FOR OFFICIAL USE ONLY AMERICAS ARMY THE STRENGTH






















- Slides: 39

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Special Security Office, Army SCI SECURITY ORIENTATION TRAINING FOR OFFICIAL USE ONLY 1

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Message The protection of government assets, people and property, both classified and official but unclassified, is the responsibility of each and every member of the Department of Defense (Do. D); regardless of how it was obtained or what form it takes. Our vigilance is imperative in the protection of national security information. Everyone with SCI access to these vital resources has an obligation to protect it. FOR OFFICIAL USE ONLY 2

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Message It is your personal responsibility to know that the person you are dealing with is both properly cleared and has a Clearance need to know. Administrative action usually involving a CL background investigation = Need to Know SCI indoctrination/Duties BL Access Availability to classified VL information requiring you to work with SCI You must never reveal or discuss classified information with anyone other than those that are properly cleared and have a need to know. FOR OFFICIAL USE ONLY 3

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Summary • Why SCI Security Orientation • Foreign Intelligence Threat Awareness • Security Classification Management • Individual Duties and Responsibilities • Reporting Obligations and Requirements • Marking, Handling, and Safeguarding of Classified Information • Publication Review Requirement • Information Security • Identification of Local SCI Security Official/Security POC’s • Local Procedures FOR OFFICIAL USE ONLY 4

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Why is this required? Personnel are required by DOD 5105. 21 -V 3, Sensitive Compartmented Information (SCI) Administrative Security Manual and Intelligence Community Policy Directive 704 to be reminded annually of their Security Responsibilities regarding: - Personnel Security (PERSEC) - Physical Security (PHYSEC) - Information Security (INFOSEC) If your status has changed over the past year please contact the Special Security Office (SSO) FOR OFFICIAL USE ONLY 5

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Foreign Intelligence Threat 1. THE FOREIGN INTELLIGENCE THREAT BRIEF (FITB) addresses efforts by Foreign Intelligence Services (FIS), foreign commercial enterprises, foreign terrorists, or foreign computer intruders to acquire U. S. classified, sensitive, or proprietary information or material, and the unauthorized disclosure of such information or material to foreign sources. 2. The FITB discusses the Source and the Threat, OPSEC, Type of Information Being Targeted. Insider Threat, Volunteer Spies, Personal Security Indicators that would indicate Improper or Suspicious Activity, and the Technical/Non-HUMINT Threat. 3. Think about it! How does the FIS Agent gather information about you or your organization? Your detailed signature block on your e-mail that lists your home, work, cell phone, e-mail, and physical address; FOR OFFICIAL USE ONLY 6

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Foreign Intelligence Threat yours or family members’ personal web sites such as My Space or Facebook Pages; conversations with fellow commuters about the frustrations of the day soon to turn into discussions about where you work, what you do, family, the cost of housing, kids college, and other financial woes, cell phone conversations with clients or co-workers discussing work, setting up meetings, going over slides to correct errors; organizational websites highlighting new technology and specifications, news releases, deployment photos, social calendars, and much more is collected to be used against us. 4. How much did you disclose? What has the FIS agent gained? Who have you endangered? What damaged have you caused? When the puzzle of information is put together and the dots connected, you may have disclosed sensitive and classified information. FOR OFFICIAL USE ONLY 7

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Foreign Intelligence Threat you have placed your family, co-workers, yourself, troops overseas, and your Nation in Grave Danger! The damage you have caused is irreparable and the devastation can be seen in body bags and grave sites! 5. You can protect yourself and your organization by maintaining situational awareness, practicing OPSEC, and staying educated by using the resources available within the Intel Community. Unclassified information on the current Foreign Intelligence Threat, and other CI publications can be found on the Office of the Director National Intelligence/Office of the National Counterintelligence Executive webpage http: //www. ncix. gov/ 6. The following invaluable resources are located in the NCIX Archives, Publications, CI Issues Sections, and Threats from Foreign Entities: a. A highly recommended resource for industry that details current intel FOR OFFICIAL USE ONLY 8

