Fortify Performance Guide HP ESP User Group Spring








![SCAState [options] <SCA process ID> Options --all --heap-dump --thread-dump --full-thread-dump --program-info -properties -scaversion -timers SCAState [options] <SCA process ID> Options --all --heap-dump --thread-dump --full-thread-dump --program-info -properties -scaversion -timers](https://slidetodoc.com/presentation_image/4544c744f1b70dd6844f5ad3d387c364/image-30.jpg)


- Slides: 33

Fortify Performance Guide HP ESP User Group – Spring 2015 Simon Corlett HP Fortify Technical Account Manager simon. corlett@hp. com © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Web. Inspect Performance

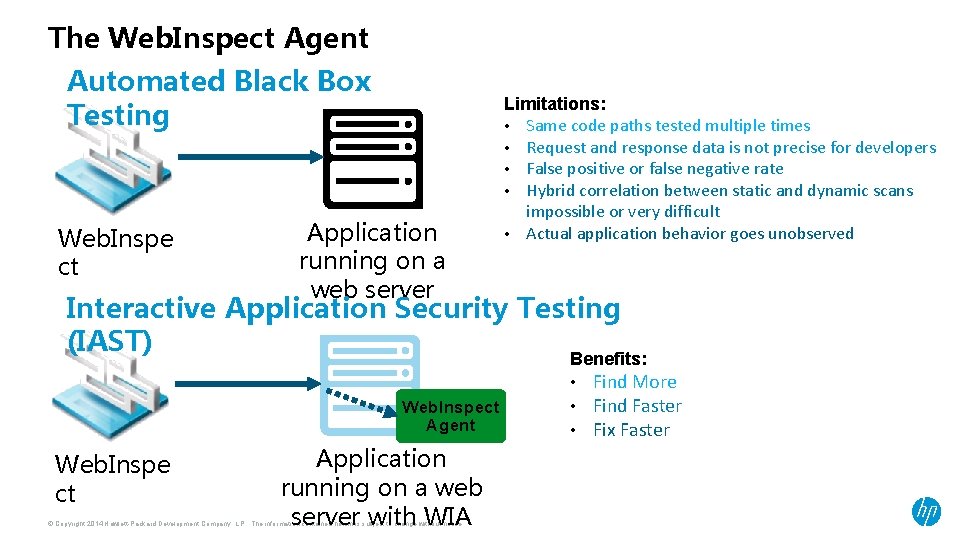
The Web. Inspect Agent Automated Black Box Testing Web. Inspe ct Application running on a web server Limitations: • Same code paths tested multiple times • Request and response data is not precise for developers • False positive or false negative rate • Hybrid correlation between static and dynamic scans impossible or very difficult • Actual application behavior goes unobserved Interactive Application Security Testing (IAST) Benefits: Web. Inspect Agent Web. Inspe ct Application running on a web server with WIA © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. • • • Find More Find Faster Fix Faster

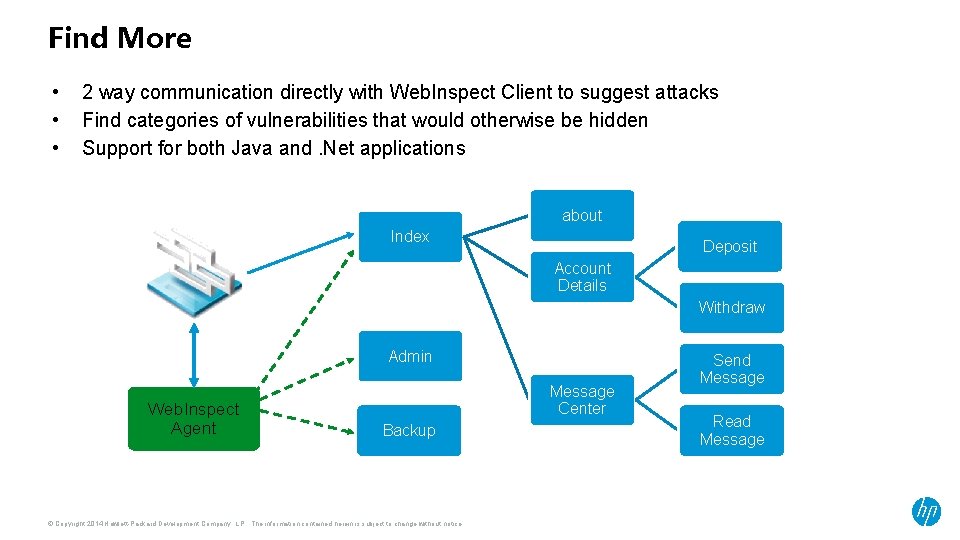
Find More • • • 2 way communication directly with Web. Inspect Client to suggest attacks Find categories of vulnerabilities that would otherwise be hidden Support for both Java and. Net applications about Index Deposit Account Details Withdraw Admin Web. Inspect Agent Message Center Backup © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Send Message Read Message

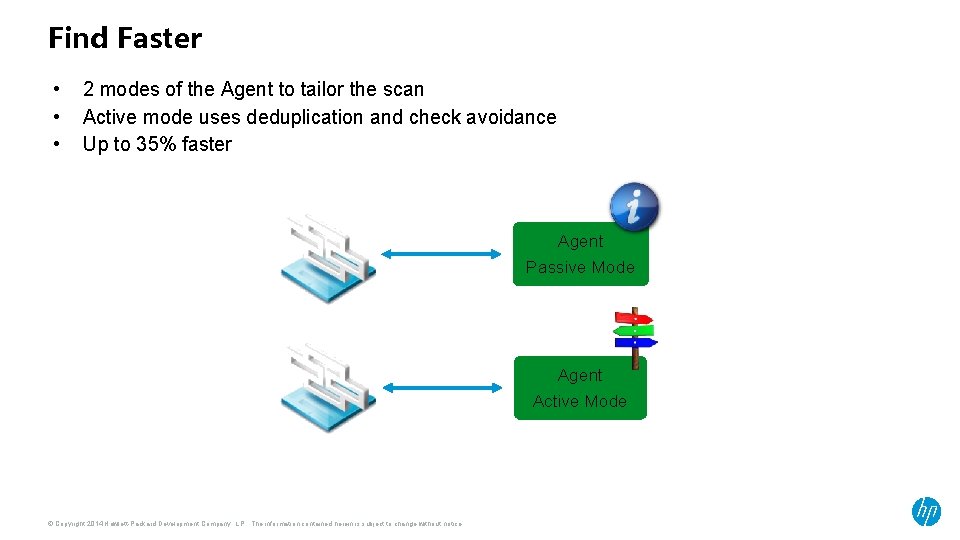
Find Faster • • • 2 modes of the Agent to tailor the scan Active mode uses deduplication and check avoidance Up to 35% faster Agent Passive Mode Agent Active Mode © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

