Firewall Technologies nfhuangcs nthu edu tw Firewall 1





- Slides: 107

Firewall Technologies 黃能富 教授 國立清華大學資訊 程系 nfhuang@cs. nthu. edu. tw Firewall. 1

Contents n Firewall Introduction n Firewall Hardware Types n Firewall Technologies n Firewall Architecture n Firewall Deployment n VPN (Virtual Private Network) n Firewall Labs : Iptables Firewall. 2

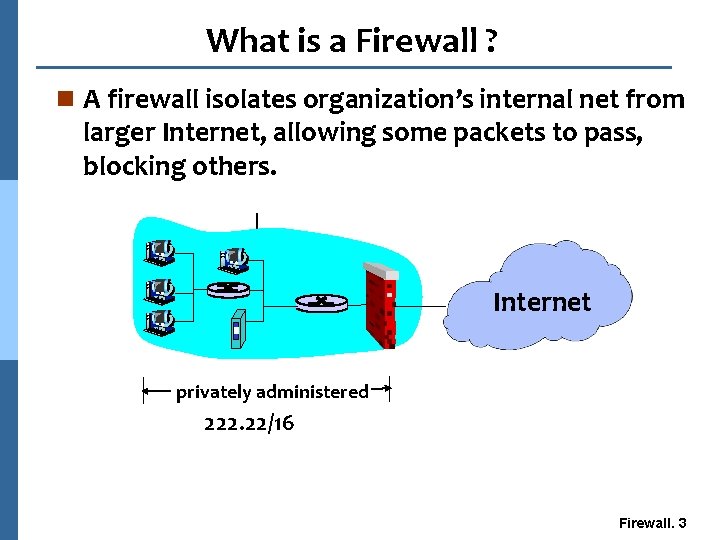
What is a Firewall ? n A firewall isolates organization’s internal net from larger Internet, allowing some packets to pass, blocking others. Internet privately administered 222. 22/16 Firewall. 3

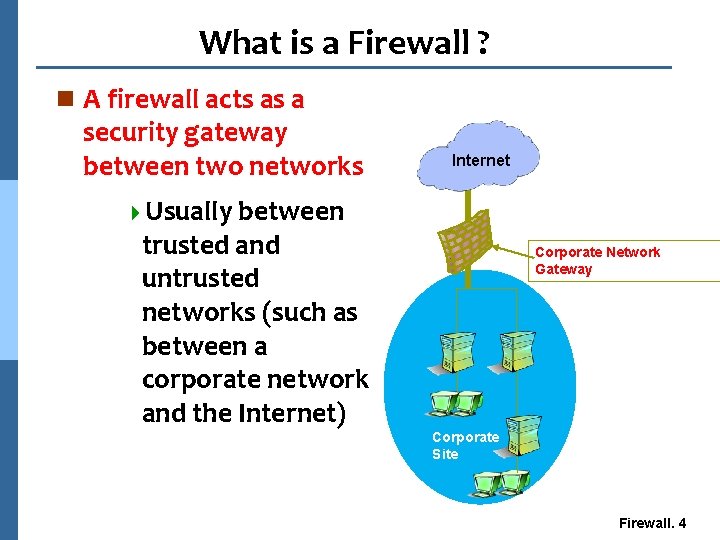
What is a Firewall ? n A firewall acts as a security gateway between two networks Internet 4 Usually between trusted and untrusted networks (such as between a corporate network and the Internet) Corporate Network Gateway Corporate Site Firewall. 4

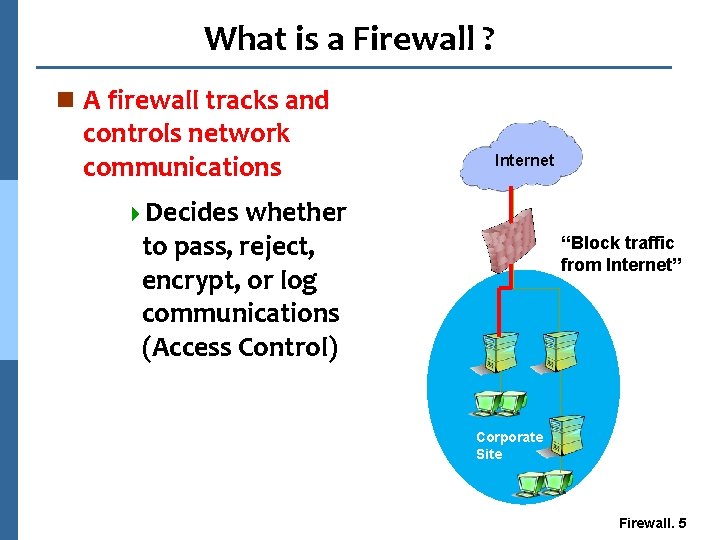
What is a Firewall ? n A firewall tracks and controls network communications Internet 4 Decides whether to pass, reject, encrypt, or log communications (Access Control) “Allow traffic Traffic “Block to Internet” from Internet” Corporate Site Firewall. 5

What is a Firewall? n A firewall is a security policy enforcement point that regulates access between computer networks n Filters are inherently insecure services n Controls TCP protocols l http, smtp, ftp, telnet etc n Only one of many different security tool’s to control and regulate network traffic Firewall. 6

Why Firewalls are Needed n Prevent attacks from untrusted networks n Protect data integrity of critical information n Preserve customer and partner confidence Firewall. 7

Firewall goals: n All traffic from outside to inside and vice-versa passes through the firewall. n Only authorized traffic, as defined by local security policy, will be allowed to pass. n The firewall itself is immune to penetration. Firewall. 8

What do Firewalls Protect? n Data l Proprietary corporate information Financial information l Sensitive employee or customer data l n Resources Computing resources l Time resources l Bandwidth resources l n Reputation Loss of confidence in an organization l Intruder uses an organization’s network to attack other sites l Firewall. 9

Common Internet Threats n Denial of service attacks Specific attacks that can cause a server crash l Flooding the server with traffic to disrupt or deny service l n Intrusion threats n Attacks on services/exploits l The backend server may not be hardened enough for adequate protection, but the firewall can block external attacks n Information threats Firewall. 10

How Vulnerable are Internet Services? n E-mail or smtp – Simple Mail Transfer Protocol TCP/IP based port 25 (POP 110) l Risks Include l 4 E-mail bombing (stalking) – – Anonymous harassment Large amounts of e-mail to a single user address 4 Spamming – Messages sent to numerous different users from a host 4 Virus download mechanism – – Code Red Nimda 4 Not always traceable l POP and IMAP can be very insecure Firewall. 11

How Vulnerable are Internet Services? n FTP - File Transfer Protocol l TCP/IP based port 20/21 l Risks Include 4 Unencrypted authentication and data transfers – Usernames and passwords can be”sniffed” 4 Unencrypted data transfers – Data can be viewed 4 Often part of default installations 4 Anonymous ftp is possible Firewall. 12

How Vulnerable are Internet Services? n Telnet l TCP/IP based port 23 l Risks include 4 Unencrypted authentication 4 Unencrypted interactive session 4 Session hijacking 4 Included in default installations 4 Can allow remote root login Firewall. 13

How Vulnerable are Internet Services? n HTTP – Hypertext Transfer Protocol TCP/IP based port 80 l Risks Include 4 Browsers can be used to run dangerous commands 4 Difficult to secure 4 Remote execution of commands and execution (server side) 4 Non-secure add-on applications l – – Java Cookies Firewall. 14

How Vulnerable are Internet Services? n HTTPS – Secure Hypertext Transfer Protocol l TCP/IP based port 443 l Risks Include 4 Browsers can be used to run dangerous commands 4 Remote execution of commands and execution (server side) 4 Becomes a tunnel for any data 4 Can be used to subvert firewall/security controls Firewall. 15

How Vulnerable are Internet Services? n DNS l TCP and UDP based ports 53 and 1024 l Risks include 4 DNS cache poisoning – Bad data to redirect valid connections to the wrong server 4 DNS spoofing – Bad data to redirect valid connections to the wrong server 4 Absolutely needed for network services Firewall. 16

How Vulnerable are Internet Services? n SNMP – Simple Network Management Protocol l UDP based l Risks include 4 Unencrypted data transfers 4 Poor authentication through “community relationships” 4 Transfer of highly sensitive data 4 Does use access lists Firewall. 17

How Vulnerable are Internet Services? n NFS – Network File System l NFS is a shared file structure l Based on a trust model of network machines 4 Certain machines can access shared file systems l Risks include 4 No “user” authentication 4 IP Spoofing to gain access 4 Most secure NFS is still very insecure Firewall. 18

Contents n Firewall Introduction n Firewall Hardware Types n Firewall Technologies n Firewall Architecture n Firewall Deployment n VPN (Virtual Private Network) n Firewall Labs : Iptables Firewall. 19

Firewall Hardware Types n Three basic hardware types l Appliance based systems 4 Purpose built 4 Simple 4 Highly integrated l 3 rd Party servers 4 General use systems 4 Additional support channel 4 Greater flexibility l Hybrid servers 4 Purpose built for a limited product line 4 Often closely integrated with software offerings 4 May have separate support channel 4 Most have highly integrated components Firewall. 20

Firewall Hardware Types n Appliance based system problems OS and Kernel hardening and security may be done by vendor only l Tightly coupled software and hardware may have insecure code unknown to user l 4 Hard to inspect or verify All security controls are determined through a single vendor l Appliances are used to simplify implementation and support efforts causing some loss of administrative control l Firewall. 21

Firewall Hardware Types n 3 rd Party server problems l OS and Kernel hardening and security must be done by implementation staff 4 Expertise 4 procedures l OS software may have many known vulnerabilities/ security holes 4 Each must be plugged All security controls are determined through corporate policy l 3 rd party systems require a larger degree of administration and procedure l Firewall. 22

Firewall Hardware Types n Hybrid servers l OS and Kernel hardening is started by vendor and completed by end user security staff—can help to make it more robust l Packaged software and hardware generally reviewed for security All security controls are determined through a more partnered structure l Hybrid servers are also used to simplify implementation and support efforts without giving away administrative control l Firewall. 23

Contents n Firewall Introduction n Firewall Hardware Types n Firewall Technologies n Firewall Architecture n Firewall Deployment n VPN (Virtual Private Network) n Firewall Labs : Iptables Firewall. 24

Firewalls Technologies n Traditional packet filters l filters often combined with router, creating a firewall l widely available in routers, linux n Application gateways n often implemented with SOCKS today n Stateful Inspection filters l maintains connection state Firewall. 25