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Foreign Intelligence Threat threat against corporations is the, Annual Report to Congress on Foreign Economic Collection and Industrial Espionage, 2009 -2011 http: //www. ncix. gov/publications/reports/fecie_all/Foreign_Economic_Collection_20 11. pdf b. CI Reader: An American Revolution into the New Millennium Volumes I, II, and III http: //www. ncix. gov/publications/ci_references/index. php 7. Additional information is posted on these IC and security-related sites: a. Economic Espionage http: //www. fbi. gov/hq/ci/economic. htm b. Research & Technology (RPT) Program http: //www. infragard. net/ c. State Department http: //www. state. gov/ FOR OFFICIAL USE ONLY 9

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Foreign Intelligence Threat d. Office of the Director of National Intelligence http: //www. dni. gov/index. php/newsroom/testimonies e. DSS Industrial Security Counterintelligence http: //www. dss. mil/ci/index. html 8. The key to reducing the Foreign Intelligence Threat is to practice and remember OPSEC! If you feel you have been targeted; contact your local CI official, force protection officer or law enforcement agency. National security is everybody’s business! FOR OFFICIAL USE ONLY 10

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Classification Management a. Improper use of the classification management system is prohibited b. If holders of information have substantial reason to believe that the information is improperly or unnecessarily classified, they shall communicate that belief to their security manager or the OCA to bring about any necessary correction. This may be done informally or by submitting a formal challenge to the classification in accordance with Do. DM 5200. 01 -V 1, Encl 4, para 22 a. c. Additional guidance that pertains to classified national security information can be found in Executive Order (E. O. ) 13526, E. O. 13556, Information Security Oversight Office (ISOO) and Controlled Access Program Coordination Office (CAPCO). FOR OFFICIAL USE ONLY 11

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Classification Management Original Classification - Original Classification is the initial decision to designate a certain item of information as classified. Original Classifying Authority (OCA) is granted by position: Commanding General, Deputy Chief of Staff, G-2 is an OCA Derivative Classification - The act of incorporating, paraphrasing, restating, or generating in new form information that is already classified, and marking the newly developed material consistent with the markings of the source information. Individuals will derivatively classify documents based on guidance from a source document, Security Classification Guide (SCG) or other documented guidance from your OCA. FOR OFFICIAL USE ONLY 12

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Classification Management Intelligence Sources & Methods Examples Open Source Intelligence (OSINT) Signals Intelligence (SIGINT) Imagery Intelligence (IMINT) Human Intelligence (HUMINT) Electronic Intelligence (ELINT) Measurement and Signature Intelligence (MASINT) Foreign Instrumentation Signal Intelligence (FISINT) Compartments � SI – Communications Intelligence (COMINT) � G – (GAMMA) � TK – Talent Keyhole � HCS – (HUMINT) Control System FOR OFFICIAL USE ONLY 13

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Classification Management IAW ICD 710, Para F; the classification markings allowed on classified information are TOP SECRET, and CONFIDENTIAL. No other term or phrase shall be used to identify classified information. Levels of Classification CONFIDENTIAL - Unauthorized Disclosure Could Cause Damage to National Security. SECRET – Unauthorized Disclosure Could Cause Serious Damage to National Security. TOP SECRET – Unauthorized Disclosure Could Cause Exceptionally Grave Damage to National Security. FOR OFFICIAL USE ONLY 14

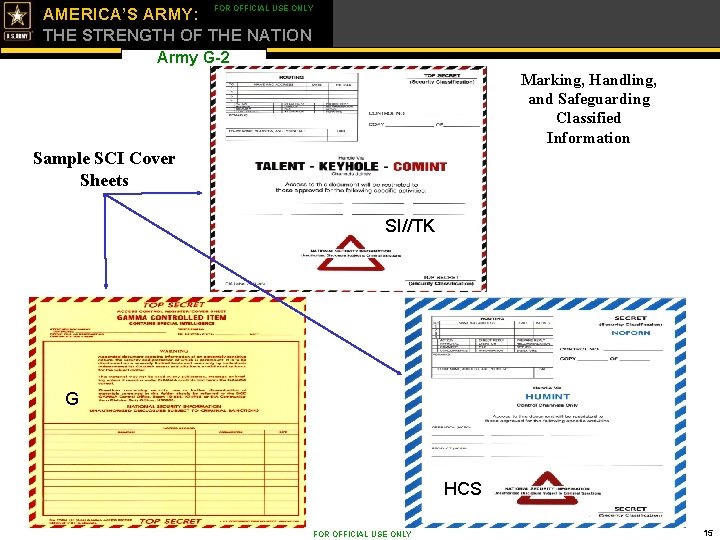
FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Marking, Handling, and Safeguarding Classified Information Sample SCI Cover Sheets SI//TK G HCS FOR OFFICIAL USE ONLY 15

