FITSPA Module 3 Risk Management Framework Leadership Through


































- Slides: 60

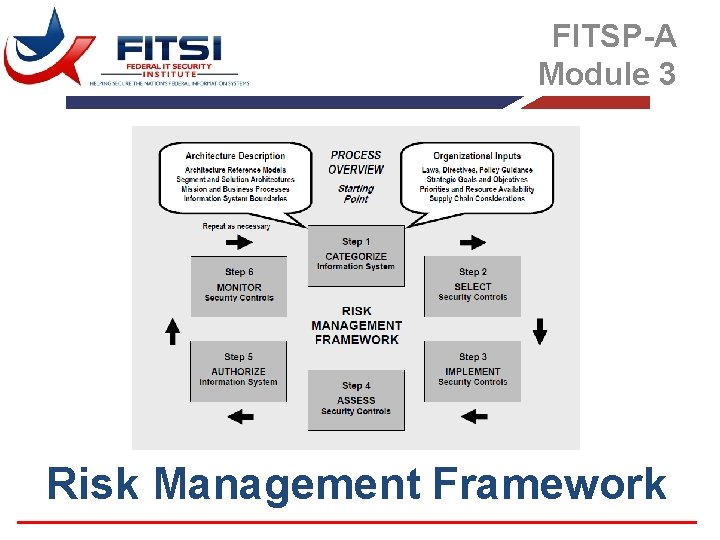
FITSP-A Module 3 Risk Management Framework


Leadership “…Through the process of risk management, leaders must consider risk to U. S. interests from adversaries using cyberspace to their advantage and from our own efforts to employ the global nature of cyberspace to achieve objectives in military, intelligence, and business operations… “ - The National Strategy For Cyberspace Operations Office Of The Chairman, Joint Chiefs Of Staff, U. S. Department Of Defense

FITSP-A Exam Module Objectives § § § Application Security Contingency Planning Data Security Planning Risk Assessment Security Assessments and Authorization

Risk Management Framework Overview § Section A: SP 800 -37 r 1 – Evolution of Risk Management – International and National Standards – Components of Risk Management § Section B: Risk Management Framework (RMF) – Characteristics of RMF – The Fundamentals of RMF § Section C: Roles & Responsibilities § Section D: Steps in the RMF Process

Section A SP 800 -37 R 1 - GUIDE FOR APPLYING THE RISK MANAGEMENT FRAMEWORK TO FEDERAL INFORMATION SYSTEMS

Evolution of Risk Management § SP 800 -37 updated Revision 1 From Guidelines for C&A of Federal Information Systems to Guide for Applying the Risk Management Framework to Federal Information Systems: A Security Life Cycle Approach § SP 800 -39 supersedes SP 800 -30 From Risk Management Guide for Information Technology Systems to Managing Information Security Risk Organization, Mission and Information System View

Risk Management Approach

Risk Management Redefined

Harmonization of International and National Standards § ISO/IEC 31000 - Risk management – Principles and guidelines § ISO/IEC 31010 - Risk management – Risk assessment techniques § ISO/IEC 27001 - Information technology – Security techniques – Information security management systems – Requirements § ISO/IEC 27005 - Information technology – Security techniques – Information security risk management systems

Section B SP 800 -37 R 1 – RISK MANAGEMENT FRAMEWORK (RMF)

