Forge an Ironclad Reporting Strategy for Security Metrics



- Slides: 11

Forge an Ironclad Reporting Strategy for Security Metrics Help the board understand what they need to know – no more, no less. Info-Tech Research Group Inc. is a global leader in providing IT research and advice. Info-Tech’s products and services combine actionable insight and relevant advice with ready-to-use tools and templates that cover the full spectrum of IT concerns. © 1997 -2019 Info-Tech Research Group Inc. Info-Tech Research Group 1

ANALYST PERSPECTIVE Your time with the board will be short, so make it count. When it comes to reporting security metrics to the board, less is more. But that doesn’t mean you can’t share all of the data you think is key to enhancing your security program. It just means you have to be clever about how you integrate that material. You need to boil down your key security metrics into just three high-level categories that tell the board a story about risk. This way, you can present several related metrics as one unified metric that captures and summarizes the risks you’ve been observing. Risk is a language business leaders understand, so putting your metrics in that context helps to make them more relatable than a lowlevel discussion about how the security program does what it does. Logan Rohde, Research Specialist, Security, Risk, & Compliance Info-Tech Research Group 2

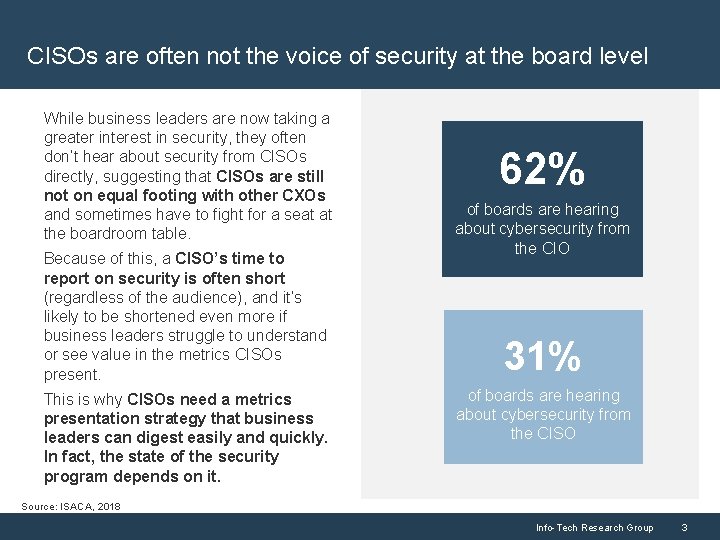
CISOs are often not the voice of security at the board level While business leaders are now taking a greater interest in security, they often don’t hear about security from CISOs directly, suggesting that CISOs are still not on equal footing with other CXOs and sometimes have to fight for a seat at the boardroom table. Because of this, a CISO’s time to report on security is often short (regardless of the audience), and it’s likely to be shortened even more if business leaders struggle to understand or see value in the metrics CISOs present. This is why CISOs need a metrics presentation strategy that business leaders can digest easily and quickly. In fact, the state of the security program depends on it. 62% of boards are hearing about cybersecurity from the CIO 31% of boards are hearing about cybersecurity from the CISO Source: ISACA, 2018 Info-Tech Research Group 3

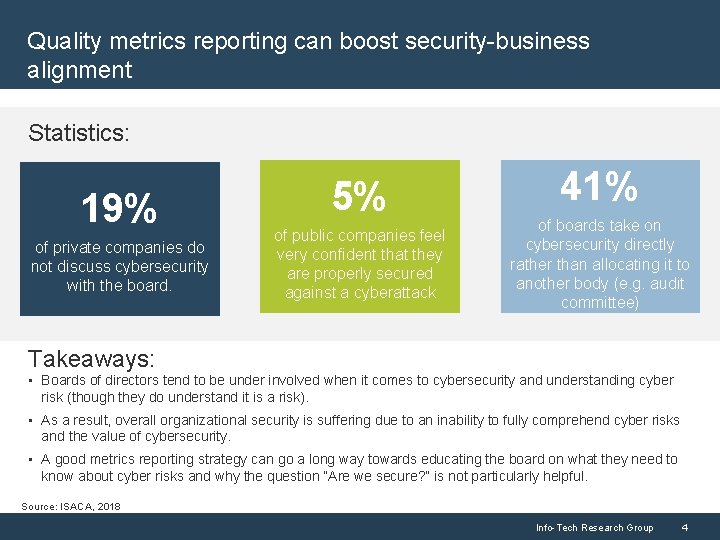
Quality metrics reporting can boost security-business alignment Statistics: 19% of private companies do not discuss cybersecurity with the board. 5% of public companies feel very confident that they are properly secured against a cyberattack 41% of boards take on cybersecurity directly rather than allocating it to another body (e. g. audit committee) Takeaways: • Boards of directors tend to be under involved when it comes to cybersecurity and understanding cyber risk (though they do understand it is a risk). • As a result, overall organizational security is suffering due to an inability to fully comprehend cyber risks and the value of cybersecurity. • A good metrics reporting strategy can go a long way towards educating the board on what they need to know about cyber risks and why the question “Are we secure? ” is not particularly helpful. Source: ISACA, 2018 Info-Tech Research Group 4

