Formal Verification of a Novel Snooping Cache Coherence



- Slides: 17

Formal Verification of a Novel Snooping Cache Coherence Protocol for CMP Xuemei Zhao, Karl Sammut, and Fangpo He Flinders University, Australia

Background n n n The emergence of CMP brings huge research space to increase performance More caches on chip, low L 2 latency, fast cache-to-cache access Traditional SMP memory hierarchy and cache coherence protocol will diminish CMP’s performance. Two traditional structures: Private L 2 and Shared L 2. Two protocols: Snooping protocol, Directory-based protocol Formal verification is useful for discovering and correcting any errors at the early stage.

Outline n n n Cache architecture of SPS 2 Description of SPS 2 protocol Verification using Hytech Verification using SMV Conclusion

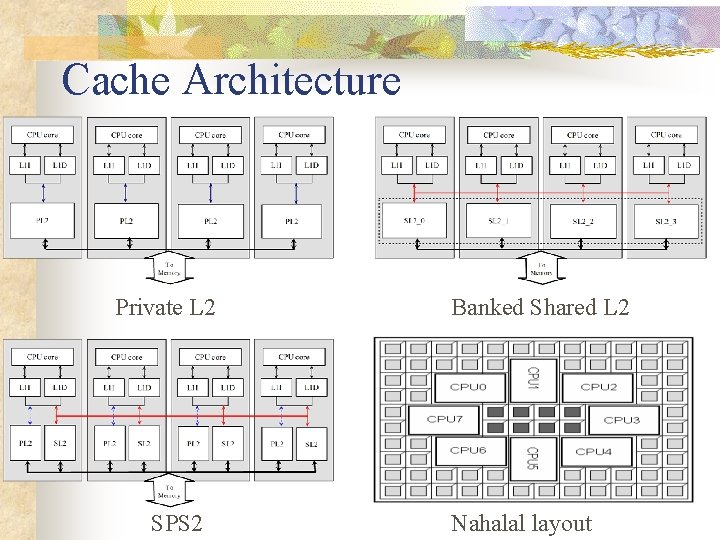
Cache Architecture Private L 2 SPS 2 Banked Shared L 2 Nahalal layout

Advantages of SPS 2 n n n PL 2 and SL 2 could use different association mechanism PL 2 and SL 2 could have different size and replacement policy PL 2 leads to low latency. SL 2 provides high capacity No need new CPU instruction, simple interface

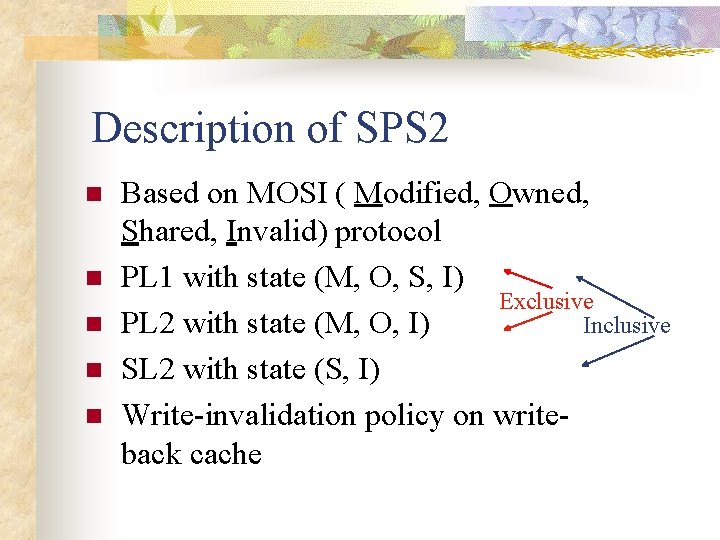
Description of SPS 2 n n n Based on MOSI ( Modified, Owned, Shared, Invalid) protocol PL 1 with state (M, O, S, I) Exclusive Inclusive PL 2 with state (M, O, I) SL 2 with state (S, I) Write-invalidation policy on writeback cache