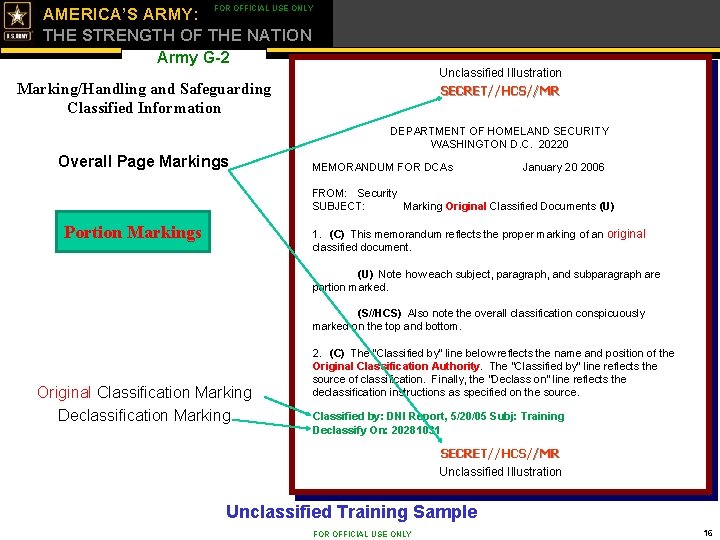
FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Unclassified Illustration Marking/Handling and Safeguarding Classified Information SECRET//HCS//MR DEPARTMENT OF HOMELAND SECURITY WASHINGTON D. C. 20220 Overall Page Markings MEMORANDUM FOR DCAs January 20 2006 FROM: Security SUBJECT: Marking Original Classified Documents (U) Portion Markings 1. (C) This memorandum reflects the proper marking of an original classified document. (U) Note how each subject, paragraph, and subparagraph are portion marked. (S//HCS) Also note the overall classification conspicuously marked on the top and bottom. Original Classification Marking Declassification Marking 2. (C) The “Classified by” line below reflects the name and position of the Original Classification Authority. The “Classified by” line reflects the source of classification. Finally, the “Declass on” line reflects the declassification instructions as specified on the source. Classified by: DNI Report, 5/20/05 Subj: Training Declassify On: 20281031 SECRET//HCS//MR Unclassified Illustration Unclassified Training Sample FOR OFFICIAL USE ONLY 16

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Unclassified Illustration Marking/Handling and Safeguarding Classified Information SECRET//HCS//MR DEPARTMENT OF HOMELAND SECURITY WASHINGTON D. C. 20220 Overall Page Markings MEMORANDUM FOR DCAs January 20 2006 FROM: Security SUBJECT: Marking Derivatively Classified Documents (U) Portion Markings 1. (C) This memorandum reflects the proper marking of a derivatively classified document. (U) Note how each subject, paragraph, and subparagraph are portion marked. (S//HCS) Also note the overall classification conspicuously marked on the top and bottom. Derivative Classification Marking Declassification Marking 2. (C) The “Derived From” line below reflects the name and position of the Derivative Classification Authority. The “Derived From” line reflects the source of classification. Finally, the “Declass on” line reflects the declassification instructions as specified on the source. Derived From: CIA Report, 5/20/05 Subj: Training Declassify On: 20281031 SECRET//HCS//MR Unclassified Illustration Unclassified Training Sample FOR OFFICIAL USE ONLY 17