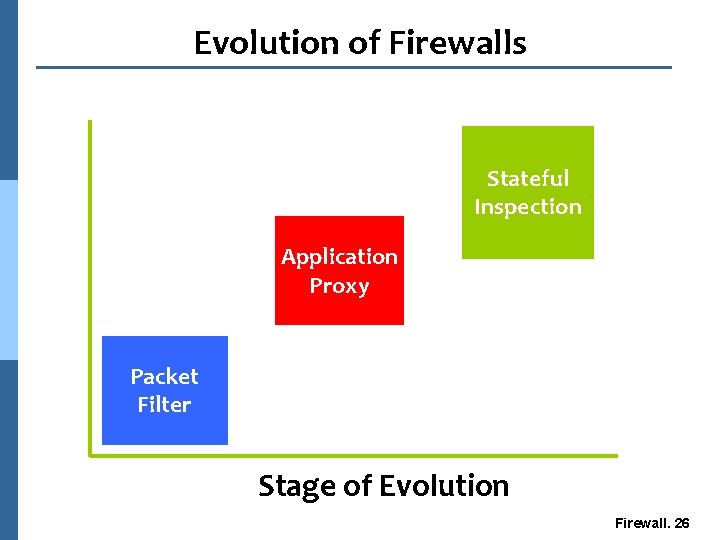
Evolution of Firewalls Stateful Inspection Application Proxy Packet Filter Stage of Evolution Firewall. 26

Traditional packet filters Analyzes each datagram going through it; makes drop decision based on: n source IP address n destination IP address n source port n destination port n TCP flag bits SYN bit set: datagram for connection initiation l ACK bit set: part of established connection l n TCP or UDP or ICMP l Firewalls often configured to block all UDP n direction l Is the datagram leaving or entering the internal network? n router interface l decisions can be different for different interfaces Firewall. 27

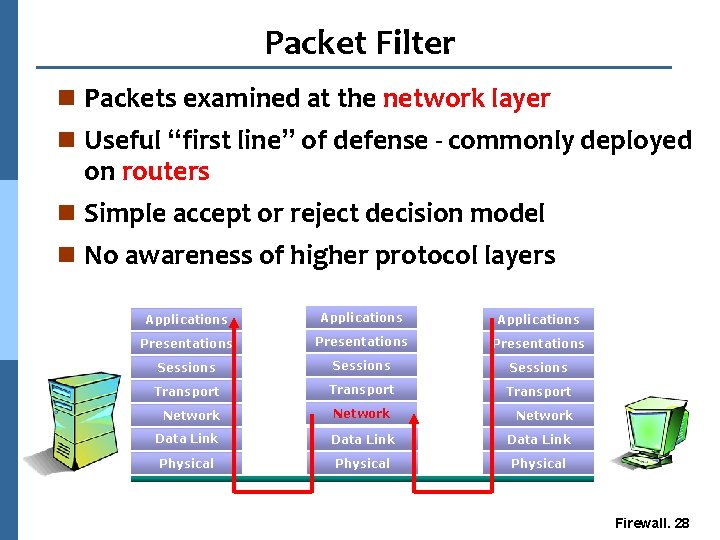
Packet Filter n Packets examined at the network layer n Useful “first line” of defense - commonly deployed on routers n Simple accept or reject decision model n No awareness of higher protocol layers Applications Presentations Sessions Transport Network Data Link Physical Firewall. 28

Packet Filtering Firewalls n Packet filtering is one of the oldest, and one of the most common types of firewall technologies. n Packet filters inspect each packet of information individually, examining the source and destination IP addresses and ports. n This information is compared to access control rules to decide whether the given packet should be allowed through the firewall. n Packet filters consider only the most basic attributes of each packet, and they don't need to remember anything about the traffic since each packet is examined in isolation. n For this reason they can decide packet flow very quickly. Firewall. 29

Packet Filtering Firewalls n Because every packet of every connection is checked against the access control rules, larger, complex rule bases decrease performance. n And because packet filters can only check low-level attributes, they are not secure against malicious code hiding in the other layers. n Packet filters are often used as a first defense in combination with other firewall technologies, and their most common implementation today is seen in the access control lists of routers at the perimeters of networks. n For simple protocols or one-sided connections, like ICMP or SNMP traps, it is still useful to use packet filtering technology. Firewall. 30

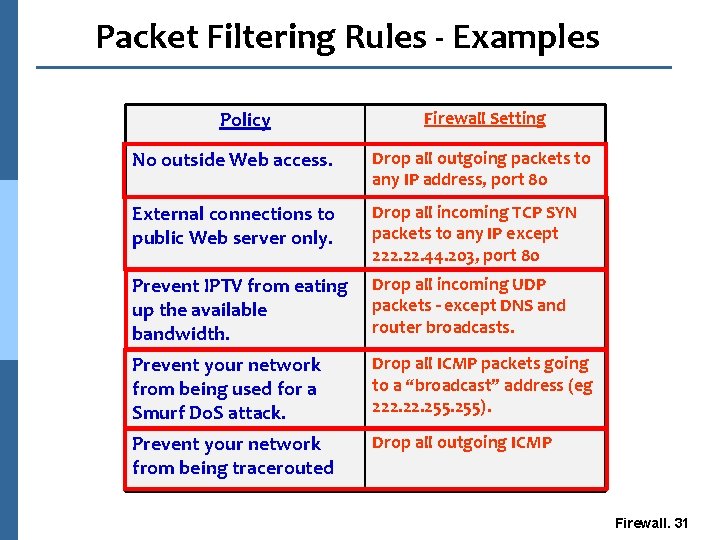
Packet Filtering Rules - Examples Policy Firewall Setting No outside Web access. Drop all outgoing packets to any IP address, port 80 External connections to public Web server only. Drop all incoming TCP SYN packets to any IP except 222. 44. 203, port 80 Prevent IPTV from eating up the available bandwidth. Drop all incoming UDP packets - except DNS and router broadcasts. Prevent your network from being used for a Smurf Do. S attack. Drop all ICMP packets going to a “broadcast” address (eg 222. 255). Prevent your network from being tracerouted Drop all outgoing ICMP Firewall. 31

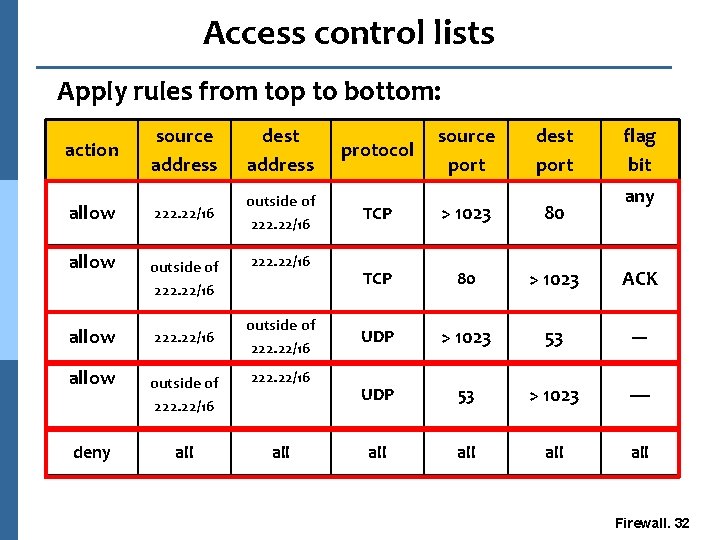
Access control lists Apply rules from top to bottom: action allow deny source address dest address 222. 22/16 outside of 222. 22/16 all protocol source port dest port flag bit any TCP > 1023 80 TCP 80 > 1023 ACK UDP > 1023 53 --- UDP 53 > 1023 ---- all all Firewall. 32

Access control lists n Each router/firewall interface can have its own ACL n Most firewall vendors provide both command- line and graphical configuration interface Firewall. 33

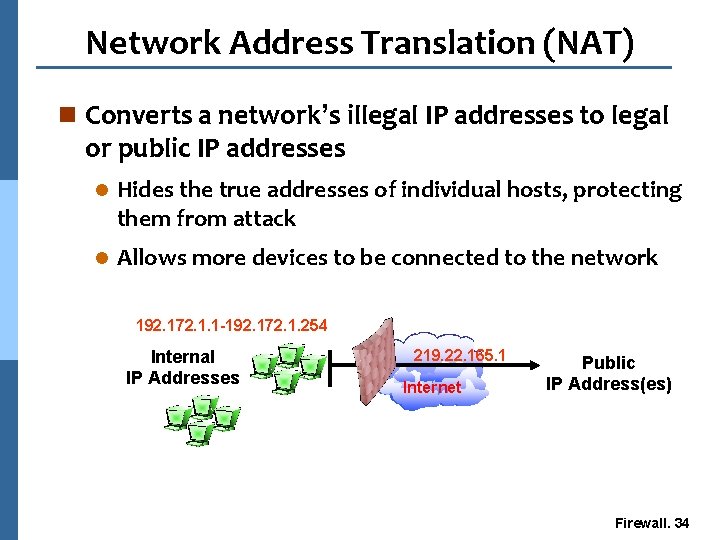
Network Address Translation (NAT) n Converts a network’s illegal IP addresses to legal or public IP addresses l Hides the true addresses of individual hosts, protecting them from attack l Allows more devices to be connected to the network 192. 172. 1. 1 -192. 172. 1. 254 Internal IP Addresses Corporate LAN 219. 22. 165. 1 Internet Public IP Address(es) Firewall. 34

Traditional packet filters n Advantages l One screening router can protect entire network l Can be efficient if filtering rules are kept simple l Widely available. Almost any router, even Linux boxes n Disadvantages l Can possibly be penetrated l Cannot enforce some policies. For example, permit certain users. l Rules can get complicated and difficult to test Firewall. 35

Application Level Firewalls n These firewalls, also known as application proxies, provide the most secure type of data connection because they can examine every layer of the communication, including the application data. n To achieve this security proxies, as their name suggests, actually mediate connections. n The connection from a client to a server is intercepted by the proxy. Firewall. 36

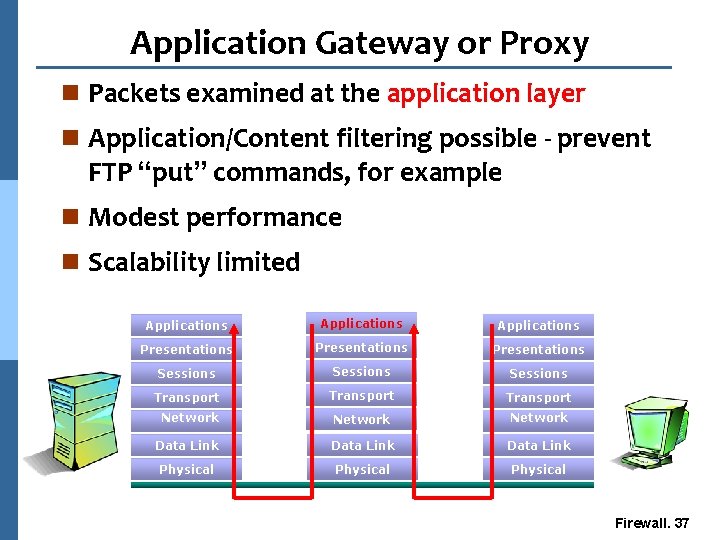
Application Gateway or Proxy n Packets examined at the application layer n Application/Content filtering possible - prevent FTP “put” commands, for example n Modest performance n Scalability limited Applications Presentations Sessions Transport Network Data Link Physical Firewall. 37