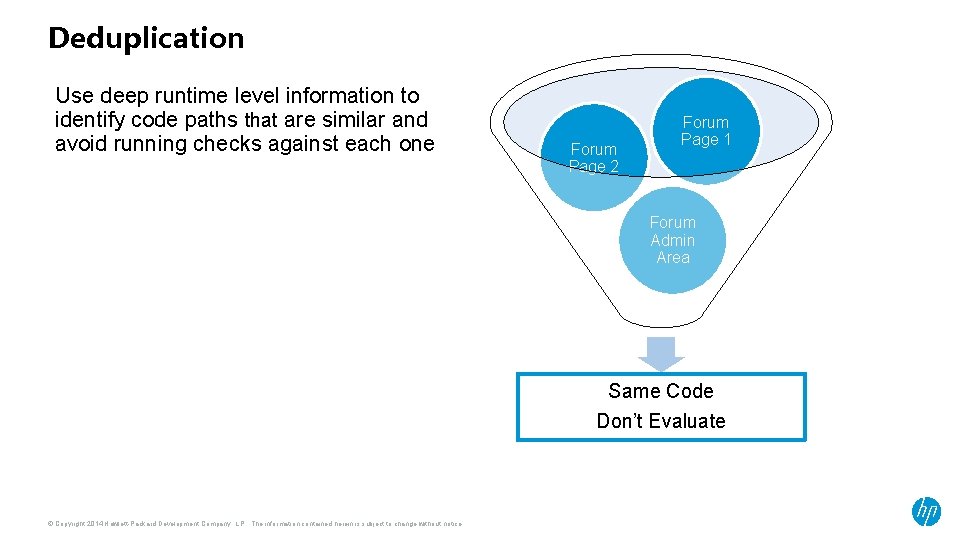
Deduplication Use deep runtime level information to identify code paths that are similar and avoid running checks against each one Forum Page 2 Forum Page 1 Forum Admin Area Same Code Don’t Evaluate © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

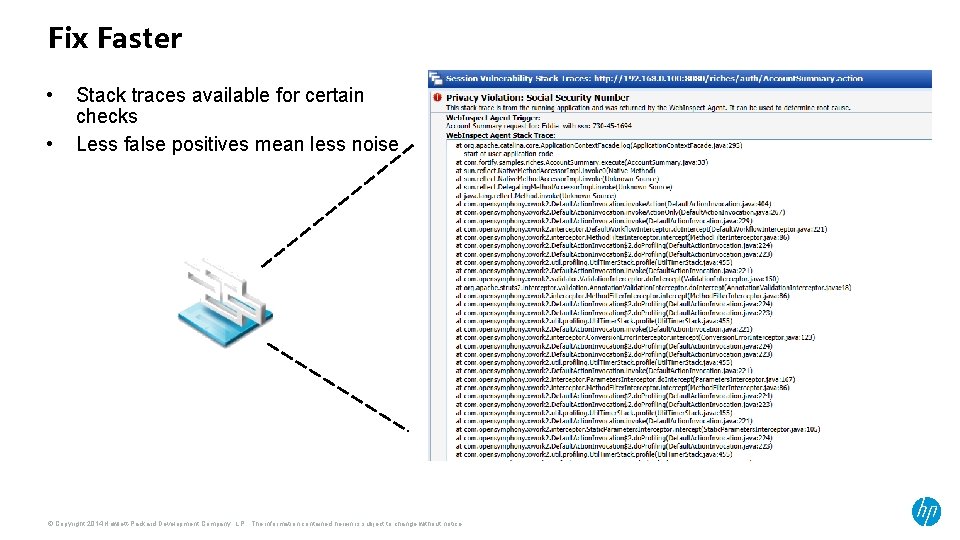
Fix Faster • • Stack traces available for certain checks Less false positives mean less noise © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Any questions? © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

SCA Performance

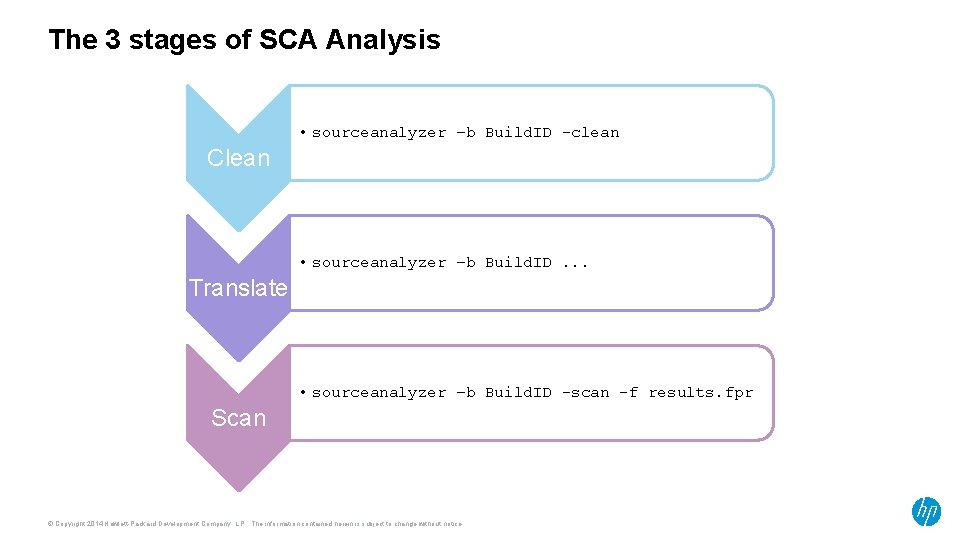
The 3 stages of SCA Analysis • sourceanalyzer –b Build. ID -clean Clean • sourceanalyzer –b Build. ID. . . Translate • sourceanalyzer –b Build. ID -scan -f results. fpr Scan © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Factors affecting SCA Performance • • • Code type Size of the codebase Ancillary languages used (i. e. JSP, Java. Script, HTML…) Number of vulnerabilities Type of vulnerabilities (i. e. what analyzer is used) Complexity of the codebase © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