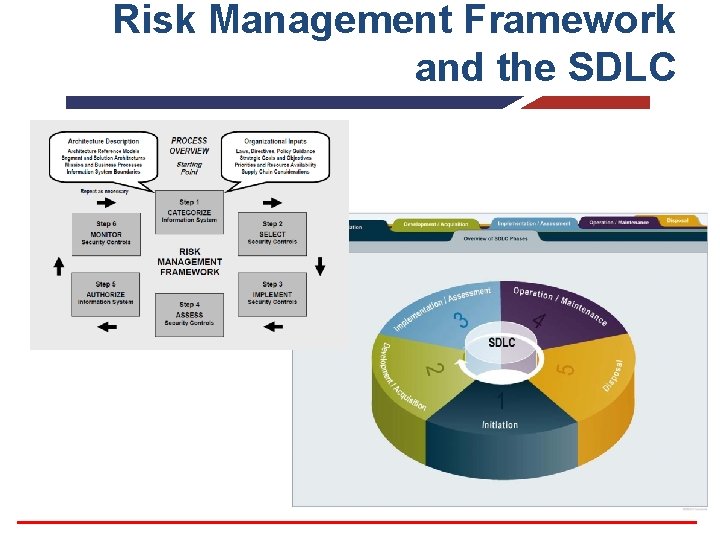
Risk Management Framework and the SDLC

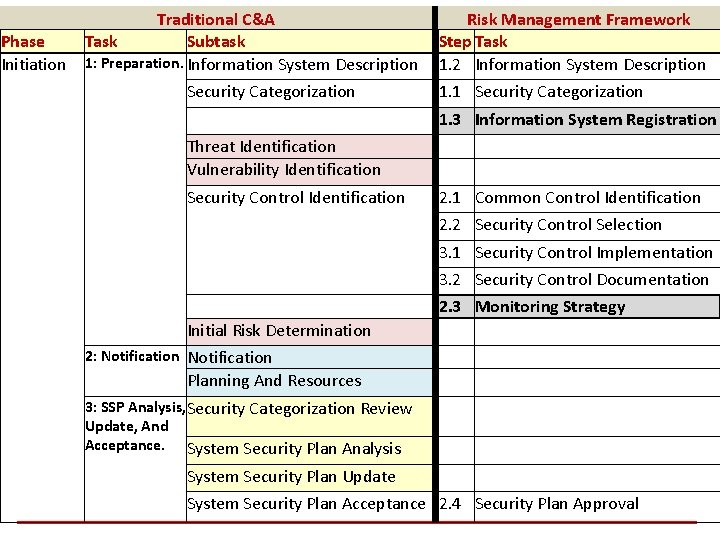
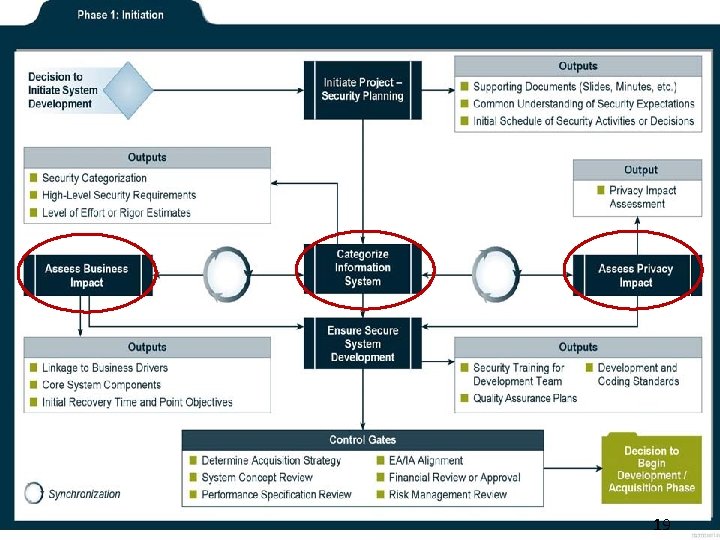
Phase Initiation Traditional C&A Risk Management Framework Task Subtask Step Task 1: Preparation. Information System Description 1. 2 Information System Description Security Categorization 1. 1 Security Categorization 1. 3 Information System Registration Threat Identification Vulnerability Identification Security Control Identification 2. 1 Common Control Identification 2. 2 Security Control Selection 3. 1 Security Control Implementation 3. 2 Security Control Documentation Initial Risk Determination 2: Notification Planning And Resources 3: SSP Analysis, Security Categorization Review Update, And Acceptance. System Security Plan Analysis System Security Plan Update 2. 3 Monitoring Strategy System Security Plan Acceptance 2. 4 Security Plan Approval