Application Level Firewalls n If the proxy determines that the connection is allowed, it opens a second connection to the server from itself, on behalf of the original host. n The data portion of each packet must be stripped off, examined, rebuilt, and sent again on the second connection. n This thorough examination and handling of packets means that proxy firewalls are very secure and generally slow. n Proxies are also limited as firewalls, because they must understand the application layer. n As new protocols are developed, new proxies must be written and implemented to handle them. Firewall. 38

Application Level Firewalls n Web Proxy Severs n Application Proxy Servers n A mail server is an example of an application gateway l Can’t deposit mail in recipient’s mail server without passing through sender’s mail server n Second Generation Firewall Technology l Makes connections on behalf of the client l Not flexible Firewall. 39

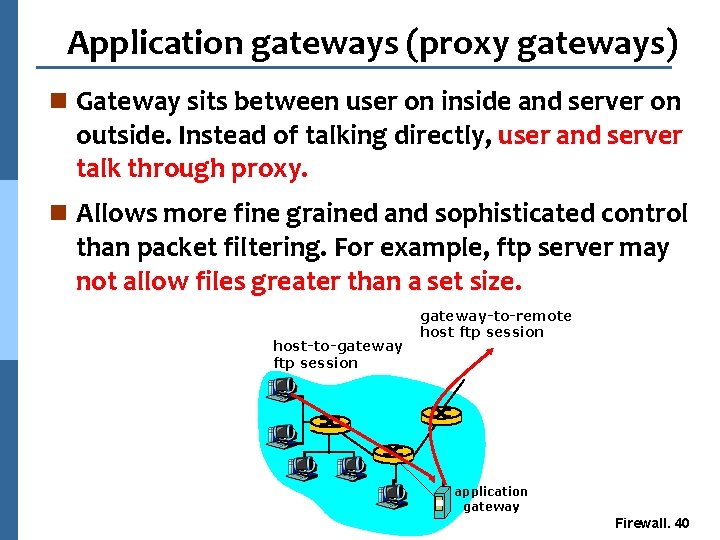
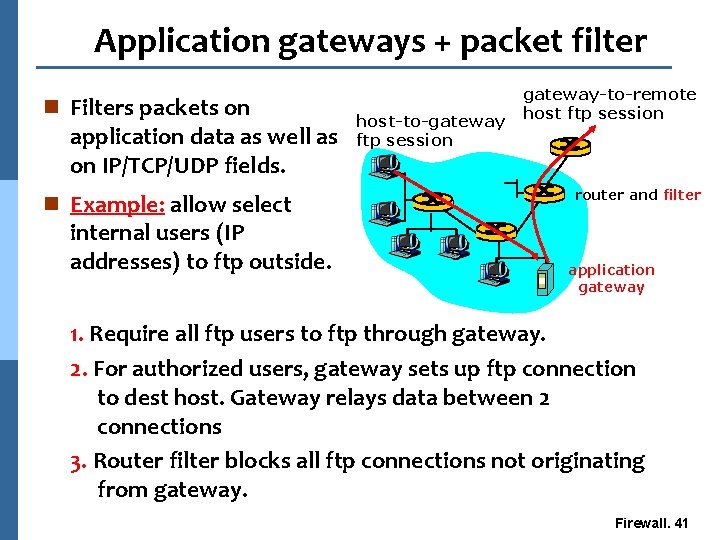
Application gateways (proxy gateways) n Gateway sits between user on inside and server on outside. Instead of talking directly, user and server talk through proxy. n Allows more fine grained and sophisticated control than packet filtering. For example, ftp server may not allow files greater than a set size. host-to-gateway ftp session gateway-to-remote host ftp session application gateway Firewall. 40

Application gateways + packet filter n Filters packets on application data as well as on IP/TCP/UDP fields. n Example: allow select internal users (IP addresses) to ftp outside. host-to-gateway ftp session gateway-to-remote host ftp session router and filter application gateway 1. Require all ftp users to ftp through gateway. 2. For authorized users, gateway sets up ftp connection to dest host. Gateway relays data between 2 connections 3. Router filter blocks all ftp connections not originating from gateway. Firewall. 41

Chaining Proxies proxy 2 proxy 1 Firewall. 42

SOCKS Proxy protocol n Generic proxy protocol l Don’t have to redo all of the code when proxifying an application. n Can be used by HTTP, FTP, telnet, SSL, … l Independent of application layer protocol n Includes authentication, restricting which users/apps/IP addresses can pass through firewall. Firewall. 43

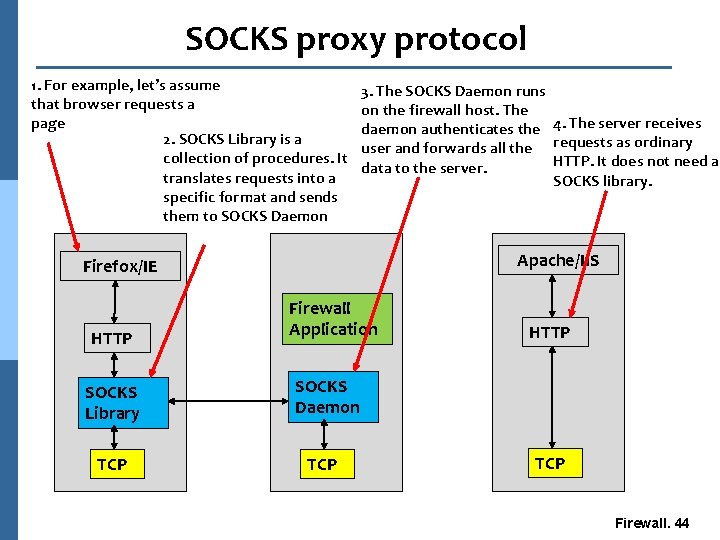
SOCKS proxy protocol 1. For example, let’s assume that browser requests a page 2. SOCKS Library is a collection of procedures. It translates requests into a specific format and sends them to SOCKS Daemon 3. The SOCKS Daemon runs on the firewall host. The daemon authenticates the 4. The server receives user and forwards all the requests as ordinary HTTP. It does not need a data to the server. SOCKS library. Apache/IIS Firefox/IE HTTP SOCKS Library TCP Firewall Application HTTP SOCKS Daemon TCP Firewall. 44

Proxy gateways n Advantages l Proxy can log all connections, activity in connections l Proxy can provide caching l Proxy can do intelligent filtering based on content l Proxy can perform user-level authentication n Disadvantages l Not all services have proxied versions l May need different proxy server for each service l Requires modification of client l Performance Firewall. 45

Stateful Filters n Stateful filter: Adds more intelligence to the filter decision-making process l Stateful = remember past packets l Memory implemented in a very dynamic state table Firewall. 46

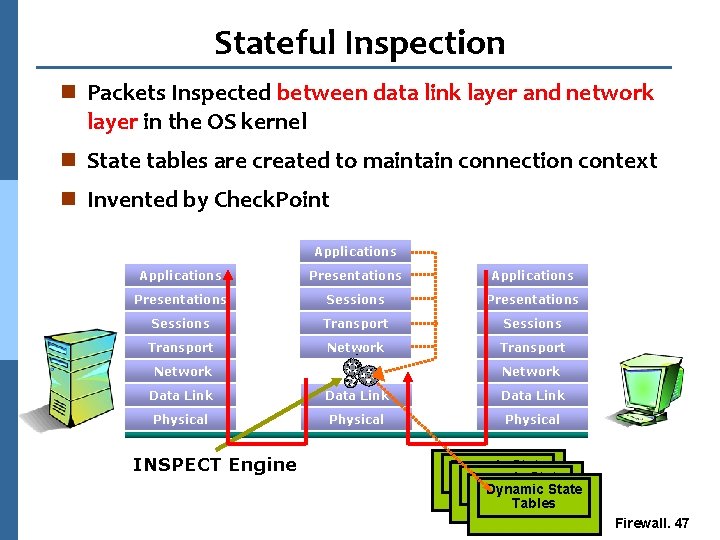
Stateful Inspection n Packets Inspected between data link layer and network layer in the OS kernel n State tables are created to maintain connection context n Invented by Check. Point Applications Presentations Sessions Transport Network Data Link Physical INSPECT Engine Dynamic State Dynamic Tables State Tables Firewall. 47

Stateful Inspection © n Stateful inspection architecture utilizes a unique, patented INSPECT Engine which enforces the security policy on the gateway on which it resides. n The INSPECT Engine looks at all communication layers and extracts only the relevant data, enabling highly efficient operation, support for a large number of protocols and applications, and easy extensibility to new applications and services. n The INSPECT Engine is programmable using Check. Point's powerful INSPECT Language. Firewall. 48

Stateful Inspection © n This provides important system extensibility, allowing Check. Point, as well as its technology partners and endusers, to incorporate new applications, services, and protocols, without requiring new software to be loaded. n For most new applications, including most custom applications developed by end users, the communicationrelated behavior of the new application can be incorporated simply by modifying one of Firewall-1's built -in script templates via the graphical user interface. n Even the most complex applications can be added quickly and easily via the INSPECT Language. Firewall. 49

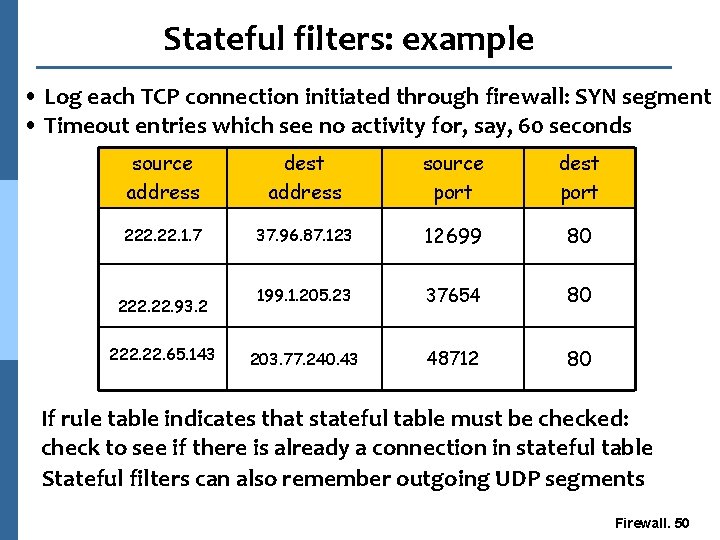
Stateful filters: example • Log each TCP connection initiated through firewall: SYN segment • Timeout entries which see no activity for, say, 60 seconds source address dest address source port dest port 222. 1. 7 37. 96. 87. 123 12699 80 199. 1. 205. 23 37654 80 203. 77. 240. 43 48712 80 222. 93. 2 222. 65. 143 If rule table indicates that stateful table must be checked: check to see if there is already a connection in stateful table Stateful filters can also remember outgoing UDP segments Firewall. 50