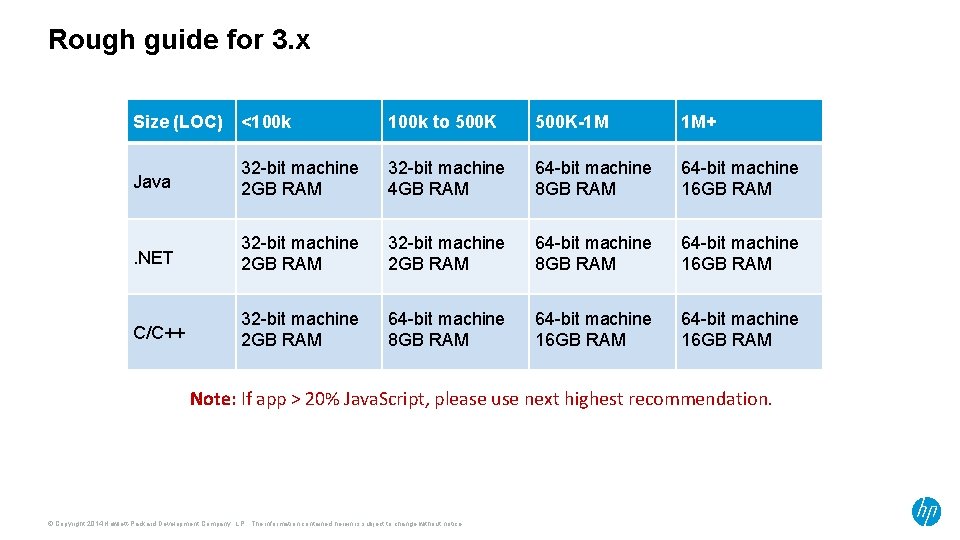
Rough guide for 3. x Size (LOC) <100 k to 500 K-1 M 1 M+ Java 32 -bit machine 2 GB RAM 32 -bit machine 4 GB RAM 64 -bit machine 8 GB RAM 64 -bit machine 16 GB RAM . NET 32 -bit machine 2 GB RAM 64 -bit machine 8 GB RAM 64 -bit machine 16 GB RAM C/C++ 32 -bit machine 2 GB RAM 64 -bit machine 8 GB RAM 64 -bit machine 16 GB RAM Note: If app > 20% Java. Script, please use next highest recommendation. © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

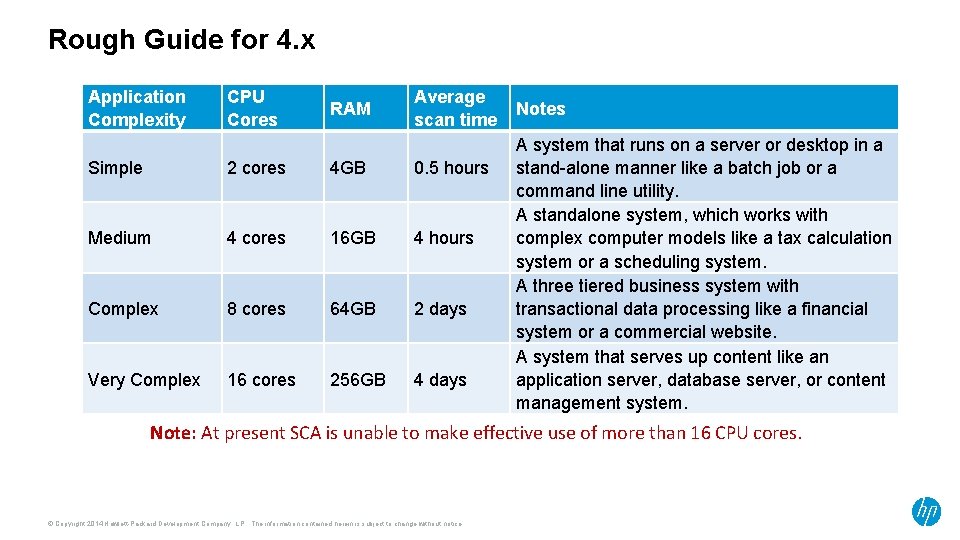
Rough Guide for 4. x Application Complexity CPU Cores RAM Average scan time Simple 2 cores 4 GB 0. 5 hours Medium 4 cores 16 GB 4 hours Complex 8 cores 64 GB 2 days Very Complex 16 cores 256 GB 4 days Notes A system that runs on a server or desktop in a stand-alone manner like a batch job or a command line utility. A standalone system, which works with complex computer models like a tax calculation system or a scheduling system. A three tiered business system with transactional data processing like a financial system or a commercial website. A system that serves up content like an application server, database server, or content management system. Note: At present SCA is unable to make effective use of more than 16 CPU cores. © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Tips on Improving Performance

