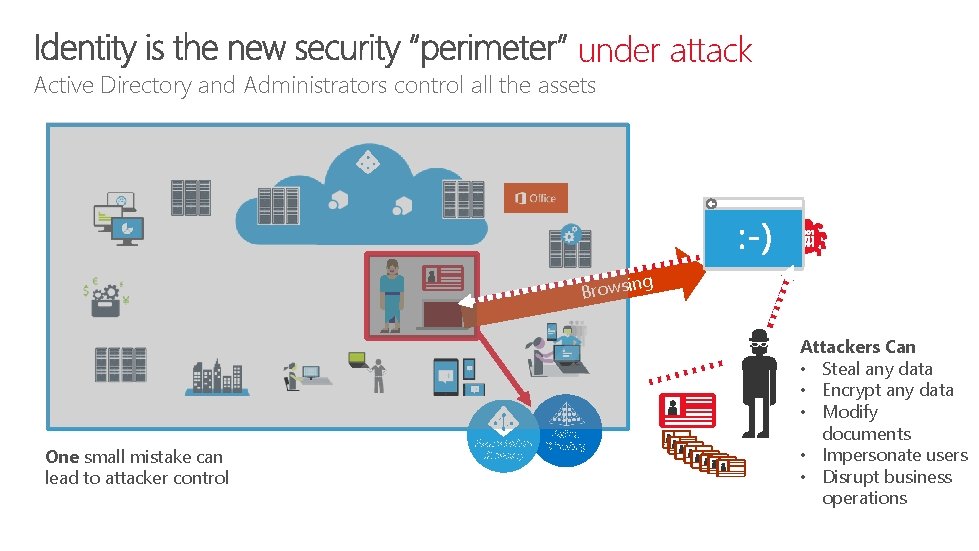
under attack Active Directory and Administrators control all the assets ng Browsi One small mistake can lead to attacker control Azure Active Directory Attackers Can • Steal any data • Encrypt any data • Modify documents • Impersonate users • Disrupt business operations
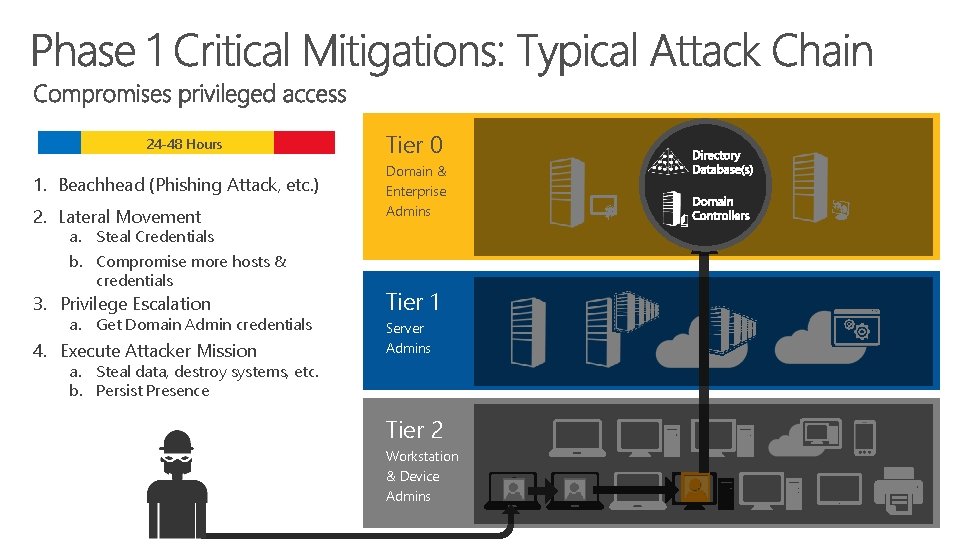
24 -48 Hours 1. Beachhead (Phishing Attack, etc. ) 2. Lateral Movement a. Steal Credentials b. Compromise more hosts & credentials Tier 0 Domain & Enterprise Admins 3. Privilege Escalation Tier 1 4. Execute Attacker Mission Server Admins a. Get Domain Admin credentials a. Steal data, destroy systems, etc. b. Persist Presence Tier 2 Workstation & Device Admins
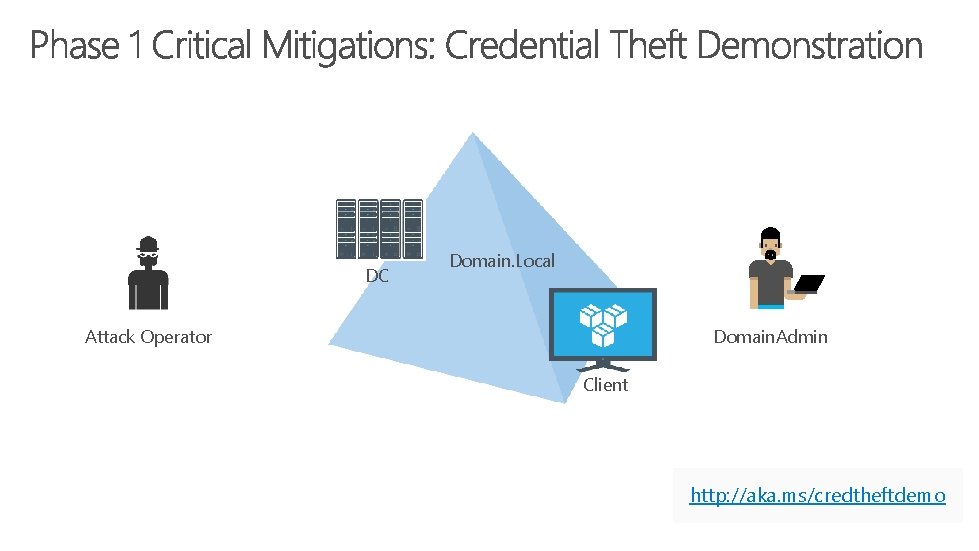
DC Domain. Local Attack Operator Domain. Admin Client http: //aka. ms/credtheftdemo
