Felipe Santos Manoj Deshpande ECE 4112 Internetwork Security
















- Slides: 28

Felipe Santos Manoj Deshpande ECE 4112 – Internetwork Security Georgia Institute of Technology SPAM OVER IP TELEPHONY (SPIT) Identification and prevention Techniques

Background SPAM considered one of biggest problems in Internet SPIT is expected to become a major issue in the next few years with increasing deployment of Vo. IP solutions Potential for productivity disturbance is much greater than SPAM

Background Definition: The transmission of unsolicited calls over Internet telephony (Vo. IP) “SPITTERS” will forge their identities SPITTING agent capable of placing hundreds of simultaneous automated calls SIP is not voice only, but applies to Instant Messaging and video as well

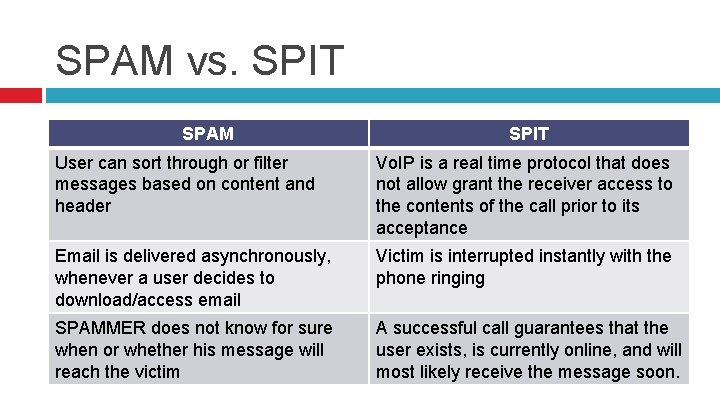
SPAM vs. SPIT SPAM SPIT User can sort through or filter messages based on content and header Vo. IP is a real time protocol that does not allow grant the receiver access to the contents of the call prior to its acceptance Email is delivered asynchronously, whenever a user decides to download/access email Victim is interrupted instantly with the phone ringing SPAMMER does not know for sure when or whether his message will reach the victim A successful call guarantees that the user exists, is currently online, and will most likely receive the message soon.

SPIT Prevention Framework Goals: Minimize false positives & negatives Minimize callee interaction in identifying SPIT Minimize inconvenience to caller General enough to work in different environments (work, home, etc) and cultures

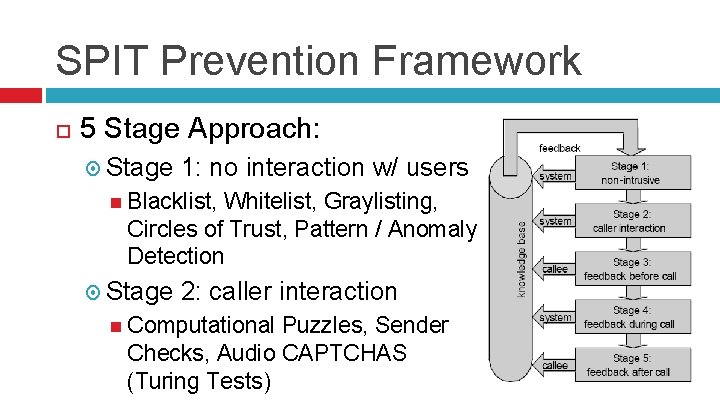
SPIT Prevention Framework 5 Stage Approach: Stage 1: no interaction w/ users Blacklist, Whitelist, Graylisting, Circles of Trust, Pattern / Anomaly Detection Stage 2: caller interaction Computational Puzzles, Sender Checks, Audio CAPTCHAS (Turing Tests)

SPIT Prevention Framework 5 Stage Approach (continued): Stage 3: feedback before call Stage 4: during the call Manual authorization to receive call and/or authenticate user Content analysis (not currently viable) Stage 5: feedback after call Reputation System, Limited-Use Address, Payments at Risk, Litigation

SPIT Prevention Techniques Blacklists & Whitelists Pros: Simplementation Effective (users in whitelist will always be allowed through and vice versa) Cons: Manual data gathering by user or global service required to build such lists SPITTERS can easily spoof identity and bypass lists

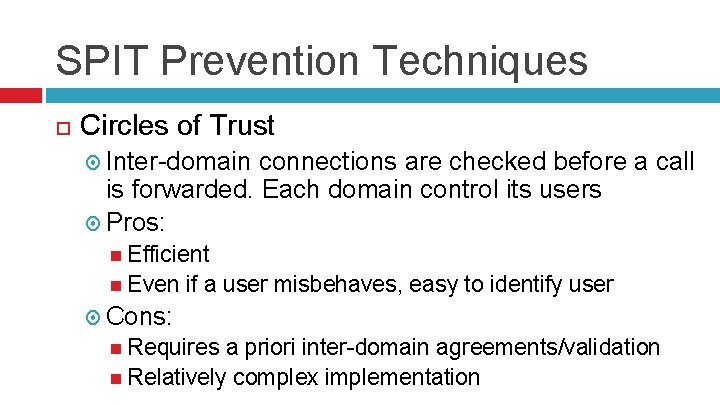
SPIT Prevention Techniques Circles of Trust Inter-domain connections are checked before a call is forwarded. Each domain control its users Pros: Efficient Even if a user misbehaves, easy to identify user Cons: Requires a priori inter-domain agreements/validation Relatively complex implementation