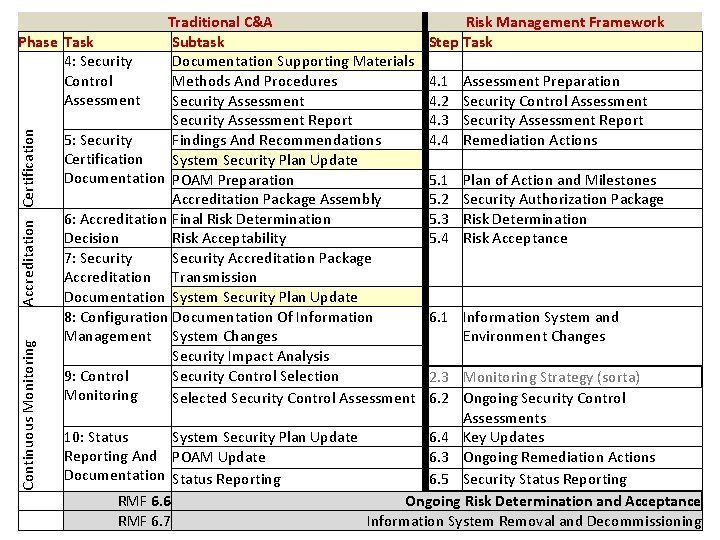
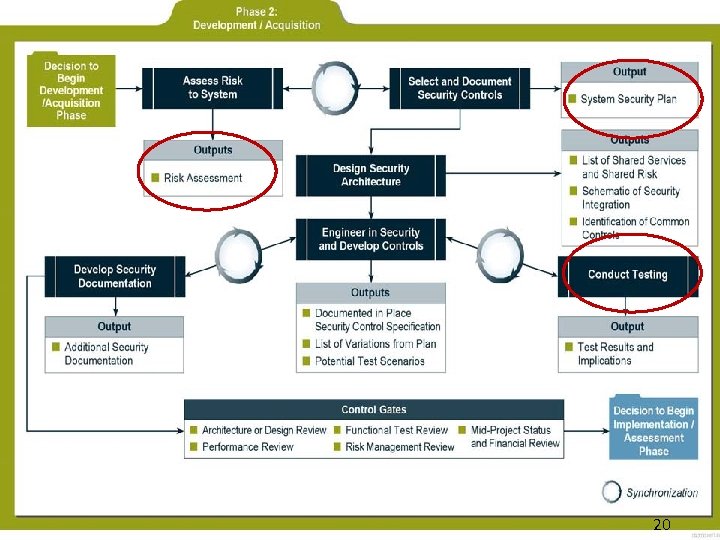
Continuous Monitoring Accreditation Certification Traditional C&A Phase Task Subtask 4: Security Documentation Supporting Materials Control Methods And Procedures Assessment Security Assessment Report 5: Security Findings And Recommendations Certification System Security Plan Update Documentation POAM Preparation Accreditation Package Assembly 6: Accreditation Final Risk Determination Decision Risk Acceptability 7: Security Accreditation Package Accreditation Transmission Documentation System Security Plan Update 8: Configuration Documentation Of Information Management System Changes Security Impact Analysis 9: Control Security Control Selection Monitoring Selected Security Control Assessment Risk Management Framework Step Task 4. 1 Assessment Preparation 4. 2 Security Control Assessment 4. 3 Security Assessment Report 4. 4 Remediation Actions 5. 1 Plan of Action and Milestones 5. 2 Security Authorization Package 5. 3 Risk Determination 5. 4 Risk Acceptance 6. 1 Information System and Environment Changes 2. 3 Monitoring Strategy (sorta) 6. 2 Ongoing Security Control Assessments 10: Status System Security Plan Update 6. 4 Key Updates Reporting And POAM Update 6. 3 Ongoing Remediation Actions Documentation Status Reporting 6. 5 Security Status Reporting RMF 6. 6 Ongoing Risk Determination and Acceptance RMF 6. 7 Information System Removal and Decommissioning

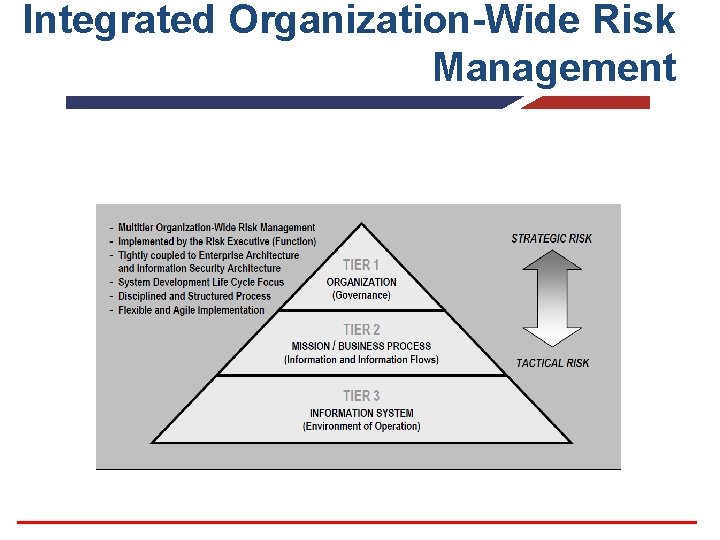
Fundamentals of RMF § § § Integrated Organization-wide Risk Management System Development Life Cycle Information System Boundaries Security Control Allocation Roles & Responsibilities

