Fragmentation Attack What is Fragmentation Fragmentation Attacks How


























- Slides: 35

Fragmentation Attack

• What is Fragmentation • Fragmentation Attacks • How to mitigate fragmentation attacks Tools required • Fragrouter • Metasploit Framework • Snort • tcpdump. exe

• Fragmentation is necessary in order for traffic, which is being sent across different types of network media to arrive successfully at its intended destination. • The reason for this is that different types of network media and protocols have different rules involving the maximum size allowed for datagrams on its network segment. • This is known as the maximum transmission unit or MTU. • In order to transmit a datagram across a network segment which has a MTU smaller than that of the packet to be transmitted fragmentation is required.

In order for a fragmented packet to be successfully reassembled at the destination each fragment must obey the following rules: – Must share a common fragment identification number. Also known as fragment Id. – Each fragment must say what its place or offset is in the original unfragmented packet. – Each fragment must tell the length of the data carried in the fragment. – Finally the fragment must know whether more fragments follow this one. • • All of this information will be contained in the IP header. The header will be placed in an IP datagram followed by an encapsulated fragment

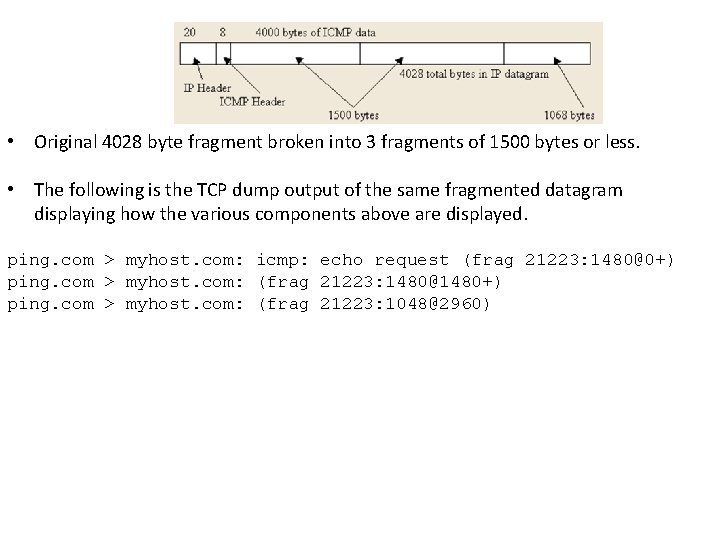
• Original 4028 byte fragment broken into 3 fragments of 1500 bytes or less. • The following is the TCP dump output of the same fragmented datagram displaying how the various components above are displayed. ping. com > myhost. com: icmp: echo request (frag 21223: 1480@0+) ping. com > myhost. com: (frag 21223: 1480@1480+) ping. com > myhost. com: (frag 21223: 1048@2960)

• Fragment Offset specifies the fragment's position within the original Datagram, measured in 8 -byte units. • Accordingly, every fragment except the last must contain a multiple of 8 bytes of data. It is obvious that Fragment Offset can hold 8192 (2^13) units but the datagram can't have 8192 * 8 = 65536 bytes of data because "Total Length" field of IP header records the total size including the header and data. • An IP header is at least 20 bytes long, so the maximum value for "Fragment Offset" is restricted to 8189, which leaves room for 3 bytes in the last fragment. • Because an IP internet can be connectionless, fragments from one datagram may be interleaved with those from another at the destination. The "Identification field" uniquely identifies the fragments of a particular datagram.

• Three fields in the IP header are used to implement fragmentation and reassembly. • The "Identification", "Flags" and "Fragment Offset" fields. Flags: • A 3 bit field which says if the datagram is a part of a fragmented data frame or not. • Bit 0: reserved, must be zero (unless datagram is adhering to RFC 3514) • Bit 1: (DF) 0 = May Fragment, 1 = Don't Fragment. • Bit 2: (MF) 0 = Last Fragment, 1 = More Fragments.

IP Fragmentation Example • Given 2366 byte packet coming into our Ethernet network. • The Ethernet networks MTU is 1500 bytes so our packet will need to be divided into 2 fragments. • Fragment 1: The first packet will be 1500 bytes in length. The first packet's DF fragbit will be set to 0 that means "may fragment" and the MF fragbit will be set to 1 which means More fragments to come. Since this is the first fragment, the fragment offset will be 0 • Fragment 2: The second packet's DF flag will still be set to 0 to mean "May fragment" but the MF flag will be set to 0 that means this will be the last fragment. The fragment offset of this packet will be somewhere around 910 or so. This is calculated based upon the data portion of previous packets and doesn't include the 20 or 40 bytes for the packet header lengths.

