Fraud Examination 4 E Chapter 6 DataDriven Fraud













- Slides: 26

Fraud Examination, 4 E Chapter 6: Data-Driven Fraud Detection Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license distributed with a certain product or service or otherwise on a password-protected website for classroom use.

Learning Objectives q Describe the importance of data-driven fraud detection, including the difference between accounting anomalies and fraud. q Explain the steps in the data analysis process. q Be familiar with common data analysis packages. q Understand the principles of data access, including open database connectivity (ODBC), text import, and data warehousing. Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Learning Objectives q Perform basic data analysis procedures for fraud detection. q Read analyze a Matasos matrix. q Understand how fraud is detected by analyzing financial statements. Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

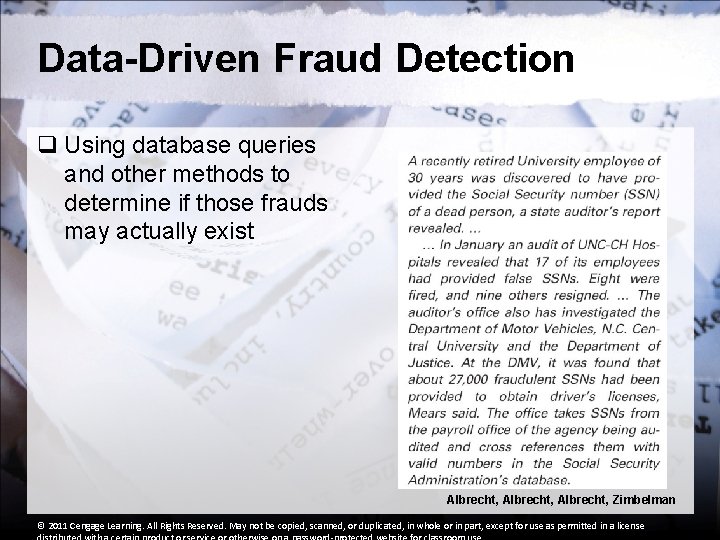
Data-Driven Fraud Detection q Using database queries and other methods to determine if those frauds may actually exist Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Anomalies Versus Fraud q Anomalies… § are not intentional § will be found throughout a data set q Fraud… § is intentional § is found in very few data sets § is like “finding a needle in a haystack” Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

