FORWARD FURTHER FASTER TOGETHER INTO A FUTURE OF









- Slides: 23

FORWARD, FURTHER, FASTER TOGETHER INTO A FUTURE OF HEIGHTENED ACHIEVEMENT

Time to Detection SECURITY CHALLENGES Technology Complexities Personnel Challenges Rise Cost of SOC

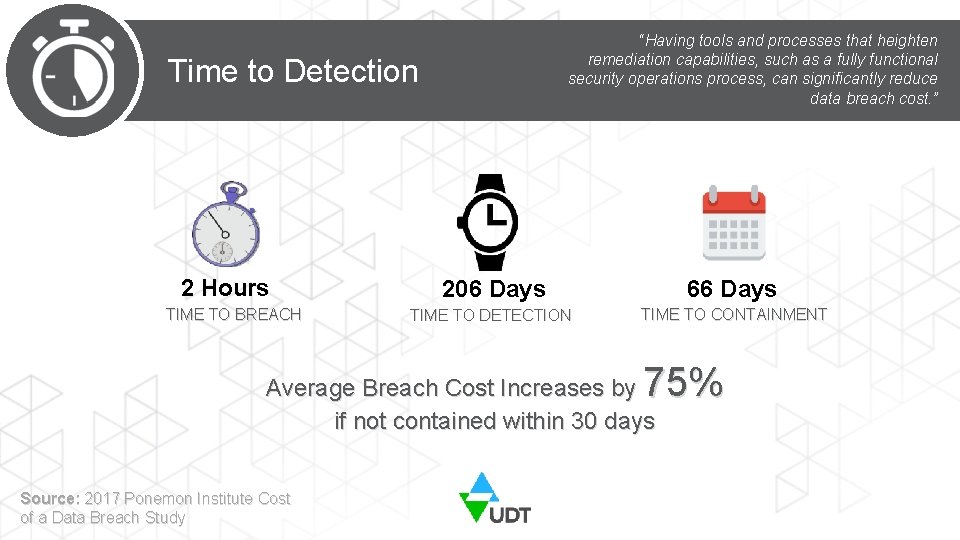
“Having tools and processes that heighten remediation capabilities, such as a fully functional security operations process, can significantly reduce data breach cost. ” Time to Detection 2 Hours TIME TO BREACH 206 Days 66 Days TIME TO DETECTION TIME TO CONTAINMENT 75% Average Breach Cost Increases by if not contained within 30 days Source: 2017 Ponemon Institute Cost of a Data Breach Study

Technology Complexities “The Fog of War” ORGANIZATIONS FACE A WIDE ARRAY OF SOLUTIONS ACROSS MULTIPLE VENDORS + 85 + 45 SECURITY TOOLS VENDORS FROM

Personnel Changes • Demand for qualified cybersecurity professionals continues to outpace supply • Security skills gap leaves 1 in 4 organizations exposed for 6 months or longer • High turnover of qualified security personnel • Higher pay down the road • Small staff vs. varying skillsets • Avg. security staff size • Audit-minded vs. technology-minded staff

Rising Cost of SOC Hardware & Infrastructure Training and Process Development Experienced Resources SIEM Licensing & Maintenance Fees Expense of building and operating a SOC At least 12 people, SIEM Costs, Operating costs, etc. Hardware & Infrastructure ~($300, 000) Resource Costs (12 resources) ~($780, 000) Training and Process Development ~($70, 000) Threat Intelligence Feeds ~($30, 000) SIEM Licensing and Maint. ~($280, 000) Other Capital Costs ~($320, 000) Initial Start Up Costs Threat Intelligence Feeds Other Capital Costs ~($1, 780, 000)

WHY UDT SECURE?