SPIT Prevention Techniques Pattern/Anomaly Detection Statistical analysis of a user’s calling behavior based on studies that identify “normal” call behavior. Pros: Potentially most acurate Mature methodology Cons: Requires monitoring agent to keep track of user behavior Never before implemented to voice calls

SPIT Prevention Techniques Graylisting Consists of calculating a gray level for each and every caller Gray level determines how likely a caller is to be a SPITTER

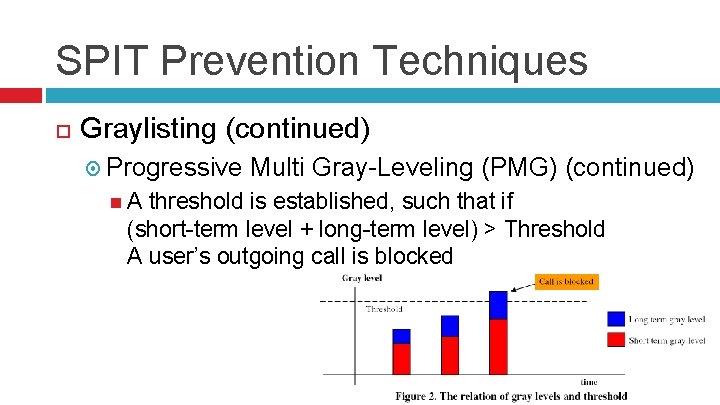
SPIT Prevention Techniques Graylisting (continued) Progressive Multi Gray-Leveling (PMG) Considers two levels per caller: short-term level and long-term level Short-term level considers the number of calls a given user places within a short period of time (i. e. 10 min) Level changes rapidly - Prevents Do. S attacks Long-term level considers the number of calls a given user places within a long period of time (i. e. 10 hours) Level changes slowly – prevents SPITTER from regaining calling rights

SPIT Prevention Techniques Graylisting (continued) Progressive A Multi Gray-Leveling (PMG) (continued) threshold is established, such that if (short-term level + long-term level) > Threshold A user’s outgoing call is blocked

SPIT Prevention Techniques Graylisting (continued) Pros: Effective caller limiting approach Relatively simplementation Makes a SPITTER’s task much harder Cons: Legitimate users can potentially have calls blocked just for placing too many calls within a given time frame.

SPIT Prevention Techniques Computational Puzzle Verify a caller’s “willingness” to place the call by imposing that the client solves a digital puzzle/calculation prior to call establishment Caller must spend at least a given minimum period of time to ensure solution is not “guessed” Pros: Limit a SPITTER’s calling rate by adding required computational overhead to establish Cons: Increased overhead for call establishment Could be relatively easily circumvented

SPIT Prevention Techniques Sender Check Verify/authenticate a caller by actively consulting its domain Equivalent of Sender Policy Framework (SPF) and Sender ID in email Pros: Originating domain certifies its users Prevents user ID spoofing Cons: Relies on remote domain information that may not be correctly implemented or updated

SPIT Prevention Techniques Turing Test Differentiate between automated computer placed calls (likely SPIT) and calls placed by human beings Uses Audio Completely Automated Public Turing test to tell Computers and Humans Apart (CAPTCHAS) Pros: Quickly and easily identify automated vs. human calls Cons: Increased overhead for connection establishment Could potentially block non-SPIT automated calls (banks, package delivery notifications, reverse 911, etc)

SPIT Prevention Techniques Consent-Based Communication User authentication / identity verification Callee authoizes caller a priori with a previously exchanged key or passphrase Pros: SPIT is completely blocked, since only authorized callers can place call to user Cons: Any new caller who wishes to contact a user must request and receive the shared key a priori

SPIT Prevention Techniques Content Filtering Process call content to detect SPIT as done in SPAM filters Pros: If viable, would be the most accurate technique Cons: Not viable / implementable. Although there exist DSP algorithms to analyze audio data and convert audio waveforms to ASCII text, process is not real-time and call contents are not available for processing until after the call is actually placed.