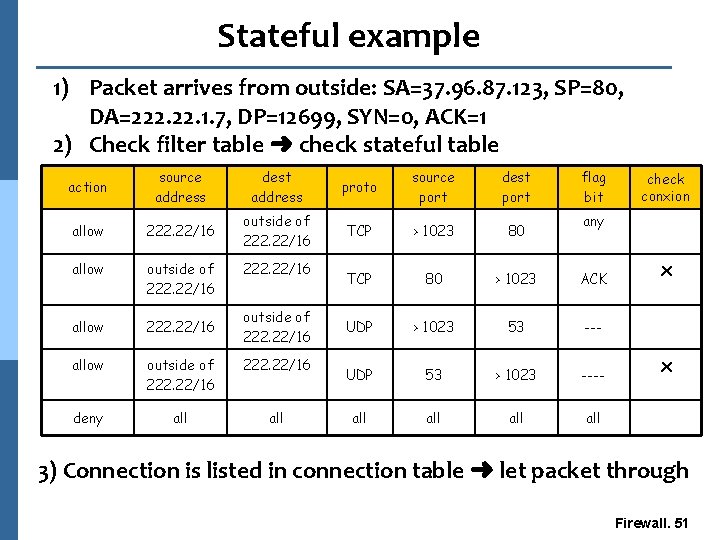
Stateful example 1) Packet arrives from outside: SA=37. 96. 87. 123, SP=80, DA=222. 1. 7, DP=12699, SYN=0, ACK=1 2) Check filter table ➜ check stateful table action source address dest address proto source port dest port allow 222. 22/16 outside of 222. 22/16 TCP > 1023 80 allow outside of 222. 22/16 TCP 80 > 1023 ACK allow 222. 22/16 UDP > 1023 53 --- allow outside of 222. 22/16 UDP 53 > 1023 ---- deny all all all 222. 22/16 outside of 222. 22/16 flag bit check conxion any x x 3) Connection is listed in connection table ➜ let packet through Firewall. 51

Contents n Firewall Introduction n Firewall Hardware Types n Firewall Technologies n Firewall Architecture n Firewall Deployment n VPN (Virtual Private Network) n Firewall Labs : Iptables Firewall. 52

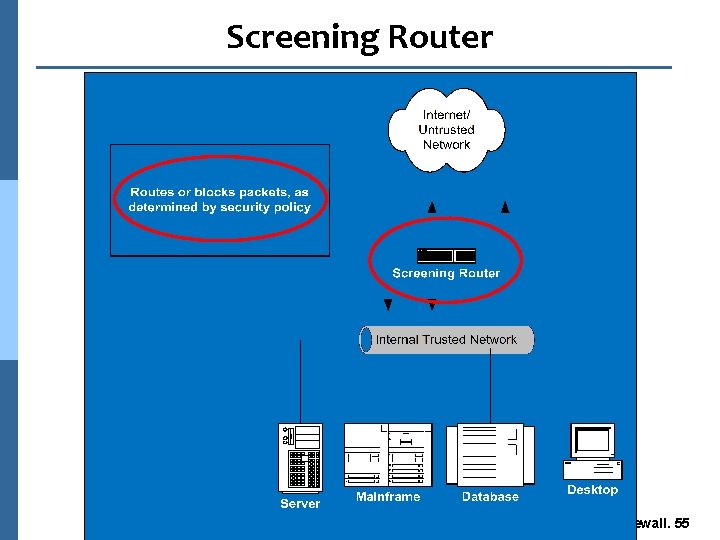
Network Firewall Architectures n Screening Router n Simple Firewall n Multi-Legged firewall n Firewall Sandwich n Layered Security Architecture Firewall. 53

Screening Router n Access Lists provide security n Routers are not application aware l Only inspects network level information l Layer 3 of the OSI model n Does not provide a great deal of security n Very fast n Not commonly used alone for security Firewall. 54

Screening Router Firewall. 55

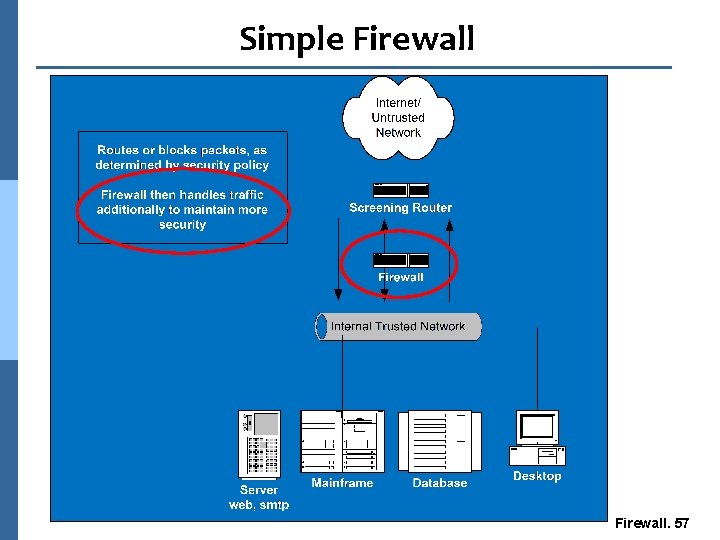
Simple Firewall n Small Companies with limited security needs n Only utilizes two interfaces l Trusted l Un-trusted n Provides modest security n Does not offer dmz sandbox n Inherently allows some level of connections between trusted and un-trusted networks Firewall. 56

Simple Firewall. 57

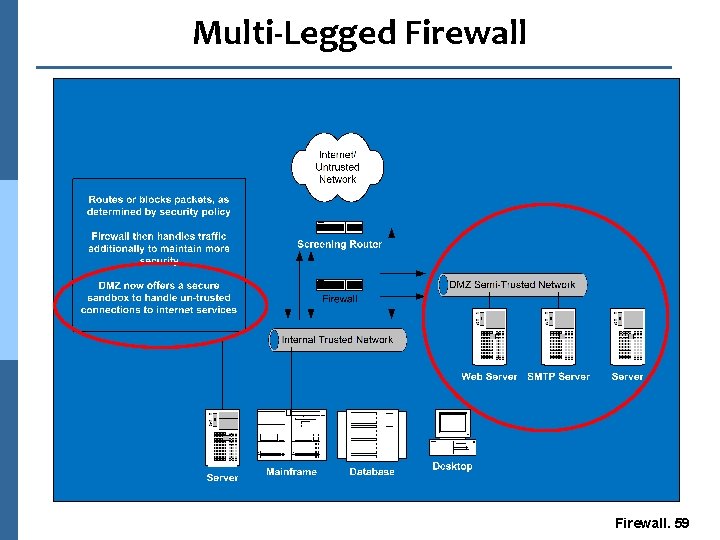
Multi-Legged Firewall n Small to large sized business n Security need is expanded n Provides stronger security n Creates a secure sandbox for semi-trusted services n Flexible and secure Firewall. 58

Multi-Legged Firewall. 59

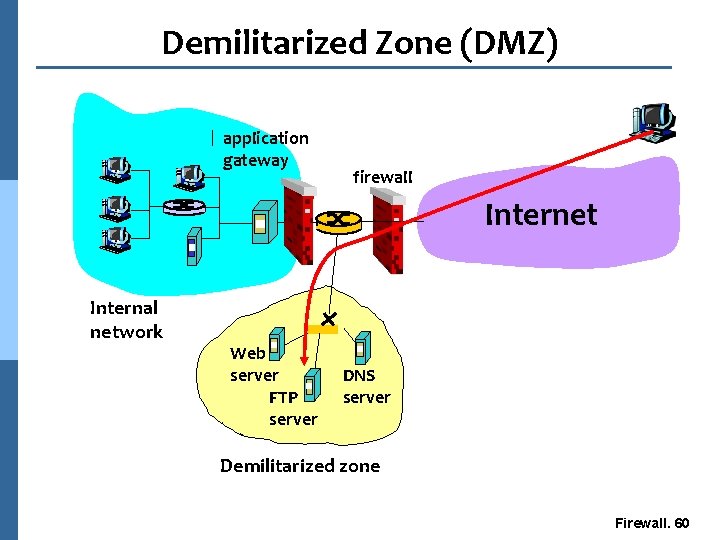
Demilitarized Zone (DMZ) application gateway firewall Internet Internal network Web server FTP server DNS server Demilitarized zone Firewall. 60

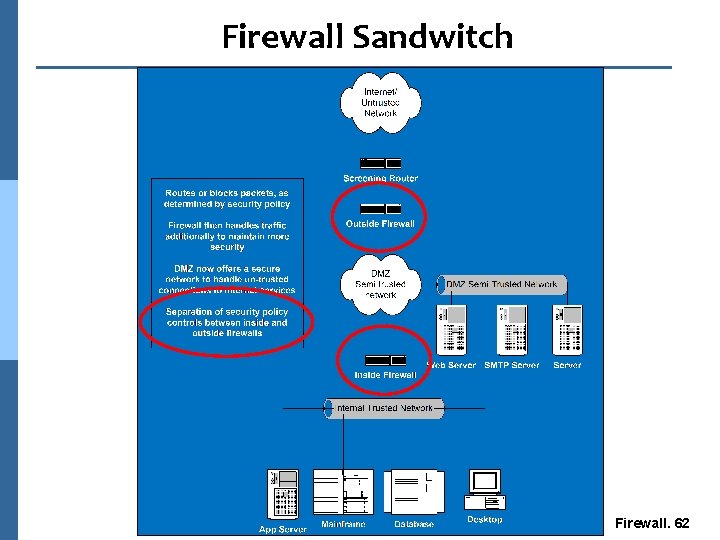
Firewall Sandwich n Medium to large businesses l Higher costs n More serious need for security l Provides a physical separation of networks n Provides policy segregation between inside and outside firewalls l Reduces administrative holes Firewall. 61