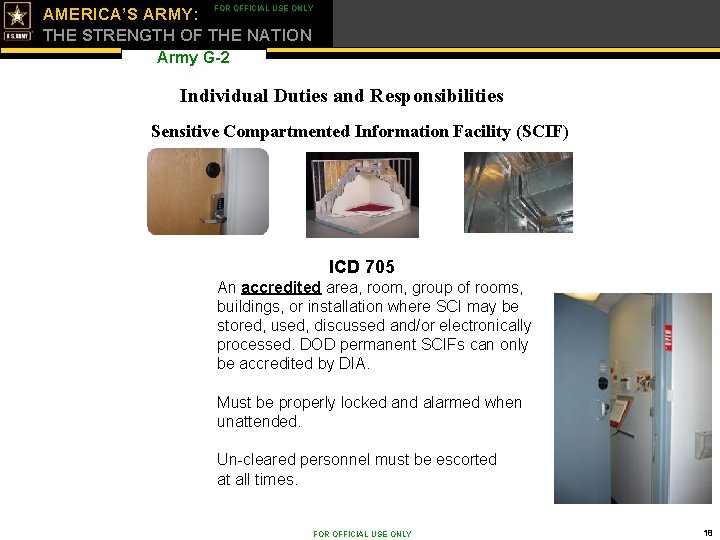
FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Individual Duties and Responsibilities Sensitive Compartmented Information Facility (SCIF) ICD 705 An accredited area, room, group of rooms, buildings, or installation where SCI may be stored, used, discussed and/or electronically processed. DOD permanent SCIFs can only be accredited by DIA. Must be properly locked and alarmed when unattended. Un-cleared personnel must be escorted at all times. FOR OFFICIAL USE ONLY 18

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Individual Duties and Responsibilities Temporary Secure Working Area (TSWA) No storage of SCI Operational less than 40 hrs/month Tactical /Temporary SCIF (T-SCIF) The perimeter shall be guarded by walking or fixed guards to provide observation of the entire controlled area. Under field or combat conditions 24/7 operations mandatory. SIOs at ACOM, ASSC, and DRU will approve T-SCIFs for a period not to exceed one year. FOR OFFICIAL USE ONLY 19

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Individual Duties and Responsibilities - SCIF PROTOCOL Contact your Local SCI security officials for: • Regulatory guidance and local standing operating procedures in the areas of personnel and physical security that will allow employees to operate in a secure SCI environment. • Information on the SCIF’s Emergency Action Plan (EAP) and emphasize the importance of the emergency destruction and removal guidelines for national security information. FOR OFFICIAL USE ONLY 20

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Reporting Obligations and Requirements • Change of name, marital status, citizenship • Foreign Contact/Travel (business and pleasure) • Close and continuing relationships with non-US citizens • Financial difficulties • Alcohol or drug abuse W IA M D Do 5. 21 u 0 51 , Yo 3 V ust t M or p Re It! • Coercion, blackmail, or recruitment attempts • Contact with Foreign Intelligence Service (FIS) • Unauthorized disclosure of media leaks • Major financial deposit (i. e. , large inheritance, lottery, gambling, etc. , over $10, 000) • Willful violation or security regulations • Adverse information, such as DUI, arrest, or conviction FOR OFFICIAL USE ONLY 21

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Risks with New Technology Mass Storage Miniaturization Imaging Technology Wireless Technology Advances THE FOLLOWING SLIDES DEPICTS DEVICES THAT ARE CAPABLE OF ELECTRONICALLY GATHERING/COPYING INFORMATION "Protecting Our Nation's Intelligence" FOR OFFICIAL USE ONLY 22

