Forensic and Investigative Accounting Chapter 14 Digital Forensics












- Slides: 19

Forensic and Investigative Accounting Chapter 14 Digital Forensics Analysis © 2009 CCH. All Rights Reserved. 4025 W. Peterson Ave. Chicago, IL 60646 -6085 1 800 248 3248 www. CCHGroup. com

Hacker Defined A hacker is generally defined as an individual or group whose intent is to gain access to a computer network for malicious purposes. Chapter 14 Forensic and Investigative Accounting 2

Collecting Clues and Evidence A forensic investigator needs to be familiar with the protocols used on the Internet to be able to collect clues about either internal or external attackers. In addition, when law enforcement officials send requests or subpoenas for information about a company’s logs, the forensic analyst must understand the type of information being sought. Chapter 14 Forensic and Investigative Accounting 3

Protocols Internet protocols are those rules allowing different operating systems and machines to communicate with one another over the Internet. Chapter 14 Forensic and Investigative Accounting 4

Transmission Control Protocol (TCP) and Internet Protocol (IP) TCP/IP protocols are the communication guidelines used and widely supported over the Internet. n Almost every packet of information sent over the Internet uses the datagrams contained within a TCP/IP envelope. The datagrams consist of layers of information needed to verify the packet and get the information from the sender’s to the receiver’s location following traffic control guidelines. n Chapter 14 Forensic and Investigative Accounting 5

Transmission Control Protocol (TCP) and Internet Protocol (IP) Message encapsulation is used in sending the packets. In message encapsulation, each layer of information in the sent packet is interpreted by the same layer at the receiving end of the transmission. Additionally, each layer can only communicate with the one directly above or below it. Chapter 14 Forensic and Investigative Accounting 6

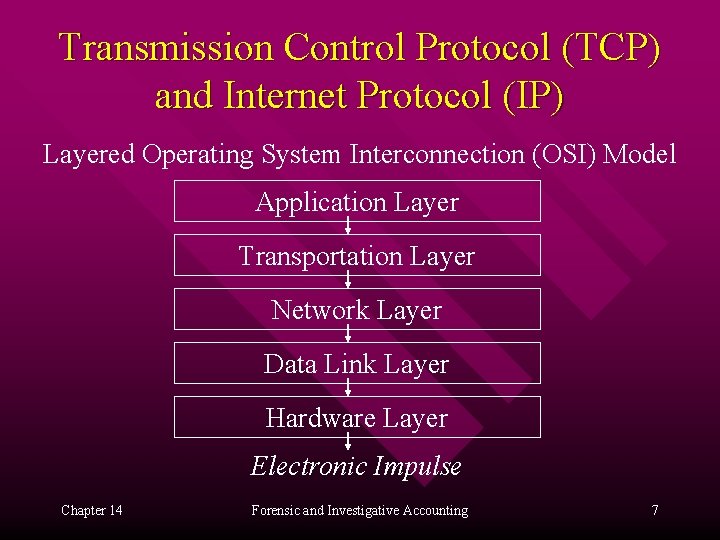
Transmission Control Protocol (TCP) and Internet Protocol (IP) Layered Operating System Interconnection (OSI) Model Application Layer Transportation Layer Network Layer Data Link Layer Hardware Layer Electronic Impulse Chapter 14 Forensic and Investigative Accounting 7

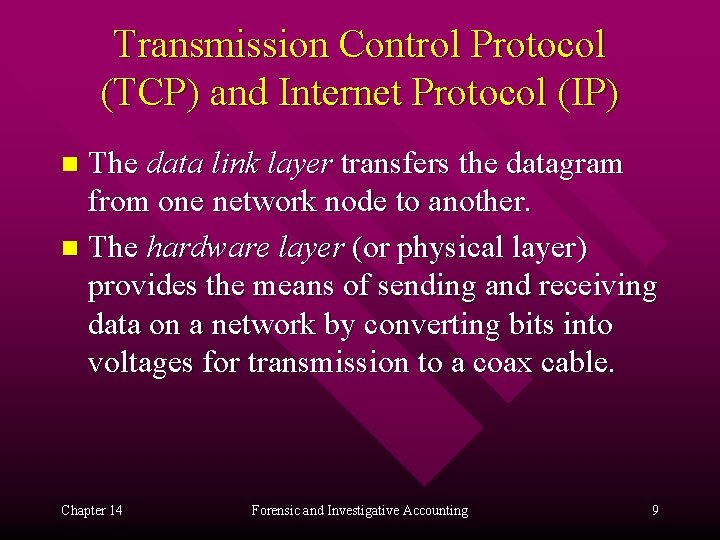
Transmission Control Protocol (TCP) and Internet Protocol (IP) The application layer issues the commands that define the operations. n The transportation layer functions to provide reliable message delivery. n The network layer controls the route the data takes to get to its destination. n (continued on next slide) Chapter 14 Forensic and Investigative Accounting 8

Transmission Control Protocol (TCP) and Internet Protocol (IP) The data link layer transfers the datagram from one network node to another. n The hardware layer (or physical layer) provides the means of sending and receiving data on a network by converting bits into voltages for transmission to a coax cable. n Chapter 14 Forensic and Investigative Accounting 9