Integrated Organization-Wide Risk Management

19

20

21

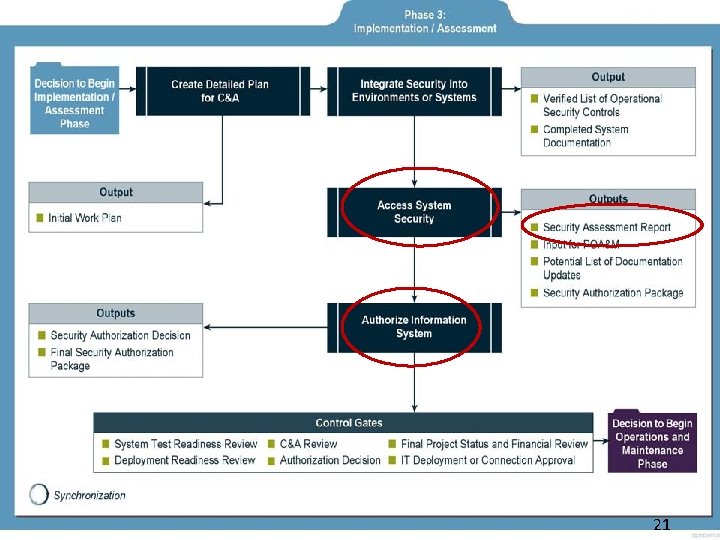
22

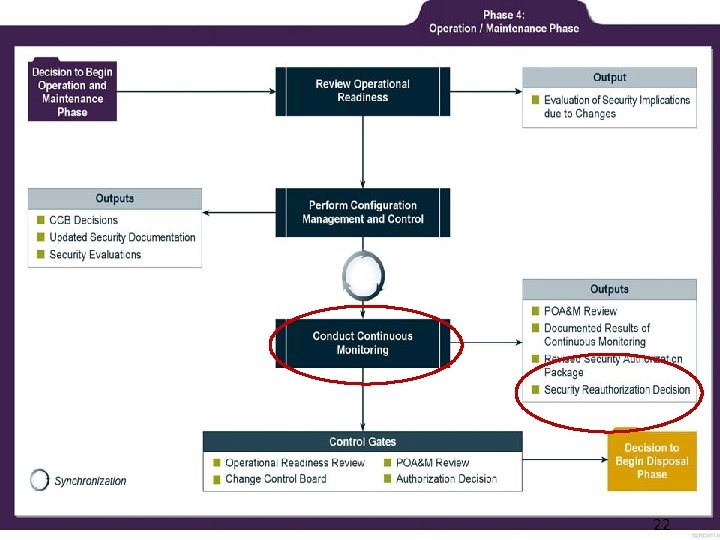
23

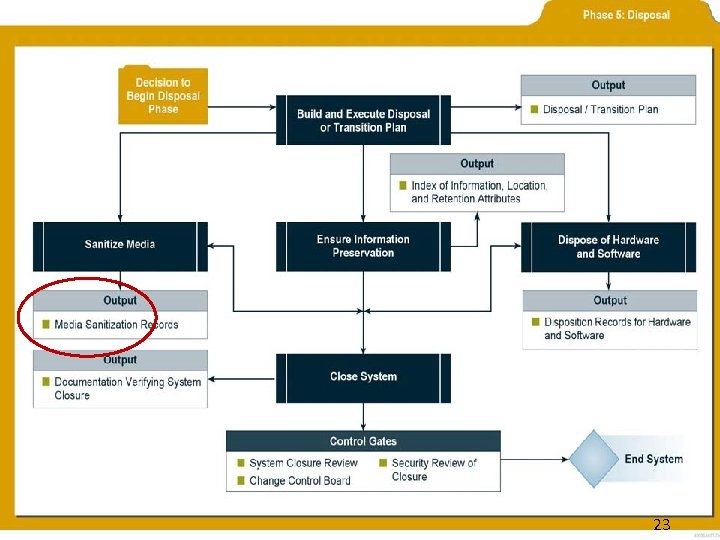
System Development Life Cycle § Phases of the SDLC – – – Initiation Development/Acquisition Implementation Operation/Maintenance Disposal § Security Requirements § Integrated Project Teams § Reusing Information