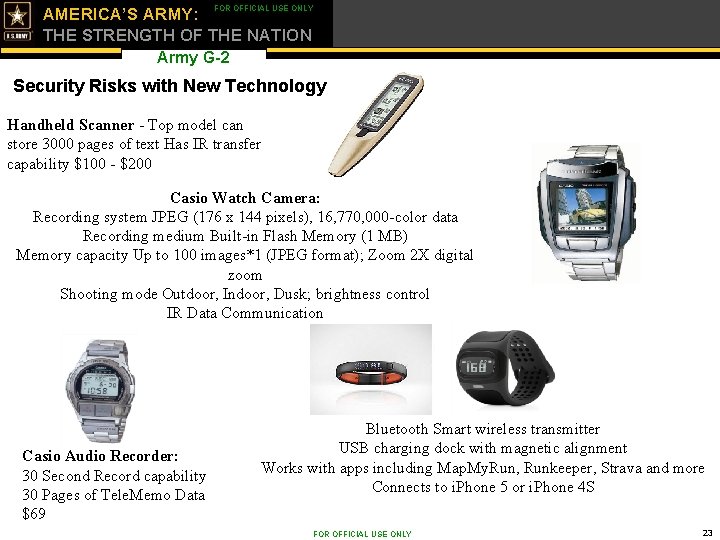
FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Risks with New Technology Handheld Scanner - Top model can store 3000 pages of text Has IR transfer capability $100 - $200 Casio Watch Camera: Recording system JPEG (176 x 144 pixels), 16, 770, 000 -color data Recording medium Built-in Flash Memory (1 MB) Memory capacity Up to 100 images*1 (JPEG format); Zoom 2 X digital zoom Shooting mode Outdoor, Indoor, Dusk; brightness control IR Data Communication Casio Audio Recorder: 30 Second Record capability 30 Pages of Tele. Memo Data $69 Bluetooth Smart wireless transmitter USB charging dock with magnetic alignment Works with apps including Map. My. Run, Runkeeper, Strava and more Connects to i. Phone 5 or i. Phone 4 S FOR OFFICIAL USE ONLY 23

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Risks with New Technology These devices can easily be carried in a SCIF, intentionally or unintentionally. UNLESS PRE-APPROVED BY SSO OR IA PERSONNEL , THEY ARE NOT-AUTHORIZED IN A SCIF! BE ALERT! FOR OFFICIAL USE ONLY 24

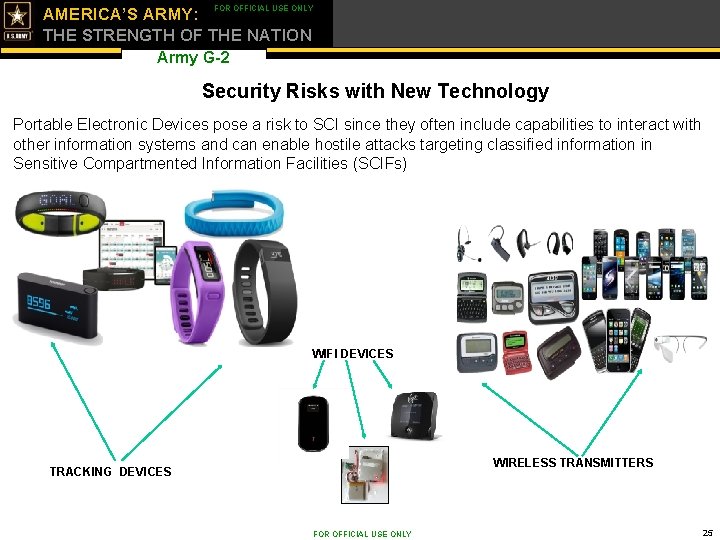
FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Risks with New Technology Portable Electronic Devices pose a risk to SCI since they often include capabilities to interact with other information systems and can enable hostile attacks targeting classified information in Sensitive Compartmented Information Facilities (SCIFs) WIFI DEVICES WIRELESS TRANSMITTERS TRACKING DEVICES FOR OFFICIAL USE ONLY 25

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Risks with New Technology The problem is real! Stolen military data for sale in Afghanistan despite crackdown, computer drives were found with names of HUMINT sources. Memory sticks (Thumb Drives) like these, on sale at the bazaar outside the U. S. military base in Bagrham, were found to contain U. S. intelligence data. FOR OFFICIAL USE ONLY 26

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Security Risks with New Technology Defensive Measures • • Educate yourself on new technology! Seek advice from your System Administrators and Information Systems Security Officers (ISSO). Be aware of possible risks and pay attention to those around you. Inquire about technical details of products you purchase. Bottom Line Don’t assume the device is authorized in the facility. Contact the security office if you have any questions. Inquire about technical details of proposed purchases BEFORE ordering items. FOR OFFICIAL USE ONLY 27