• IP fragmentation is the process of breaking up a single Internet Protocol (IP) datagram into multiple packets of smaller size. Every network link has a characteristic size of messages that may be transmitted, called the maximum transmission unit (MTU). • There are numerous ways in which attackers have used fragmentation to infiltrate and cause a denial of service to networks. • At the simplest level, fragmentation attacks are possible when several fragments, which are by themselves not a security risk and can therefore be allowed to pass through a filter or firewall, but when the fragments reach their destination the fragments are combined and produce something dangerous.

• Fragmentation attacks are usually seen in relation to the network/session layer where firewalls and IDSs try to filter packets on how dangerous they are deemed to be, • they are also used to sometimes fool those same devices which try to rearrange the packets themselves and read the streams

• To simulate this open up a terminal and type ping ip_dest -n 1 -l 65000 Download fragmentation attack related pcap files and submit the analysis

TCP Header Fragment nmap is a scanning tool and is available from www. insecure. org/nmap. It does conventional port scanning to discover what ports are open on a target host and does stealth scanning that looks for open ports, but also makes an • attempt to elude detection by intrusion-detection systems. • An nmap command-line option (-f) fragments the 20 -byte TCP headers in multiple fragments in an attempt to avoid detection. • The following TCPdump output is generated using the command: nmap -f -s. S -p 53 target. com • This sends a fragmented SYN connection to port 53 of target. com: truncated-tcp 16 (frag 25096: 16@0+) fragger. org > target. com: (frag 25096: 4@16) truncated-tcp 16 (frag 4265: 16@0+) fragger. org > target. com: (frag 4265: 4@16) truncated-tcp 16 (frag 34927: 16@0+) fragger. org > target. com: (frag 34927: 4@16) • •

• First line: a fragment with 16 bytes of truncated TCP data. The minimum TCP header is 20 bytes with no options. Because this is not a complete TCP header, TCPdump reports this as truncatedtcp. • In the next record, the additional 4 bytes of TCP header are sent. • It is possible that an intrusion-detection system might not capture or report this kind of stealth scan.

Hosts, routers, and intrusion-detection systems have to deal with many aspects of fragmentation: • make sure that all the fragments in a fragment train are received. • make sure that they are properly formatted—none may overlap—and in aggregate, they may not exceed the maximum datagram size of 65, 535. • check that no shenanigans are attempted by fragmenting protocol headers. • This is a tall order because it requires fragment reassembly and detection of mutations. • To do this correctly, this requires a commitment of memory and allocation of CPU power, and if not implemented correctly, it can cause denial of service or other problems.

Fragmentation Attacks • Ping O’ Death Fragmentation Attack • Tiny Fragment Attack • Teardrop Attack • Overlapping Fragment Attack • Unnamed Attack • Rose Fragmentation Attack

Ping O’ Death fragmentation attack • The Ping O’ Death fragmentation attack is a denial of service attack, which utilises a ping system utility to create an IP packet, which exceeds the maximum allowable size for an IP datagram of 65535 bytes. • This attack uses many small fragmented ICMP packets which when reassembled at the destination exceed the maximum allowable size for an IP datagram. This can cause the victim host to crash, hang or even reboot. • This attack has however been around for quite sometime and all operating system vendors should have fixes in place to rectify this problem. It is however essential to ensure that you have the latest patches installed for your operating system.

The Tiny Fragment Attack • This attack uses small fragments to force some of the TCP header information into the next fragment. This may produce a case whereby the TCP flags field is forced into the second fragment and filters that attempt to drop connection requests will be unable to test these flags in the first octet thereby ignoring them in subsequent fragments. • This attack can be used to circumvent user-defined filtering rules. The attacker hopes that a filtering router will examine only the first fragment and allow all other fragments to pass. • This attack can be prevented at the router by enforcing rules, which govern the minimum size of the first fragment. This first fragment should be made large enough to ensure it contains all the necessary header information.

