Exposing LTE Security Weaknesses at Protocol Inter Layer








- Slides: 24

Exposing LTE Security Weaknesses at Protocol Inter -Layer, and Inter-Radio Interactions Muhammad Taqi Raza, Fatima Muhammad Anwar and Songwu Lu University of California – Los Angeles

Ubiquitous Cellular Services • 4. 8 billion unique mobile subscribers • Supports voice and multimedia services 2

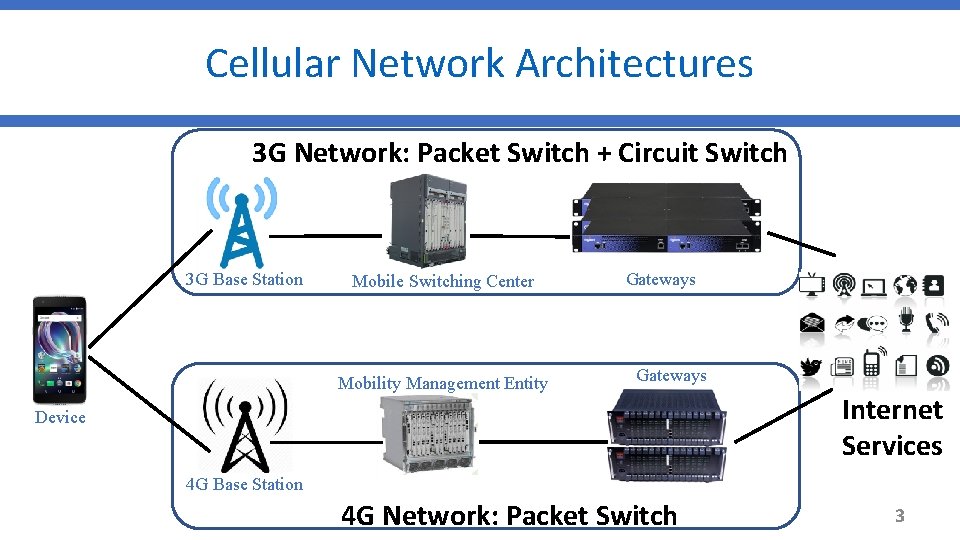
Cellular Network Architectures 3 G Network: Packet Switch + Circuit Switch 3 G Base Station Mobile Switching Center Mobility Management Entity Gateways Device Internet Services 4 G Base Station 4 G Network: Packet Switch 3

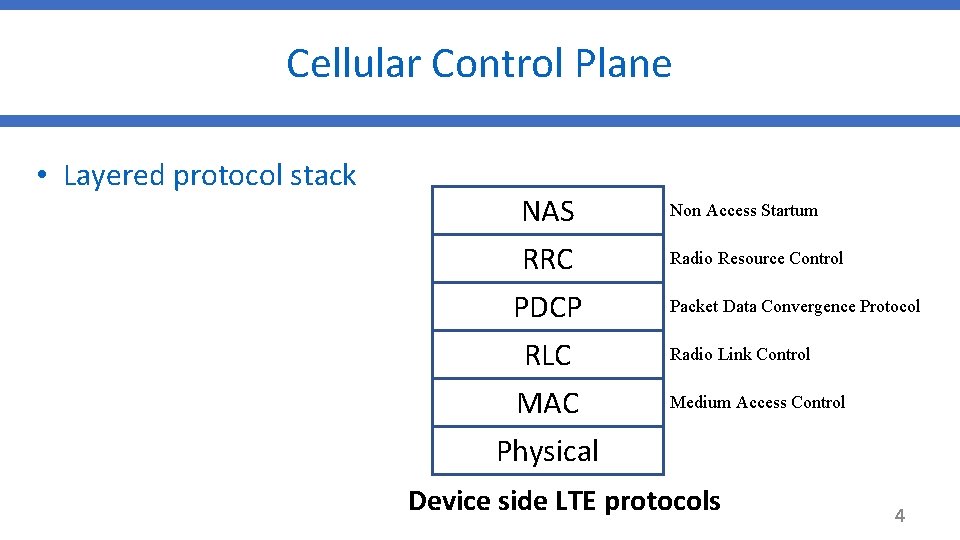
Cellular Control Plane • Layered protocol stack NAS RRC PDCP RLC MAC Physical Non Access Startum Radio Resource Control Packet Data Convergence Protocol Radio Link Control Medium Access Control Device side LTE protocols 4