Firewall Sandwitch Firewall. 62

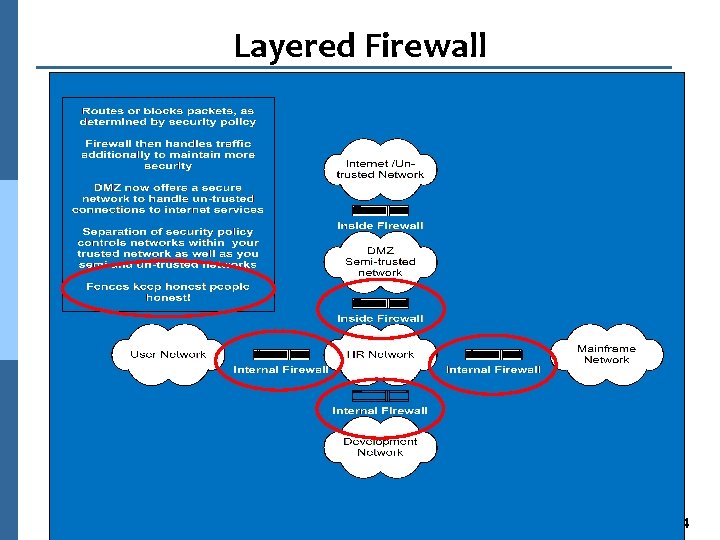
Layered Firewall Approach n Large enterprises with low risk tolerance l Separates internal environments l Reduces computer crimes 4 Most attacks are internally based 4 Deters malicious activities l Controls overhead administrative traffic l Allows IDS to work more effectively Firewall. 63

Layered Firewall. 64

Defense in depth n Security has no single right answer l Use every tool available to bolster security n Layered security is always the best approach n Strong security controls coupled with audit, administrative reviews, and an effective security response plan will provide a strong holistic defense Firewall. 65

Contents n Firewall Introduction n Firewall Hardware Types n Firewall Technologies n Firewall Architecture n Firewall Deployment n VPN (Virtual Private Network) n Firewall Labs : Iptables Firewall. 66

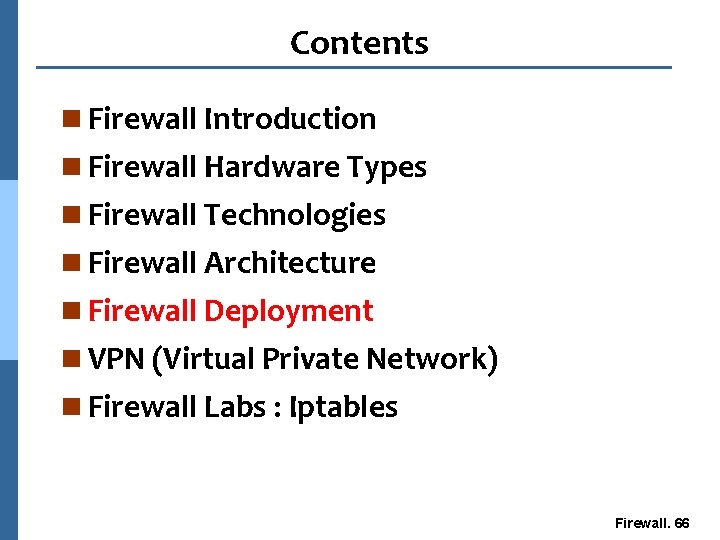
Firewall Deployment n Corporate Network Gateway DMZ Internet Demilitarized Zone (DMZ) Public Servers l Protect internal network from attack Corporate Network Gateway l Most common Human Resources Network deployment point Corporate Site Firewall. 67

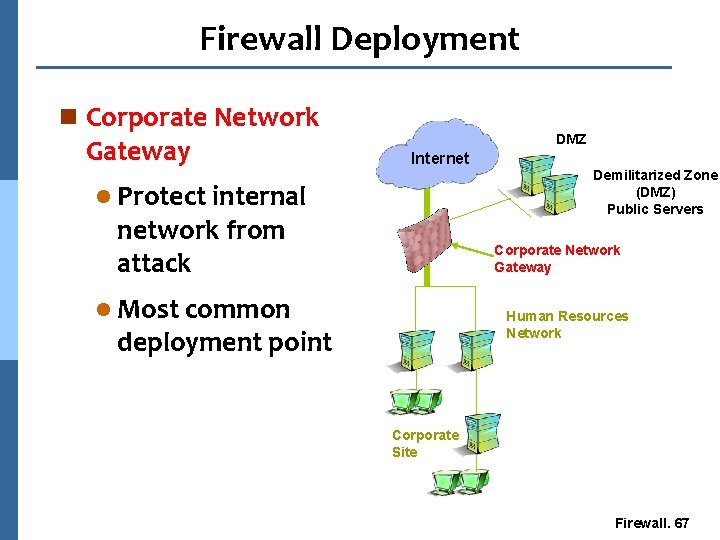
Firewall Deployment n Internal Segment Gateway l l l Protect sensitive segments (Finance, HR, Product Development) Internet Public Servers Demilitarized Zone (Publicly-accessible servers) Provide second layer of defense Human Resources Network Ensure protection against internal attacks and misuse Internal Segment Gateway Corporate Site Firewall. 68

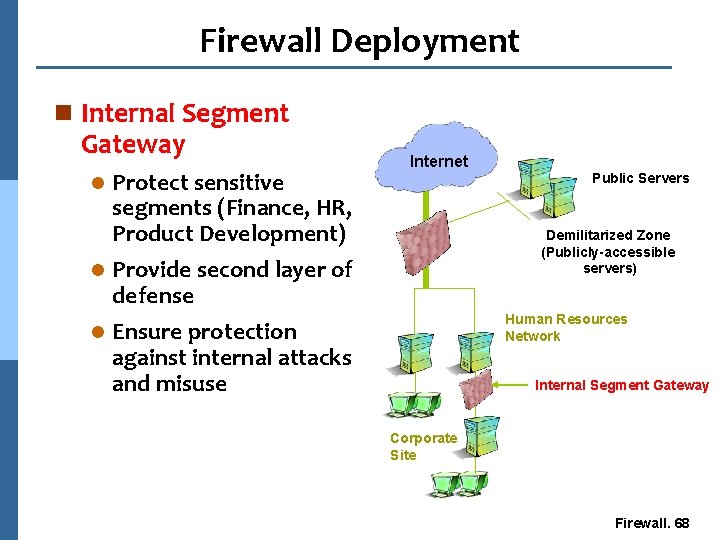
Firewall Deployment n Server-Based Firewall l Protect individual Internet Public Servers DMZ application servers l Files protect Human Resources Network Server-Based Firewall Corporate Site SAP Server Firewall. 69

Firewall Deployment n Hardware appliance based firewall l Single platform, software pre-installed l Can be used to support small organizations or branch offices with little IT support n Software based firewall l Flexible platform deployment options l Can scale as organization grows Firewall. 70

Contents n Firewall Introduction n Firewall Hardware Types n Firewall Technologies n Firewall Architecture n Firewall Deployment n VPN (Virtual Private Network) n Firewall Labs : Iptables Firewall. 71

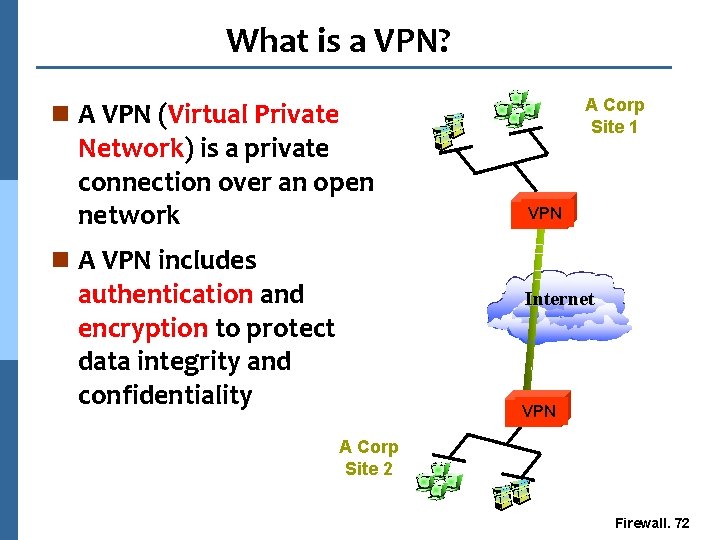
What is a VPN? A Corp Acme Site Corp 1 n A VPN (Virtual Private Network) is a private connection over an open network VPN n A VPN includes authentication and encryption to protect data integrity and confidentiality Internet VPN A Corp Site 2 Firewall. 72

Why Use Virtual Private Networks? n More flexibility l Leverage ISP point of presence l Use multiple connection types (cable, DSL, T 1, T 3) l Most attacks originate within an organization Firewall. 73

Why Use Virtual Private Networks? n More scalability l Add new sites, users quickly l Scale bandwidth to demand Firewall. 74

Why Use Virtual Private Networks? n Lower costs l Reduced frame relay/leased line costs l Reduced long distance l Reduced equipment costs (modem banks, CSU/DSUs) l Reduced technical support Firewall. 75

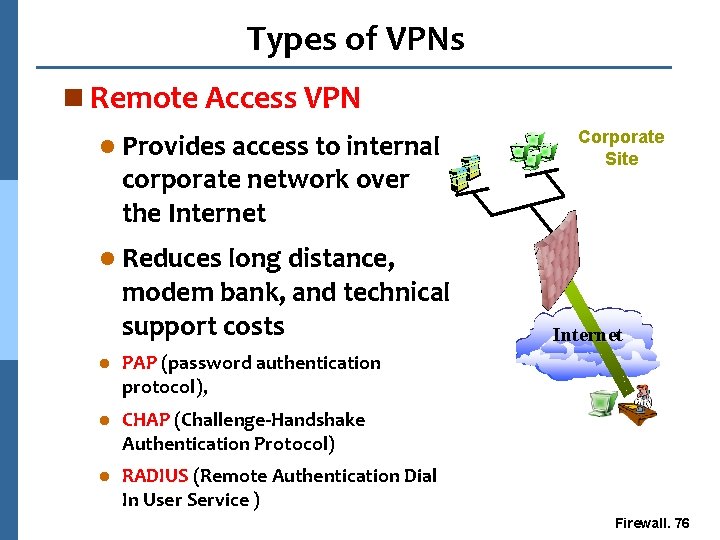
Types of VPNs n Remote Access VPN l Provides access to internal corporate network over the Internet Corporate Site l Reduces long distance, modem bank, and technical support costs l PAP (password authentication protocol), l CHAP (Challenge-Handshake Authentication Protocol) l RADIUS (Remote Authentication Dial In User Service ) Internet Firewall. 76

