Forensic Science Questioned Documents Part 3 Forging This




- Slides: 14

Forensic Science Questioned Documents: Part 3

�Forging �This money is known as counterfeiting. is one of the oldest crimes. �During the Civil War, when all banks issued their own currency, approximately one-third of money was counterfeit. This was a threat to the U. S. economy. �So in 1863, the United States adopted a national currency. Counterfeiting 2

�The adoption of the national currency really did not curtail the amount of counterfeiting. �In 1865, the Secret Service was created to investigate and stop counterfeiting. �Although counterfeiting is not as pervasive as it once was, it is still a common crime. The latest technology has made it much easier to copy and counterfeit money. In 1996, the U. S. government began to add new features to money. Counterfeiting (cont. ) 3

�Some of these features include: �A watermark �Color shifting ink �Off-center portrait �Randomly disbursed red and blue the paper �Microprinting Counterfeiting (cont. ) fibers in 4

Other Responsibilities �The Document Examination Unit not only examines questioned documents, but works with other areas that link to forgery and fraud. �One such area is Cryptology or Cryptography. �Cryptography comes from the Greek words kryptos (secret) and graphos (writing). �Codes and ciphers are examples of cryptography.

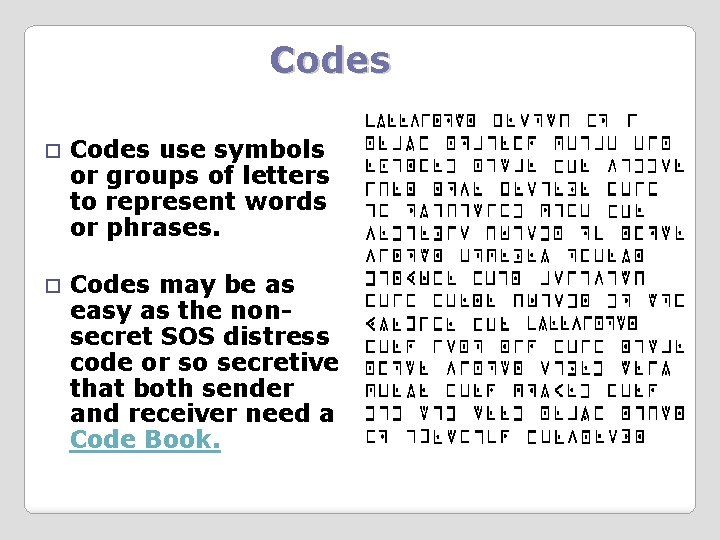
Codes use symbols or groups of letters to represent words or phrases. Codes may be as easy as the nonsecret SOS distress code or so secretive that both sender and receiver need a Code Book.

Morse Code �In 1838, Samuel Morse invented Morse Code. �Morse Code is not really a code, but an electro-magnetic telegraph system that uses a system of dots and dashes. �However, codes were sent in Morse Code format and then decoded. �Morse Code was a very important message system during World War I.

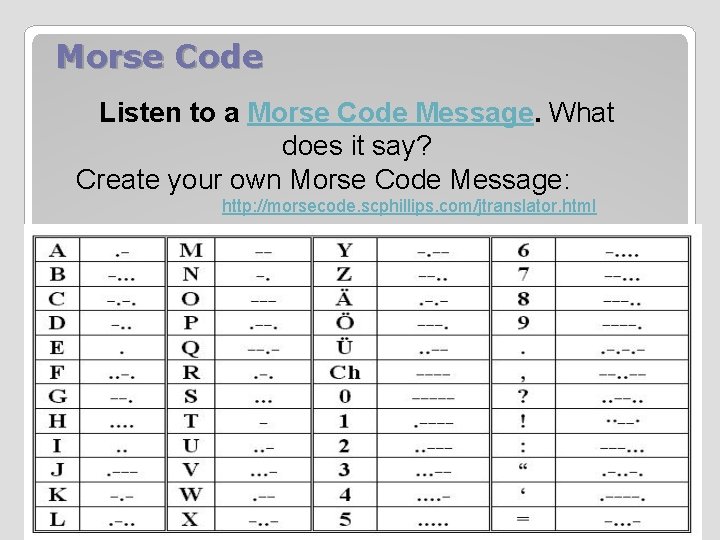
Morse Code Listen to a Morse Code Message. What does it say? Create your own Morse Code Message: http: //morsecode. scphillips. com/jtranslator. html

�During World War II, the Germans used the Enigma machine. �This machine could put a message into code in over 150 MILLION different ways. �The Germans believed that the Enigma was invincible, but eventually the code was broken by the Allies. https: //www. youtube. com/watch? v=Hb 44 b. GY 2 Kd. U The Enigma

Colossus - “The Bomb” Colossus was the machine that helped to break the Enigma code. Colossus was the world’s first programmable computer.