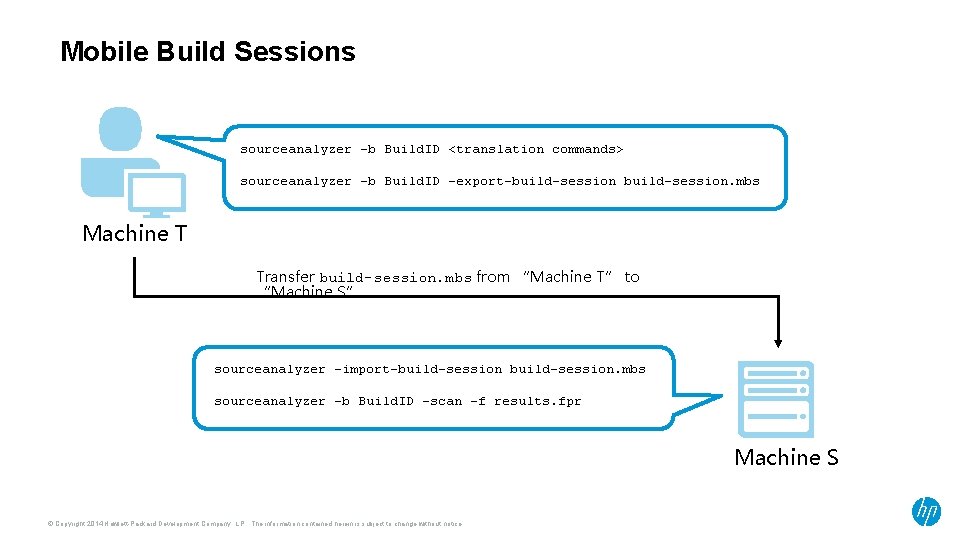
Mobile Build Sessions sourceanalyzer -b Build. ID <translation commands> sourceanalyzer -b Build. ID -export-build-session. mbs Machine T Transfer build-session. mbs from “Machine T” to “Machine S” sourceanalyzer -import-build-session. mbs sourceanalyzer -b Build. ID -scan -f results. fpr Machine S © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

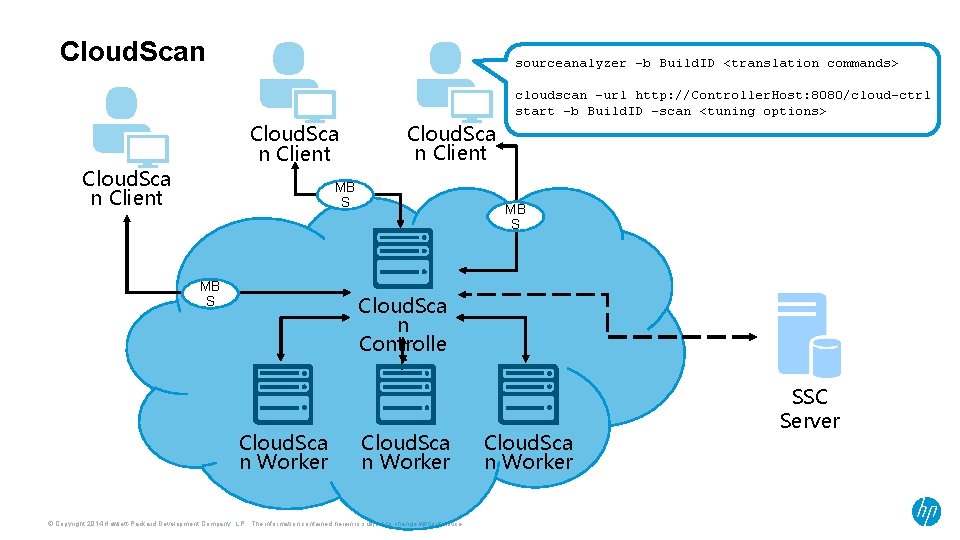
Cloud. Scan sourceanalyzer -b Build. ID <translation commands> cloudscan –url http: //Controller. Host: 8080/cloud-ctrl start -b Build. ID -scan <tuning options> Cloud. Sca n Client MB S Cloud. Sca n Controlle r Cloud. Sca n Worker © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Cloud. Sca n Worker SSC Server

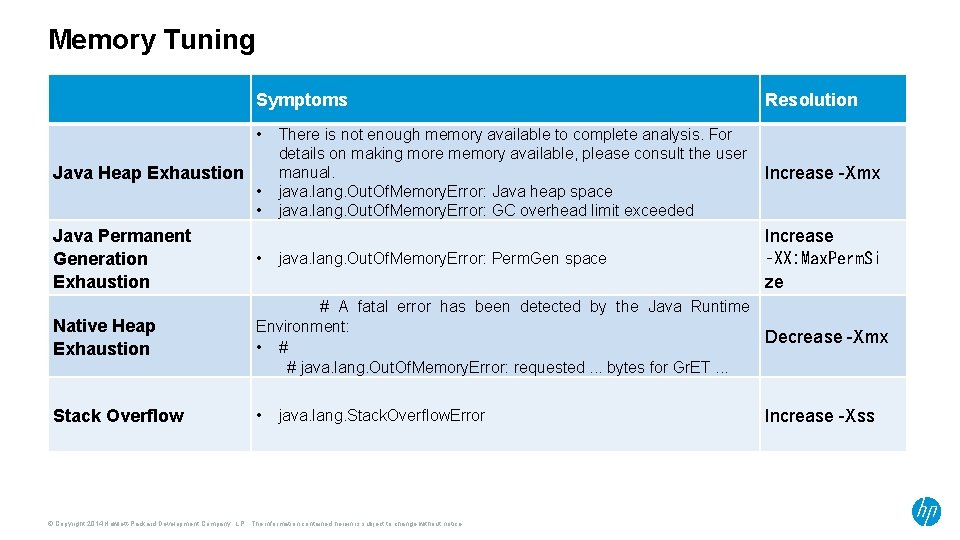
Memory Tuning Symptoms • Java Heap Exhaustion • • Resolution There is not enough memory available to complete analysis. For details on making more memory available, please consult the user manual. java. lang. Out. Of. Memory. Error: Java heap space java. lang. Out. Of. Memory. Error: GC overhead limit exceeded Increase -Xmx java. lang. Out. Of. Memory. Error: Perm. Gen space Increase ‑XX: Max. Perm. Si ze Java Permanent Generation Exhaustion • Native Heap Exhaustion # A fatal error has been detected by the Java Runtime Environment: Decrease -Xmx • # # java. lang. Out. Of. Memory. Error: requested. . . bytes for Gr. ET. . . Stack Overflow • java. lang. Stack. Overflow. Error © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Increase -Xss