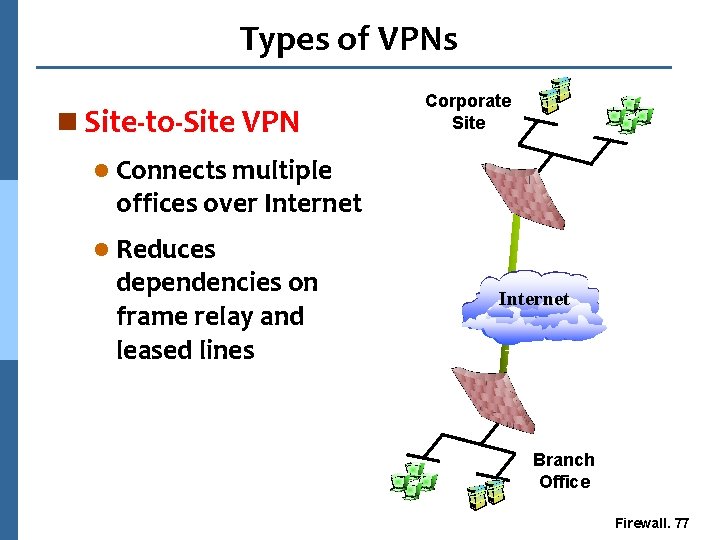
Types of VPNs n Site-to-Site VPN Corporate Site l Connects multiple offices over Internet l Reduces dependencies on frame relay and leased lines Internet Branch Office Firewall. 77

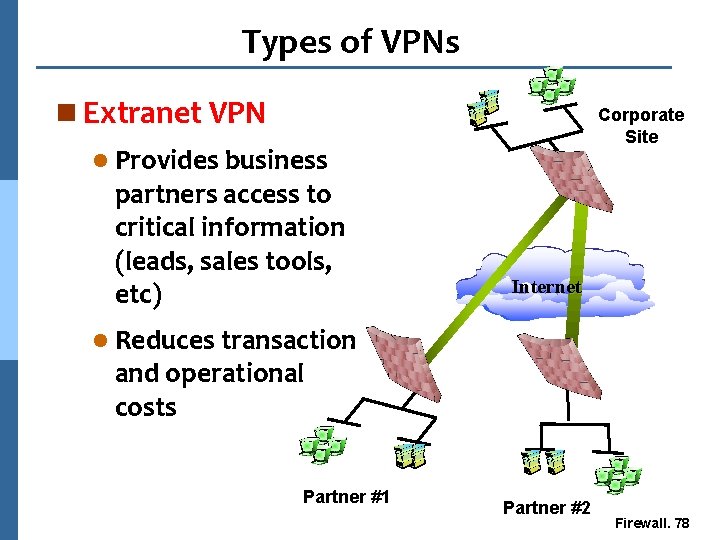
Types of VPNs n Extranet VPN Corporate Site l Provides business partners access to critical information (leads, sales tools, etc) Internet l Reduces transaction and operational costs Partner #1 Partner #2 Firewall. 78

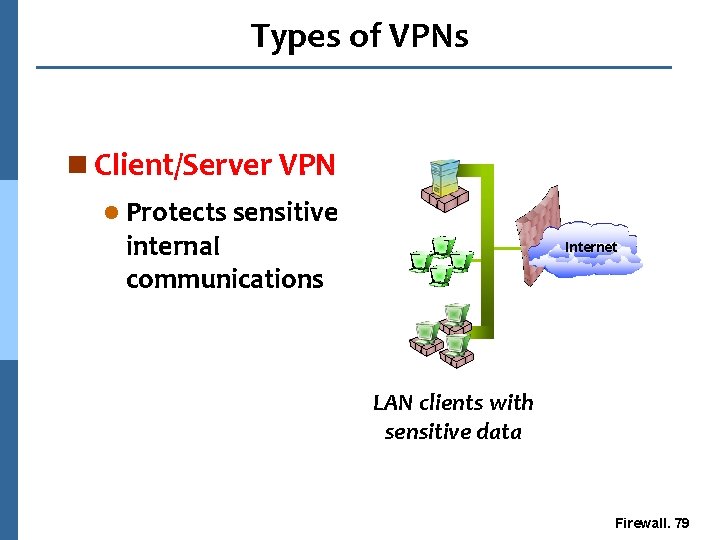
Types of VPNs n Client/Server VPN l Protects sensitive internal communications Database Server LAN clients Internet LAN clients with sensitive data Firewall. 79

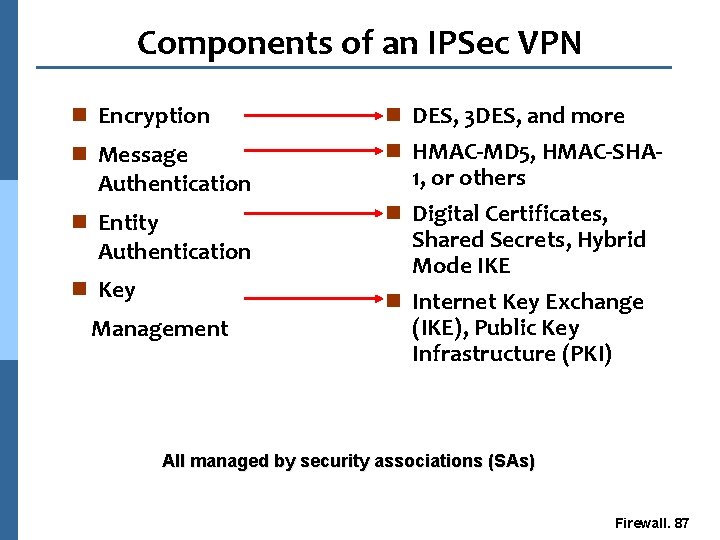
Components of a VPN n Encryption n Key management n Message authentication n Entity authentication Firewall. 80

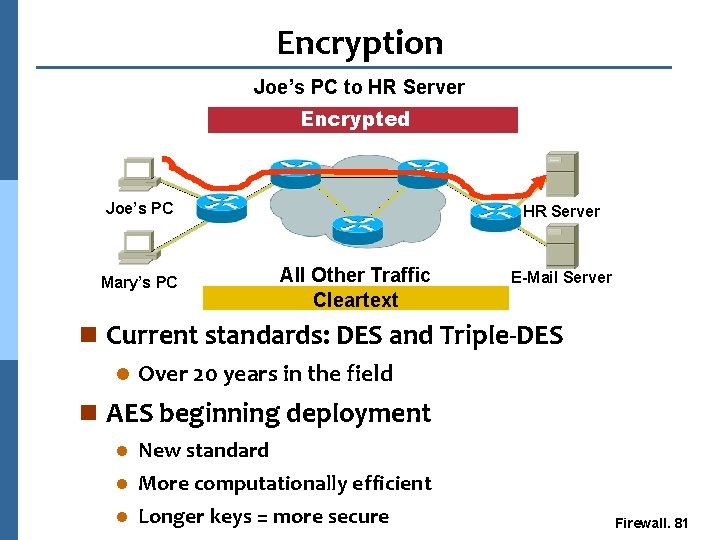
Encryption Joe’s PC to HR Server Encrypted Joe’s PC Mary’s PC HR Server All Other Traffic Cleartext E-Mail Server n Current standards: DES and Triple-DES l Over 20 years in the field n AES beginning deployment New standard l More computationally efficient l Longer keys = more secure l Firewall. 81

Key Management n Public key cryptosystems enable secure exchange of private crypto keys across open networks n Re-keying at appropriate intervals n IKE = Internet Key Exchange protocols l Incorporates ISAKMP (Internet Security Association and Key Management Protocol) Firewall. 82

Authentication n IPsec standards focus on authentication of two network devices to each other l IP address/preshared key l Digital certificates n User authentication is added on top if required l RADIUS and TACACS+ (Terminal Access Controller Access-Control System Plus) are the standard protocols for authentication servers n XAUTH is being added to the standards to address user authentication Firewall. 83

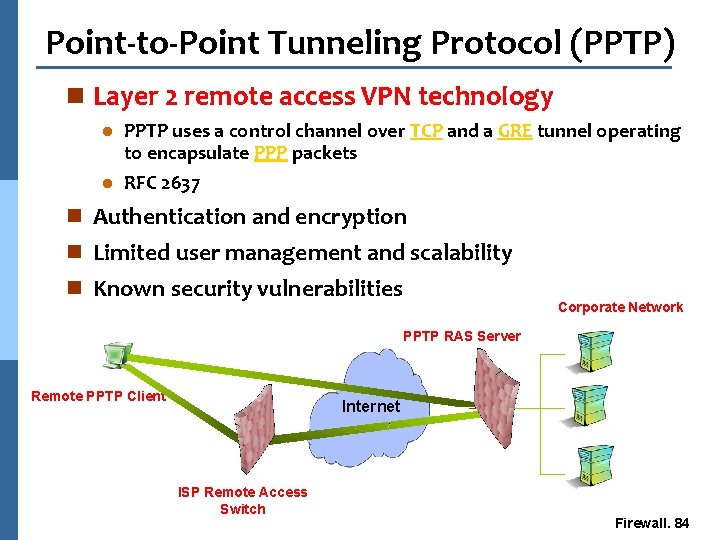
Point-to-Point Tunneling Protocol (PPTP) n Layer 2 remote access VPN technology PPTP uses a control channel over TCP and a GRE tunnel operating to encapsulate PPP packets l RFC 2637 l n Authentication and encryption n Limited user management and scalability n Known security vulnerabilities Corporate Network PPTP RAS Server Remote PPTP Client Internet ISP Remote Access Switch Firewall. 84

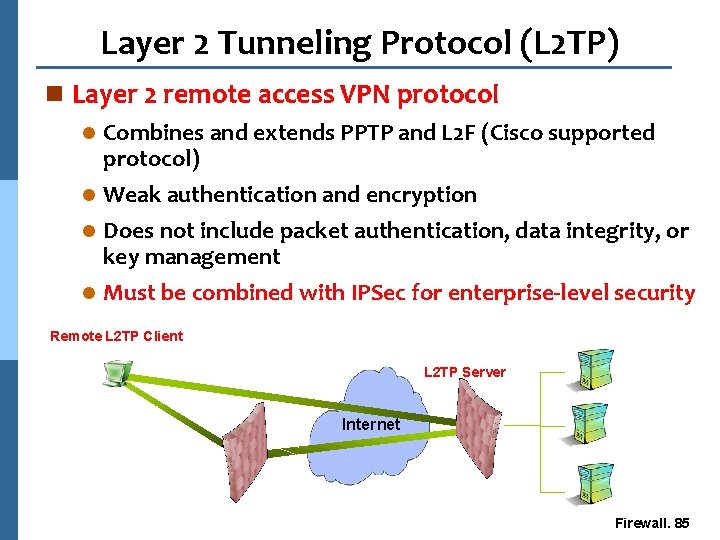
Layer 2 Tunneling Protocol (L 2 TP) n Layer 2 remote access VPN protocol Combines and extends PPTP and L 2 F (Cisco supported protocol) l Weak authentication and encryption l l Does not include packet authentication, data integrity, or key management l Must be combined with IPSec for enterprise-level security Corporate Network Remote L 2 TP Client L 2 TP Server Internet ISP L 2 TP Concentrator Firewall. 85