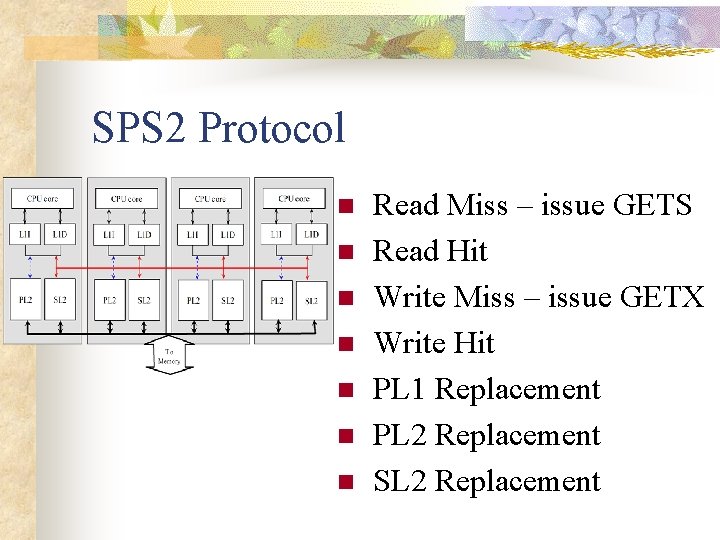
SPS 2 Protocol n n n n Read Miss – issue GETS Read Hit Write Miss – issue GETX Write Hit PL 1 Replacement PL 2 Replacement SL 2 Replacement

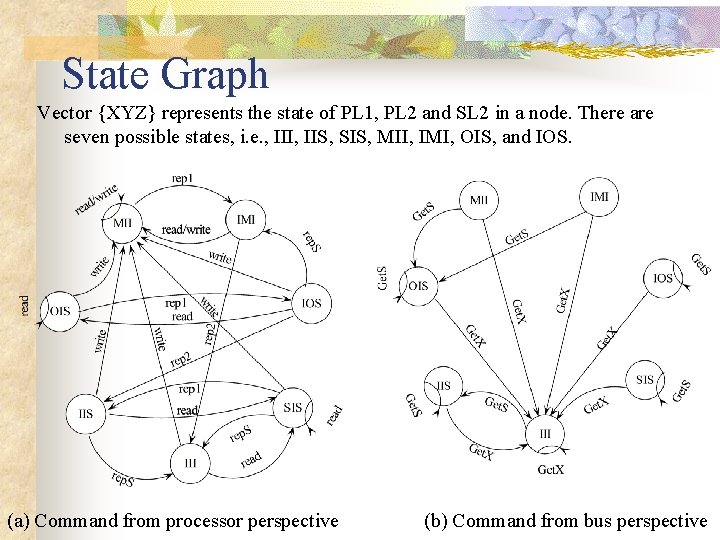
State Graph Vector {XYZ} represents the state of PL 1, PL 2 and SL 2 in a node. There are seven possible states, i. e. , III, IIS, SIS, MII, IMI, OIS, and IOS. (a) Command from processor perspective (b) Command from bus perspective

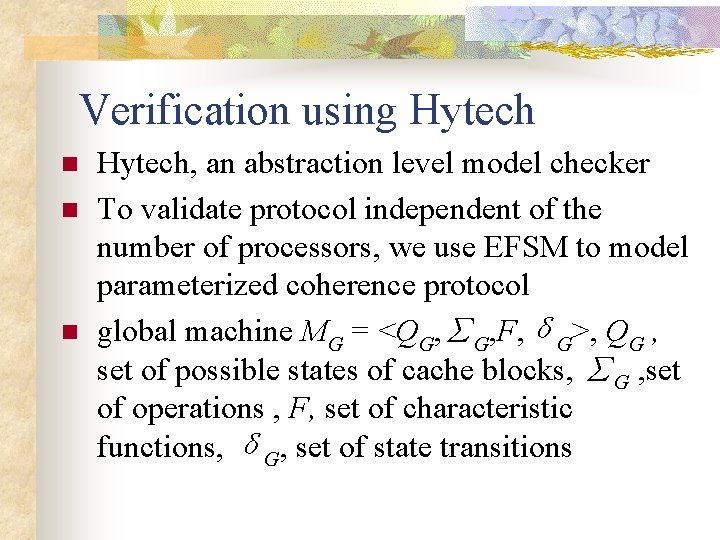
Verification using Hytech n n n Hytech, an abstraction level model checker To validate protocol independent of the number of processors, we use EFSM to model parameterized coherence protocol global machine MG = <QG, ∑G, F, δG>, QG , set of possible states of cache blocks, ∑G , set of operations , F, set of characteristic functions, δG, set of state transitions

