FREENET UDAYA S PISIPATI 022608 CONTENTS Introduction Design











- Slides: 19

FREENET UDAYA S PISIPATI 02/26/08

CONTENTS § § § Introduction Design goals Architecture § § § § Protocol details Performance Analysis § § § Basic model Keys in searching Retrieving data Storing data Managing data Adding nodes Small world model Security Conclusion

INTRODUCTION § Drawbacks of current networked systems: Privacy Availability § Systems offering greater security and reliability are needed § Freenet -distributed information storage and retrieval system designed to address these concerns § Preliminary implementation can be downloaded from http: //www. freenetproject. org/

DESIGN GOALS Anonymity for both producers and consumers of information Deniability for stores of information Resistance to attempts by third parties to deny access to information Efficient dynamic storage and routing of information Decentralization of all network functions

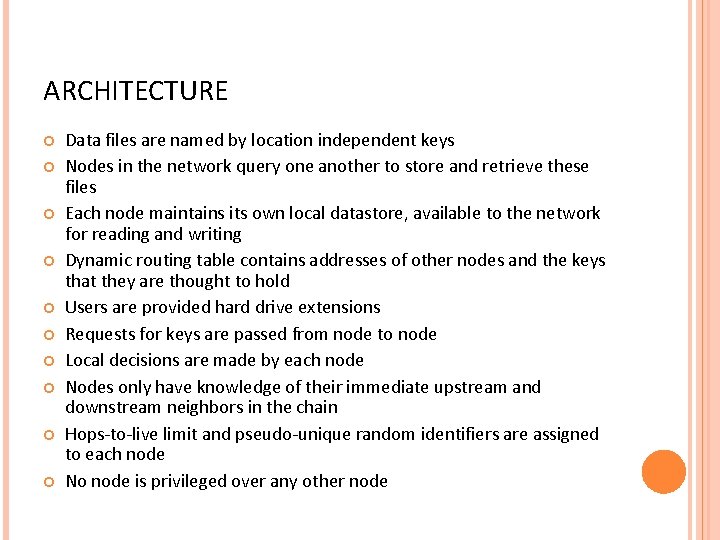
ARCHITECTURE Data files are named by location independent keys Nodes in the network query one another to store and retrieve these files Each node maintains its own local datastore, available to the network for reading and writing Dynamic routing table contains addresses of other nodes and the keys that they are thought to hold Users are provided hard drive extensions Requests for keys are passed from node to node Local decisions are made by each node Nodes only have knowledge of their immediate upstream and downstream neighbors in the chain Hops-to-live limit and pseudo-unique random identifiers are assigned to each node No node is privileged over any other node

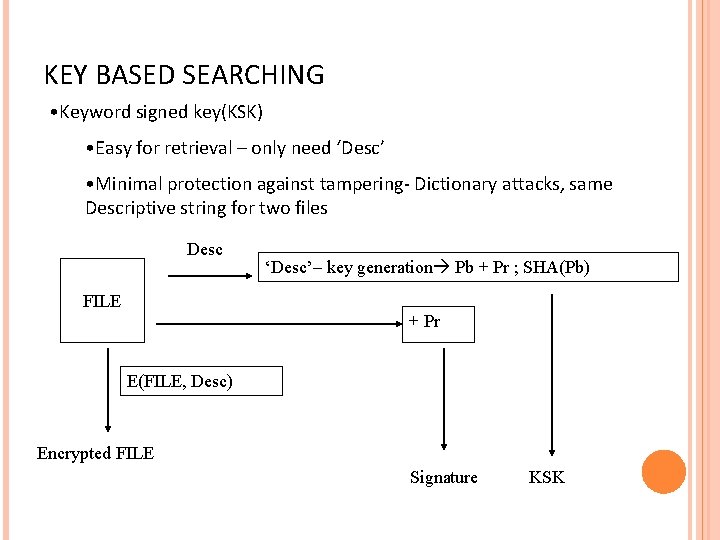
KEY BASED SEARCHING • Keyword signed key(KSK) • Easy for retrieval – only need ‘Desc’ • Minimal protection against tampering- Dictionary attacks, same Descriptive string for two files Desc ‘Desc’– key generation Pb + Pr ; SHA(Pb) FILE + Pr E(FILE, Desc) Encrypted FILE Signature KSK

KEYS AND SEARCHING…. . Problems with KSK – flat namespace (collisions), key squatting, dictionary attacks Signed Subspace Key (SSK) � Randomly generated key pair namespace ID � SSK = SHA(‘D’) XOR SHA(Pb) ) � Pr used to sign the file, file encrypted by using D � (-)Publish – subspace Pb + ‘D’ � (+)Owner can construct hierarchical space of arbitrary depth - using indirect files

