Fore Scout Technologies Inc Frontline Defense against Network




- Slides: 15

Fore. Scout Technologies Inc. Frontline Defense against Network Attack Tim Riley, Forescout 1

Active. Scout Solution Active. Scout solution provides: § Preemptive identification of potential attackers § Accurate identification of potential attackers to reduce false positives to zero § Automatic action to block attackers in real time § Minimal installation and daily operational costs 2

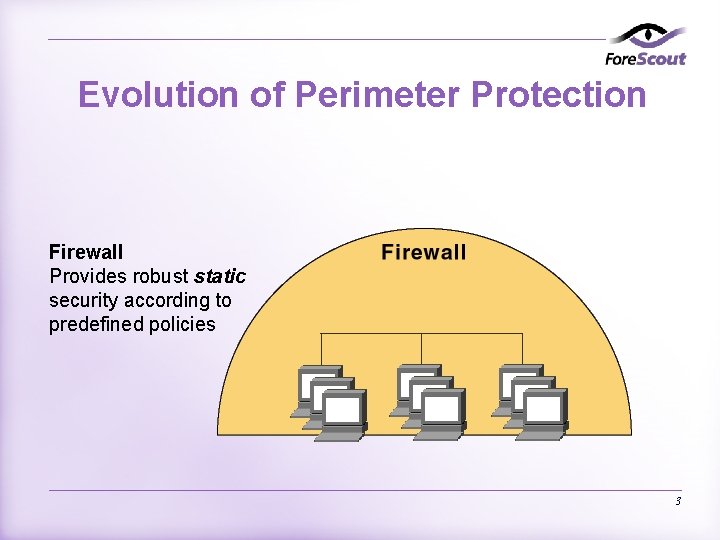
Evolution of Perimeter Protection Firewall Provides robust static security according to predefined policies 3

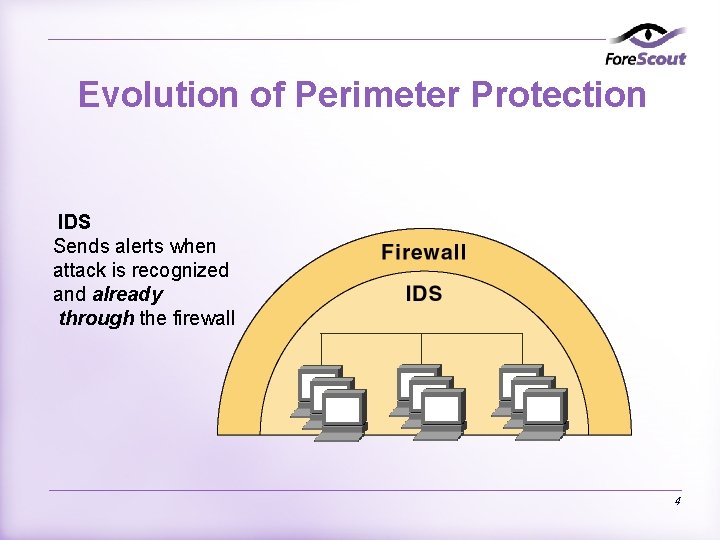
Evolution of Perimeter Protection IDS Sends alerts when attack is recognized and already through the firewall 4

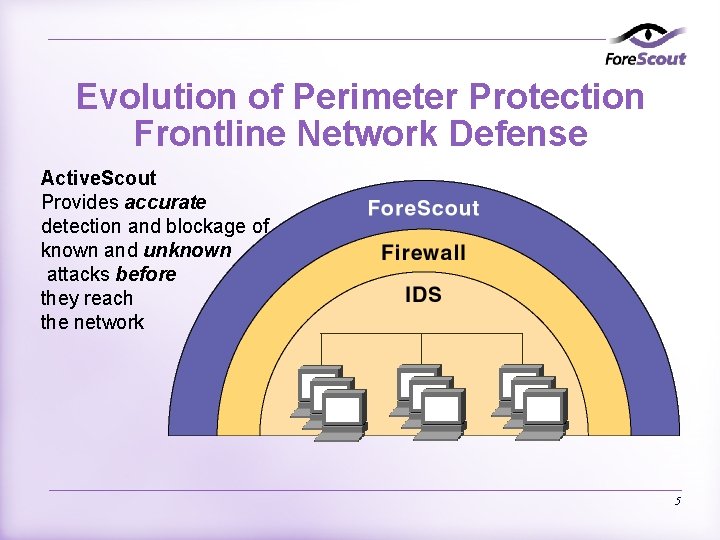
Evolution of Perimeter Protection Frontline Network Defense Active. Scout Provides accurate detection and blockage of known and unknown attacks before they reach the network 5