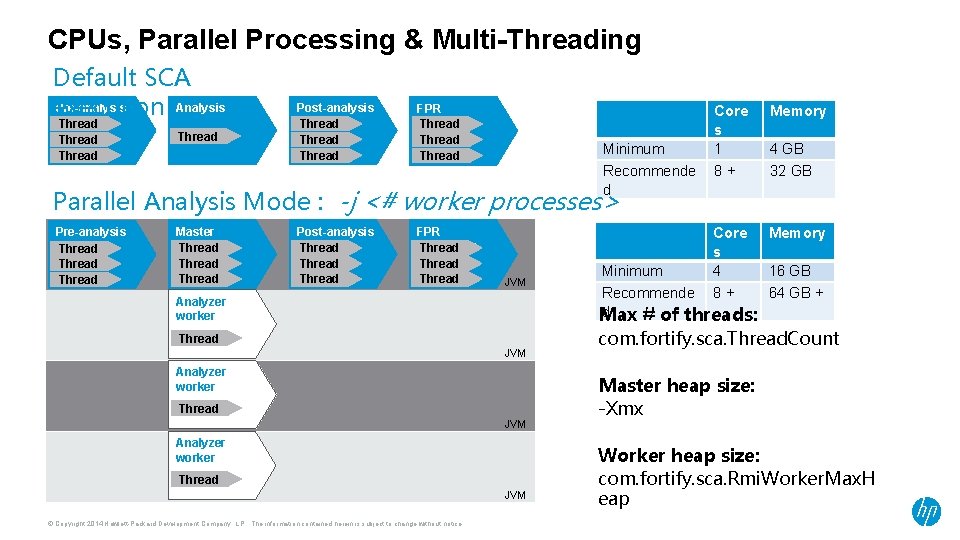
CPUs, Parallel Processing & Multi-Threading Default SCA Pre-analysis Analysis execution Thread Post-analysis Thread FPR generation Thread Minimum Recommende d Core s 1 8+ Memory Core s 4 8+ Memory 4 GB 32 GB Parallel Analysis Mode : -j <# worker processes> Pre-analysis Thread Master Thread Post-analysis Thread FPR generation Thread JVM Analyzer worker Thread JVM © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Minimum 16 GB Recommende 64 GB + d Max # of threads: com. fortify. sca. Thread. Count Master heap size: -Xmx Worker heap size: com. fortify. sca. Rmi. Worker. Max. H eap

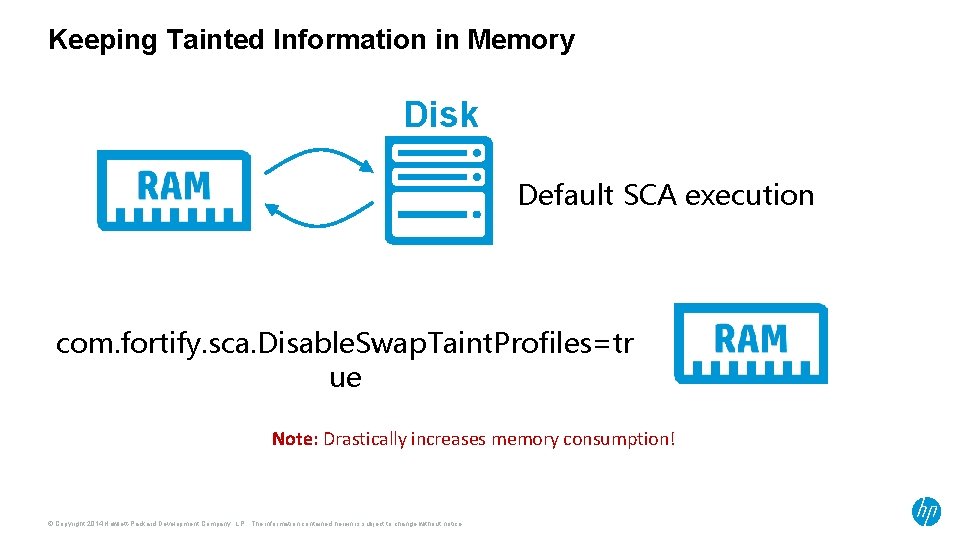
Keeping Tainted Information in Memory Disk Default SCA execution com. fortify. sca. Disable. Swap. Taint. Profiles=tr ue Note: Drastically increases memory consumption! © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Scan Quality vs. Performance

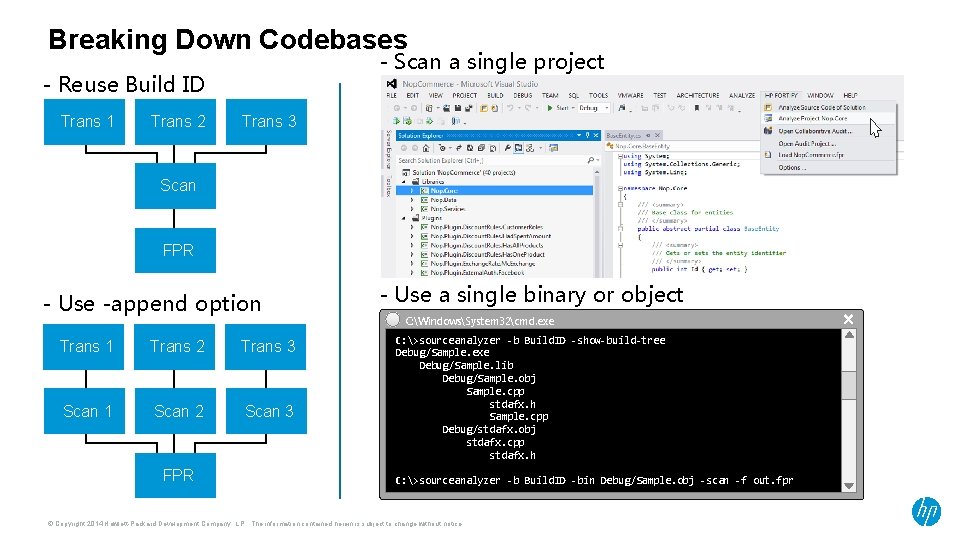
Breaking Down Codebases - Scan a single project - Reuse Build ID Trans 1 Trans 2 Trans 3 Scan FPR - Use -append option Trans 1 Trans 2 Trans 3 Scan 1 Scan 2 Scan 3 FPR - Use a single binary or object C: WindowsSystem 32cmd. exe (C/C++) C: >sourceanalyzer -b Build. ID -show-build-tree Debug/Sample. exe Debug/Sample. lib Debug/Sample. obj Sample. cpp stdafx. h Sample. cpp Debug/stdafx. obj stdafx. cpp stdafx. h C: >sourceanalyzer -b Build. ID -bin Debug/Sample. obj -scan -f out. fpr © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