KEYS AND SEARCHING… Content Hash Keys (CHK) = SHA (file contents) � Files encrypted by a random encryption key � Publish CHK + decryption key � CHK + SSK easily updateable files 2 step process – publish file, publish pointer Results in pointers to newer version Older versions accessed thru CHK � Can be used for splitting files

KEYS AND SEARCHING: INSERT, UPDATE AND SPLIT Insert a file under its CHK An indirect file (whose contents are the CHK) is inserted under the SSK Retrieval possible in two steps when SSK is known For updating the file, insert a new version under its CHK (different from the CHK of the old version) Insert a new indirect file under the original SSK pointing to the updated version Key collision occurs when the insert reaches the node which possesses the old version Check the signature on the new version and replace the old version if the signature is valid and most recent Split the file into a number of parts and insert each part under a CHK, also create an indirect file to point to the individual parts

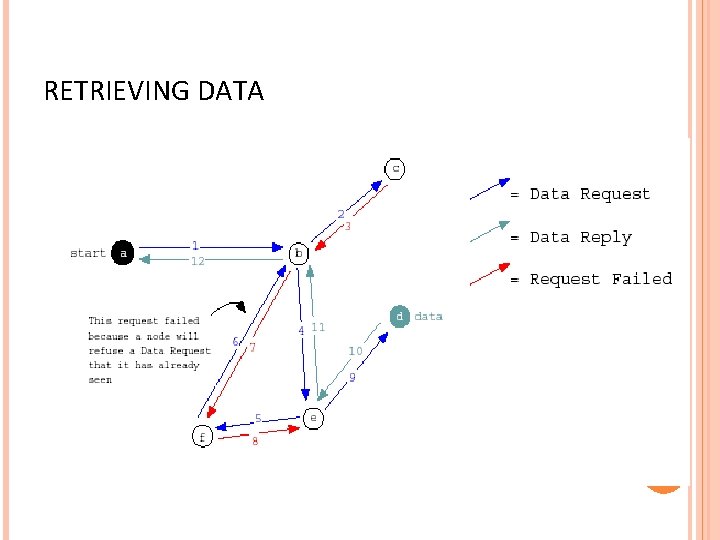
RETRIEVING DATA

STORING DATA User calculates the binary file key for the file and sends a message to the his/her own node specifying the proposed key and a hops to live value The node checks to see if the key is already taken, if the key is found, the node returns the file like the result of a search, the user now chooses a different key and repeats the procedure If key is not found, the user node looks up the nearest key in its routing table and forwards the insert to the corresponding node If the hops-to-live limit has been reached without a key collision being detected, an “all clear” result will be propagated to the original inserter

MANAGING DATA Node storage is managed as an LRU cache When a new file arrives which would cause the datastore to exceed the designated size, LRU files are evicted in order until there is room Advantage: This method allows outdated documents to fade away naturally

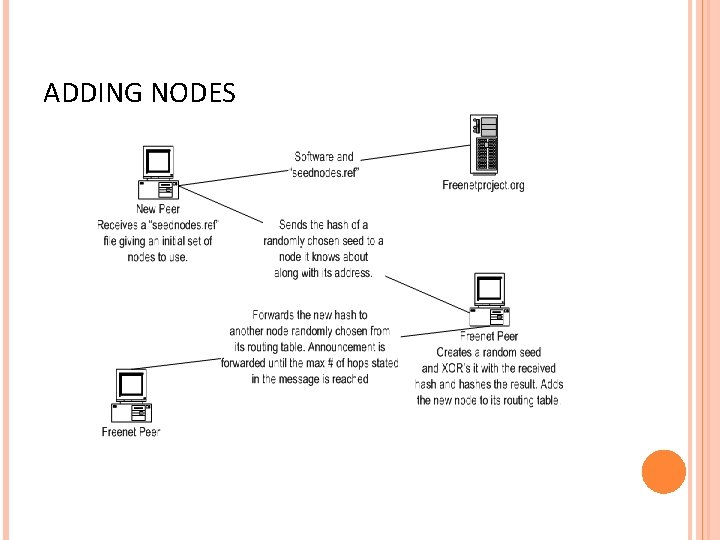
ADDING NODES

PROTOCOL DETAILS Packet oriented protocol Request. Handshake Reply. Handshake Request. Data Reply. Restart Send. Data Reply. Not. Found Request. Insert