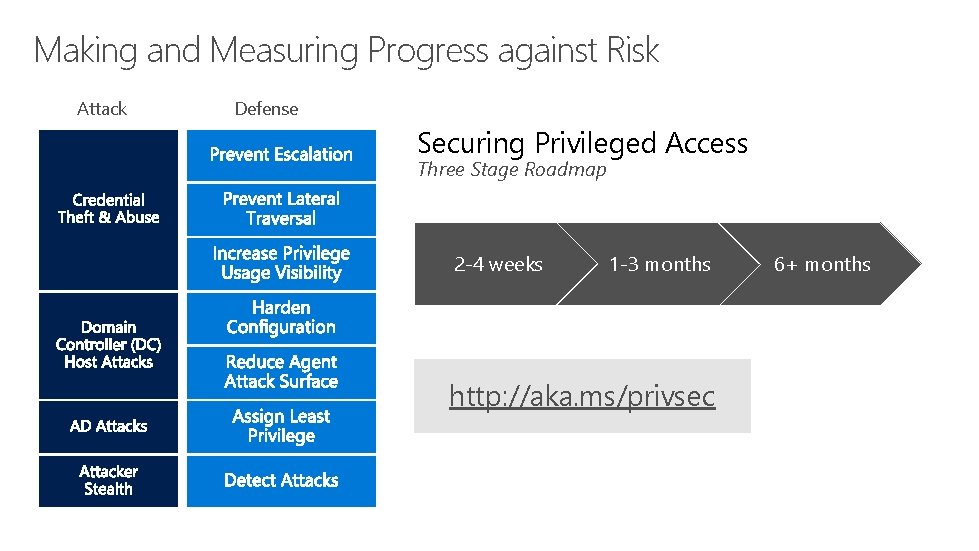
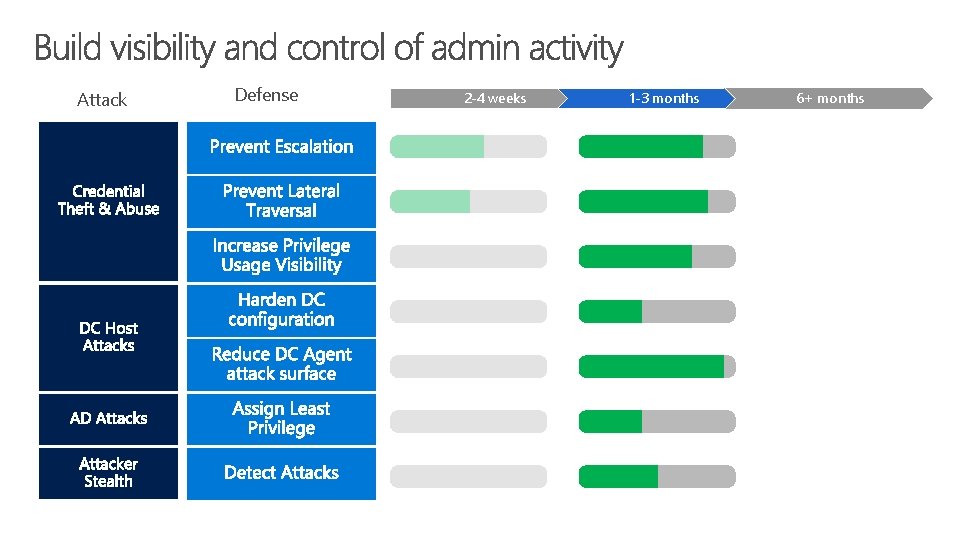
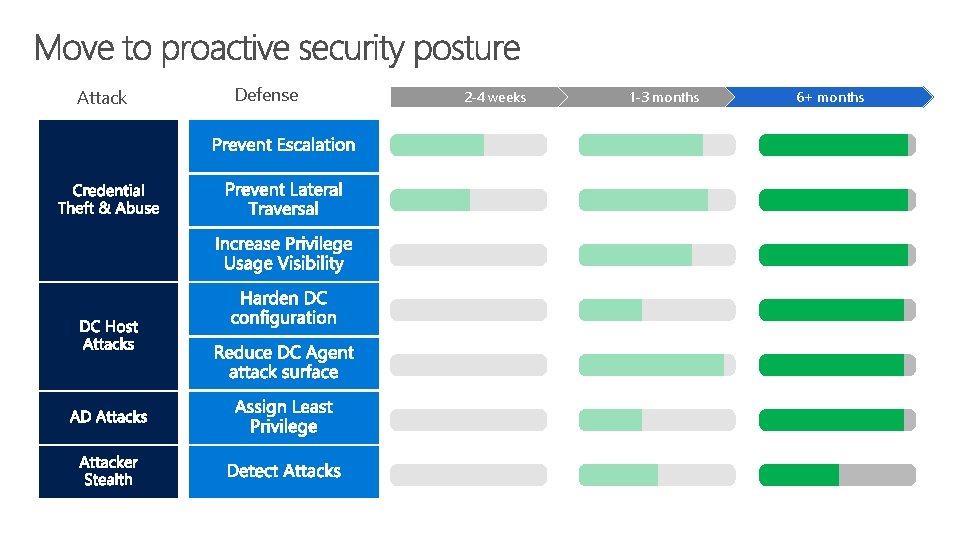
Making and Measuring Progress against Risk Attack Defense Securing Privileged Access Three Stage Roadmap 2 -4 weeks 1 -3 months http: //aka. ms/privsec 6+ months
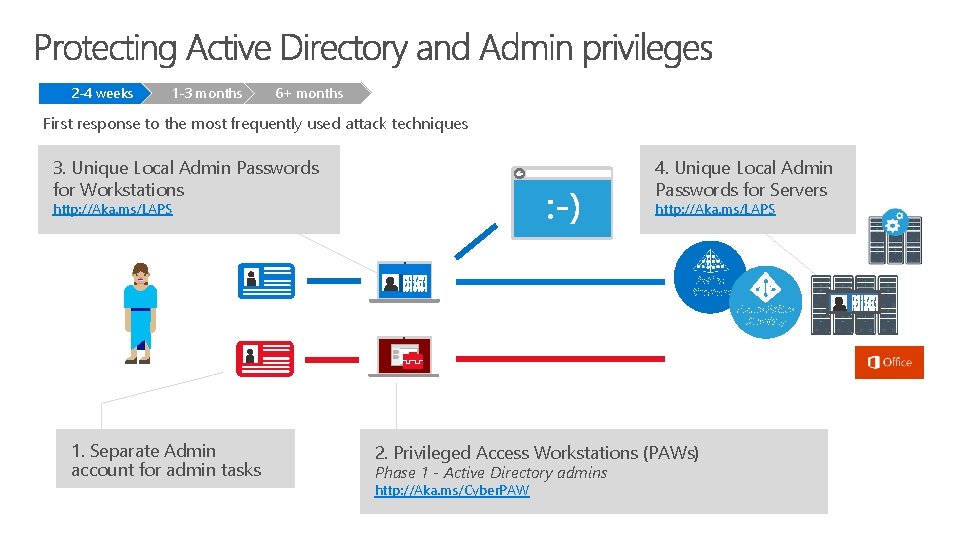
2 -4 weeks 1 -3 months 6+ months First response to the most frequently used attack techniques 4. Unique Local Admin Passwords for Servers 3. Unique Local Admin Passwords for Workstations http: //Aka. ms/LAPS Active Directory Azure Active Directory 1. Separate Admin account for admin tasks 2. Privileged Access Workstations (PAWs) Phase 1 - Active Directory admins http: //Aka. ms/Cyber. PAW

First response to the most frequently used attack techniques Attack Defense 2 -4 weeks 1 -3 months 6+ months Top Priority Mitigations