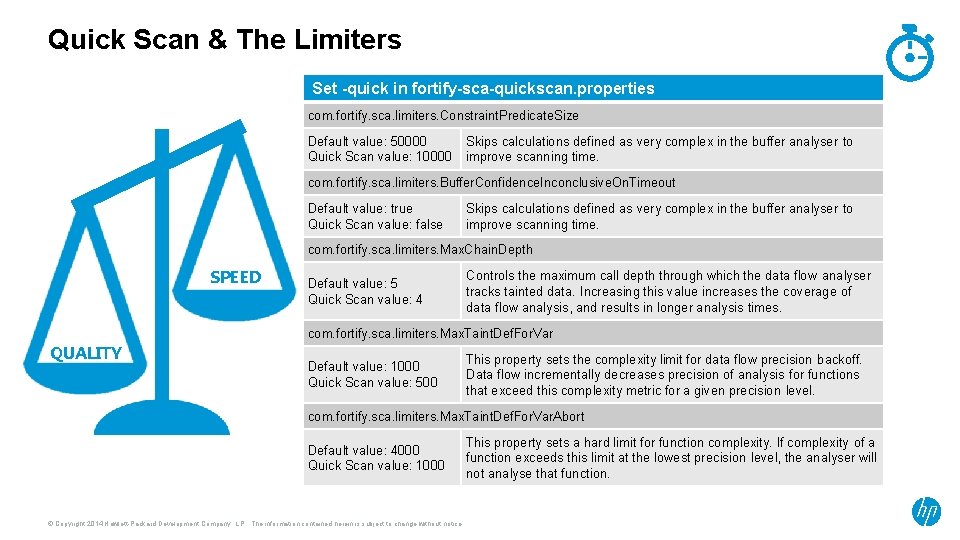
Quick Scan & The Limiters Set -quick in fortify-sca-quickscan. properties com. fortify. sca. limiters. Constraint. Predicate. Size Default value: 50000 Quick Scan value: 10000 Skips calculations defined as very complex in the buffer analyser to improve scanning time. com. fortify. sca. limiters. Buffer. Confidence. Inconclusive. On. Timeout Default value: true Quick Scan value: false Skips calculations defined as very complex in the buffer analyser to improve scanning time. com. fortify. sca. limiters. Max. Chain. Depth SPEED Default value: 5 Quick Scan value: 4 Controls the maximum call depth through which the data flow analyser tracks tainted data. Increasing this value increases the coverage of data flow analysis, and results in longer analysis times. com. fortify. sca. limiters. Max. Taint. Def. For. Var QUALITY Default value: 1000 Quick Scan value: 500 This property sets the complexity limit for data flow precision backoff. Data flow incrementally decreases precision of analysis for functions that exceed this complexity metric for a given precision level. com. fortify. sca. limiters. Max. Taint. Def. For. Var. Abort Default value: 4000 Quick Scan value: 1000 © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. This property sets a hard limit for function complexity. If complexity of a function exceeds this limit at the lowest precision level, the analyser will not analyse that function.

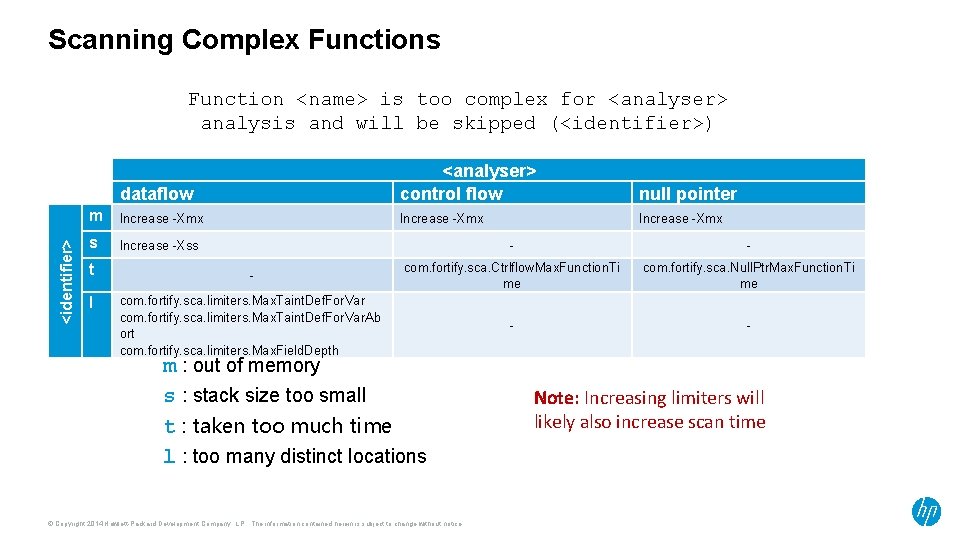
Scanning Complex Functions Function <name> is too complex for <analyser> analysis and will be skipped (<identifier>) dataflow <identifier> m Increase -Xmx s t l <analyser> control flow null pointer Increase -Xmx Increase -Xss - - - com. fortify. sca. Ctrlflow. Max. Function. Ti me com. fortify. sca. Null. Ptr. Max. Function. Ti me com. fortify. sca. limiters. Max. Taint. Def. For. Var. Ab ort com. fortify. sca. limiters. Max. Field. Depth - - m : out of memory s : stack size too small t : taken too much time l : too many distinct locations © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Note: Increasing limiters will likely also increase scan time

