Freeware Security Tools You Need Randy Marchany VA
















































![IP Filter Log Format Jul 30 01: 46: 52 myhost. vt. edu ipmon[147]: [ID IP Filter Log Format Jul 30 01: 46: 52 myhost. vt. edu ipmon[147]: [ID](https://slidetodoc.com/presentation_image/b9661dafa8bd568877353c1c4499b895/image-55.jpg)












































- Slides: 119

Freeware Security Tools You Need Randy Marchany VA Tech Computing Center Blacksburg, VA 24060 Marchany@vt. edu 540 -231 -9523

Suggested Strategy F Use freeware tools to gain experience with your system/network environment. F Gain experience with the features provided by these tools in order to better analyze a vendor tool. F Freeware tools provide a good short-term solution. F Vendor tools may provide better long-term solution.

The Tools F Audit/Port Scanning Tools – – – F Nessus Saint Sara Nmap, strobe Tripwire, AIDE “Personal” Firewall – TCP Wrappers – Portsentry, ipfilters – Zone. Alarm, Black. Ice, Neo. Works

The Tools F Syslog Scanners – Logcheck F Sniffers – Snoop, iptrace, tcpdump – Netwatch (NT) – Snort

The Tools F Sysadmin Tools – Big Brother – Password Checkers • Crack, nt-crack, l 0 phtcrack, npasswd, passwd+ – Lsof, inzider (NT) – Sudo (unix) F Remote Control Tools – VNCviewer F Homegrown Tools – Network Mgt Tools that can be used for Incident Response

Audit/Port Scan Tools F These tools can be used to scan your systems and network for vulnerabilities. F Some tools can perform integrity checks on designated files. F They have very good reporting tools usually based on HTML.

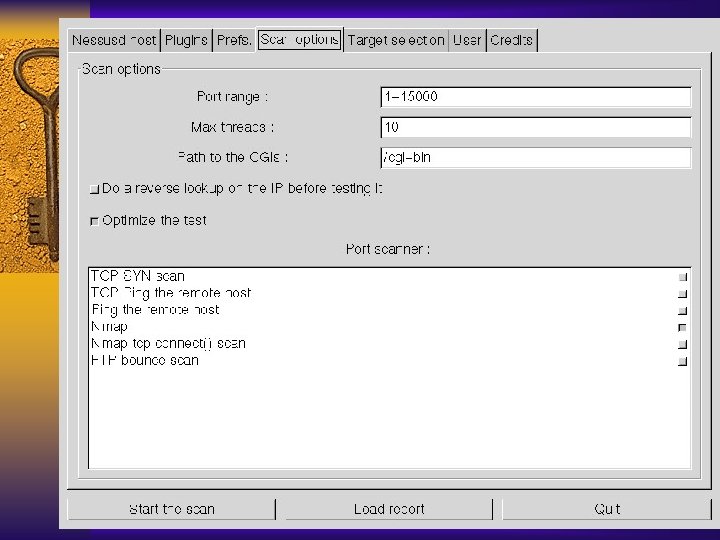
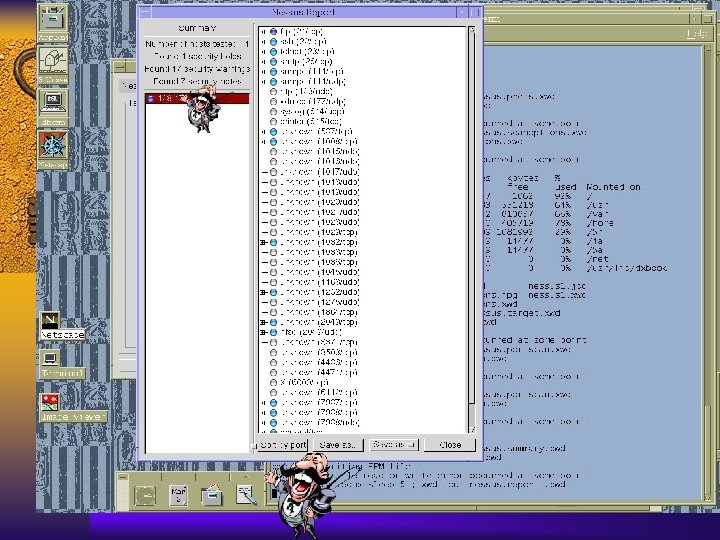
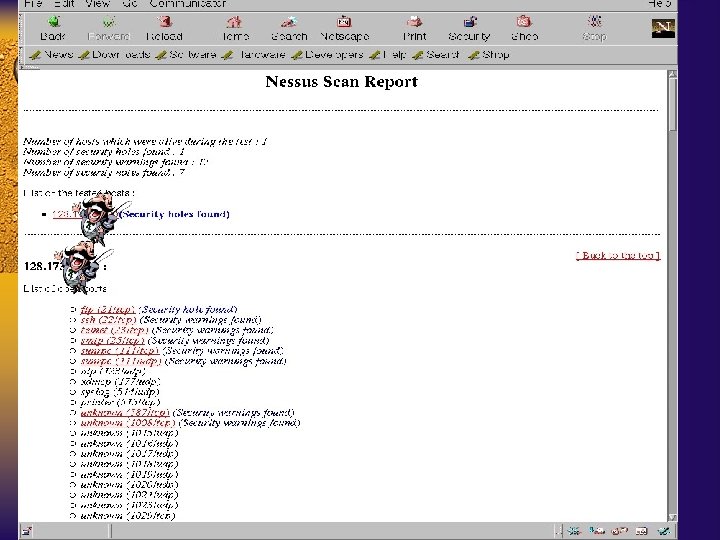
Nessus F Available from www. nessus. org F Best of the scanning tools F Easy to build for Linux, harder for Solaris, need to work on other OS. F Requires GNU tools F Provides HTML based reports F Has distributed architecture: clients (Windows, Unix) & engines (Unix only)