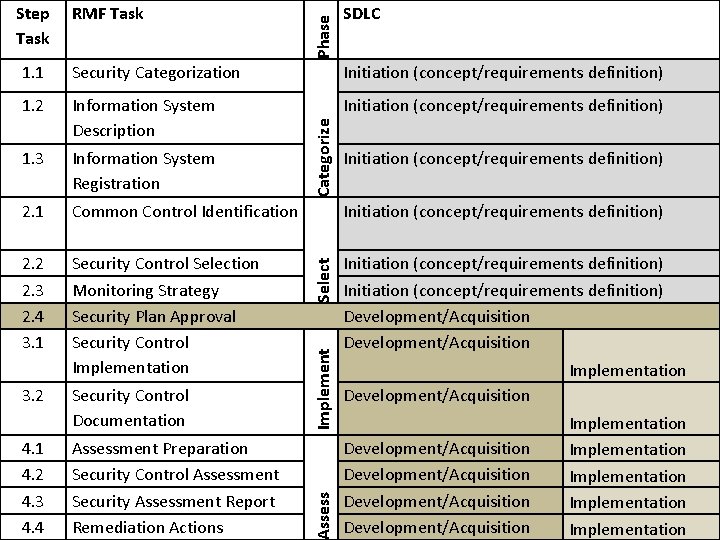
Phase Step RMF Task SDLC Security Categorization Initiation (concept/requirements definition) 1. 2 Information System Description Initiation (concept/requirements definition) 1. 3 Information System Registration 2. 1 Common Control Identification Initiation (concept/requirements definition) 2. 2 2. 3 2. 4 3. 1 Security Control Selection Monitoring Strategy Security Plan Approval Security Control Implementation Initiation (concept/requirements definition) Development/Acquisition 4. 1 4. 2 4. 3 4. 4 Assessment Preparation Security Control Assessment Security Assessment Report Remediation Actions Select Implement Security Control Documentation Assess 3. 2 Categorize 1. 1 Initiation (concept/requirements definition) Implementation Development/Acquisition Development/Acquisition Implementation Implementation

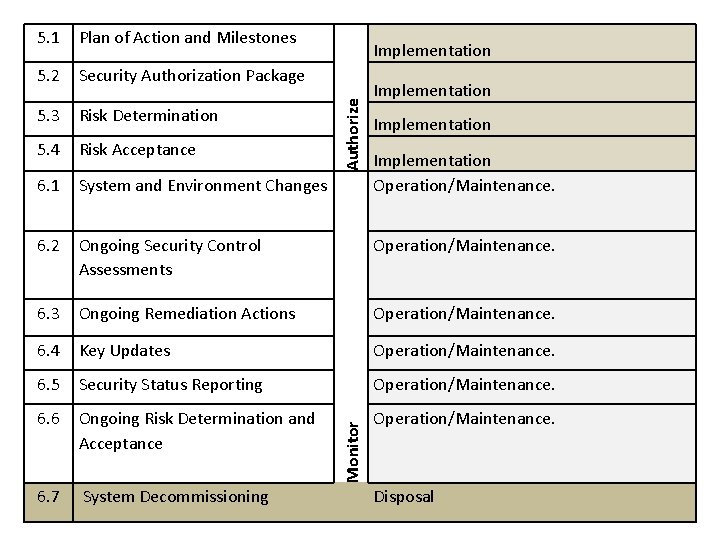
5. 1 Plan of Action and Milestones 5. 2 Security Authorization Package 5. 3 Risk Determination 5. 4 Risk Acceptance 6. 1 System and Environment Changes 6. 2 Ongoing Security Control Assessments Operation/Maintenance. 6. 3 Ongoing Remediation Actions Operation/Maintenance. 6. 4 Key Updates Operation/Maintenance. 6. 5 Security Status Reporting Operation/Maintenance. 6. 6 Ongoing Risk Determination and Acceptance Operation/Maintenance. 6. 7 System Decommissioning Monitor Authorize Implementation Operation/Maintenance. Disposal