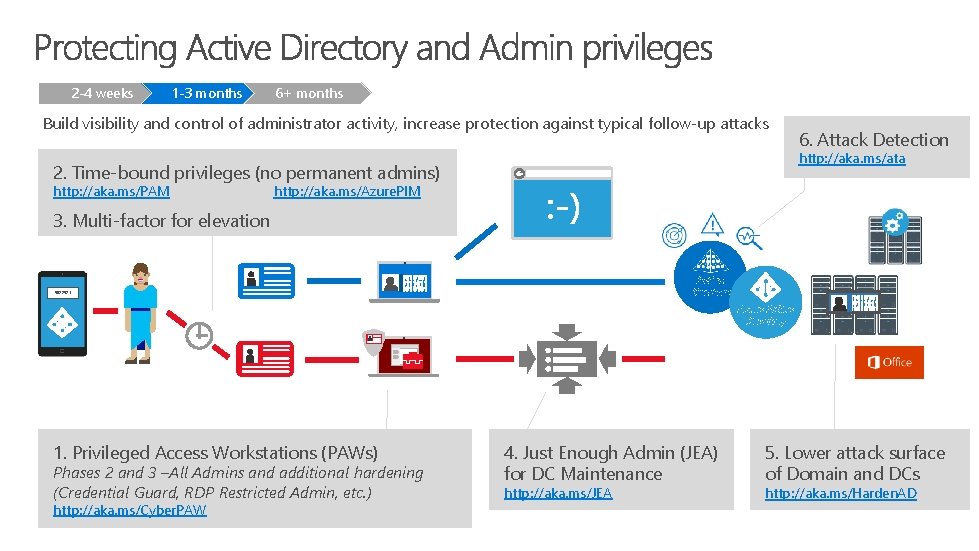
2 -4 weeks 1 -3 months 6+ months Build visibility and control of administrator activity, increase protection against typical follow-up attacks http: //aka. ms/ata 2. Time-bound privileges (no permanent admins) http: //aka. ms/PAM 6. Attack Detection http: //aka. ms/Azure. PIM 3. Multi-factor for elevation Active Directory 9872521 Azure Active Directory 1. Privileged Access Workstations (PAWs) Phases 2 and 3 –All Admins and additional hardening (Credential Guard, RDP Restricted Admin, etc. ) http: //aka. ms/Cyber. PAW 4. Just Enough Admin (JEA) for DC Maintenance http: //aka. ms/JEA 5. Lower attack surface of Domain and DCs http: //aka. ms/Harden. AD
Attack Defense 2 -4 weeks 1 -3 months 6+ months
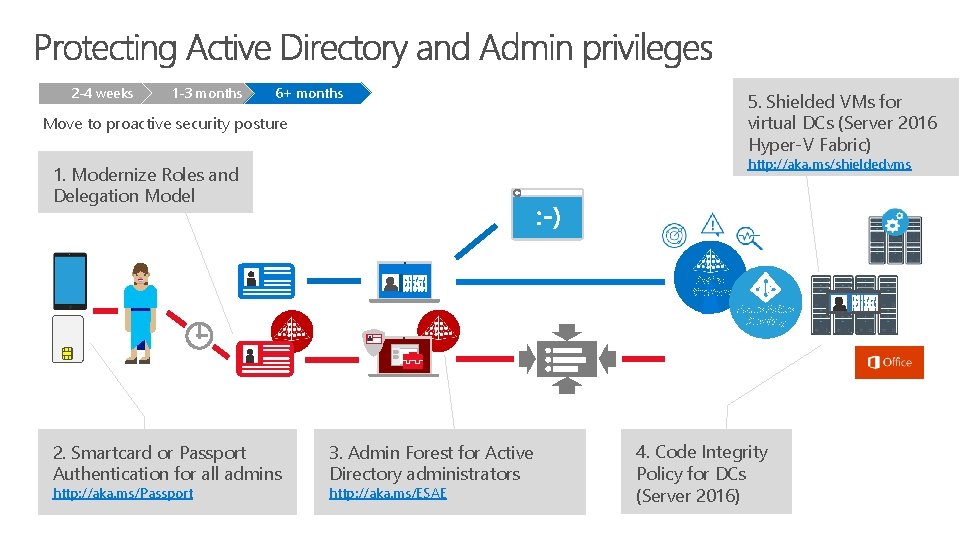