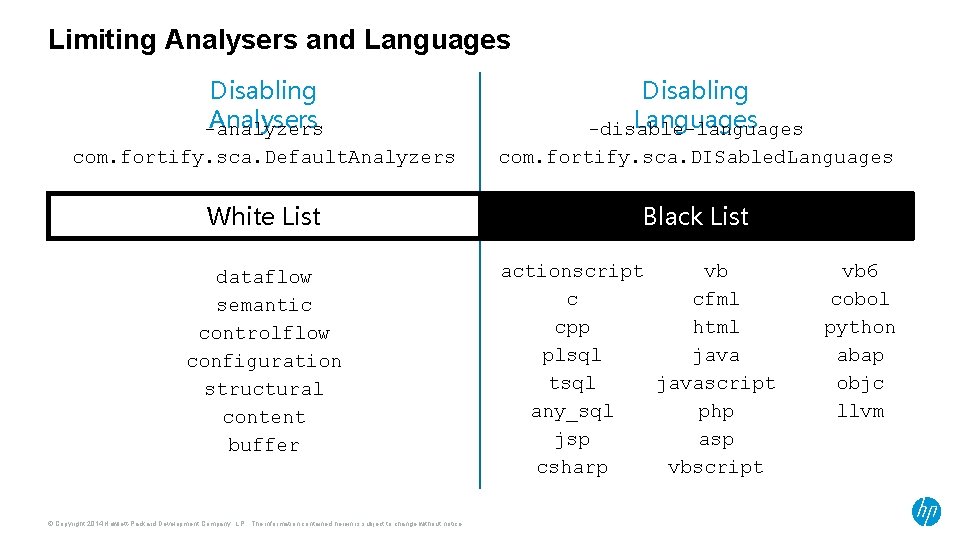
Limiting Analysers and Languages Disabling Analysers -analyzers Disabling Languages -disable-languages com. fortify. sca. Default. Analyzers com. fortify. sca. DISabled. Languages White List Black List dataflow semantic controlflow configuration structural content buffer © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. actionscript vb c cfml cpp html plsql java tsql javascript any_sql php jsp asp csharp vbscript vb 6 cobol python abap objc llvm

Scan Size vs. Performance

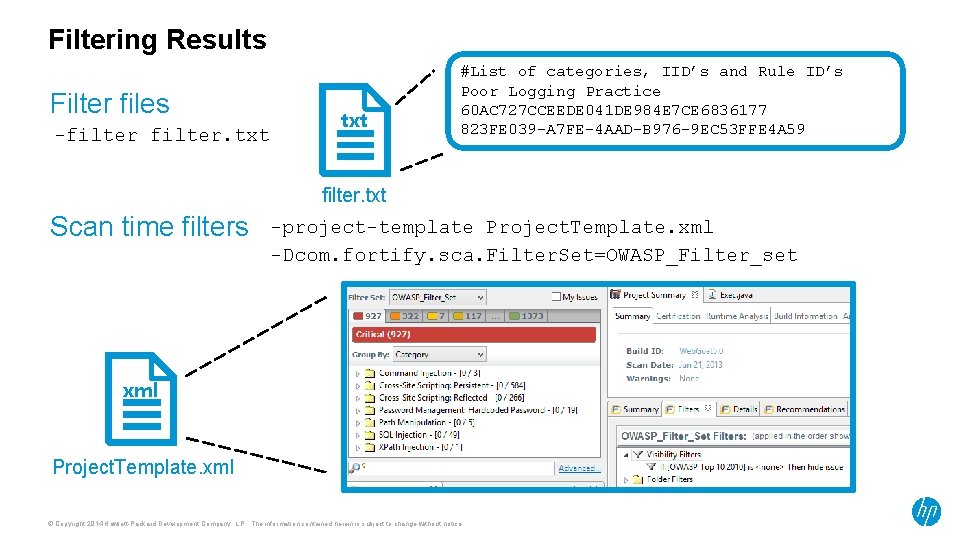
Filtering Results Filter files -filter. txt #List of categories, IID’s and Rule ID’s Poor Logging Practice 60 AC 727 CCEEDE 041 DE 984 E 7 CE 6836177 823 FE 039 -A 7 FE-4 AAD-B 976 -9 EC 53 FFE 4 A 59 filter. txt Scan time filters -project-template Project. Template. xml -Dcom. fortify. sca. Filter. Set=OWASP_Filter_set xml Project. Template. xml © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

