Frauds and Scams Jack Lang Health Warning DO
















- Slides: 19

Frauds and Scams Jack Lang ***Health Warning*** DO NOT TRY THIS AT HOME You will meet strange new people and change your life…. not for the better Its easy to steal. Its much harder to enjoy the proceeds…

Frauds and Scams l Straightforward dishonesty – – – l System weaknesses – – – l Ponzi schemes Lotteries Financial Euphoria Institutional fraud – l Insider trading: Guinness, Leason and others Boiler room schemes Money laundering: layering Unreal Maths – – – l Telco fraud TV decoders Hack attack: blackmail – Do. S attacks Inside trading and market manipulation – – – l False accounting • Insider abuse False customer claims Credit cards etc: Attacks and counter measures Identity theft Long firm Con tricks Enron, false customer numbers, churn Countermeasures – Follow the money

Dishonesty l Most likely attack – Insider with authorised access • False accounting – – Spoof invoices Spoof purchases Spoof bank orders etc Poor control: Leason etc – Countermeasures: • Cleanliness: – Double entry book-keeping; asset register; purchasing system – 2 signatures for critical functions (e. g. cheques) • Good control systems and audit – Locks & keys • Vet staff & have good staff relations – Corporate culture • Unusual behaviour patterns – Unsocial hours, expensive tastes

Credit Cards l Overall cost of fraud – – l Spain 0. 01% UK 0. 2% USA 1. 0% BUT for certain sites, customer not present – 40% Motivation – who gets the reward? – Huge hype “Evil Hackers” • Employment for security types – No case of fraud resulting from interception! • Getting sense from mail is hard – Real problem: hacked or crooked end systems l Many ways to collect or generate valid card numbers – “Shoulder surfing” – video camera – Hacking end systems more for show than practicality

Dishonest customers l False customer claims and repudiation • “I did not order these goods” • “You did not ship me the goods I ordered” – Countermeasures: • Audit – Secure audit trails l Stolen credit cards – Countermeasures: • Check card before shipping – e. g. $1 transaction end to end • Check ship address is card address

Credit Cards l l l Originally fraud risk borne by banks Introduction of mail order and telephone (and web) order (MOTO) risk for transactions with the cardholder not present passed to merchant. MOTO have lower floor limits, and in delivery only to cardholder address – Not possible to check addresses for e-delivery, or overseas or services like Worldpay) – 40% fraud for some sites – Paypal fraud l Traditional frauds: – Stolen cards – Pre-issue – Identity theft

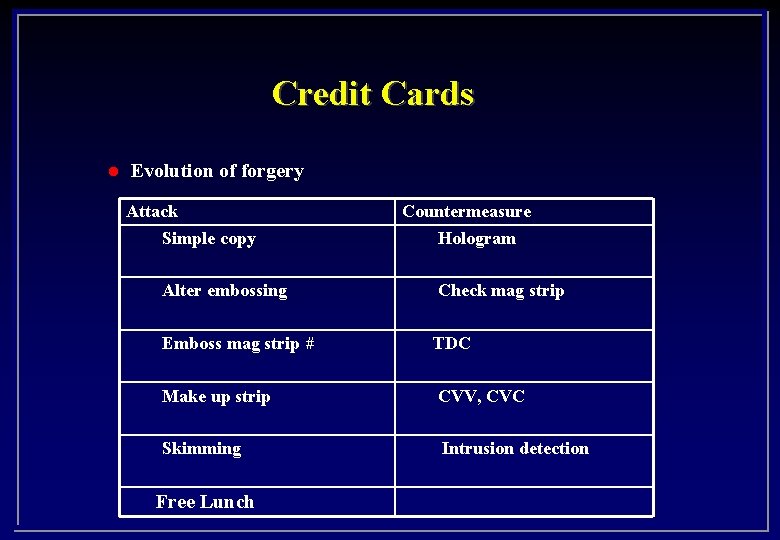
Credit Cards l Evolution of forgery Attack Simple copy Countermeasure Hologram Alter embossing Check mag strip Emboss mag strip # TDC Make up strip CVV, CVC Skimming Intrusion detection Free Lunch

Lotteries and Scams l Lotteries: tax on the ignorant – Poor estimate of low probability events l Premium rate telephone scams – TV quiz shows and auctions – Phone this number to win… l Straight frauds – – Ponzi schemes (Pyramid sells) Credit card and other personal details misuse Telecom scams Boiler room operations