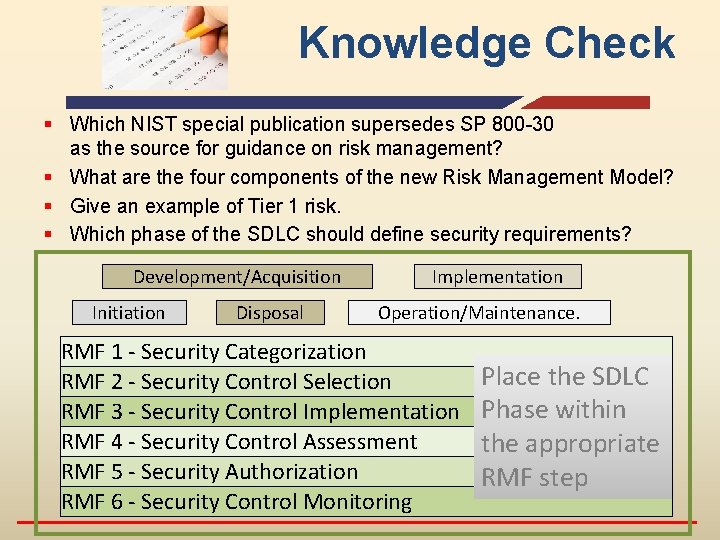
Knowledge Check § Which NIST special publication supersedes SP 800 -30 as the source for guidance on risk management? § What are the four components of the new Risk Management Model? § Give an example of Tier 1 risk. § Which phase of the SDLC should define security requirements? Development/Acquisition Initiation Disposal Implementation Operation/Maintenance. RMF 1 - Security Categorization RMF 2 - Security Control Selection RMF 3 - Security Control Implementation RMF 4 - Security Control Assessment RMF 5 - Security Authorization RMF 6 - Security Control Monitoring Place the SDLC Phase within the appropriate RMF step

Information System Boundaries § Establishing Information System Boundaries § Boundaries for Complex Information Systems § Changing Technologies and the Effect on Information System Boundaries

Effect of Changing Technologies on Information System Boundaries § Dynamic Subsystems – Net-centric – Service-oriented Architecture – Cloud Computing § External Subsystems – Contractor Systems § Trust Relationships

Fed. RAMP § Federal Risk and Authorization Management Program § Accelerate the adoption of secure cloud solutions through reuse of assessments and authorizations § Increase confidence in security of cloud solutions § Achieve consistent security authorizations using a baseline set of agreed upon standards and accredited independent third party assessment organizations § Ensure consistent application of existing security practices § Increase confidence in security assessments § Increase automation and near real-time data for continuous monitoring

Security Control Allocation Options § § System-specific Common Hybrid Inherited

Section C ROLES & RESPONSIBILITIES

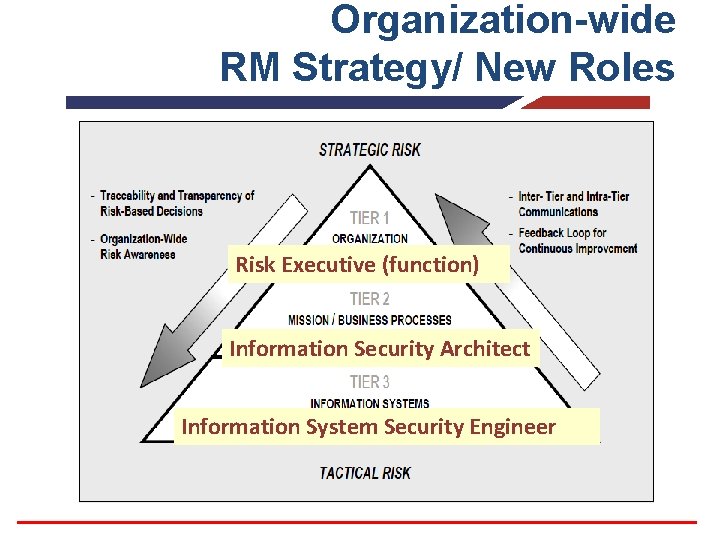
Organization-wide RM Strategy/ New Roles Risk Executive (function) Information Security Architect Information System Security Engineer