Nessus – Building It F Linux – Download the RPMs – Add nessus user – Start up nessusd daemon – Start up nessus client – Start testing

Nessus – Pros/Con F Pro – Easy to install if you have linux – Most comprehensive tests for your money F Con – Not that easy to understand at first – Non-linux builds require GNU software – Some inconsistency in quality of checks – Must use Unix server for specific user accounts






X






SAINT F Based on SATAN, developed by World Wide Security, Inc. (www. wwdsi. com) F Security Administrator’s Integrated Network Tool – Gathers info on remote hosts/nets – Looks at finger, NFS, NIS, ftp, tftp, rexd, statd – Can run heavy, moderate or light probes on targets. F Will check for the SANS Top 10 Threats




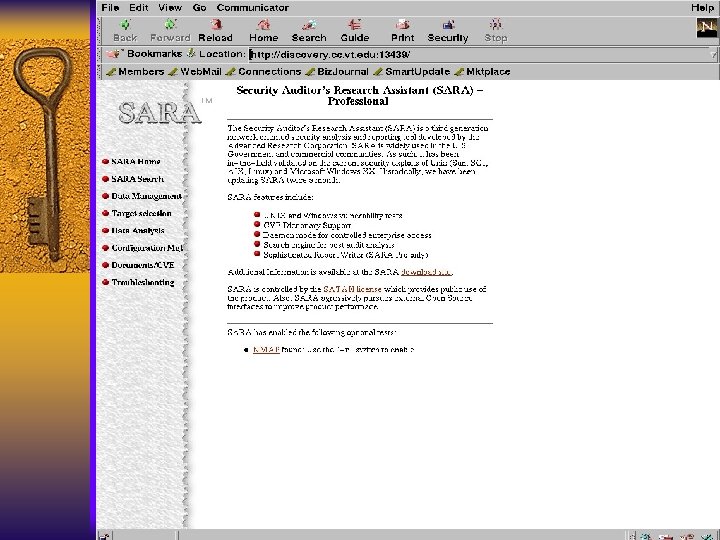
SARA F Security Auditor’s Research Assistant – www-arc. com/sara F Checks for SANS Top 10 Threats F Does Unix/Windows vulnerability tests F Has CVE dictionary support F Search engine for post audit analysis F Has a Report Writer





Port Scanning Tools F Strobe was one of the earliest port scanning tools. – Available from ciac. llnl. gov F Nmap is the more sophisticated grandson of strobe – Available from www. insecure. org



Tripwire F Available from www. tripwire. com F First of the file integrity checkers F Unix and NT versions available – Network capable versions available F Academic version is free. Commercial and NT versions are not. F Useful in finding trojan programs

Tripwire F Generates a “signature” for each file based on checksums and other characteristics. F These signatures are stored in a database file that should be kept offline. F This is the baseline. F Latest threat involves dynamic exec redirection. This is part of the newer Kernel Module Rootkits.

Tripwire F List of files to check: tw. config – All files in a directory will be checked. – Can prune directories from the check step. – Can examine just the directory and nothing else. – Can check by access time but not recommended since you’ll get a report of everything that changed. Everything!