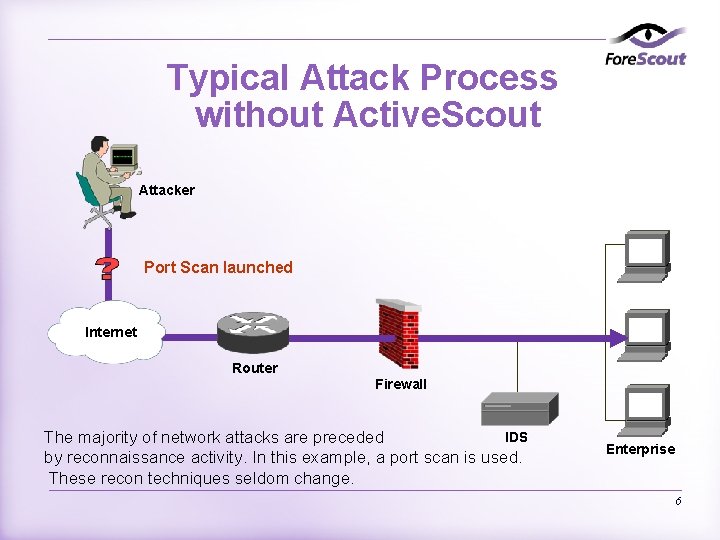
Typical Attack Process without Active. Scout Attacker Port Scan launched Internet Router Firewall IDS The majority of network attacks are preceded by reconnaissance activity. In this example, a port scan is used. These recon techniques seldom change. Enterprise 6

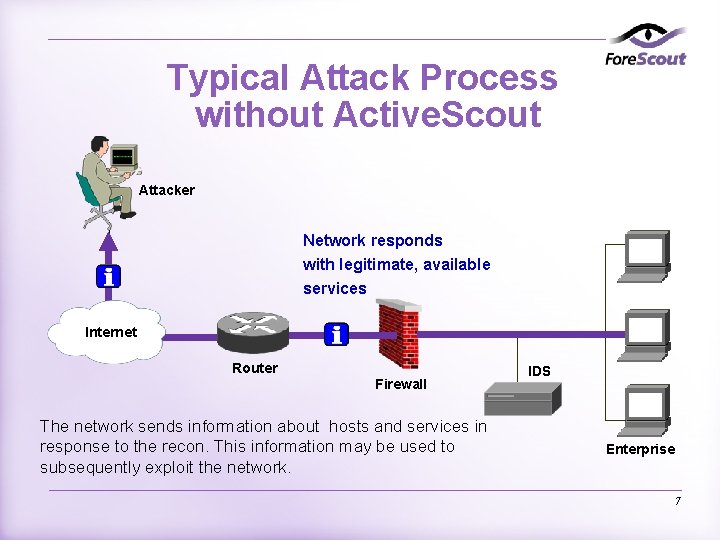
Typical Attack Process without Active. Scout Attacker Network responds with legitimate, available services Internet Router Firewall The network sends information about hosts and services in response to the recon. This information may be used to subsequently exploit the network. IDS Enterprise 7