RMF Roles & Responsibilities § § § § Head Of Agency (Chief Executive Officer) Risk Executive (Function) Chief Information Officer Information Owner/Steward Senior Information Security Officer Authorizing Official Designated Representative Common Control Provider Information System Owner Information System Security Officer Information Security Architect Information System Security Engineer Security Control Assessor

Head Of Agency (Chief Executive Officer) § Highest-level Senior Official § Overall Responsibility – Information & Information Systems § Security Integrated with Strategic and Operational Processes § Sufficiently Trained Personnel § Establishes Appropriate Accountability § Provides Active Support § Oversight of Monitoring

Risk Executive (Function) § Ensures Risk-related Considerations are Organizationwide § Consistent Across Organization § Coordinates with Senior Leadership to: – – – Provide Comprehensive Approach Develop a Risk Management Strategy Facilitate Sharing of Risk Information Provides Oversight Provide Forum to Consider All Risk Sources

Chief Information Officer § § Designating Senior Information Security Officer Information Security Policies Ensuring Adequately Trained Personnel Assisting Senior Officials with Their Security Responsibilities § Appropriate Allocation of Resources § FISMA Reporting

Information Owner/Steward § § § Authority For Specified Information May or May Not Be the Same as System Owner Provide Input to Information System Owners Rules of Behavior Single System May Contain Information from Multiple Information Owners/Stewards

Senior Information Security Officer § § Carries Out the CIO FISMA Responsibilities Primary Liaison for CIO to Organization’s Senior Officials Possesses Professional Qualifications Heads Office that Conducts FISMA Reporting

Authorizing Official § § § Formally Assumes Responsibility Budgetary Oversight Accountable for Security Risks Senior Management Position Approve Security Plans and Plan of Actions and Milestones (POAMs) § Information System May Involve Multiple Authorizing Officials § Authorizing Official Designated Representative

Common Control Provider § § Documenting Common Controls Validating Required Control Assessments Documenting Assessment Findings in SAR Producing POAMs

Information System Owner § § § Program Manager Focal Point for Information System (IS) Responsible for IS throughout the SDLC Addressing the Operational Interests of User Community Ensuring Compliance with Information Security Requirements § SSP Development and Maintenance § Deciding Who Has Access to System § Works with Assessor to Remediate Deficiencies

Information System Security Officer § Ensures Appropriate Security Posture § Principal Advisor § Day-to-Day Security Operations – – – Environmental Physical Personnel Incident Handling Training and Awareness § Policies and Procedures § Active System Monitoring

Information Security Architect § Ensures Security Requirements Are Adequately Addressed In Enterprise Architecture – Reference Models – Segment And Solution Architectures – Resulting Information Systems § Liaison Between The Enterprise Architect And Information System Security Engineer § Advisor to Senior Officials – – – System Boundaries Assessing Severity of Deficiencies POAMs Risk Mitigation Approaches Security Alerts

Information System Security Engineering: A process that captures and refines information security requirements and ensures that the requirements are effectively integrated into information technology component products and information systems through purposeful security architecting, design, development, and configuration. § Part of the Development Team § Employ Security Control Best Practices § Coordinate Security-related Activities

Security Control Assessor § § § Conduct SSP Assessments Conduct Control Assessments Provide Assessment of Deficiencies Recommend Corrective Action Prepare SAR (Security Assessment Report) § Assessor Independence – Unbiased Assessment Process – Objective Information for Risk Determination

Knowledge Check § What establishes the scope of protection for organizational information systems? § What program uses a “do once, use many times” framework that will save cost, time, and staff required to conduct redundant agency security assessments? § Security Controls are allocated into what three categories? § Which RMF role helps to ensure that risk-related considerations for individual information systems are viewed from an organization-wide perspective? § Which RMF role is responsible for ensuring that the information security requirements necessary to protect the organization’s core missions and business processes are adequately addressed in all aspects of enterprise architecture?