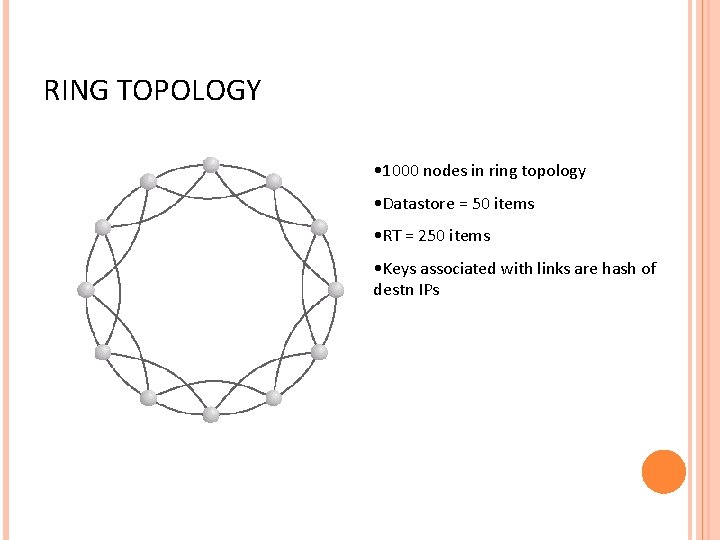
RING TOPOLOGY • 1000 nodes in ring topology • Datastore = 50 items • RT = 250 items • Keys associated with links are hash of destn IPs

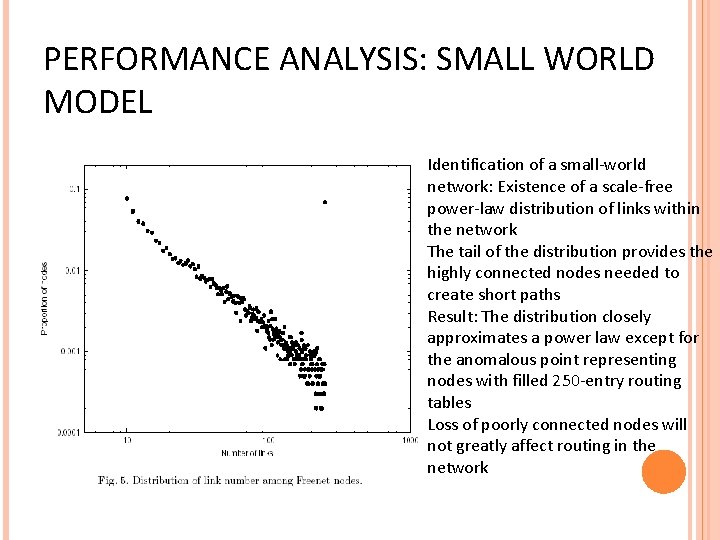
PERFORMANCE ANALYSIS: SMALL WORLD MODEL Identification of a small-world network: Existence of a scale-free power-law distribution of links within the network The tail of the distribution provides the highly connected nodes needed to create short paths Result: The distribution closely approximates a power law except for the anomalous point representing nodes with filled 250 -entry routing tables Loss of poorly connected nodes will not greatly affect routing in the network

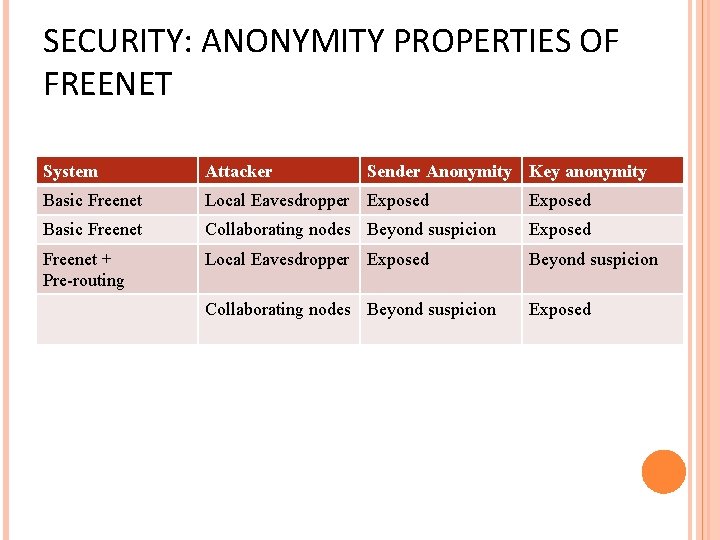
SECURITY: ANONYMITY PROPERTIES OF FREENET System Attacker Sender Anonymity Key anonymity Basic Freenet Local Eavesdropper Exposed Basic Freenet Collaborating nodes Beyond suspicion Exposed Freenet + Pre-routing Local Eavesdropper Exposed Beyond suspicion Collaborating nodes Beyond suspicion Exposed

CONCLUSION Freenet provides an effective means of anonymous information storage and retrieval It keeps information anonymous and available while remaining highly scalable WIP: Implementing of a simulation and visualization suite which will enable more rigorous tests of the protocol and routing algorithm WIP: Implementation of a public-key infrastructure to authenticate nodes and create a searching mechanism

REFERENCES "Freenet: A Distributed Anonymous Information Storage and Retrieval System” http: //www. doc. ic. ac. uk/~twh 1/academic/papers/icsi-revised. pdf