The Data Analysis Process Proactive – Not Reactive q use reengineered methods to be effective q learn new methodologies, software tools, and analysis techniques q brainstorm the schemes and symptoms q a hypothesis-testing approach Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Proactive Method Of Fraud Detection The Six Steps of the Proactive Method: 1. Understand the business 2. Identify possible frauds that could exist 3. Catalog possible fraud symptoms 4. Use technology to gather data about symptoms 5. Analyze results 6. Investigate symptoms Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Understanding the Business Ways to understand a business: q Tour the business, department, or plant q Become familiar with competitor processes q Interview key personnel q Analyze accounting information q Review process documentation q Work with auditors and security personnel q Observe employees performing their duties Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Identify Possible Frauds q Divide the business into individual functions q Interview people in the business functions—ask questions like… § Who are the key players in the business? § What types of employees, vendors, or contractors are involved in business transactions? § How do insiders and outsiders interact with each other? § What types of fraud have occurred or been suspected in the past? Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Identify Possible Frauds § What types of fraud could be committed against the company or on behalf of the company? § How could employees or management acting alone commit fraud? § How could vendors or customers working in collusion with employees commit fraud? Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Catalog Possible Fraud Symptoms Divided into five groups (Chapter 5): § § § Accounting anomalies Internal control weaknesses Analytical anomalies Extravagant lifestyles Unusual behaviors Tips and complaints Example: Kickbacks Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Catalog Possible Fraud Symptoms q Red Flags of Kickbacks q Analytical Symptoms § Increasing prices § Larger order quantities § Increasing purchases from favored vendor § Decreasing purchases from other vendors § Decreasing quality Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Catalog Possible Fraud Symptoms q Red Flags of Kickbacks q Behavioral Symptoms § Buyer doesn’t relate well to other buyers and vendors § Buyer’s work habits change unexpectedly Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Catalog Possible Fraud Symptoms q Red Flags of Kickbacks q Lifestyle Symptoms § Buyer lives beyond known salary § Buyer purchases more expensive automobile § Buyer builds more expensive home Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Catalog Possible Fraud Symptoms q Red Flags of Kickbacks q Control Symptoms § All transactions with one buyer and one vendor § Use of unapproved vendors q Document Symptoms § 1099 s from vendor to buyer’s relative Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Catalog Possible Fraud Symptoms q Red Flags of Kickbacks q Tips and Complaints § Anonymous complaints about buyer or vendor § Unsuccessful vendor complaints § Quality complaints about purchased products Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Steps 4 -6 4. Use technology to gather data about symptoms § § Data analysis applications Structured query language (SQL) 5. Analyze results § § Screen results using computer algorithms Real-time analysis and detection of fraud 6. Investigate symptoms § § Pursue most promising indicators Highlight frauds while they are still small Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Data Analysis Software ACL Audit Analytics § Powerful program for data analysis § Most widely used by auditors worldwide Case. Ware’s IDEA § Recent versions include an increasing number of fraud techniques § ACL’s primary competitor Picalo § Similar to IDEA and ACL but incorporates “Detectlets”— small plug-ins to detect fraud indicators Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Data Analysis Software Microsoft Office + Active. Data § § a plug-in for Microsoft Office provides data analysis procedures based in Excel and Access less expensive alternative to ACL and IDEA SAS and SPSS § Statistical analysis programs with available fraud modules Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Data Access q Gathering the right data in the right format during the right time period. Methods include: q Open Database Connectivity (ODBC) q Text Import q Hosting a Data Warehouse Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Data Access Open Database Connectivity (ODBC) § standard method of querying data from corporate databases § a connector between analysis applications (ACL, IDEA, and Picalo) and the company databases (Oracle, SQL Server, and My. SQL) § best way to retrieve data for analysis because § § it can retrieve data in real time it allows use of the SQL language it allows repeated pulls for iterative analysis it retrieves metadata (like column types and relationships) directly Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Data Access Text Import § Import data with a delimited text (CSV or TSV) § CSV: ID, Date, First Name, Last Name, Phone Number, etc. 342, 12/23/2007, Seth, Knab, 000 -0000, etc. § TSV: ID Date 342 12/23/2007 § First Name Seth Last Name Phone Knab 000 -0000 Import data with XML or other language Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Data Access Hosting a Data Warehouse q Data are imported, stored, and analyzed within ACL or other program q An all-in-one solution for the investigator Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Data Analysis q Analysis techniques that are most commonly used by fraud investigators: § § § § Data Preparation Benford’s Law Digital Analysis Outlier Investigation Stratification and Summarization Time Trend Analysis Fuzzy Matching Real-Time Analysis Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

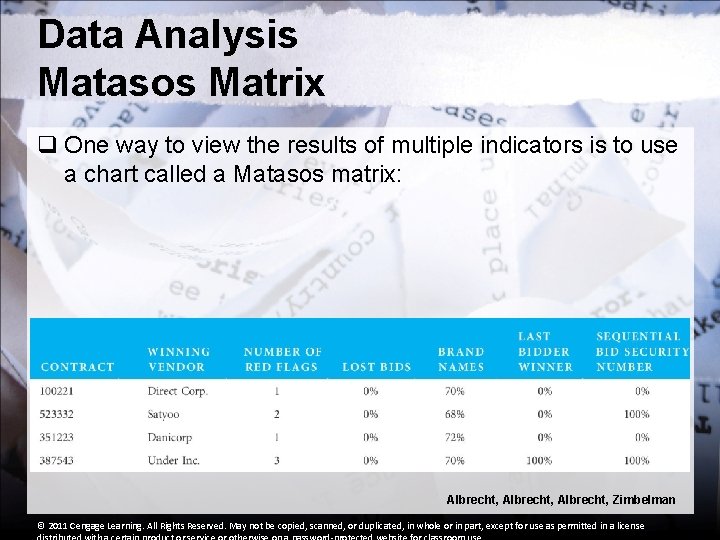
Data Analysis Matasos Matrix q One way to view the results of multiple indicators is to use a chart called a Matasos matrix: Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license

Financial Statement Analysis Approaches to Financial Statement Analysis: 1. comparing account balances from one period to the next 2. calculating key ratios and comparing them from period to period 3. performing vertical analysis 4. performing horizontal analysis Albrecht, Zimbelman © 2011 Cengage Learning. All Rights Reserved. May not be copied, scanned, or duplicated, in whole or in part, except for use as permitted in a license