Tripwire F To initialize the DB: tripwire –initialize F Update DB interactively: tripwire -interactive F Non-interactive DB update: tripwire – update <FN>

Tripwire F Security Issues – Need to protect the DB – Need to protect the vulnerable executables F Advantages – Simple interface, good choice of crypto hash functions, good all-around tool F Disadvantages – Kernel mod attacks, initial tw. config takes some time to customize, NT version is good but costs $$$, no network security


Personal Firewall Tools F These tools monitor connection attempts to your system and give you the option of allowing or denying the access F They log the connection attempt to standard log files F More valuable than real Firewall, IMHO.

Portsentry/TCP Wrappers Available from www. psionic. com F TCP Wrappers available from ciac. llnl. gov and a ton of other sites F Any host that scans a list of “banned” ports is placed in an /etc/hosts. deny file F Need TCP Wrappers installed on the machine F – Tcpwrappers logs attempts to connect to services

TCP Wrappers F Everyone should buy Wietse Venema dinner for writing this tool. F Purpose – Log network connections to a system – Allow you to filter who connects to the system F Needs an inetd-like program to act as the dispatcher of network services

TCP Wrappers Features F Allows you to monitor/filter incoming requests for SYSTAT, FINGER, FTP, TELNET, R-Commands, TFTP, TALK and other network services. F Provides access control to restrict what systems connect to what network daemons. F Provides some protection from host spoofing

TCP Wrapper Installation F Easy to do F “Advanced Installation” easier than “Easy Installation” IMHO F Install done by Makefile – make <os-type> F Creates 5 modules that are ready to use.

TCP Wrappers F 4 components – – Tcpd – the actual wrapper program Tcpdmatch, tcpdchk – ACL testing programs Try-from – tests host lookup function Safe-finger – a better version of finger Logs hostname, IP address and username (identd if possible) via syslog facility. Typically, it logs to the mail facility logs F Change this by editing Makefile: F – FACILITY=LOG_AUTH – FACILITY=LOG_WARN

TCP Wrappers Access Control is enabled by default. F 2 files F – /etc/hosts. deny – restrict access if IP addr here – /etc/hosts. allow – allow access if IP addr here • Can restrict to username@host if services are enabled Reverse lookup is done. Paranoid selection terminates the connection immediately if there’s a mismatch. F Set KILL_IP_OPTIONS in Makefile to refuse connections that use source routing. This prevents IP spoofing although your routers should do this. F

TCP Wrappers F IDENT service – Remote username lookup required remote host to run ident (RFC 1413) protocol. – Works only for TCP not UDP F Limitations – TCP – checks the 1 st connection for each instance of the daemon – UDP – 1 st datagram only for the service – RPC/TCP – no checking since portmapper does this.

TCP Wrappers F Advantages – Logs and applies access controls to remote connections – Lets you define which daemons are wrapped – Does good reverse lookup on hosts F Disadvantages – – Ident service not reliable Only looks at network daemons spawned by inetd Doesn’t wrap ALL services (RPC) Could give a false sense of security

Portsentry F Available from www. psionic. com F Monitors ports and performs an action when an attempt to access the port is made. F Usually access is denied to the probing systems. F Monitors TCP and UDP traffic. A little more flexible than TCP Wrappers

Portsentry Configuration Files F Portsentry. conf contains the list of ports to be monitored. F 3 levels of paranoia


IP Filter Software package that can do NAT or basic firewall services. F Designed to be used as a loadable kernel module but can be incorporated into a Unix kernel F Can be configured to do IP Accounting (count # bytes), IP Filtering or IP authentication or NAT. F http: //coombs. anu. edu. au/~avalon/ip-filter. html F

IP Filter F Can explicitly allow/deny any packet. F Distinguishes between multiple interfaces. F Filters by IP network, hosts or protocol. F Filters by port number or port range. F Logs the following: – TCP/UDP/ICMP/IP packet headers – First 128 bytes – Pass or blocked status

IP Filter F Statistics collected include: – Packets blocked – Packets used for accounting (packet count) – Packets passed – Packets logged – Inbound/outbound packet information