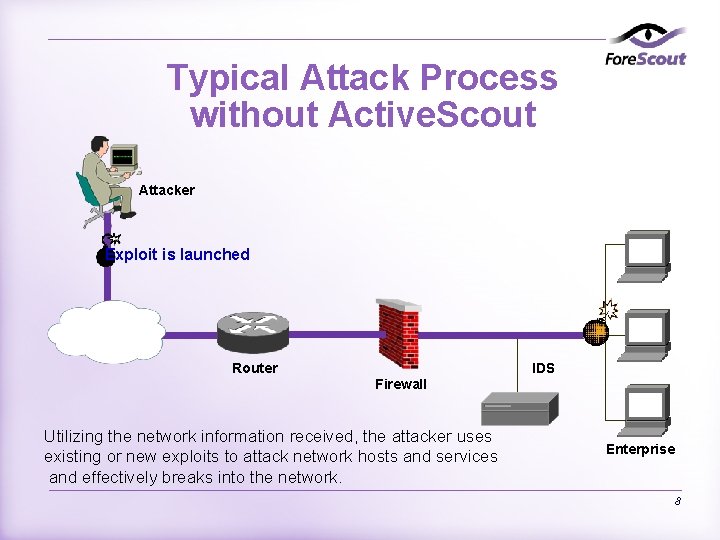
Typical Attack Process without Active. Scout Attacker Exploit is launched Internet Router IDS Firewall Utilizing the network information received, the attacker uses existing or new exploits to attack network hosts and services and effectively breaks into the network. Enterprise 8

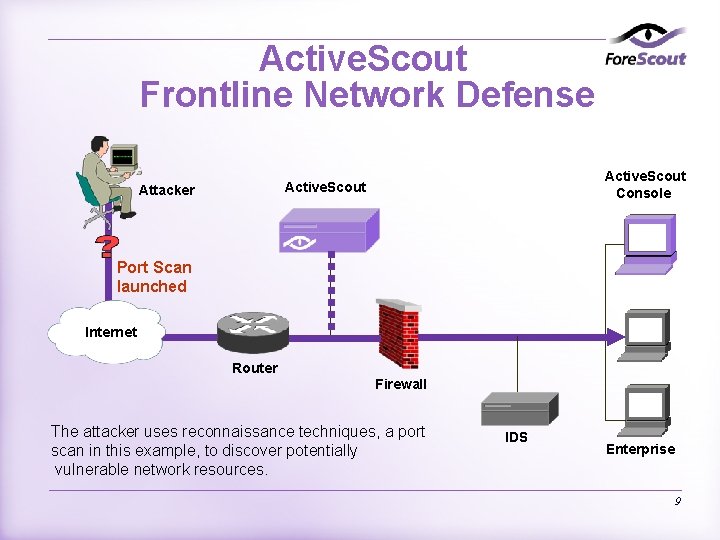
Active. Scout Frontline Network Defense Active. Scout Console Active. Scout Attacker Port Scan launched Internet Router Firewall The attacker uses reconnaissance techniques, a port scan in this example, to discover potentially vulnerable network resources. IDS Enterprise 9

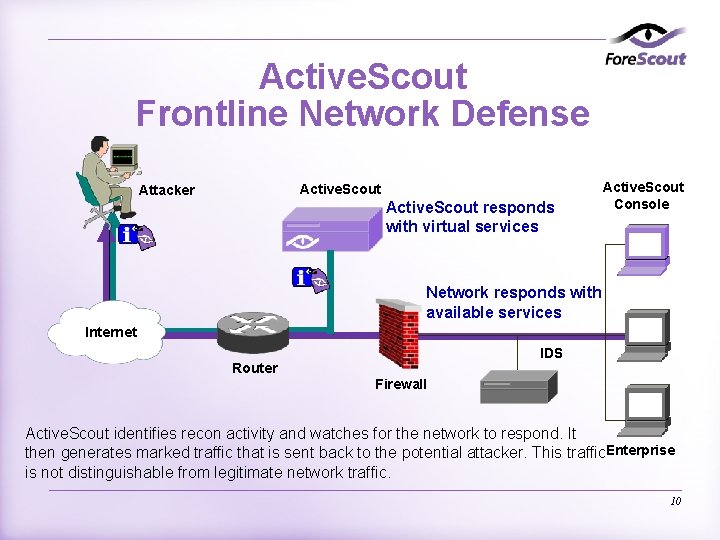
Active. Scout Frontline Network Defense Active. Scout Attacker Active. Scout responds with virtual services Active. Scout Console Network responds with available services Internet Router IDS Firewall Active. Scout identifies recon activity and watches for the network to respond. It then generates marked traffic that is sent back to the potential attacker. This traffic. Enterprise is not distinguishable from legitimate network traffic. 10