2 -4 weeks 1 -3 months 6+ months 5. Shielded VMs for virtual DCs (Server 2016 Hyper-V Fabric) Move to proactive security posture http: //aka. ms/shieldedvms 1. Modernize Roles and Delegation Model Active Directory Azure Active Directory 2. Smartcard or Passport Authentication for all admins http: //aka. ms/Passport 3. Admin Forest for Active Directory administrators http: //aka. ms/ESAE 4. Code Integrity Policy for DCs (Server 2016)
Attack Defense 2 -4 weeks 1 -3 months 6+ months


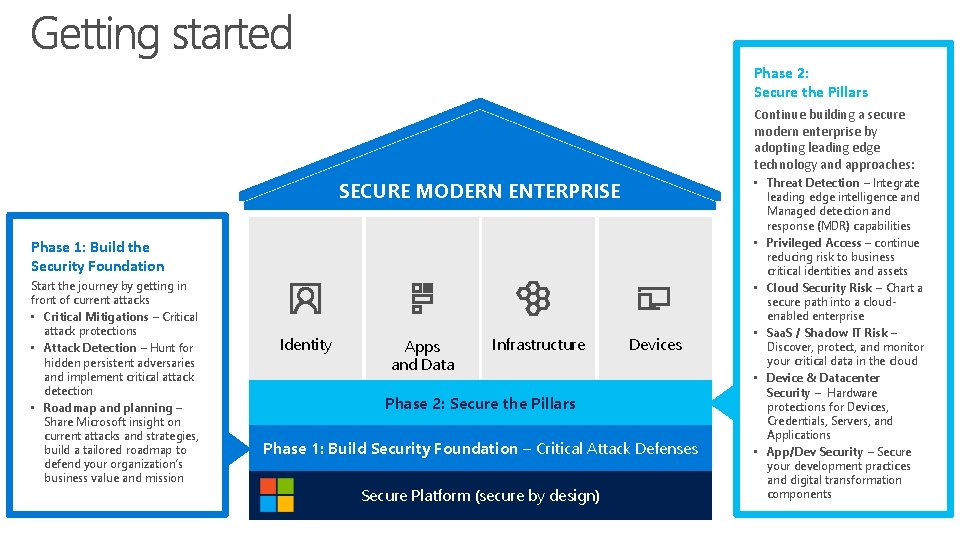
Phase 2: Secure the Pillars Continue building a secure modern enterprise by adopting leading edge technology and approaches: SECURE MODERN ENTERPRISE Phase 1: Build the Security Foundation Start the journey by getting in front of current attacks • Critical Mitigations – Critical attack protections • Attack Detection – Hunt for