![IP Filter Log Format Jul 30 01 46 52 myhost vt edu ipmon147 ID IP Filter Log Format Jul 30 01: 46: 52 myhost. vt. edu ipmon[147]: [ID](https://slidetodoc.com/presentation_image/b9661dafa8bd568877353c1c4499b895/image-55.jpg)
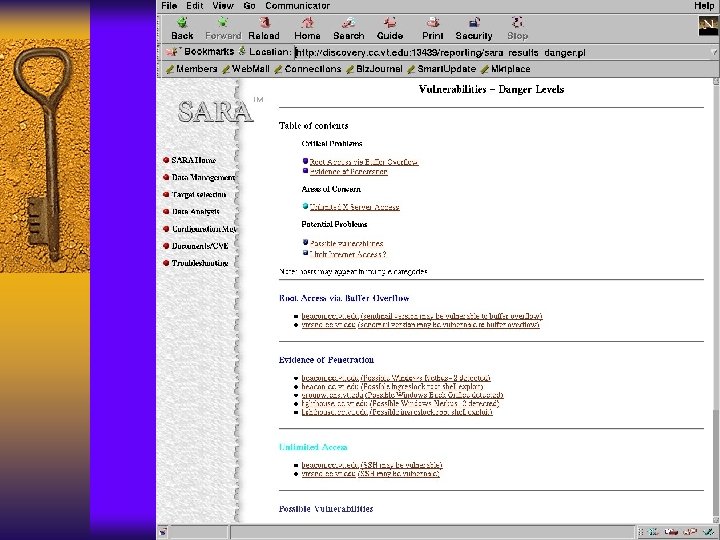
IP Filter Log Format Jul 30 01: 46: 52 myhost. vt. edu ipmon[147]: [ID 702911 local 0. warning] 01: 46: 52. 196772 hme 0 @0: 5 b 194. 143. 66. 126, 21 ->198. 82. 255, 21 PR tcp len 20 40 -S IN Jul 30 01: 47: 03 myhost. vt. edu ipmon[147]: [ID 702911 local 0. warning] 01: 47: 03. 269595 hme 0 @0: 5 b 194. 143. 66. 126, 21 ->198. 82. 255, 21 PR tcp len 20 40 -S IN Jul 30 05: 53: 51 myhost. vt. edu ipmon[147]: [ID 702911 local 0. warning] 05: 53: 50. 699235 hme 0 @0: 5 b 203. 90. 84. 163, 1781 ->198. 82. 255, 21 PR tcp len 20 60 -S IN

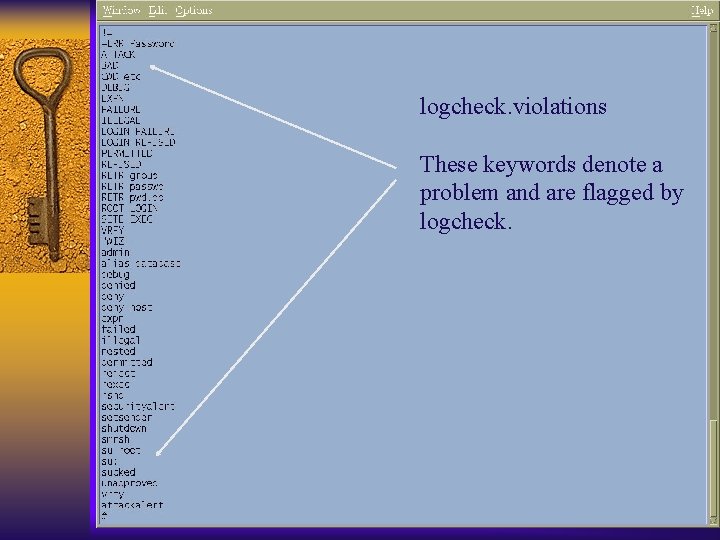
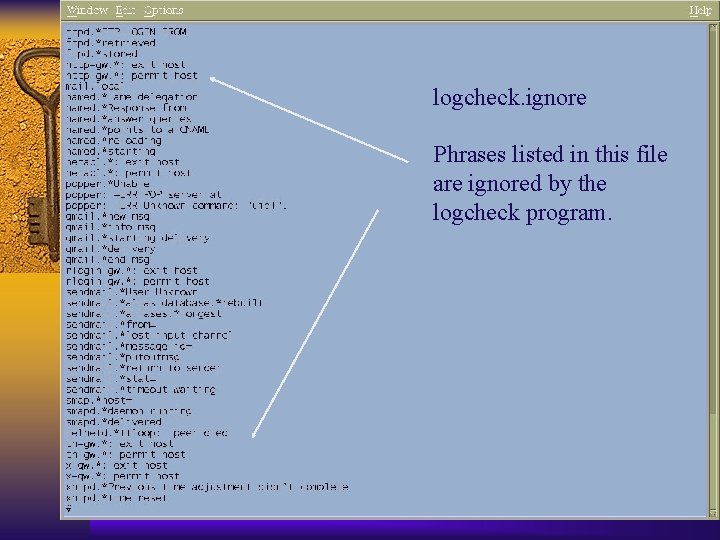
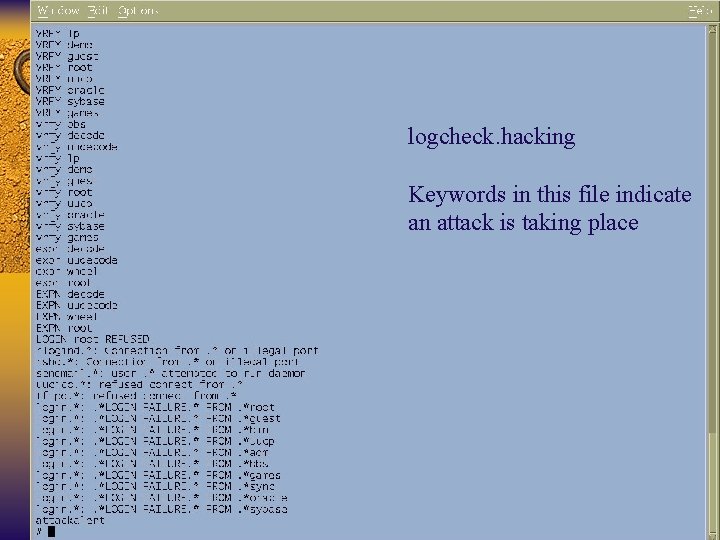
Logcheck F Available from www. psionic. com F Syslog keyword scanner F When it matches something, it does something – Send email – Page someone – Run a command