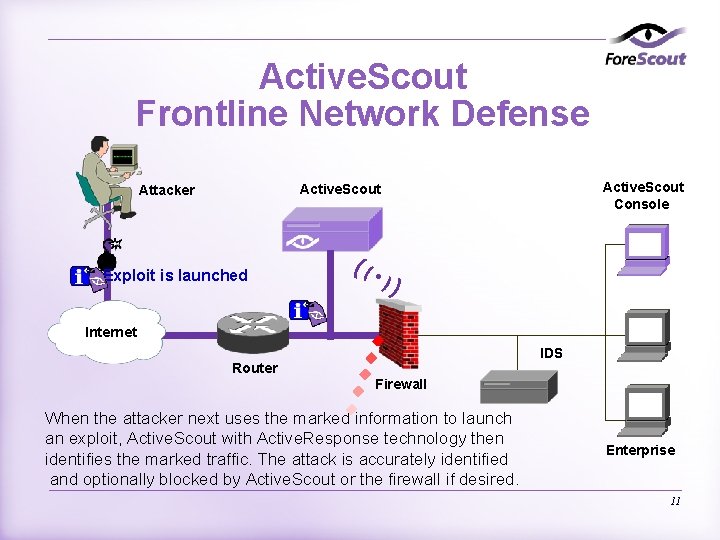
Active. Scout Frontline Network Defense Active. Scout Console Active. Scout Attacker Exploit is launched (( • )) Internet Router IDS Firewall When the attacker next uses the marked information to launch an exploit, Active. Scout with Active. Response technology then identifies the marked traffic. The attack is accurately identified and optionally blocked by Active. Scout or the firewall if desired. Enterprise 11

Active. Response Technology Patented technology that: § Identifies all reconnaissance activity § Replies to the recon attempt with an authenticlooking response, created on the fly and registered within Active. Scout § Identifies potential attacks based on this ‘marked information’ and optionally blocks them, regardless of attack method Result: Accurately identifies attackers and then prevents them from implementing new and/or existing attacks against the network. 12

Active. Scout Solution Distinguishes real attacks from the noise § Scarce security resources are focused on the real crises and do not waste time on false positives § Identifies ‘low and slow’ attacks Provides Closed Loop Perimeter Protection § After identifying an attacker Active. Scout can optionally: – Automatically block attackers – Have the firewall automatically block – Update all Active. Scouts when an attacker has been identified to provide automatic perimeter lockdown 13

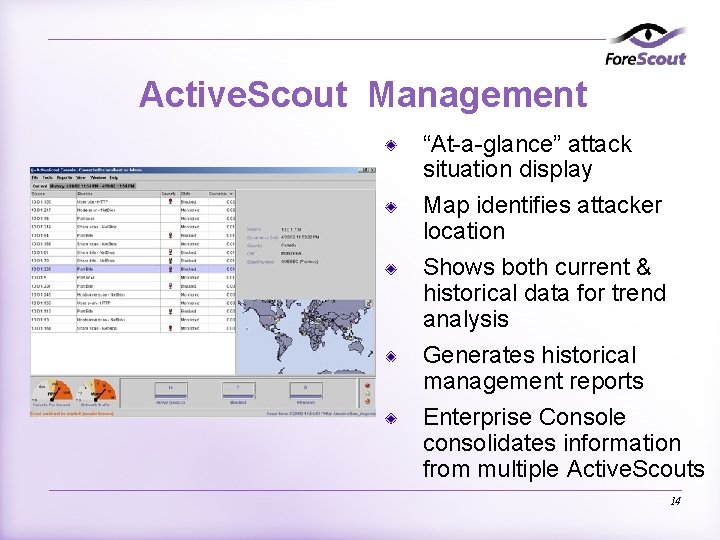
Active. Scout Management “At-a-glance” attack situation display Map identifies attacker location Shows both current & historical data for trend analysis Generates historical management reports Enterprise Console consolidates information from multiple Active. Scouts 14

Summary The Active. Scout solution utilizes patented Active. Response technology to provide Frontline Network Defense that § § Eliminates false positives Prevents Unkown attacks Reduces Op. Ex through automation Provides Enterprise wide protection 15