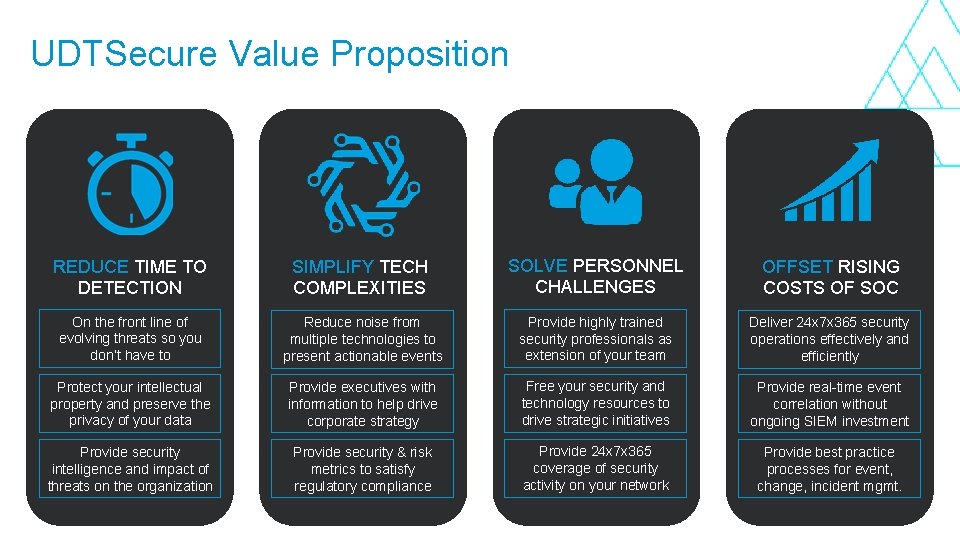
UDTSecure Value Proposition REDUCE TIME TO DETECTION SIMPLIFY TECH COMPLEXITIES SOLVE PERSONNEL CHALLENGES OFFSET RISING COSTS OF SOC On the front line of evolving threats so you don’t have to Reduce noise from multiple technologies to present actionable events Provide highly trained security professionals as extension of your team Deliver 24 x 7 x 365 security operations effectively and efficiently Protect your intellectual property and preserve the privacy of your data Provide executives with information to help drive corporate strategy Free your security and technology resources to drive strategic initiatives Provide real-time event correlation without ongoing SIEM investment Provide security intelligence and impact of threats on the organization Provide security & risk metrics to satisfy regulatory compliance Provide 24 x 7 x 365 coverage of security activity on your network Provide best practice processes for event, change, incident mgmt.

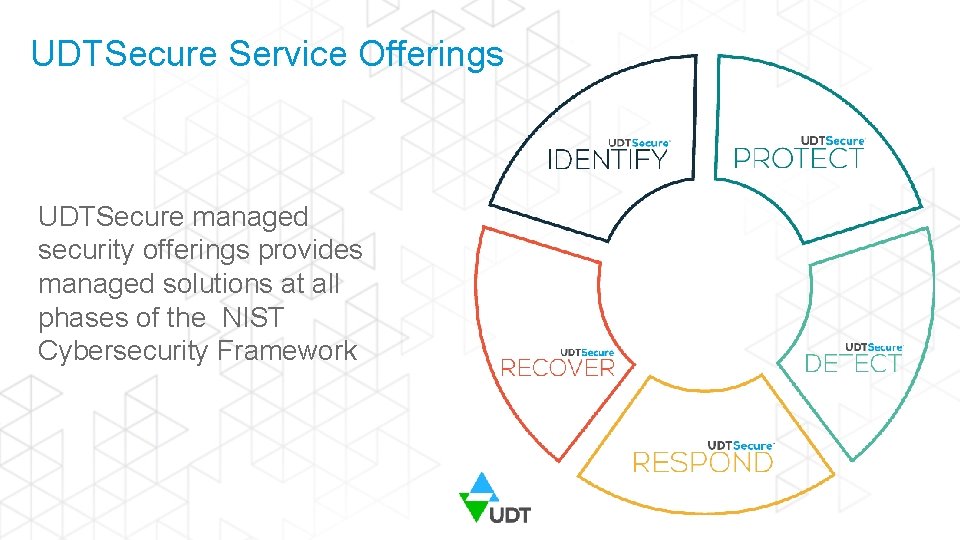
UDTSecure Service Offerings UDTSecure managed security offerings provides managed solutions at all phases of the NIST Cybersecurity Framework