logcheck. violations These keywords denote a problem and are flagged by logcheck.

logcheck. ignore Phrases listed in this file are ignored by the logcheck program.

logcheck. hacking Keywords in this file indicate an attack is taking place


Zone Alarm F Available from www. zonelabs. com F Not quite free F Client based, application level firewall F Designed to prevent unauthorized sending and receiving of packets to your workstation F Good defense against trojans

Basic Installation Steps F The following steps were developed by Marc Debonis for our site. – – – – – Download latest version from http: //www. zonelabs. com Run the installer, zonealarm. exe Click Next, click Next Enter name, company and email (can be invalid) Uncheck both boxes Click Next , click next, click finish, click start Check “don’t show this message again” box Click OK and reboot if necessary Zone Alarm is installed

Configuring Zone Alarm F ZA requires you authorize each & every application that attempts to send receive information to/from your network connection. F Default is BLOCK. This pops up a window asking what to do

Basic Setup Click the arrow in ZA box that points down and to the right F Click the security button F Verify local security is set to MEDIUM F Verify internet security is set to HIGH F Click the advanced button F Do NOT put a checkmark next to your adapter, OW, all machines in your subnet will be considered to be in your local zone F Click OK F




Black Ice Defender Available from www. networkice. com F Workstation Version F – End-user PC with a single connection – Tuned for common attacks to workstations F Server Version – Additional NT and W 2 K attacks signatures Ice. Pac Suite allows multiple agents to be managed from a single host. Can install agents remotely. F Not quite free F


Neo. Watch Available from www. neoworx. com F Another Personal FW type tool for Windows systems. F Does traceback to the originating site. F Similar features as Zone Alarm and Black Ice Defender F Can send data to a central site. F Not quite Free $39. 95. Trial version is free for 30 days F




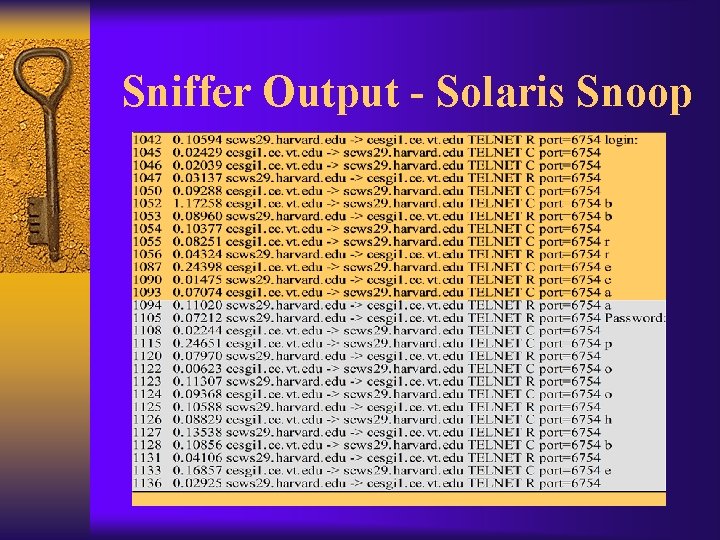
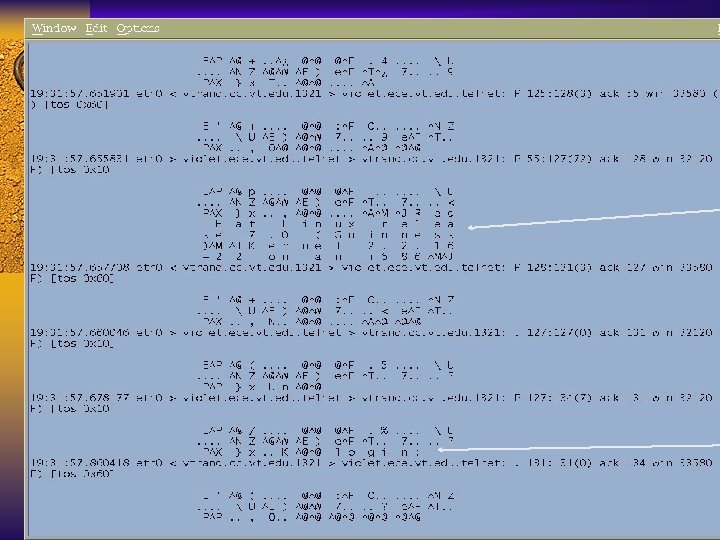
Sniffers: snoop, iptrace, tcpdump, snort F Some systems have builtin sniffers – Solaris - snoop – AIX - iptrace – Linux - tcpdump – NT/2000 - netwatch F Tcpdump is the generic sniffer for those systems with no builtin sniffer