2014. Please log-in to AKO and go to Self Service, My Training, ALMS FOR OFFICIAL USE ONLY Portal, Mandatory Training, and then select "Initial Security Orientation. " Please send me a copy of your certificate of completion no later than 7 November 2014. Thank you. AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Types of Security Incidents Security Violations A security violation is a compromise of classified information to persons not authorized to receive it or a serious failure to comply with the provisions of government security regulations; which is likely to result in compromise. A security violation requires investigation. Infractions An infraction (formerly known as a “practice dangerous to security”) is a failure to comply with provisions of government security regulations or any other action that causes a potential compromise of classified information. FOR OFFICIAL USE ONLY 28

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Report Security Incidents When Classified material, facility, or equipment is left unprotected Classified information is transmitted via unclassified email systems Downloading/uploading classified information on unclassified systems Unclassified faxes or scanners are used to transmit classified information Disclosure of classified to un-cleared personnel Copied on unauthorized equipment Unauthorized methods of destruction is used Classified information improperly marked Classified information is discussed in non-secured areas FOR OFFICIAL USE ONLY 29

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Sample Security Incident A CG member properly transported SCI material to CGHQ for a presentation, however; the material was improperly processed and stored in a Secret space over night. Weakness: Failure to follow established policies and regulations. SCI can only be processed in a SCIF. FOR OFFICIAL USE ONLY 30

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Sample Security Incident A CG member printed SCI material from a JWICS terminal, then only protected it at the collateral classification level (SECRET) vice at the SCI level. Weakness Inattention to classification markings. SCI can be Top Secret, Secret or Confidential, but must be protected within SCI security controls. FOR OFFICIAL USE ONLY 31

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Sample Security Incident A CG member received a briefing packet with overall markings of Unclassified. Within the packet was a slide with classified SCI portion markings. Weakness: Failure to thoroughly check all documents before removing them from a classified space. Additionally, when the document was printed it wasn’t reviewed and marked at the highest overall level of classification. FOR OFFICIAL USE ONLY 32

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Consequences for Security Incidents/Violations Additional training / changes in procedures Counseling Fines, Leave w/o pay Removal from position Loss of access/ clearances Criminal Prosecution $10, 000, 10 years; life imprisonment; FOR OFFICIAL USE ONLY 33

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Prepublication Review Requirement Security review prior to release • All SCI related or SCI developed information • Any release outside SCI protected channels - Unclassified - Classified – collateral Examples • • • Books and manuscripts Articles and reports Presentations Resumes and performance reports Email, blogs and chat rooms Clearance statement for resume-- Cleared for Top Secret information and granted access to Sensitive Compartmented Information based on a single scope Background Investigation completed on (date) FOR OFFICIAL USE ONLY 34

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Information Security Telephone SCI discussed in a SCIF only Across secure telecommunications equipment ie. STE, STU III, or Sectara Wireline Terminal JWICS E-mail (whenever possible) Person to Person – In a SCIF Hand Carry - Authorized Courier Secure Fax Defense Courier Service (DEFCOS) SCI may Never be sent via US Postal Service FOR OFFICIAL USE ONLY 35

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Information Security I SC Packaging requirements for SCI - Double wrapped - inner wrap marked with classification - outer wrap marked only with name & address of sender and recipient P TO Carrying between SCIFs within one building or compound - Locked container may serve as outer wrap written authorization (courier card) not required SE T/ RE C er n n I et k c Pa To be opened only by: SSO Outer Packet Top Secret material and higher delivered via the Defense Courier Service (DCS). Site Reg via link. FOR OFFICIAL USE ONLY 36

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Information Security Destruction of SCI Material • Shredding • NSA APPROVED SHREDDER ONLY • Melting • Grinding • Acid-bath • Incinerating • Burn Bags FOR OFFICIAL USE ONLY 37

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 Summary Protect Your Security Clearance Keep Security Advised Release Classified Information Only To cleared person with A Need-To. Know Never Leave Classified Information Unattended Never Take Classified Information Home Be Alert To Threats And Vulnerabilities When in doubt – Contact your SSO or Security Office FOR OFFICIAL USE ONLY 38

FOR OFFICIAL USE ONLY AMERICA’S ARMY: THE STRENGTH OF THE NATION Army G-2 The very nature of our jobs dictates we lead the way in sound security practices. Anything less is simply------ UNACCEPTABLE Thank You! FOR OFFICIAL USE ONLY 39