Forensic Investigation Techniques Michael Jones Overview Purpose People





- Slides: 10

Forensic Investigation Techniques Michael Jones

Overview • Purpose • People • Processes Michael Jones Digital Forensic Investigations 2

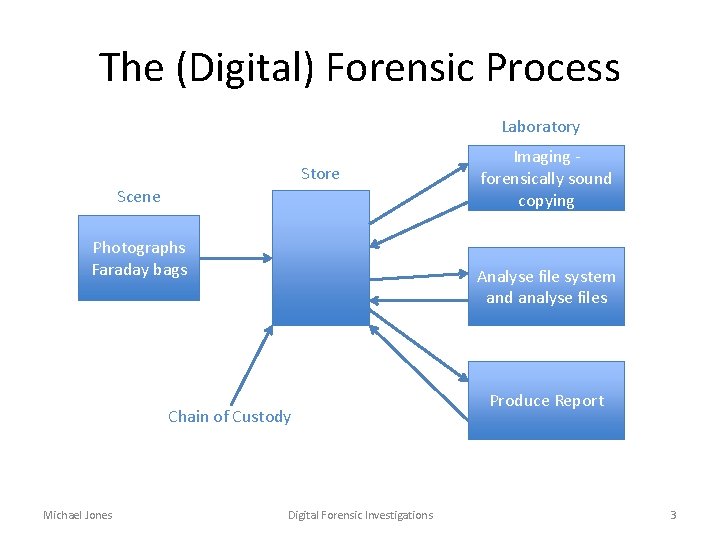
The (Digital) Forensic Process Laboratory Store Scene Photographs Faraday bags Analyse file system and analyse files Chain of Custody Michael Jones Imaging forensically sound copying Digital Forensic Investigations Produce Report 3

Review: Logical and Physical Views • Logical view – As seen via the file manager • Physical view – What is (physically) on the device • Questions – What might these be different? – What is ‘striping’? – Is ‘physical’ really physical? Michael Jones Digital Forensic Investigations 4

Imaging • Low (device) level – Duplicating the bit sequence – Output is a file – Multiple copies may be taken • Verification – Applying (hashing) algorithms to device and copy • MD 5, SHA 1 • If device and copy hashes match then copy is forensically sound • Devices and copies returned to (case) store Michael Jones Digital Forensic Investigations 5

Analysing the Image • Before: apply hashing algorithms • Processes: – Identify file system – Scan for known file types – Compare with logical view – Match logical and physical views and identify deleted files – Deeper analysis • After: apply hashing algorithms Michael Jones Digital Forensic Investigations 6

Digital Forensics Triage • Triage – Quick analysis to identify priorities – why? • Focus on logical view – Plus deleted files • Ideal outcomes of triage Michael Jones Digital Forensic Investigations 7

Main Analysis • That which is actually there – File dates and times – File and directory (folder) names – Metadata • That which might require interpretation – Examples • encoding and encryption • File manipulation (e. g. , changing first byte of a jpeg) Michael Jones Digital Forensic Investigations 8

Deeper Analysis • Can be time consuming • Secondary data – Additional processes needed • Examples – Use of slack space, unused space – Encoding and encryption – Steganography • E. g. , Snow Michael Jones Digital Forensic Investigations 9

Summary • Rigorous processes need to be followed – E. g. , ACPO guidelines • All investigations produce documentation • All documents and artefacts must be labelled and stored appropriately • Chain of custody must be unbroken Michael Jones Digital Forensic Investigations 10