EFSM expression of SPS 2 (r 1) SIS+OIS+MII≥ 1→__ (r 2) III≥ 1, MII=0, IMI=0 → III'=0, SIS'=SIS+1, IIS'=IIS+III-1 (r 3) III≥ 1, MII≥ 1 → III'=0, SIS'=SIS+1, MII'=MII-1, OIS'=OIS+1, IIS'=IIS+III-1 (r 4) III≥ 1, IMI≥ 1 → III'=0, SIS'=SIS+1, IMI'=IMI-1, IOS'=IOS+1, IIS'=IIS+III-1 (r 5) IIS≥ 1 → IIS'=IIS-1, SIS'=SIS+1 (r 6) IMI≥ 1 → MII'=MII+1, IMI'=IMI-1 (r 7) IOS≥ 1 → OIS'=OIS+1, IOS'=IOS-1 ……. . . Read hit event (r 1), read miss events (r 2) – (r 7)

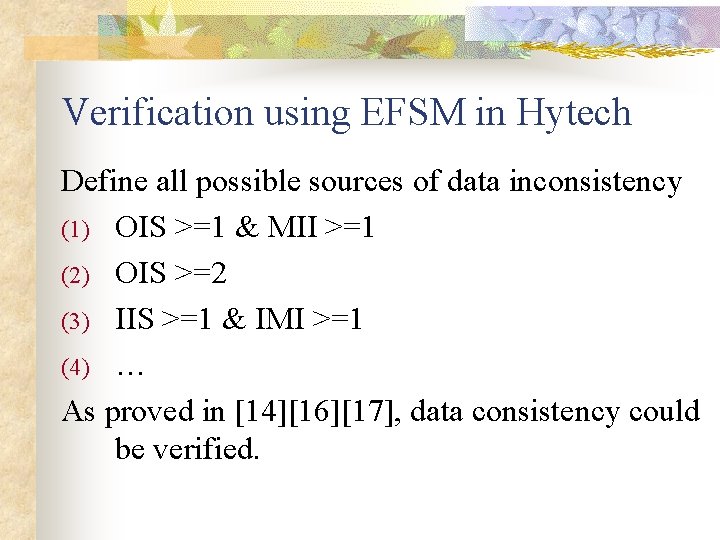
Verification using EFSM in Hytech Define all possible sources of data inconsistency (1) OIS >=1 & MII >=1 (2) OIS >=2 (3) IIS >=1 & IMI >=1 (4) … As proved in [14][16][17], data consistency could be verified.

Verification using SMV n n n SMV is an intermediate formal verification tool. To avoid state explosion, SMV uses OBDD (ordered binary decision diagrams), which could check finite-state systems satisfy specification given in CTL Protocols have been proven by SMV: Gigamax, Futurebus+, FLASH

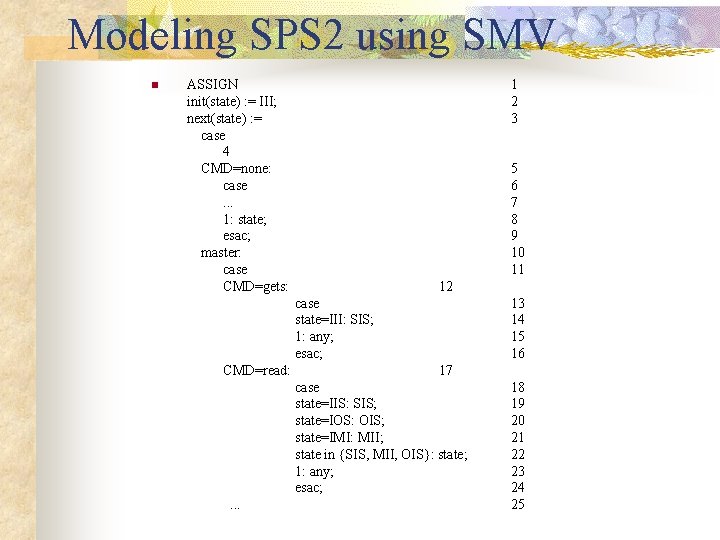
Modeling SPS 2 using SMV n ASSIGN init(state) : = III; next(state) : = case 4 CMD=none: case. . . 1: state; esac; master: case CMD=gets: 1 2 3 5 6 7 8 9 10 11 12 case state=III: SIS; 1: any; esac; CMD=read: 13 14 15 16 17 case state=IIS: SIS; state=IOS: OIS; state=IMI: MII; state in {SIS, MII, OIS}: state; 1: any; esac; . . . 18 19 20 21 22 23 24 25