The Teardrop Attack • This is also a denial of service attack that can cause the victim host to hang crash or reboot, as was the Ping O’ Death attack. • The teardrop attack utilises the weakness of the IP protocol reassembly process. The teardrop attack is a UDP attack, which uses overlapping offset fields in an attempt to bring down the victim host. • This type of attack has also been around for some time and most operating system vendors have patches available to guard against this sort of malicious activity.

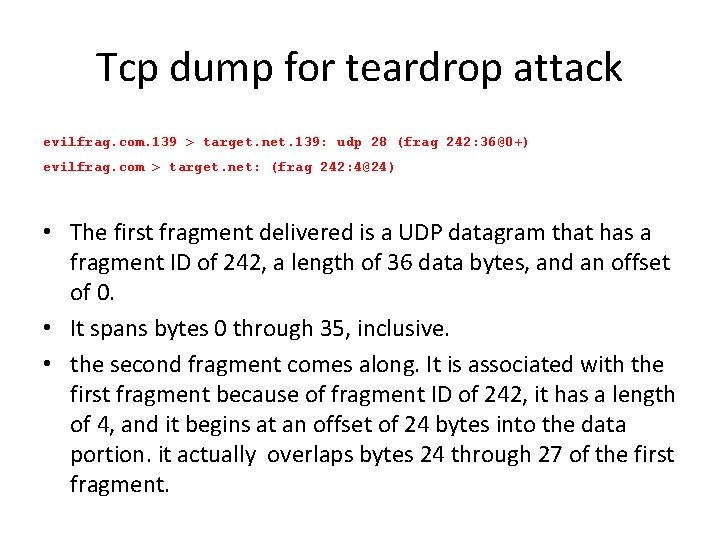
Tcp dump for teardrop attack evilfrag. com. 139 > target. net. 139: udp 28 (frag 242: 36@0+) evilfrag. com > target. net: (frag 242: 4@24) • The first fragment delivered is a UDP datagram that has a fragment ID of 242, a length of 36 data bytes, and an offset of 0. • It spans bytes 0 through 35, inclusive. • the second fragment comes along. It is associated with the first fragment because of fragment ID of 242, it has a length of 4, and it begins at an offset of 24 bytes into the data portion. it actually overlaps bytes 24 through 27 of the first fragment.

• The Teardrop attack exploits weaknesses in the reassembly process of fragments. • The Teardrop program creates fragments with overlapping offset fields. • When these fragments are reassembled at the destination host, some systems will crash, hang, or reboot.

The Overlapping Fragment Attack • Another variation on the teardrop attack that also uses overlapping fragments is the Overlapping Fragment Attack. This attack however is not a denial of service attack but it is used in an attempt to bypass firewalls to gain access to the victim host. • This attack can be used to overwrite part of the TCP header information of the first fragment, which contained data that was allowed to pass through the firewall, with malicious data in subsequent fragments. A common example of this is to overwrite the destination port number to change the type of service i. e. change from port 80 (HTTP) to port 23 (Telnet) which would not be allowed to pass the router in normal circumstances. • Ensuring a minimum fragment offset is specified in the router’s IP filtering code can prevent this attack.

The Unnamed Attack • This attack is yet another variation on the teardrop attack that attempts to cause a denial of service to the victim host. This time however the fragments are not overlapping but are created in such a way that there is a gap created in the fragments. • This is done by manipulating the offset values to ensure there are parts of the fragment, which have been skipped. Some operating systems may behave unreliably when this exploit is used upon them

Rose Fragmentation Attack • a combination of the SYN attack and the "Unknown" ICMP attack • the source address and source port could be spoofed. • No TCP handshake was required. • this attack would work equally well with ICMP, UDP or TCP. • Firewalls do not matter because the packet is never evaluated / seen by the firewall.

• Send the first few bytes of a fragmented packet at offset 0 (More Fragments Bit = 1) and then send a few bytes at the end of a 64 k sized packet (More Fragments Bit = 0). The placement of the last fragment does not have to be at 64 k, this is just an attempt to use more memory. • Note that if you send with a random source address then the only way to track down the attack is to trace it hop by hop (router by router) back to the source. • Source port does not matter because the packet has not "moved up the stack" yet, so the stack does not validate that the destination port is even valid. In some cases all legitimate fragmented packets are denied or impacted (UDP, TCP and ICMP) if you attack a machine in this manner. • When you send enough of these tiny fragments the buffer in the receiving machine fills waiting for the rest of the fragments to arrive. Legitimate fragmented packets cannot enter the queue because it is already filled, waiting for the fragments that will never arrive. • Some implementations of the IP stack drop "old" fragmented packets that have not completed thus thwarting (to a greater or lesser degree) this attack.

