First step into Trace Analysis What is Trace







- Slides: 17

First step into Trace Analysis

What is Trace n Measurement data from real world networks n n n Wired networks: netflow traces Wireless networks: Association trace, encouter trace…… More general traces which represent other types of networks: GPS trace (Cabspoting)

Different types of Traces n Encounter traces n n The Intel/Cambridge Haggle/Pocket Switch Network project The U of Toronto PDA-based encounter experiments Your own encounter trace Cellphone traces n MIT Reality Mining: encounter, location of users (by cellphone tower/bluetooth), call log

Different types of Traces n WLAN traces n n UF traces, USC traces, Dartmouth Vehicular traces n Cabspotting

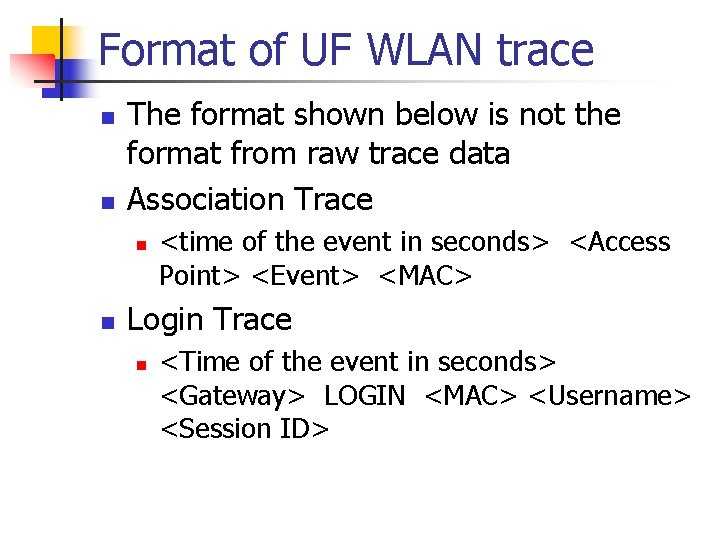
Format of UF WLAN trace n n The format shown below is not the format from raw trace data Association Trace n n <time of the event in seconds> <Access Point> <Event> <MAC> Login Trace n <Time of the event in seconds> <Gateway> LOGIN <MAC> <Username> <Session ID>

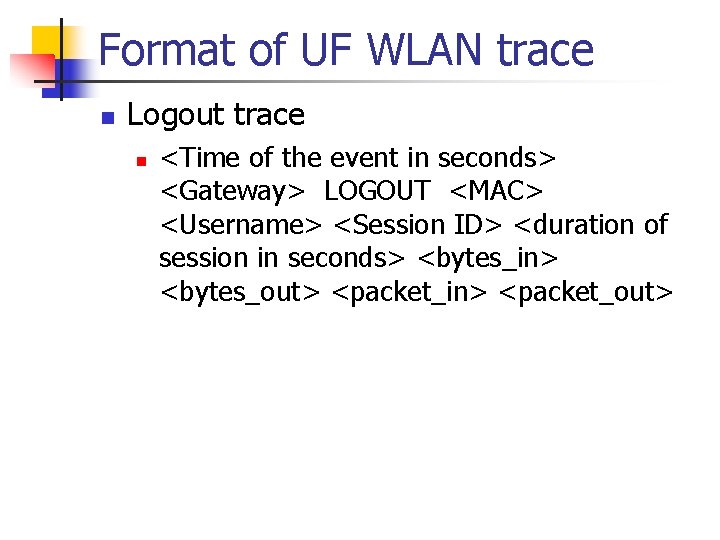
Format of UF WLAN trace n Logout trace n <Time of the event in seconds> <Gateway> LOGOUT <MAC> <Username> <Session ID> <duration of session in seconds> <bytes_in> <bytes_out> <packet_in> <packet_out>

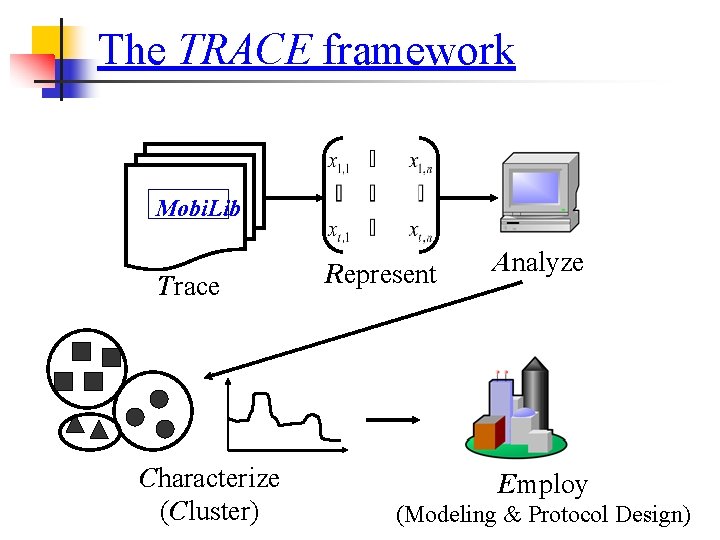
The TRACE framework Mobi. Lib Trace Characterize (Cluster) Represent Analyze Employ (Modeling & Protocol Design)

Analyze the trace n n n You should have your own perspective about what to investigate Make sure that the trace itself or together with some other possible resource can provide enough information you need Decide a scheme to parse the trace or decide what kind of tools(database…) to use to get the information out of trace in your desired format (representation)

Analyze the trace n n Now, its time to sit down and extract useful information from the trace! Then, you already convert the trace into a special representation or format. Try to identify a way to analyze it, many possibilities

Example n Study the daily user flow relationship among locations n n n From the association trace, we can build a network among all the building around campus If there is a user which first associates with one AP in Building A and then go to Building B and make another association, we draw an edge between A and B The weight of the edge donates the number of users transition from A to B in a day

Cont n Representation n n Matrix with (a, b) donates the outflux from A to B Then process the trace and populate the entries of the matrix, in the same run you may also want to get some other details (lags, sequence…. )

Cont n n Get your results Analyze it with any software, algorithm you want



Access Points Syslogs n Users are reported by MAC addresses n n When they associate with a AP When they disaccosiate from a AP When they roam away from a AP When some other event happens (error in packet checksum, max retry for a packet reached, etc. )

Authentication server syslogs n The authentication server reports the following events n n DHCP lease – IP xxx is given to MAC yyy User log in – User Gatorlink-ID logs in from MAC yyy User log out – User Gatorlink-ID logs out, and it has been online for time ttt, sent/received bbb bytes Every 30 minutes, each online user is reported for its traffic usage in the past 30 mins

Tricks of Trace Processing n Identify a common format that you can convert multiple traces into n n I use one file for each user, within each file, each line represents “time location duration” Abuse your hard drive n Keep intermediate results if they take long time to generate. . You will thank your former self years after you generated those files