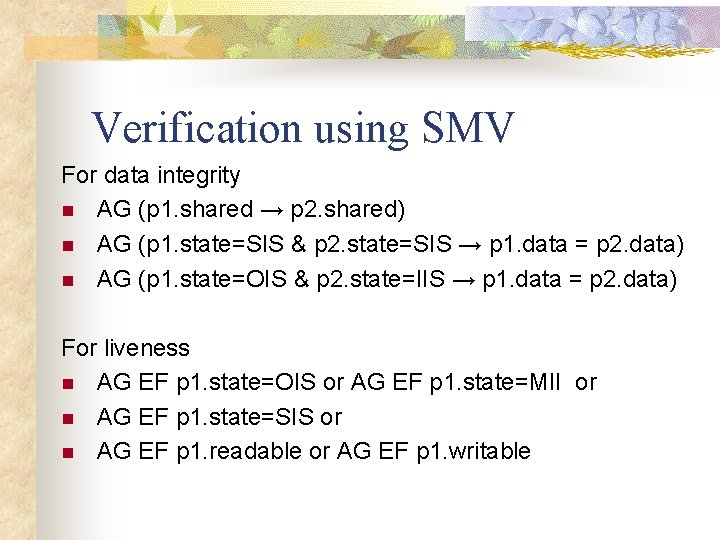
Verification using SMV For data integrity n AG (p 1. shared → p 2. shared) n AG (p 1. state=SIS & p 2. state=SIS → p 1. data = p 2. data) n AG (p 1. state=OIS & p 2. state=IIS → p 1. data = p 2. data) For liveness n AG EF p 1. state=OIS or AG EF p 1. state=MII or n AG EF p 1. state=SIS or n AG EF p 1. readable or AG EF p 1. writable

Conclusion n SPS 2 takes advantages of the low latency of L 2 P and the high capacity of L 2 S. New proposed state graph is used for description of SPS 2 and verification Using two formal verification method, function correctness of SPS 2 is proven

Thanks, any question is appreciated!

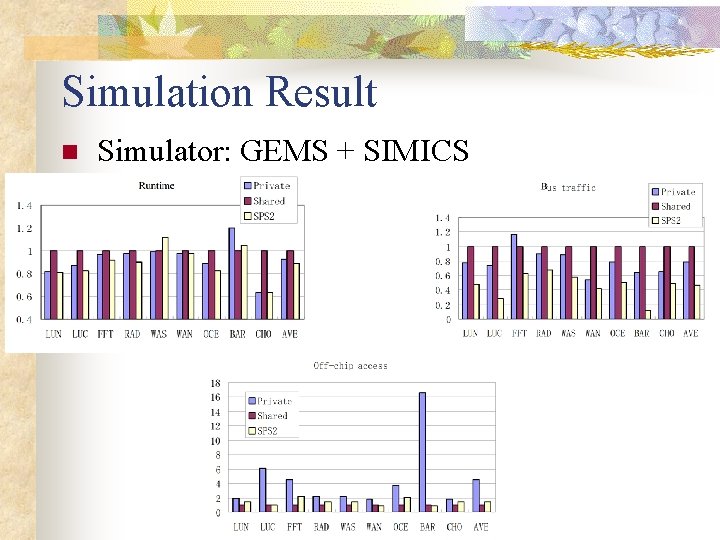
Simulation Result n Simulator: GEMS + SIMICS