SPIT Prevention Techniques Reputation System Centralized reputation score based on user behavior and other users’ feedback Pros: Centralized global resource to identify SPITTERS Cons: Requires protocol standardization for feedback framework

SPIT Prevention Techniques Payments at Risk Require a refundable payment for each call from an unknown party. The payment is only refunded if the caller was not a SPITTER. Pros: Increase cost / decrease profitability of SPIT Cons: Quite unrealistic scenario, since a standardized framework would be required for feedback and payment charging and many Vo. IP services are free and fully p 2 p

Lab Vo. IP Testbed

Lab Exercises Students will: Configure and setup the Vo. IP testbed Establish an authenticated Vo. IP call and notice a SPITTER’s inability to contact a user that requires caller authentication Create a SPIT message Place an automated SPIT call by capturing and replaying the SPIT message created above Place an automated SPIT call with a spoofed ID

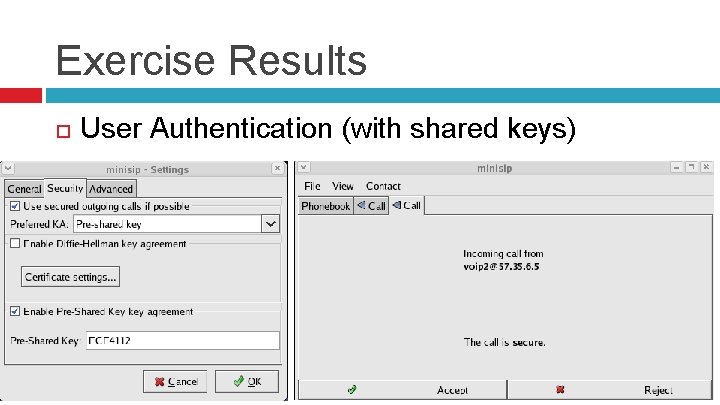
Exercise Results User Authentication (with shared keys)

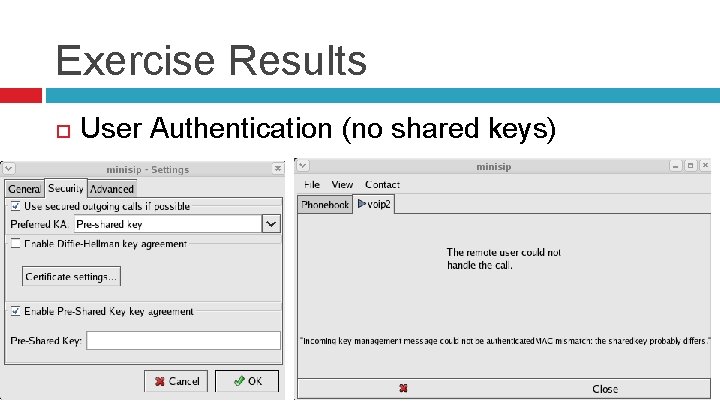
Exercise Results User Authentication (no shared keys)

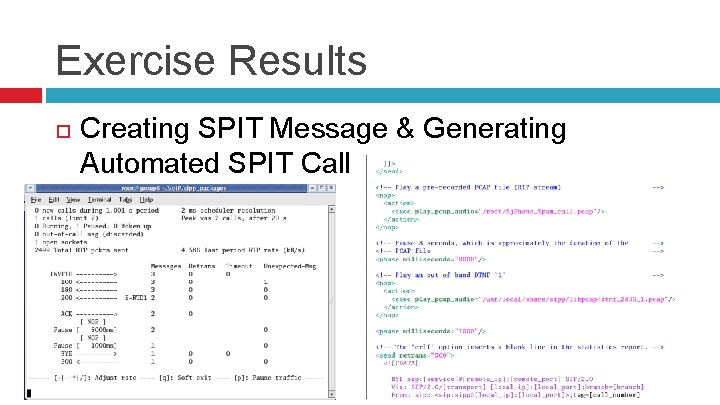
Exercise Results Creating SPIT Message & Generating Automated SPIT Call

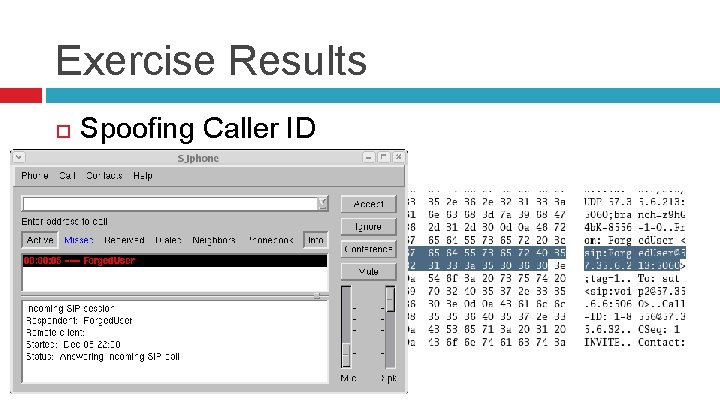
Exercise Results Spoofing Caller ID

References J. Quittek, S. Niccolini, S. Tartarelli, and R. Schlegel, “Prevention of Spam over IP Telephony, ” NEC Technical Journal, vol. 1, no. 2, Feb. , pp. 114 -119, 2006. D. Shin and C. Shim, “Voice Spam Control with Gray Leveling, ” Proceedings of 2 nd Vo. IP Security Workshop, Washington DC, June 1 -2 2005. F. Hammer et al. “Elements of Interactivity in Telephone Conversations, ” Proceedings of 8 th International Conference on Spoken Language Processing (ICSLP/INTERSPEECH 2004), Vol 3, pp. 1741 -1744, Jeju Island, Korea, Oct. 2004.