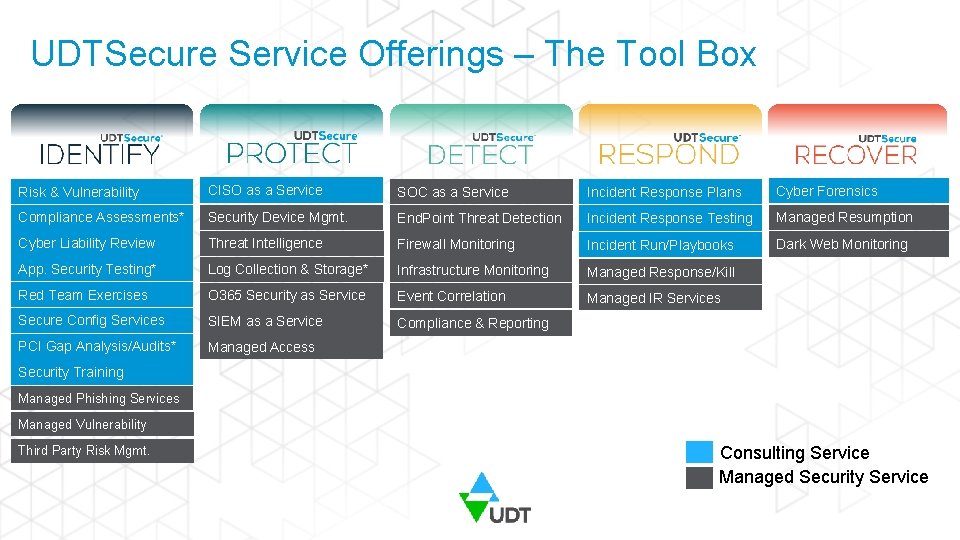
UDTSecure Service Offerings – The Tool Box Risk & Vulnerability CISO as a Service SOC as a Service Incident Response Plans Cyber Forensics Compliance Assessments* Security Device Mgmt. End. Point Threat Detection Incident Response Testing Managed Resumption Cyber Liability Review Threat Intelligence Firewall Monitoring Incident Run/Playbooks Dark Web Monitoring App. Security Testing* Log Collection & Storage* Infrastructure Monitoring Managed Response/Kill Red Team Exercises O 365 Security as Service Event Correlation Managed IR Services Secure Config Services SIEM as a Service Compliance & Reporting PCI Gap Analysis/Audits* Managed Access Security Training Managed Phishing Services Managed Vulnerability Third Party Risk Mgmt. Consulting Service Managed Security Service

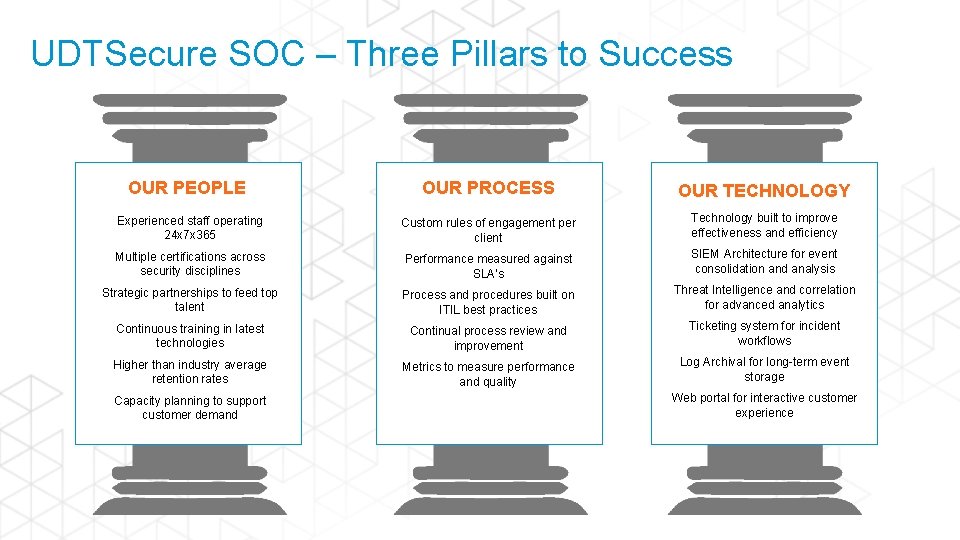
UDTSecure SOC – Three Pillars to Success OUR PEOPLE OUR PROCESS OUR TECHNOLOGY Experienced staff operating 24 x 7 x 365 Custom rules of engagement per client Technology built to improve effectiveness and efficiency Multiple certifications across security disciplines Performance measured against SLA’s SIEM Architecture for event consolidation and analysis Strategic partnerships to feed top talent Process and procedures built on ITIL best practices Threat Intelligence and correlation for advanced analytics Continuous training in latest technologies Continual process review and improvement Ticketing system for incident workflows Higher than industry average retention rates Metrics to measure performance and quality Log Archival for long-term event storage Capacity planning to support customer demand Web portal for interactive customer experience

OUR PEOPLE

UDTSecure Team Our security professionals average 10+ years of security experience and are proven subject matter experts holding multiple industry certifications.