Internet Protocol Security (IPSec) n Layer 3 protocol for remote access, intranet, and extranet VPNs l Internet standard for VPNs l Provides flexible encryption and message authentication/integrity l Includes key management Firewall. 86

Components of an IPSec VPN n Encryption n DES, 3 DES, and more n Message n HMAC-MD 5, HMAC-SHA- Authentication n Entity Authentication n Key Management 1, or others n Digital Certificates, Shared Secrets, Hybrid Mode IKE n Internet Key Exchange (IKE), Public Key Infrastructure (PKI) All managed by security associations (SAs) Firewall. 87

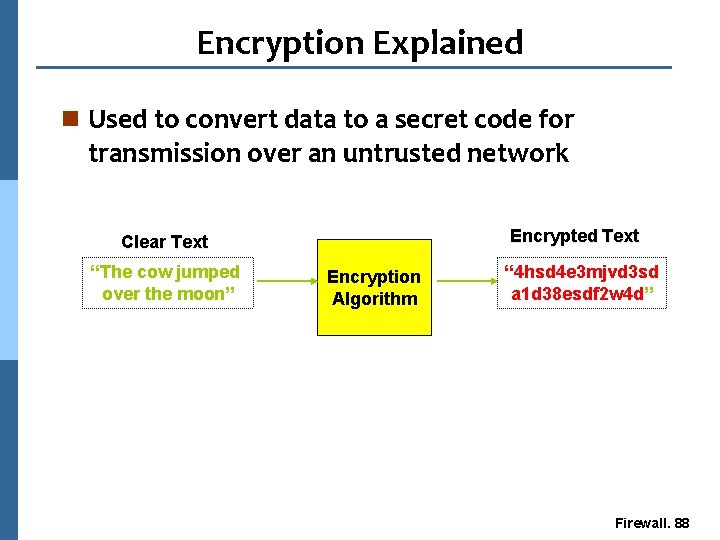
Encryption Explained n Used to convert data to a secret code for transmission over an untrusted network Encrypted Text Clear Text “The cow jumped over the moon” Encryption Algorithm “ 4 hsd 4 e 3 mjvd 3 sd a 1 d 38 esdf 2 w 4 d” Firewall. 88

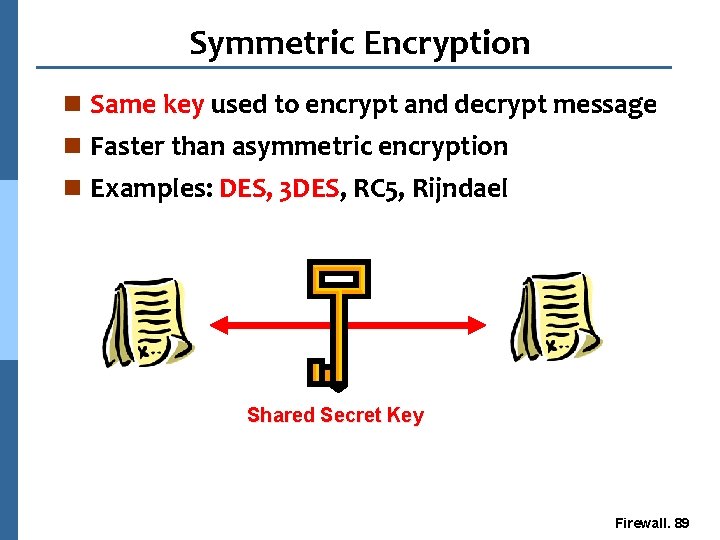
Symmetric Encryption n Same key used to encrypt and decrypt message n Faster than asymmetric encryption n Examples: DES, 3 DES, RC 5, Rijndael Shared Secret Key Firewall. 89

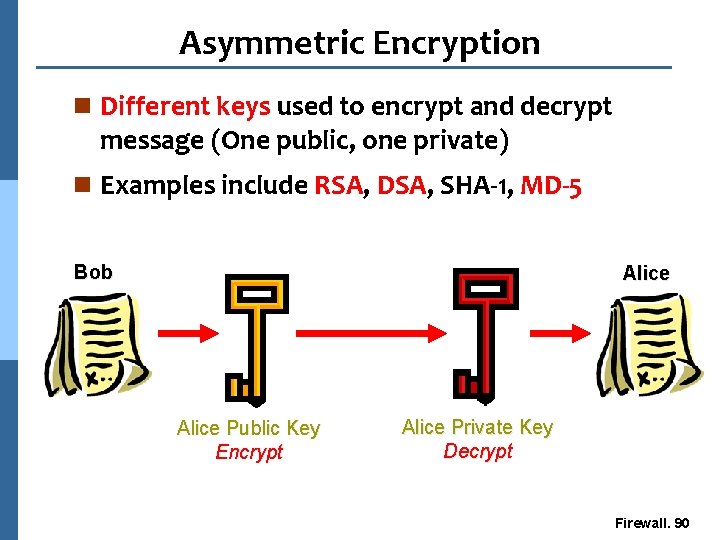
Asymmetric Encryption n Different keys used to encrypt and decrypt message (One public, one private) n Examples include RSA, DSA, SHA-1, MD-5 Bob Alice Public Key Encrypt Alice Private Key Decrypt Firewall. 90

Contents n Firewall Introduction n Firewall Hardware Types n Firewall Technologies n Firewall Architecture n Firewall Deployment n VPN (Virtual Private Network) n Firewall Labs : Iptables Firewall. 91

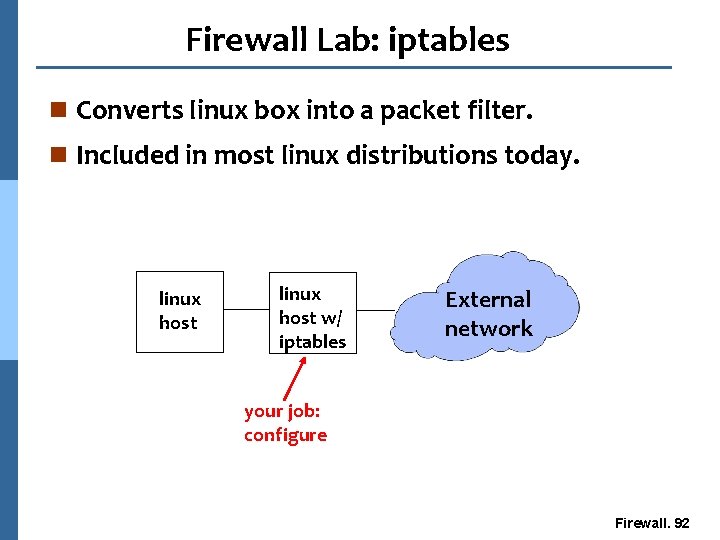
Firewall Lab: iptables n Converts linux box into a packet filter. n Included in most linux distributions today. linux host w/ iptables External network your job: configure Firewall. 92

Firewall lab: iptables n iptables l Provides firewall capability to a linux host l Comes installed with most linux distributions l Three types of tables: FILTER, NAT, MANGLE l Let’s only consider FILTER table for now Firewall. 93

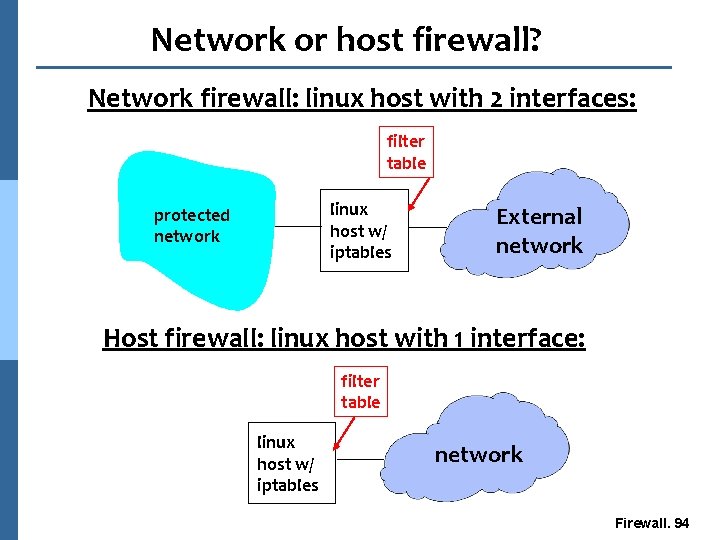
Network or host firewall? Network firewall: linux host with 2 interfaces: filter table linux host w/ iptables protected network External network Host firewall: linux host with 1 interface: filter table linux host w/ iptables network Firewall. 94

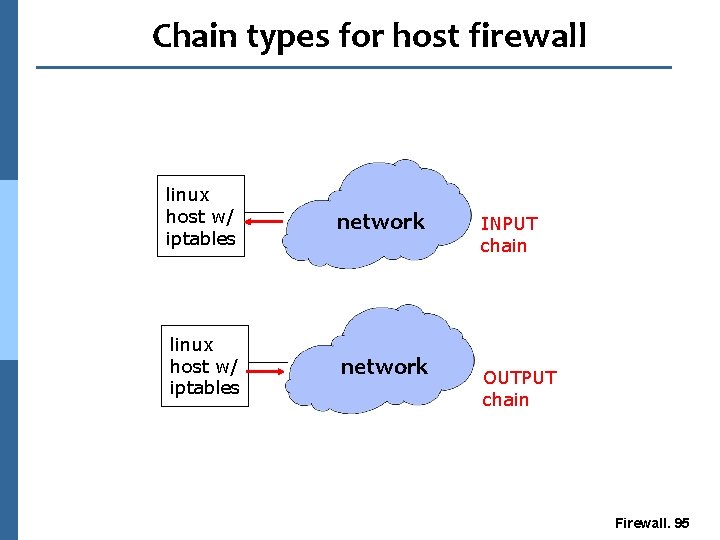
Chain types for host firewall linux host w/ iptables network INPUT chain OUTPUT chain Firewall. 95