Section D STEPS IN THE RMF PROCESS

The Risk Management Process § Well-defined, Risk-related Tasks – Sequential – Iterative § § Clearly Defined Roles Tight Integration with SDLC Milestone Checkpoints Level of Effort – Importance/Criticality of a System – Categorization, The First Step…

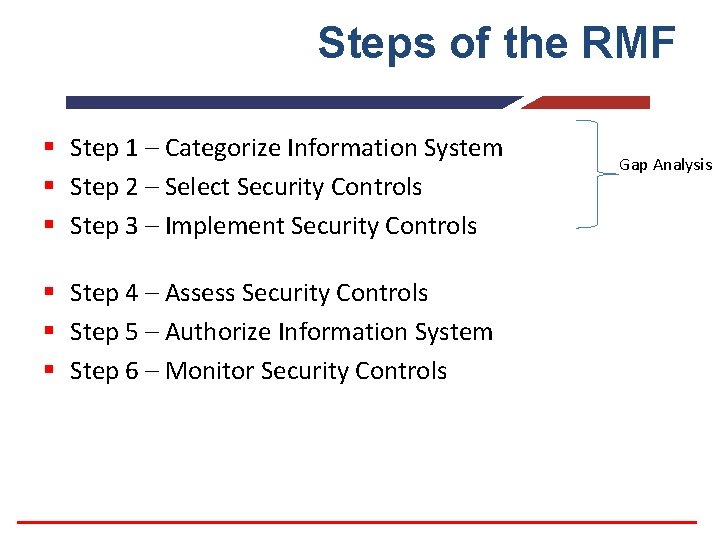
Steps of the RMF § Step 1 – Categorize Information System § Step 2 – Select Security Controls § Step 3 – Implement Security Controls § Step 4 – Assess Security Controls § Step 5 – Authorize Information System § Step 6 – Monitor Security Controls Gap Analysis

Step 1 – Categorize Information System § Security Categorization § Information System Description § Information System Registration

Step 2 – Select Security Controls § § Common Control Identification Security Control Selection Monitoring Strategy Security Plan Approval

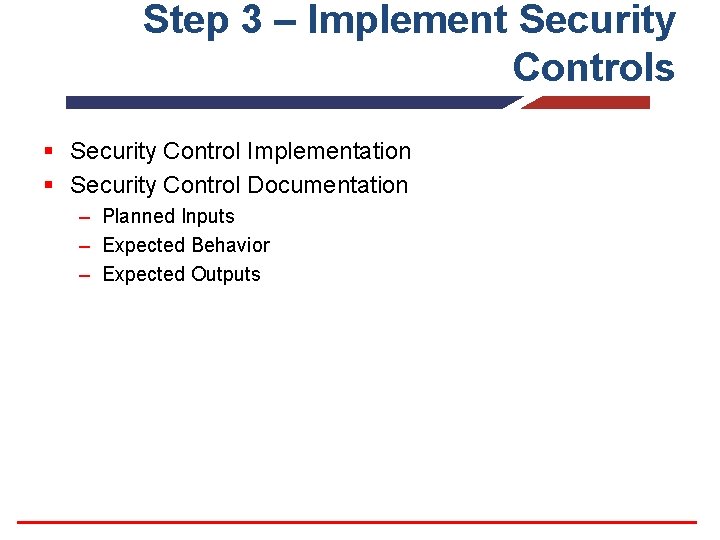
Step 3 – Implement Security Controls § Security Control Implementation § Security Control Documentation – Planned Inputs – Expected Behavior – Expected Outputs

Step 4 – Assess Security Controls § § Assessment Preparation Security Control Assessment Security Assessment Report Remediation Actions

Step 5 – Authorize Information System § § Plan Of Action And Milestones Security Authorization Package Risk Determination Risk Acceptance

Step 6 – Monitor Security Controls § § § § Information System And Environment Changes Ongoing Security Control Assessments Ongoing Remediation Actions Key Updates Security Status Reporting Ongoing Risk Determination And Acceptance Information System Removal And Decommissioning

Risk Management Framework Key Concepts & Vocabulary § Section A: SP 800 -37 r 1 – – Evolution of Risk Management Harmonization of International and National Standards Components of Risk Management Multi-tiered Risk Management § Section B: Risk Management Framework (RMF) – Characteristics of RMF – The Fundamentals of RMF – Steps in the RMF Process





Questions? Next Module: Gap Analysis