UDTSecure SOC The UDT Security Operations Center (SOC) – 24 x 7 x 365 facility in Miramar, FL – SOC 2 Type II Facility – Staffed with our highly skilled security analyst – Defined processes to manage threats and reduce security risk UDTSecure SOC’s major responsibilities are: – Monitor, analyze, correlate & escalate intrusion events – Develop appropriate responses; protect, detect, respond – Conduct Incident Management and Forensic Investigation – Apply threat intelligence to identify new threat vectors – Assist in crisis operations UDTSecure SOC’s Mission: – Protect customer’s mission-critical data and assets – Prepare for and respond to client cyber emergencies – Help provide continuity and efficient recovery of client infrastructure – Fortify our client’s infrastructure through continuous security 14

OUR PROCESS

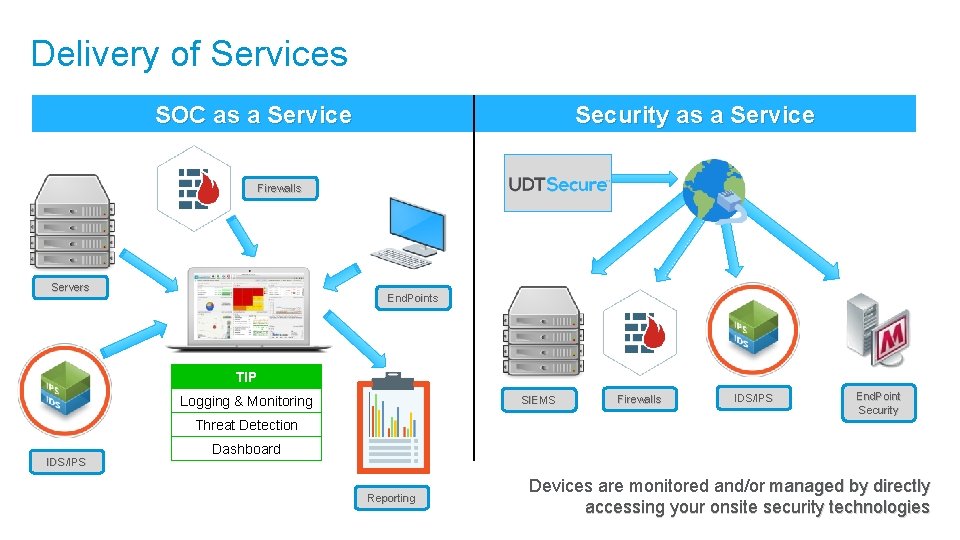
Delivery of Services SOC as a Service Security as a Service Firewalls Servers End. Points TIP Logging & Monitoring SIEMS Firewalls IDS/IPS End. Point Security Threat Detection IDS/IPS Dashboard Reporting Devices are monitored and/or managed by directly accessing your onsite security technologies