hidden persistent adversaries and implement critical attack detection • Roadmap and planning – Share Microsoft insight on current attacks and strategies, build a tailored roadmap to defend your organization’s business value and mission Identity Apps and Data Infrastructure Devices Phase 2: Secure the Pillars Phase 1: Build Security Foundation – Critical Attack Defenses Secure Platform (secure by design) • Threat Detection – Integrate leading edge intelligence and Managed detection and response (MDR) capabilities • Privileged Access – continue reducing risk to business critical identities and assets • Cloud Security Risk – Chart a secure path into a cloudenabled enterprise • Saa. S / Shadow IT Risk – Discover, protect, and monitor your critical data in the cloud • Device & Datacenter Security – Hardware protections for Devices, Credentials, Servers, and Applications • App/Dev Security – Secure your development practices and digital transformation components
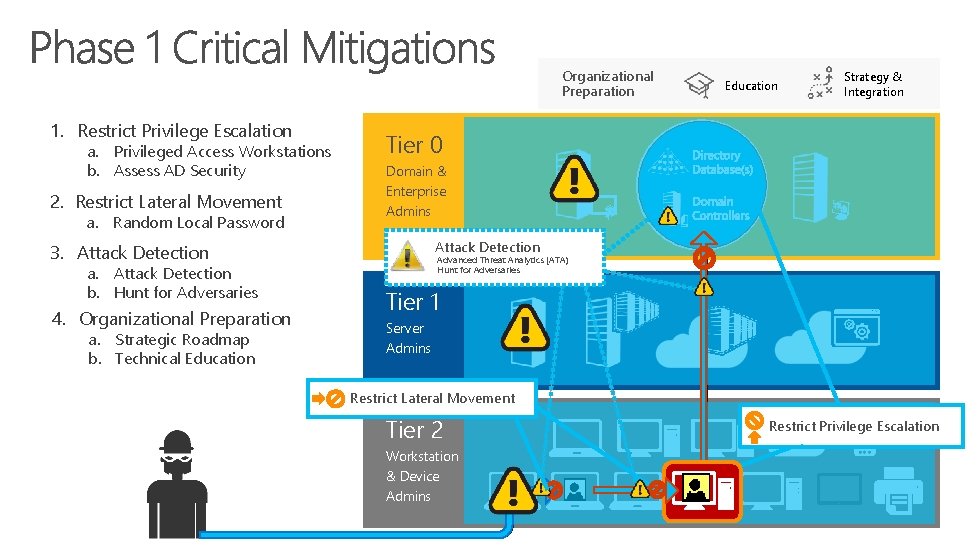
Organizational Preparation 1. Restrict Privilege Escalation a. Privileged Access Workstations b. Assess AD Security 2. Restrict Lateral Movement a. Random Local Password 4. Organizational Preparation a. Strategic Roadmap b. Technical Education Strategy & Integration Tier 0 Domain & Enterprise Admins Attack Detection 3. Attack Detection a. Attack Detection b. Hunt for Adversaries Education Advanced Threat Analytics (ATA) Hunt for Adversaries Tier 1 Server Admins Restrict Lateral Movement Tier 2 Workstation & Device Admins Restrict Privilege Escalation
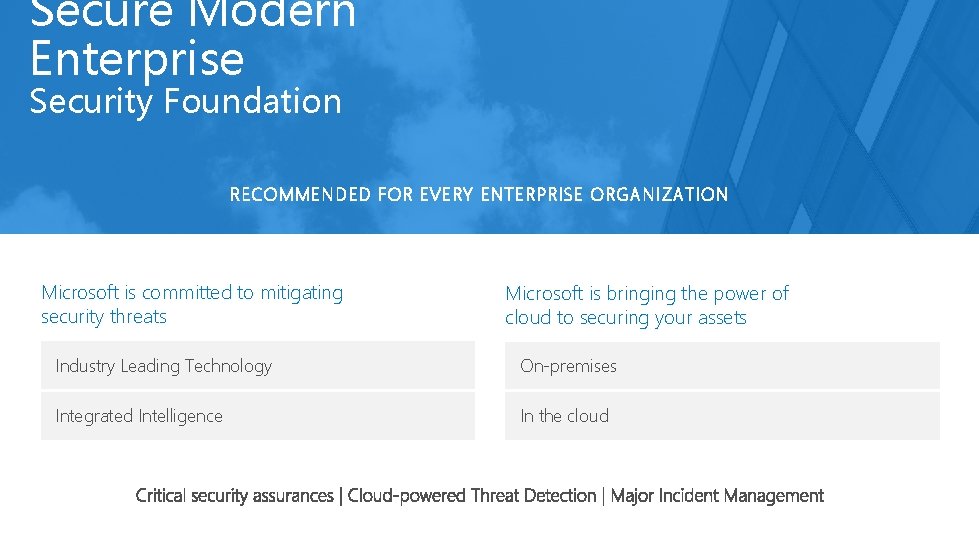