Prevention of IP fragmentation • Filtering IP Fragments • keep track of the results of applying filter rules to the first fragment (FO==0) and applying them to subsequent fragments of the same packet. • The filtering module would maintain a list of packets indexed by the source address, destination address, protocol, and IP ID. • When the initial (FO==0) fragment is seen, if the MF bit is set, a list item would be allocated to hold the result of filter access checks. • When packets with a non-zero FO come in, look up the list element with a matching SA/DA/PROT/ID and apply the stored result (pass or block). When a fragment with a zero MF bit is seen, free the list element

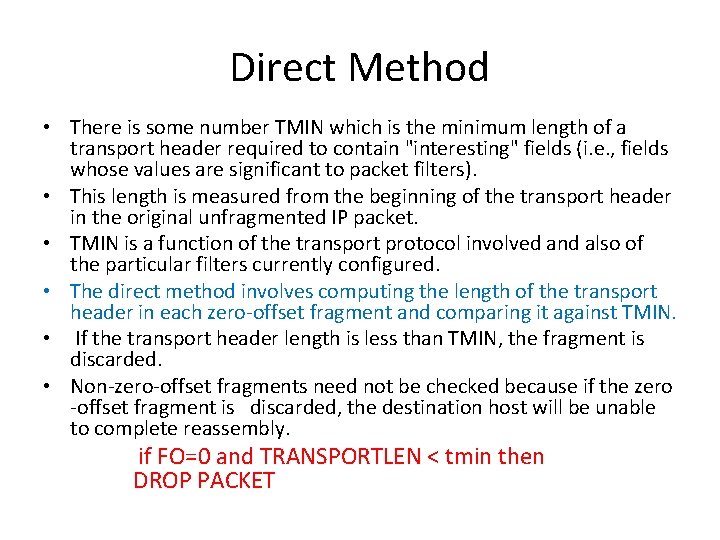
Prevention of the Tiny Fragment Attack In a router, one can prevent this sort of attack by enforcing certain limits on fragments passing through, namely, that the first fragment be large enough to contain all the necessary header information • There are two ways to guarantee that the first fragment of a "passed" packet includes all the required fields, one direct, the other indirect.

Direct Method • There is some number TMIN which is the minimum length of a transport header required to contain "interesting" fields (i. e. , fields whose values are significant to packet filters). • This length is measured from the beginning of the transport header in the original unfragmented IP packet. • TMIN is a function of the transport protocol involved and also of the particular filters currently configured. • The direct method involves computing the length of the transport header in each zero-offset fragment and comparing it against TMIN. • If the transport header length is less than TMIN, the fragment is discarded. • Non-zero-offset fragments need not be checked because if the zero -offset fragment is discarded, the destination host will be unable to complete reassembly. if FO=0 and TRANSPORTLEN < tmin then DROP PACKET

• However, the "interesting" fields of the common transport protocols, except TCP, lie in the first eight octets of the transport header, so it isn't possible to push them into a non-zero-offset fragment. • Therefore, only TCP packets are vulnerable to tiny-fragment attacks and the test need not be applied to IP packets carrying other transport protocols. • A better version of the tiny fragment test might therefore be: if FO=0 and PROTOCOL=TCP and TRANSPORTLEN < tmin then DROP PACKET • this test does not block all fragmentation attacks, and is in fact unnecessary when a more general technique is used.