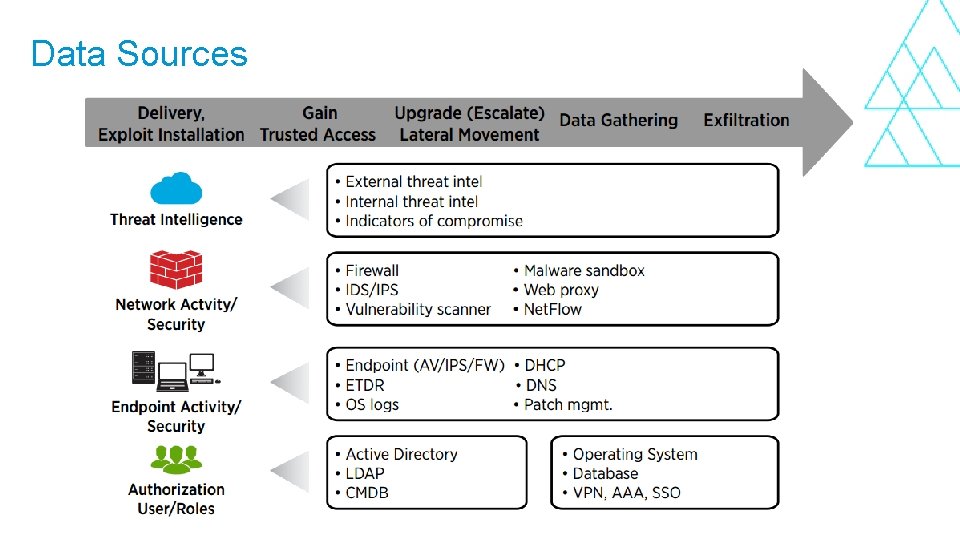
Data Sources

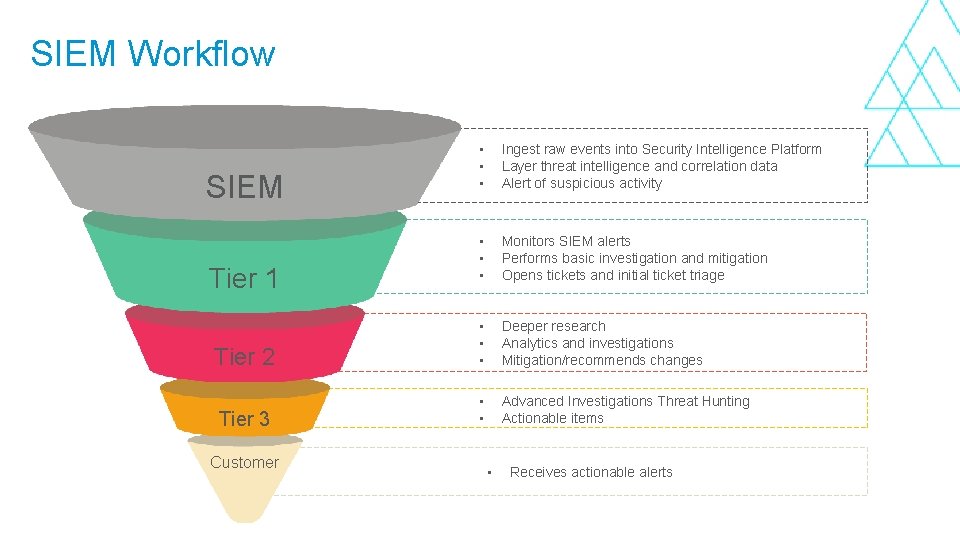
SIEM Workflow • • • Ingest raw events into Security Intelligence Platform Layer threat intelligence and correlation data i Alert of suspicious activity • • • Monitors SIEM alerts Performs basic i investigation and mitigation Opens tickets and initial ticket triage Tier 2 • • • Deeper research Analytics and i investigations Mitigation/recommends changes Tier 3 • • Advanced Investigations Threat Hunting i Actionable items SIEM Tier 1 Customer • Receives i actionable alerts