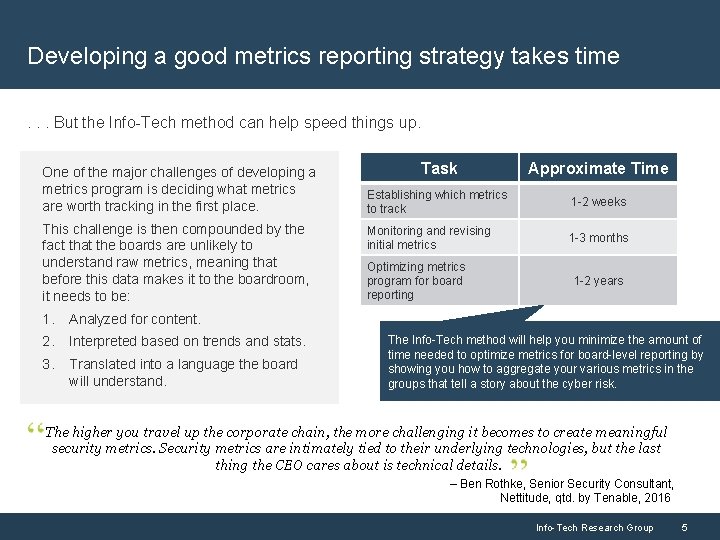
Developing a good metrics reporting strategy takes time. . . But the Info-Tech method can help speed things up. One of the major challenges of developing a metrics program is deciding what metrics are worth tracking in the first place. This challenge is then compounded by the fact that the boards are unlikely to understand raw metrics, meaning that before this data makes it to the boardroom, it needs to be: 1. Analyzed for content. 2. Interpreted based on trends and stats. 3. Translated into a language the board will understand. Task Approximate Time Establishing which metrics to track 1 -2 weeks Monitoring and revising initial metrics 1 -3 months Optimizing metrics program for board reporting 1 -2 years The Info-Tech method will help you minimize the amount of time needed to optimize metrics for board-level reporting by showing you how to aggregate your various metrics in the groups that tell a story about the cyber risk. The higher you travel up the corporate chain, the more challenging it becomes to create meaningful security metrics. Security metrics are intimately tied to their underlying technologies, but the last thing the CEO cares about is technical details. – Ben Rothke, Senior Security Consultant, Nettitude, qtd. by Tenable, 2016 Info-Tech Research Group 5

Who is this research for? This research is designed for people looking to adapt their security metrics into a format the board can understand easily digest. For this research to be helpful, you will need to have a metrics program up and running already, as this research will not walk you through the steps of how to build the entire metrics program. If you need help developing a metrics program from scratch, stop here and direct your attention towards Info-Tech’s Implement and Optimize an Effective Security Management Metrics Program blueprint. Once complete, return here and follow the Info-Tech method to get your metrics ready for the boardroom. Implement and Optimize an Effective Security Management Metrics Program Info-Tech Research Group 6

Our understanding of the problem This Research Is is Designed For: This Research Will Help You: üCISO with a well-developed security metrics üUnderstand how to convey your security program. metrics in relatable terms. üFacilitate discussions about organizational risk related to cybersecurity. üStrategize a method for reporting several complex metrics as though they were one simple metric. üMake the most of your presentation time and help demonstrate the value of security. This Research Will Also Assist: This Research Will Help Them: You: üSecurity Manager üIT Manager üBusiness leaders interested in learning more üEnhance business-security collaboration. üDefine a risk tolerance that accurately captures about cyber risks the cyber threat landscape and the organization’s place within it. Info-Tech Research Group 7

Executive summary Situation • Board-level presentations are a rare opportunity for security and the • business to understand each other’s viewpoints and the things they care about. Because both sides think in different terms, reaching this understanding can be easier said than done. Complication • Out of all the metrics your security program tracks, how do you decide • which ones are important enough to share with the board? Once you’ve made that decision, how will you explain those metrics in terms that will be meaningful to the board? 1. Metrics don’t expire Board-level metrics look different depending on maturity. However, the basic, lower-maturity metrics don’t stop being relevant to higher-maturity organizations; they just take more specified forms. 2. Hard times happen; be a leader Not all metrics show positive results. When you have to give bad news, demonstrate your knowledge and leadership by telling the board how you will address the issues. Resolution • Learn to view your individual metrics as component parts in a larger story about your organization’s security posture. • Decide what message the business needs to hear in order to appreciate the security program’s successes and areas for • • improvement. Assemble groups of metrics that help to illustrate that message. Strategize ways of using those groups to tell a broader story about risk, allowing you to bridge the language gap between security and business leaders. Info-Tech Research Group 8

Use these icons to help direct you as you navigate this research Use these icons to help guide you through each step of the blueprint and direct you to content related to the recommended activities. This icon denotes a slide where a supporting Info-Tech tool or template will help you perform the activity or step associated with the slide. Refer to the supporting tool or template to get the best results and proceed to the next step of the project. This icon denotes a slide with an associated activity. The activity can be performed either as part of your project or with the support of Info-Tech team members, who will come onsite to facilitate a workshop for your organization. Info-Tech Research Group 9

Info-Tech offers various levels of support to best suit your needs DIY Toolkit “Our team has already made this critical project a priority, and we have the time and capability, but some guidance along the way would be helpful. ” Guided Implementation Workshop Consulting “Our team knows that we need to fix a process, but we need assistance to determine where to focus. Some check-ins along the way would help keep us on track. ” “We need to hit the ground running and get this project kicked off immediately. Our team has the ability to take this over once we get a framework and strategy in place. ” “Our team does not have the time or the knowledge to take this project on. We need assistance through the entirety of this project. ” Diagnostics and consistent frameworks used throughout all four options Info-Tech Research Group 10

Forge an Ironclad Reporting Strategy for Security Metrics 1. Develop a Risk-Based Reporting Model 1. 1 Understand the importance of presenting metrics to the board and how to do it effectively 1. 2 Consider example metrics to get started 1. 3 Learn how to make the first meeting count 1. 4 Create a risk story to teach the board about your security posture 1. 5 Refine your storytelling skills Best-Practice Toolkit Start with a winning reporting strategy. Learn to communicate through risk-based terms. Guided Implementations Info-Tech Research Group 11