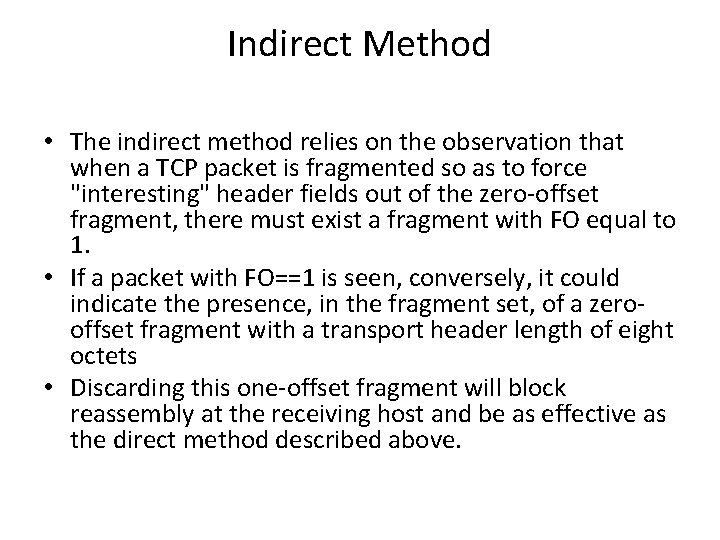
Indirect Method • The indirect method relies on the observation that when a TCP packet is fragmented so as to force "interesting" header fields out of the zero-offset fragment, there must exist a fragment with FO equal to 1. • If a packet with FO==1 is seen, conversely, it could indicate the presence, in the fragment set, of a zerooffset fragment with a transport header length of eight octets • Discarding this one-offset fragment will block reassembly at the receiving host and be as effective as the direct method described above.

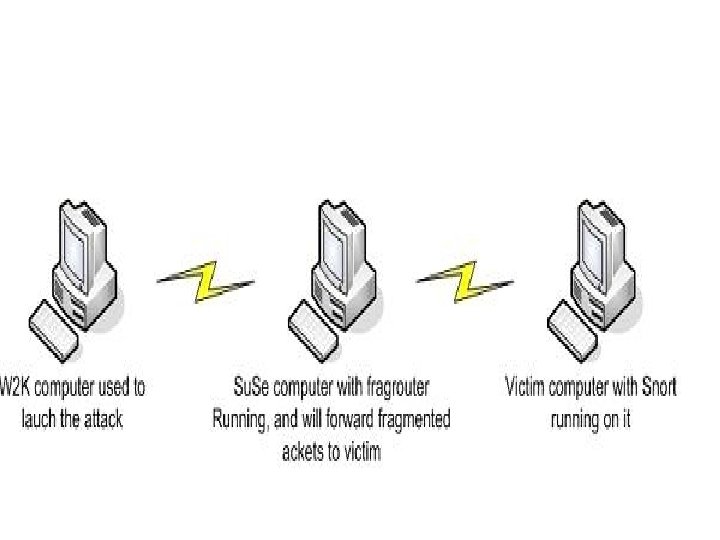
Fragmentation Tools • • According to insecure. org, fragrouter is one of the top 100 security tools of all time. It is used mainly as a "Network Intrusion detection evasion toolkit". Packets are sent to fragrouter which transforms them into fragments and forwarded to the victim. Fragrouter does produce output information to the console. It will list the fragments as well as the offset as it is doing the fragmentation. Lab Setup: Testing Snort's ability to reassemble packets and detect exploits • • • launch a Metasploit MS 03 -026 attack that is routed through a middle computer running fragrouter. Fragrouter will break up the attack in multiple fragments and send them on to a victim computer. The victim computer is running Snort IDS and see how well Snort detects the attack through fragmented packets. So, Snort has to reassemble the packets, detect the attack, and list any fragmented packets it finds.



Metasploit MS 03 -026 attack • • The Metasploit MS 03 -026 attack targets a buffer overflow vulnerability in Microsoft XP. Use the win 32 -reverse payload to actually try to get a remote shell access on the victim computer. Once shell access is gained on the victim computer, stop the attack and views Snort's statistics. Since the route was setup to forward all packets from the attack computer to the victim computer through the middle computer running fragrouter, the victim computer should see fragmented packets. What did Snort detect? No. of Logged items No. of Alerts No. of fragmented packets during the attack session Launch the same attack without using fragrouter What did Snort detect? • No. of Logged items • No. of Alerts • No. of fragmented packets during the attack session Snort - http: //www. snort. org/ Metasploit - http: //www. metasploit. com/

• IPV 4 Fragmentation Attack • WEP Fragmentation Attack • IPV 6 Fragmentation Attack

References • Network Intrusion Detection by Stephen Northcutt and Judy Novak. • Dario Forte, “Fragmentation Attacks: Protection Tools and Techniques: Called “true preliminaries to denial-of-service”, Network Security, Volume 2001, Issue 12, 1 December 2001, Pages 12– 13 Elsevier • http: //www. ouah. org/fragma. html • http: //en. wikipedia. org/wiki/IP_fragmentation_attacks