Sniffer Output - Solaris Snoop

Tcpdump Example

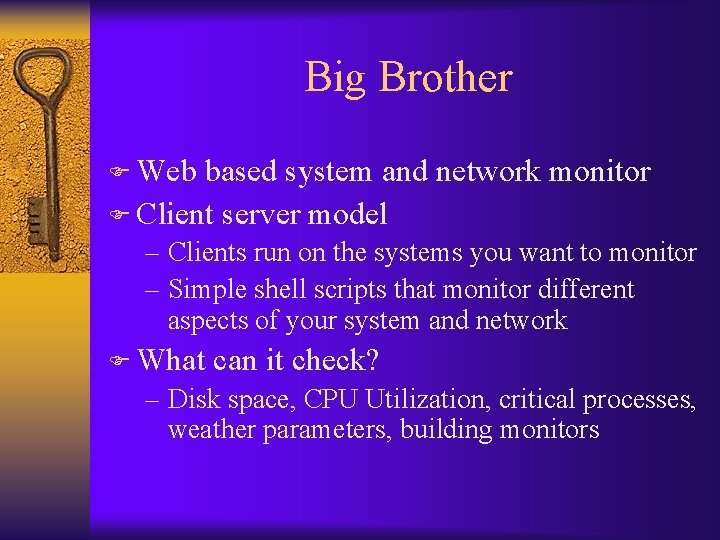
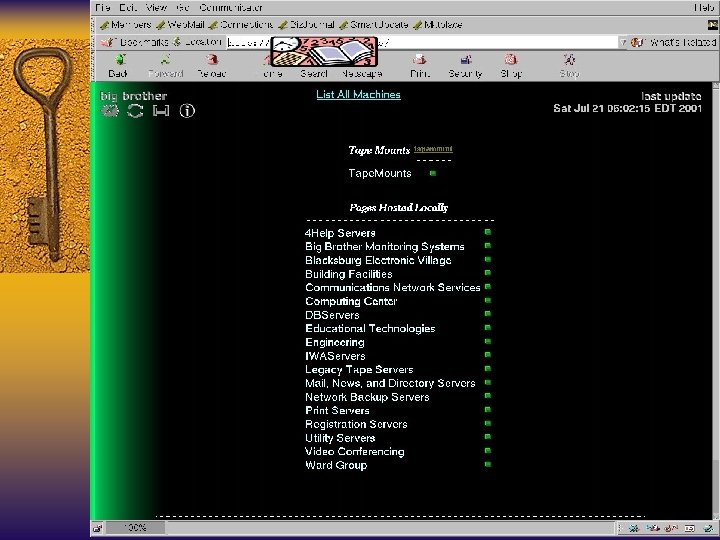
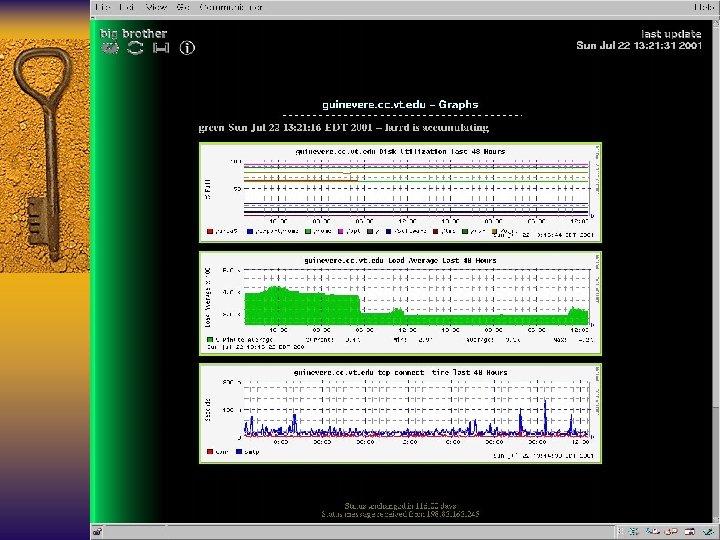
Big Brother F Web based system and network monitor F Client server model – Clients run on the systems you want to monitor – Simple shell scripts that monitor different aspects of your system and network F What can it check? – Disk space, CPU Utilization, critical processes, weather parameters, building monitors