IP Address Defined An IP address is a 32 -bit number (four bytes) that identifies the sender and recipient who is sending or receiving a packet of information over the Internet. Chapter 14 Forensic and Investigative Accounting 10

Web Log Entries One important method for finding the web trail of an attacker is in examining web logs. n Recorded network logs provide information needed to trace all website usage. n Chapter 14 Forensic and Investigative Accounting 11

Web Log Entries Information provided in a log includes the visitor’s IP address, geographical location, the actions the visitor performs on the site, browser type, time on page, and the site the visitor used before arriving. n Logs should be stored on a separate computer from the web server hosting the site so they cannot be easily altered. n Chapter 14 Forensic and Investigative Accounting 12

TCPDUMP is a form of network sniffer that can disclose most of the information contained in a TCP/IP packet. n A sniffer is a program used to secretly capture datagrams moving across a network and disclose the information contained in the datagram’s network protocols. n Chapter 14 Forensic and Investigative Accounting 13

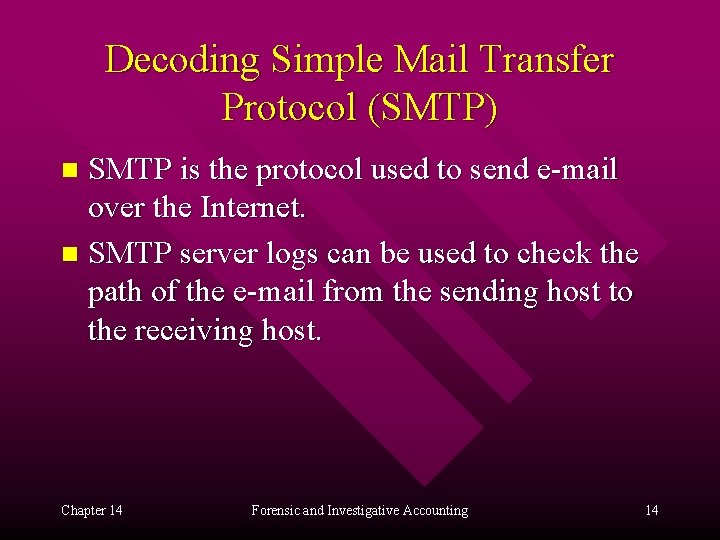
Decoding Simple Mail Transfer Protocol (SMTP) SMTP is the protocol used to send e-mail over the Internet. n SMTP server logs can be used to check the path of the e-mail from the sending host to the receiving host. n Chapter 14 Forensic and Investigative Accounting 14

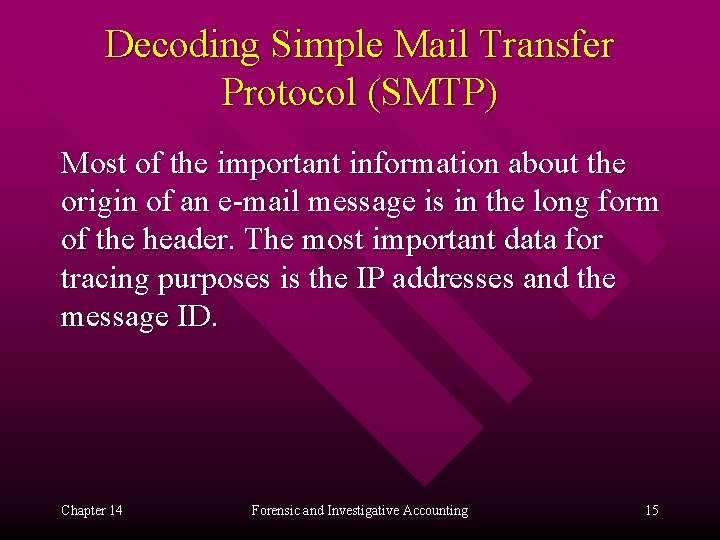
Decoding Simple Mail Transfer Protocol (SMTP) Most of the important information about the origin of an e-mail message is in the long form of the header. The most important data for tracing purposes is the IP addresses and the message ID. Chapter 14 Forensic and Investigative Accounting 15

Tracing and Decoding IP Addresses Traceroute n Whois n Ping n Finger searches n Chapter 14 Forensic and Investigative Accounting 16

Narrowing the Search Preliminary Incident Response Form n John Doe subpoena n Chapter 14 Forensic and Investigative Accounting 17

Forensic Audit n The forensic audit is an audit performed to determine whether fraud is being committed in the executive boardroom. The monitoring methods used in a forensic audit are investigative, directed at top-level executives, and do not rely on a traditional accounting audit practices. Chapter 14 Forensic and Investigative Accounting 18

Due Diligence Searches n n Internet databases – General searches – Name, telephone number, and e-mail address search engines – Internet relay chat (IRC), FTP, and Listserv searches – Usenet postings search – Legal records – Instant messaging (IM) Web page searches Government data searches Miscellaneous searches Chapter 14 Forensic and Investigative Accounting 19