False Identity l Legend: e. g. Giles Murchiston – Birth certificate ->Passport – Passport + Utility Bill-> Bank Account – Bank Account -> Credit Card – -> NHS record, Employment benefit – Email address (e. g Hotmail, Net. Identity) – Telephone entry l Long Firm Fraud

Con tricks l Setup – Select the mark – Establish credibility l Hook and Bait – Small steps – Greed and desire l Sting – Special limited time offer… – Things are not what they seem… l Shut-out – Exit route

FTC Top Ten Dot Cons Con artists have gone high-tech, using new technology to peddle traditional scams. Scam artists can be just a click away. Internet Auctions You might not get what you bought…. International Modem Dialing Hold on while we re-direct you Internet Access Services Didn’t we tell you about the cancellation fee? Credit Card Fraud Web Cramming Let us design your web site/process your orders… Multilevel Marketing Plans and Pyramids Travel and Vacation. Business Investment Opportunities Health Care Products and Services

HK Top Ten l No. 1 - Fake Gold Rings No. 2 - Bogus Modelling Agencies No. 3 - London ("Loco") Gold No. 4 - Fake Herbs etc. No. 5 - "Dropped" Money No. 6 - The "Ketchup" Gang No. 7 - Nigerian Letters No. 8 - Chain Letters And Pyramid Schemes No. 9 - Overclocking No. 10 - Superstition Deception

System weaknesses – Telco fraud • Re-direct – TV decoders • Blocking • Fake cards – Hack attacks: • blackmail – • Do. S attacks

Inside trading and market manipulation l Insider trading: Guinness, and others – Market illiquid for small stocks or large orders • “Upstairs market” – What is a “fair market”? • Anonymity and disclosure: – Pre-trade – Post-trade – Boiler room schemes l Money laundering: – Layering – Getting it into and out of the banking system • Bureau de Change & offshore banks • Disguise as legitimate business

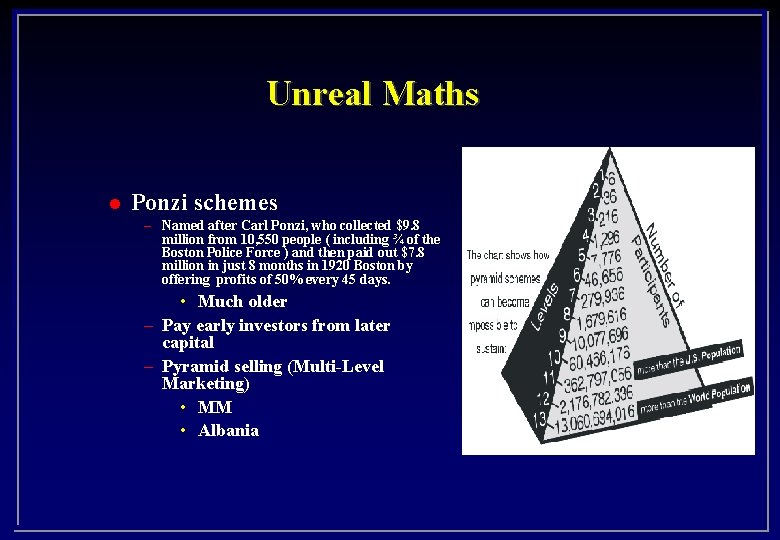
Unreal Maths l Ponzi schemes – Named after Carl Ponzi, who collected $9. 8 million from 10, 550 people ( including ¾ of the Boston Police Force ) and then paid out $7. 8 million in just 8 months in 1920 Boston by offering profits of 50% every 45 days. • Much older – Pay early investors from later capital – Pyramid selling (Multi-Level Marketing) • MM • Albania


More Maths l Lotteries – Tax on the poor and the ignorant • How Casonava made his money • Not all promoters are honest! l Financial Euphoria – – – Tulipmania (1637) South Sea Bubble (1720) Railways (1849) Radio and Aeroplanes (1920) Dot. Com • J. K. Galbraith

Institutional & Governmental fraud l False assurances – – l Enron BP Murdoch 3 G Telco licences Bad statistics – Telco customer numbers, churn – Unemployment, hospital waiting lists – Web-site clicks, adverts

Countermeasures l Caution – If something is too good to be true, it probably is! l Cleanliness – – l Conventional double-entry bookkeeping Audit Culture Realistic risk assesment Follow the money – Hard to disappear