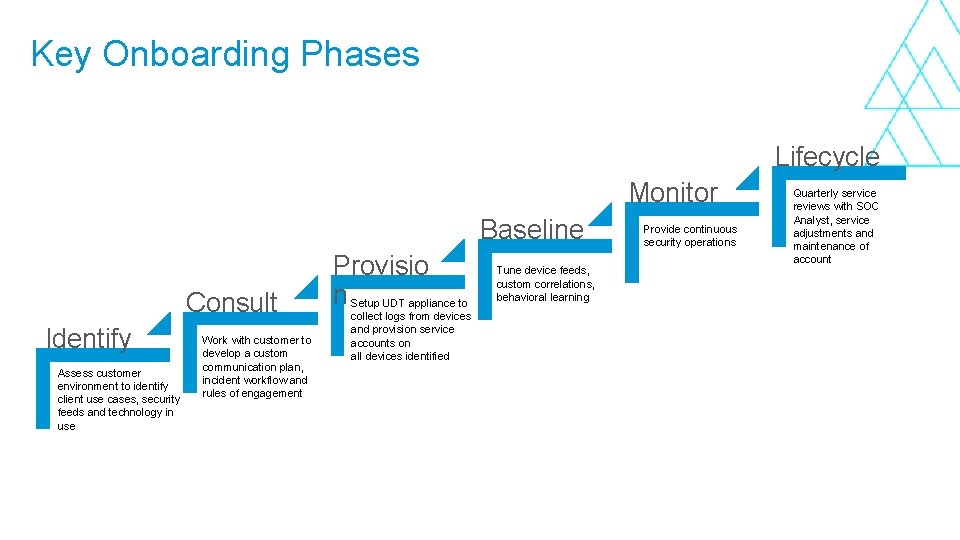
Key Onboarding Phases Lifecycle Monitor Baseline Consult Identify Assess customer environment to identify client use cases, security feeds and technology in use Work with customer to develop a custom communication plan, incident workflow and rules of engagement Provisio n Setup UDT appliance to collect logs from devices and provision service accounts on all devices identified Tune device feeds, custom correlations, behavioral learning Provide continuous security operations Quarterly service reviews with SOC Analyst, service adjustments and maintenance of account

OUR TECHNOLOGY

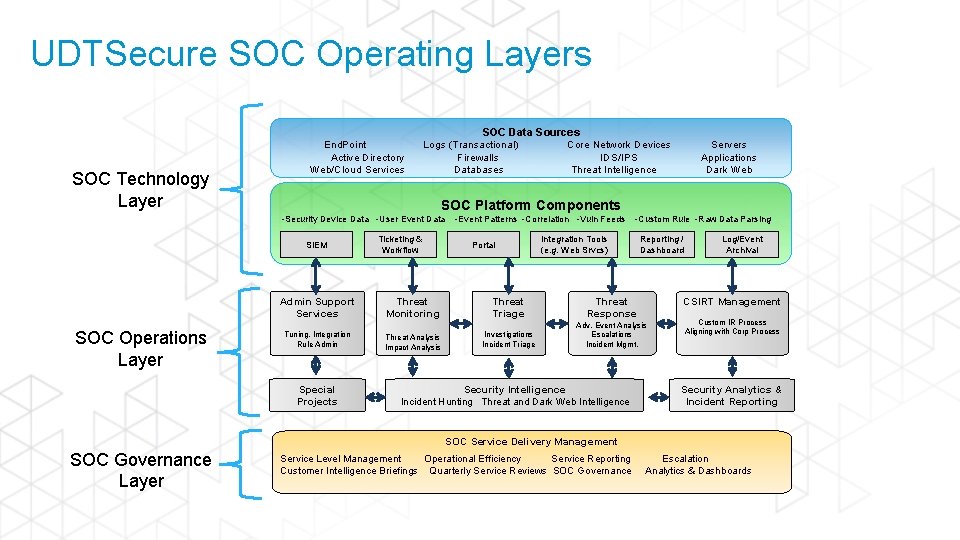
UDTSecure SOC Operating Layers SOC Technology Layer End. Point Active Directory Web/Cloud Services SOC Data Sources Logs (Transactional) Core Network Devices Firewalls IDS/IPS Databases Threat Intelligence SOC Platform Components -Security Device Data -User Event Data SIEM Admin Support Services SOC Operations Layer Servers Applications Dark Web Tuning, Integration Rule Admin Special Projects Ticketing & Workflow -Event Patterns -Correlation -Vuln Feeds Portal -Custom Rule -Raw Data Parsing Integration Tools (e. g. Web Srvcs) Reporting / Dashboard Threat Monitoring Threat Triage Threat Response Threat Analysis Impact Analysis Investigations Incident Triage Adv. Event Analysis Escalations Incident Mgmt. Security Intelligence Incident Hunting Threat and Dark Web Intelligence Log/Event Archival CSIRT Management Custom IR Process Aligning with Corp Process Security Analytics & Incident Reporting SOC Service Delivery Management SOC Governance Layer Service Level Management Operational Efficiency Service Reporting Customer Intelligence Briefings Quarterly Service Reviews SOC Governance Escalation Analytics & Dashboards

UDTSecure Portal UDTSecure SIEM

THANK YOU ACCOMPLISH MORE