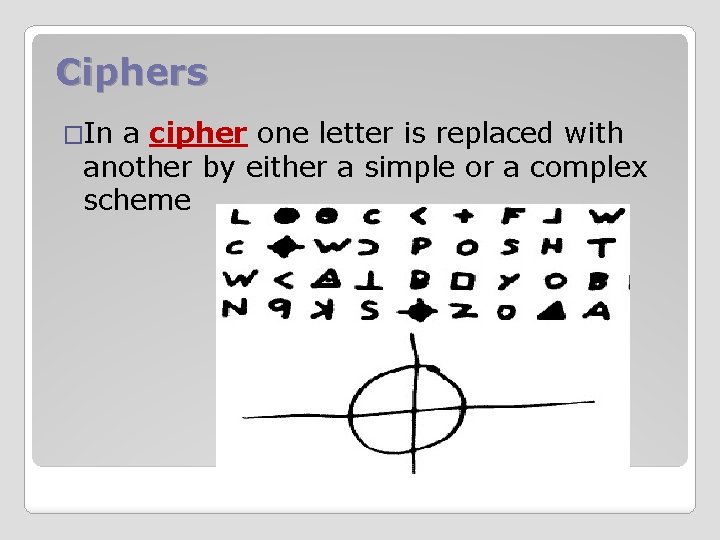
Ciphers �In a cipher one letter is replaced with another by either a simple or a complex scheme

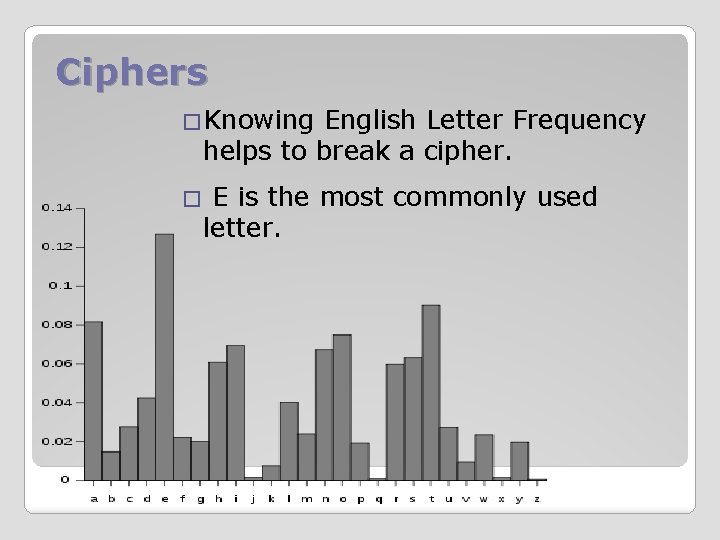
Ciphers �Knowing English Letter Frequency helps to break a cipher. E is the most commonly used letter. �

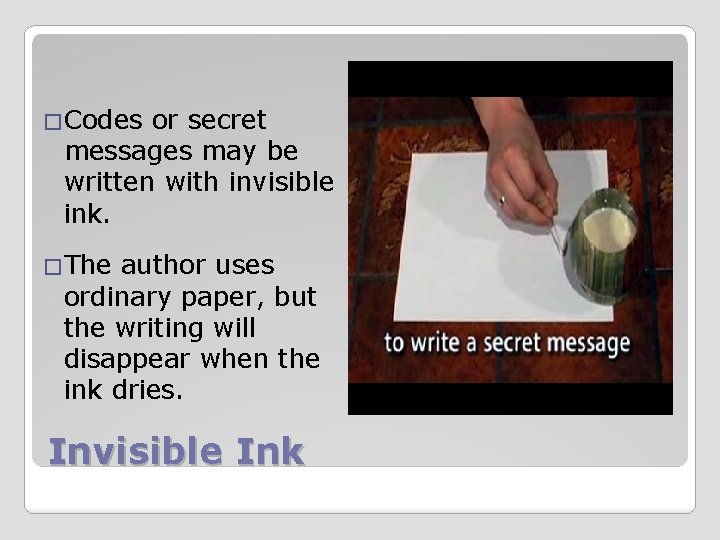
�Codes or secret messages may be written with invisible ink. �The author uses ordinary paper, but the writing will disappear when the ink dries. Invisible Ink

�Seeing the invisible message depends on the type of ink used. �UV light, heat, chemical developers or a combination of these will reveal the hidden message. Retrieving the Message