Big Brother F Color coded WWW page showing a matrix of machines and monitored functions F Notifies sysadmins by email, pager, SMS. F System requirements – Unix – www server, /bin/sh, C compiler to port BB – NT – v 4. 0 with SP 3 minimum, Intel or Alpha platforms.




Big Brother F Installation Steps – – – cd install. /bbconfig cd. . /src Make install cd. . /etc • Edit bb-hosts, bbdef. sh, bbwarnrules. cfg – cd. . –. /runbb. sh start

Big Brother F Can monitor more service by modifying bb -network. sh F BB shows historical data. Drilling down a host page and clicking on the history buttons shows the last 24 hr stats. F Doesn’t need to run as root. Run as ‘bb’. F Restricts incoming connections by ACL.

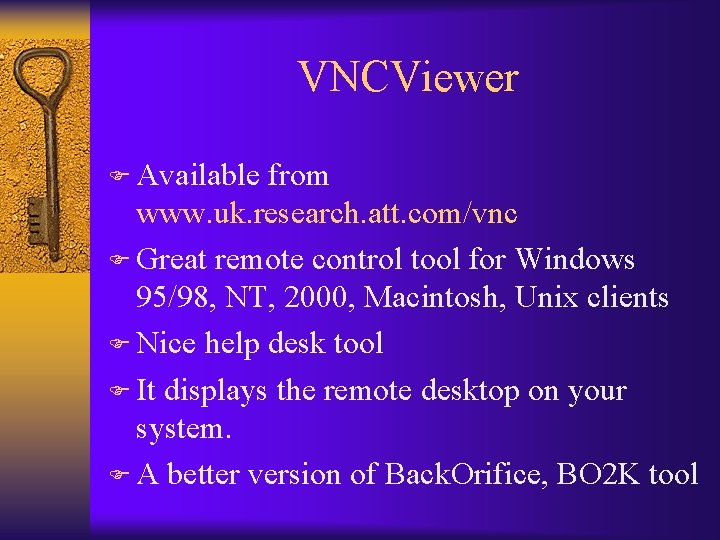
VNCViewer F Available from www. uk. research. att. com/vnc F Great remote control tool for Windows 95/98, NT, 2000, Macintosh, Unix clients F Nice help desk tool F It displays the remote desktop on your system. F A better version of Back. Orifice, BO 2 K tool




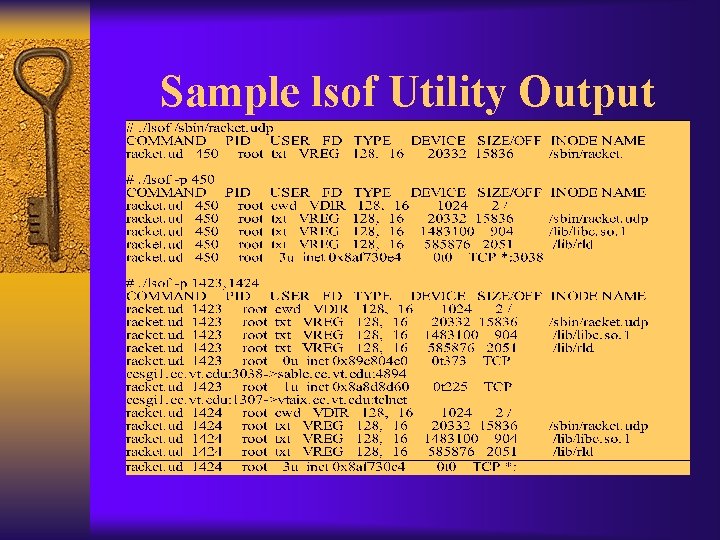
Lsof, inzider F These programs list the processes running on a system. F They also list the files opened by those processes. F Useful in finding where a sniffer log file is located

Sample lsof Utility Output

Sysadmin Tools F Sudo – Unix access control is all (root) or nothing (user). – Some commands (backup, restore) are restricted to root but are really an OPER class command. You don’t want an operator to have root access but you want them to do backups. – Sudo lets you set up this “pseudo” privilege scheme.