Secure Modern Enterprise Security Foundation RECOMMENDED FOR EVERY ENTERPRISE ORGANIZATION Microsoft is committed to mitigating security threats Microsoft is bringing the power of cloud to securing your assets Industry Leading Technology On-premises Integrated Intelligence In the cloud
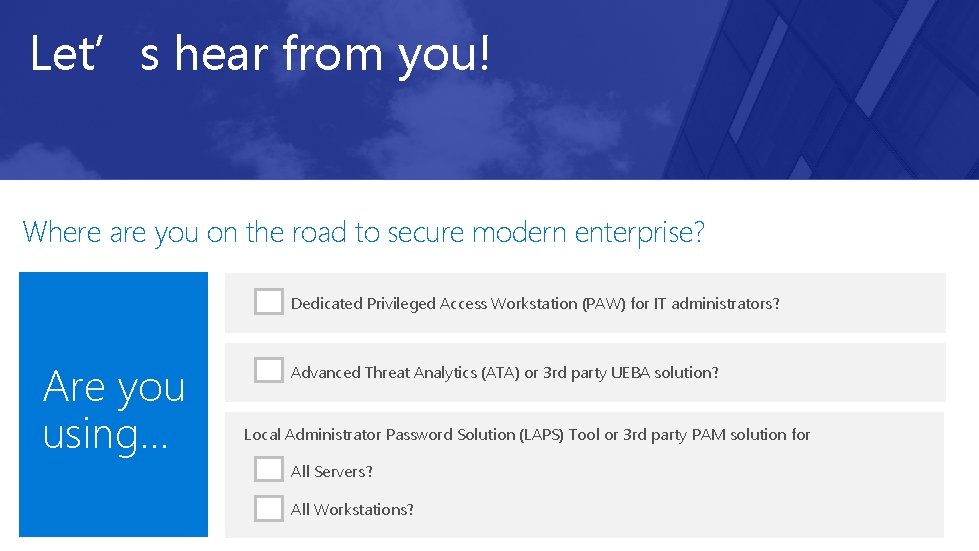
Let’s hear from you! Where are you on the road to secure modern enterprise? Dedicated Privileged Access Workstation (PAW) for IT administrators? Are you using… Advanced Threat Analytics (ATA) or 3 rd party UEBA solution? Local Administrator Password Solution (LAPS) Tool or 3 rd party PAM solution for All Servers? All Workstations?

www. microsoft. com/itprocareercenter www. microsoft. com/itprocloudessentials www. microsoft. com/mechanics https: //techcommunity. microsoft. com
http: //myignite. microsoft. com https: //aka. ms/ignite. mobileapp

- Slides: 25