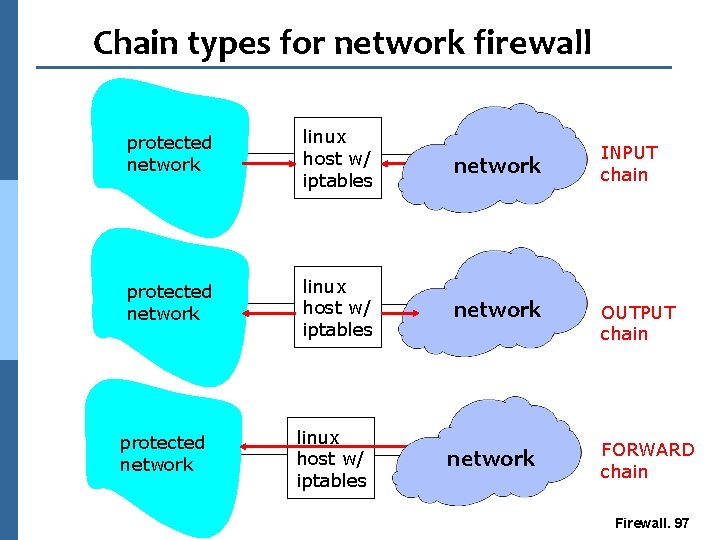
INPUT, OUTPUT, FORWARD CHAINS for network firewall n INPUT chain applies for all packets destined to firewall n OUTPUT chain applies for all packets originating from firewall n FORWARD chain applies for all packets passing through firewall. Firewall. 96

Chain types for network firewall protected network linux host w/ iptables network INPUT chain OUTPUT chain FORWARD chain Firewall. 97

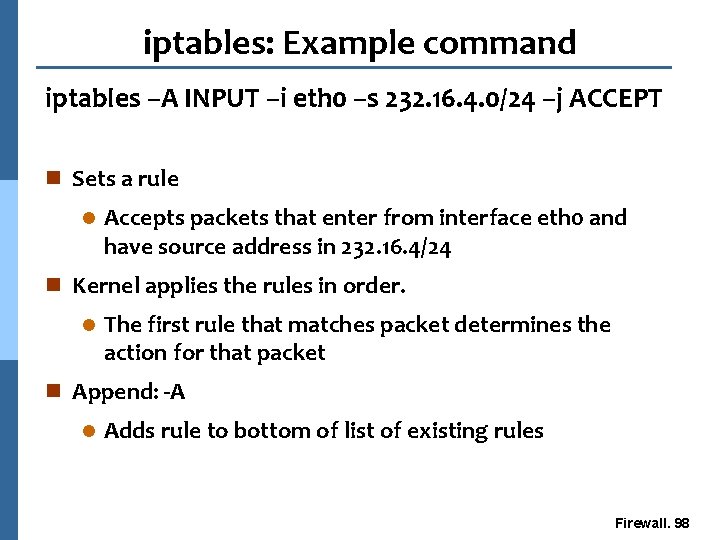
iptables: Example command iptables –A INPUT –i eth 0 –s 232. 16. 4. 0/24 –j ACCEPT n Sets a rule l Accepts packets that enter from interface eth 0 and have source address in 232. 16. 4/24 n Kernel applies the rules in order. l The first rule that matches packet determines the action for that packet n Append: -A l Adds rule to bottom of list of existing rules Firewall. 98

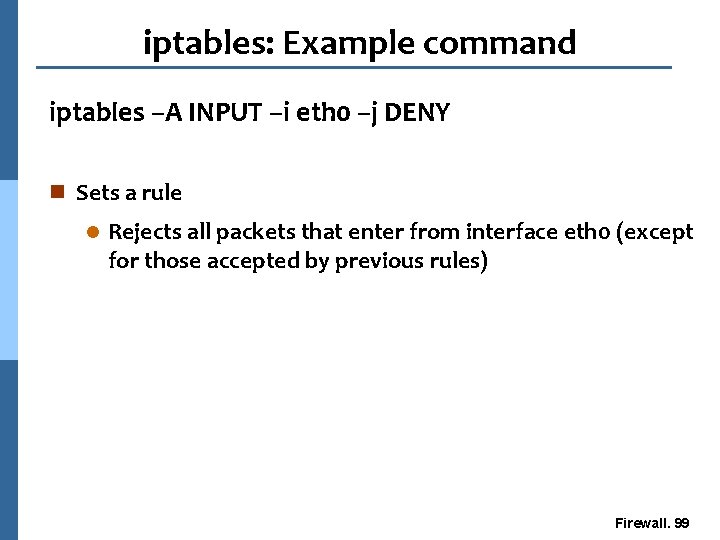
iptables: Example command iptables –A INPUT –i eth 0 –j DENY n Sets a rule l Rejects all packets that enter from interface eth 0 (except for those accepted by previous rules) Firewall. 99

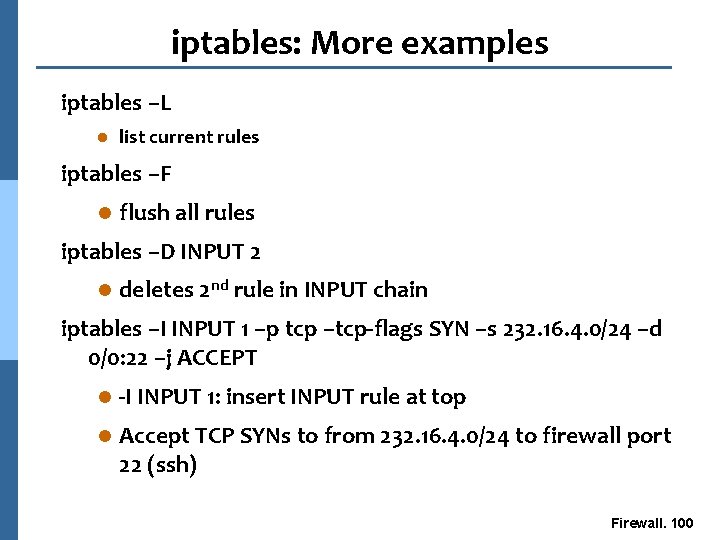
iptables: More examples iptables –L l list current rules iptables –F l flush all rules iptables –D INPUT 2 l deletes 2 nd rule in INPUT chain iptables –I INPUT 1 –p tcp –tcp-flags SYN –s 232. 16. 4. 0/24 –d 0/0: 22 –j ACCEPT l -I INPUT 1: insert INPUT rule at top l Accept TCP SYNs to from 232. 16. 4. 0/24 to firewall port 22 (ssh) Firewall. 100

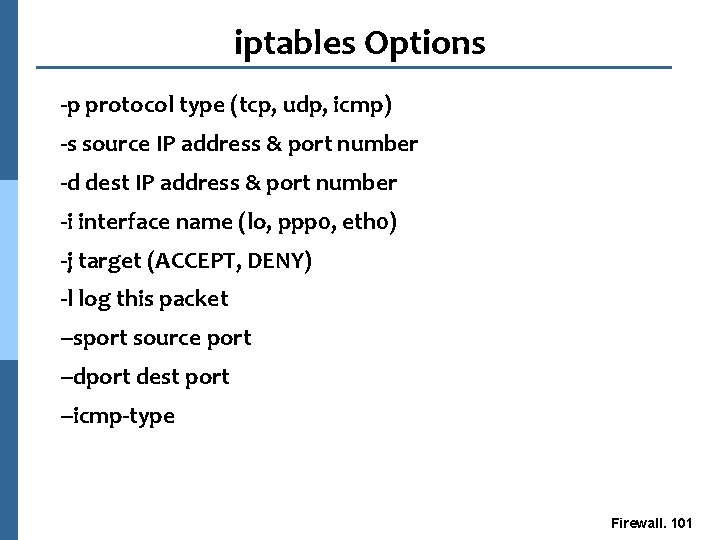
iptables Options -p protocol type (tcp, udp, icmp) -s source IP address & port number -d dest IP address & port number -i interface name (lo, ppp 0, eth 0) -j target (ACCEPT, DENY) -l log this packet --sport source port --dport dest port --icmp-type Firewall. 101

iptable Table types n FILTER: l What we have been talking about! l 3 chain types: INPUT, OUTPUT, and FORWARD n NAT: l Hide internal network hosts from outside world. Outside world only sees the gateway’s external IP address, and no other internal IP addresses l PREROUTING, POSTROUTING, and others n MANGLE l Don’t worry about it. Firewall. 102

Tables, Chains & Rules n Three types of tables: FILTER, NAT, MANGLE n A table consists of chains. l For example, a filter table can have an INPUT chain, OUTPUT chain, and a FORWARD chain. n A chain consists of a set of rules. Firewall. 103

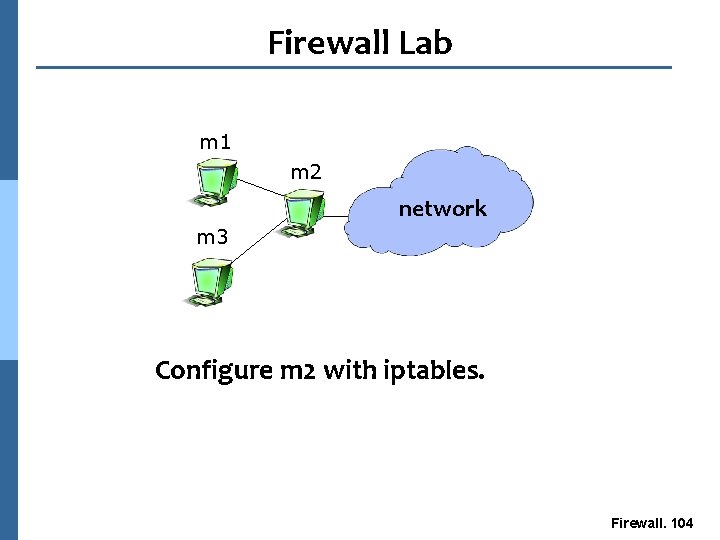
Firewall Lab m 1 m 2 network m 3 Configure m 2 with iptables. Firewall. 104

Firewall Lab: Part A n Configure NAT in m 2 using NAT table with POSTROUTING chain: l MASQUERADE packets so that internal IP addresses are hidden from external network l From m 1 and m 3, only allow ssh to external network n This NAT configuration will remain in force throughout the lab Firewall. 105

Firewall Lab: Part B Rules for packets originating from or terminating at m 2 (the gateway): n Allow ssh connections originating from m 2 and destined to m 2. n Allow pings originating from m 2 and destined to m 2. n Block all other traffic to or from m 2. n Hint: Part B requires INPUT and OUTPUT chains but no FORWARD chain Firewall. 106

Firewall Lab: Part C n Flush filter table rules from Part B. n Allow only m 1 (and not m 3) to initiate an ssh session to hosts in the external network n Reject all other traffic n Hint: Part C requires FORWARD, INPUT and OUTPUT chains Firewall. 107