Sudo F Sudo uses user identity and host to restrict the commands the user can run in “root” mode. F It is a restricted root shell. F User is prompted for a special password that allows them to run the command.

Sudo F The sudoers files lists the commands, shells, hosts that a user can execute commands F Should always list the full path name for the commands F Notifies sysadmins if illegal uses of sudo is attempted. F Notifies sysadmins if user in sudoers tries to run a restricted command

Sudo F Advantages – Good warning if someone tries to use it incorrectly. – Easy to configure for multiple machines – Adequate internal security checks • Check for “. ” in PATH • Removes LD* variables before execution F Disadvantages – Works with root userid only. Can’t use with other userids. – Doesn’t handle commands that use a subshell to spawn other commands

Proactive Password Tools Most newer OS allow you to set password rules in config files. F Crack is still the best of the bunch. F Npasswd and passwd+ are two older but still effective tools. F Npasswd is a good tool for those who don’t want to spend a lot of time configuring a password checker F Passwd+ requires more configuration time. F

Crack The first of the really good password crackers. Available on the net for the past 10 years. F Easy to customize. Works on non-shadow password files. F Use a preprocessor to rebuild in old format or use NIS, NIS+ F Can be distributed among systems F http; //www. users. dircon. co. uk/~crypto/ F

npasswd Uses ASCII dictionaries or DBM format dictionaries. F Programs to build directories included. F If the password is in the dictionary, it’s rejected. Case and reversed word checks are done as well F Does singlecase (Yes/No) checks F – Allow passwords in one case. Default = No. F Does Control Character (Yes/No) checks. – Allows passwords with ASCII control characters in them. Default = Yes. F Does min/max length checks.

npasswd F Checks for 3 sequential occurrences of the same character. This value can be modified. F Does illegal character check. (^C, ^D, ^G, ^J, ^M, ^O, ^Q, etc. F Good, quick easy tool to use.

Home Grown Tools F Network Mgt Group developed a couple of tools for their use. F Our CIRT can use the same tools to track an attack in our network. F Our Netadmins controls the ENTIRE University net and developed these tools to help them manage, fix and bill usage of net resources. SQL front ends to Oracle DB.











Using the Tools – A Strategy F Preparation F Detection F Containment F Eradication F Recovery F Followup

Preparation F Unix Host Systems – Install TCP Wrappers, Portsentry, logcheck, tripwire, lsof, ipfilter F NT/2000 – Inzider, syslog converters F Network – Ingress, egress filters in place – Router logs in place

Detection F Portsentry, TCP wrappers, Personal Firewall tools usually send the first alarm. F Network router filters may trigger an alarm as well. F Once an event is detected, reaction mechanisms are enabled

Containment F Detection tools give the source IP address. F Router blocks may be enabled to prevent additional attacks. F HC++ tool used to isolate offending system F Portsentry or PFW tools prevent further access to the systems

Eradication F HC++ tool used to shut off internal port. F Router blocks on external IP address. F Tripwire used to remove offending files. F Network backup software can be used to verify this. Why? Most network backup software does incremental backups so they can capture a newly installed file.

Recovery F “Jumpstart” style OS installation F Network and regular backup software F File servers may limit the damage

Followup F See what components worked. – Could additional scanning detect the holes? – How fast did the reaction mechanisms work? – Internal network tools work? – Backup procedures work? – What didn’t work? Why? How?

Summary F There are some excellent freeware tools that will help you with sysadmin and security issues at your site. F Use these tools to gain experience in evaluating vendor tools. F A combination of vendor and freeware tools is desired F There are MORE tools out there.

Where to Get the Tools F Http: //ciac. llnl. gov – TCP Wrappers, crack, tcpdump, lsof F Http: //www. wwdsi. com – SAINT F Http: //www. www-arc. com/sara – SARA F Http: //www. tripwire. com – tripwire

Where to Get the Tools F Http: //www. psionic. com – Logcheck, portsentry F Http: //www. uk. research. att. com/vnc – VNCViewer F Http: //www. insecure. org – Nmap F Http: //www. ssh. org – SSH

Where to Get the Tools F www. nessus. org – Nessus F http: //packetstorm. securify. com defunct) (now