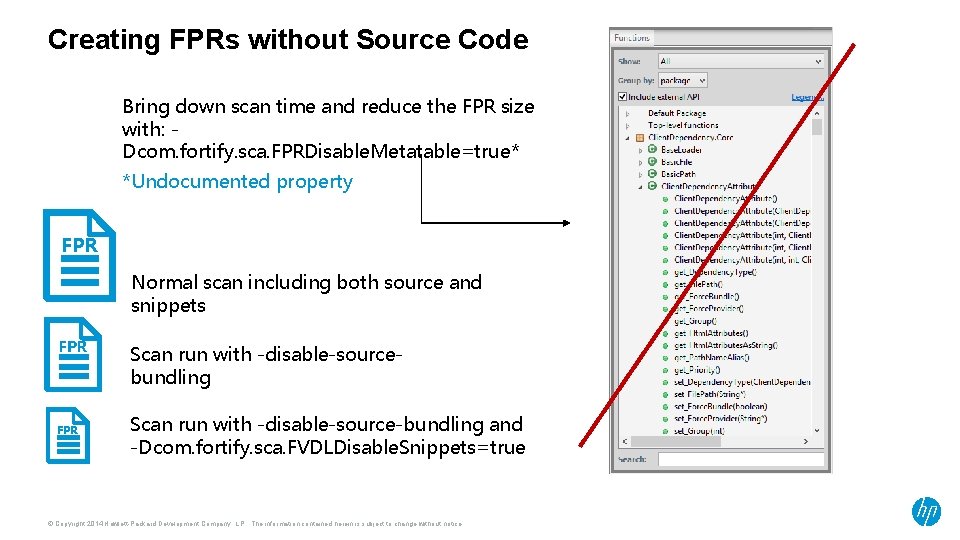
Creating FPRs without Source Code Bring down scan time and reduce the FPR size with: Dcom. fortify. sca. FPRDisable. Metatable=true* *Undocumented property FPR Normal scan including both source and snippets FPR Scan run with -disable-sourcebundling Scan run with -disable-source-bundling and -Dcom. fortify. sca. FVDLDisable. Snippets=true © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Opening Large FPRs Set in <SCA Install Directory>Coreconfigfortify. properties com. fortify. Disable. Program. Info=true This disables use of the code navigation features within AWB. com. fortify. model. Issue. Cut. Off. Start. Index=<number> (inclusive) com. fortify. model. Issue. Cut. Off. End. Index=<number> (exclusive) The Issue. Cut. Off. Start. Index property is inclusive and Issue. Cut. Off. End. Index is exclusive so that you can specify a subset of issues you wish to see. E. g. To see the first 100 issues, you can specify: com. fortify. model. Issue. Cut. Off. Start. Index=0 com. fortify. model. Issue. Cut. Off. End. Index=101 However because the Issue. Cut. Off. Start. Index is 0 by default, this can be left out. com. fortify. model. Issue. Cut. Off. By. Category. Start. Index=<number> (inclusive) com. fortify. model. Issue. Cut. Off. By. Category. End. Index=<number> (exclusive) These are similar to the above properties except these are specified for every category. E. g. If you wanted to see the first 5 issues for every category you would specify: com. fortify. model. Issue. Cut. Off. By. Category. End. Index=6 com. fortify. Restrict. Issue. Loading=true This restricts the data that is held in memory, but may cause poor performance. com. fortify. model. Minimal. Load=true This restricts a lot of data from being loaded in the FPR so that only the bare minimum information is loaded. This will also restrict usage of the functions view and may prevent the source being loaded from within the FPR. com. fortify. model. Max. Engine. Error. Count=<number> Available from v 4. 20. Limits the number of errors loaded with the FPR. For projects with a large number of scan warnings this can significantly reduce both load time in AWB and the amount of memory required to © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. FPR

Monitoring Long Running Scans
![SCAState options SCA process ID Options all heapdump threaddump fullthreaddump programinfo properties scaversion timers SCAState [options] <SCA process ID> Options --all --heap-dump --thread-dump --full-thread-dump --program-info -properties -scaversion -timers](https://slidetodoc.com/presentation_image/4544c744f1b70dd6844f5ad3d387c364/image-30.jpg)
SCAState [options] <SCA process ID> Options --all --heap-dump --thread-dump --full-thread-dump --program-info -properties -scaversion -timers -vminfo Process ID Windows • Open a command prompt • Run: tasklist • Locate java. exe PID Linux/Unix • Run: ps aux | grep sourceanalyzer © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

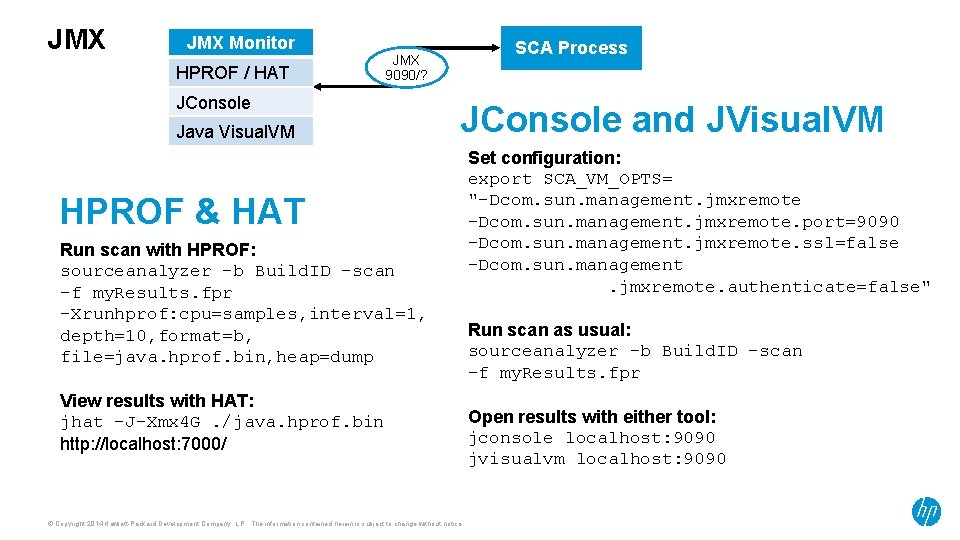
JMX Monitor HPROF / HAT SCA Process JMX 9090/? JConsole Java Visual. VM JConsole and JVisual. VM HPROF & HAT Run scan with HPROF: sourceanalyzer -b Build. ID –scan –f my. Results. fpr -Xrunhprof: cpu=samples, interval=1, depth=10, format=b, file=java. hprof. bin, heap=dump View results with HAT: jhat -J-Xmx 4 G. /java. hprof. bin http: //localhost: 7000/ © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice. Set configuration: export SCA_VM_OPTS= "-Dcom. sun. management. jmxremote. port=9090 -Dcom. sun. management. jmxremote. ssl=false -Dcom. sun. management. jmxremote. authenticate=false" Run scan as usual: sourceanalyzer -b Build. ID –scan –f my. Results. fpr Open results with either tool: jconsole localhost: 9090 jvisualvm localhost: 9090

Any questions? © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.

Thank you © Copyright 2014 Hewlett-Packard Development Company, L. P. The information contained herein is subject to change without notice.