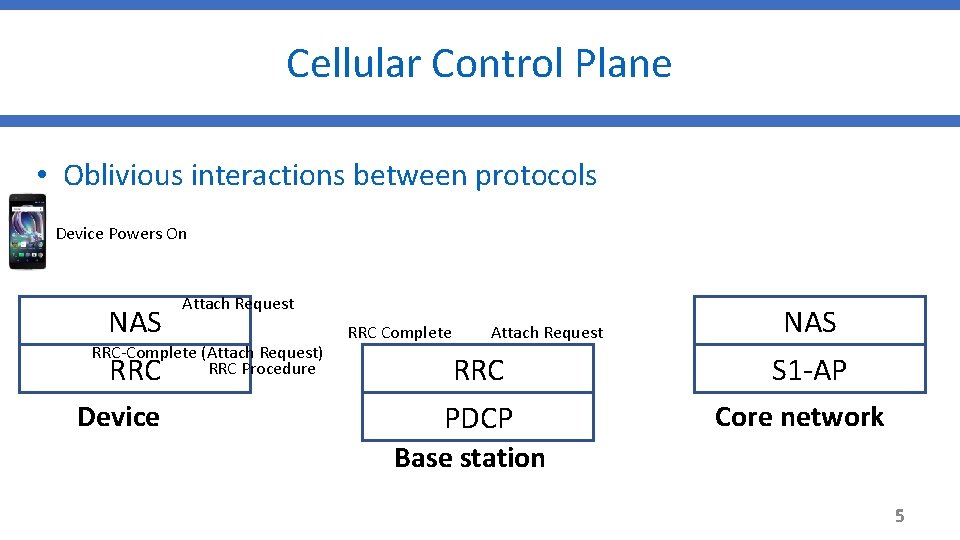
Cellular Control Plane • Oblivious interactions between protocols Device Powers On Attach Request NAS RRC-Complete (Attach Request) RRC Procedure Device RRC Complete Attach Request RRC PDCP NAS S 1 -AP Core network Base station 5

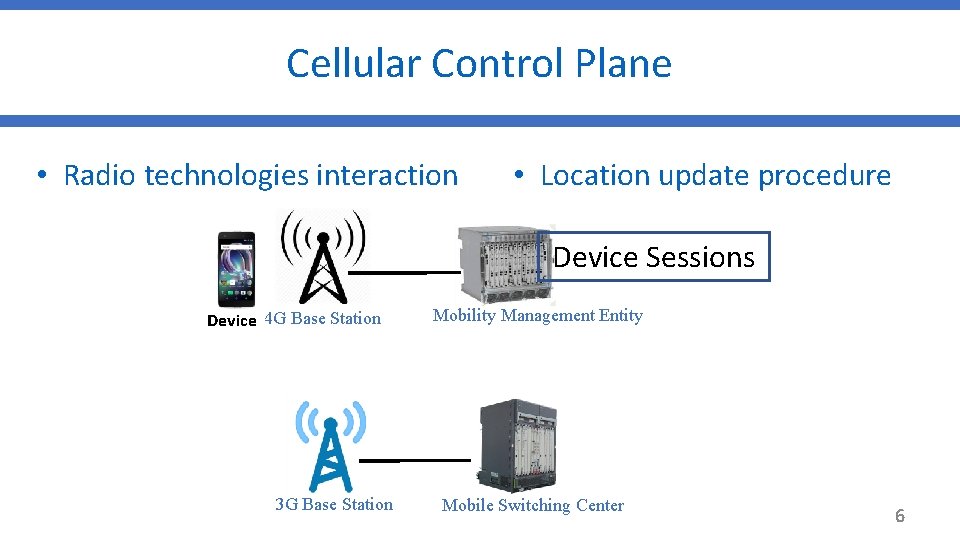
Cellular Control Plane • Radio technologies interaction • Location update procedure Device Sessions Device 4 G Base Station 3 G Base Station Mobility Management Entity Mobile Switching Center 6

Are the interaction between LTE protocols and cellular radio technologies secure ?

Findings Overview Weak Authentication: Non-Authentic Messages are Accepted • Why? – Network executes the message (even the message integrity check fails) when device is transitioning from idle to connected state. • Attack – Detach the victim from the network 8

Findings Overview Weak Security Association: Security Handshake is Skipped on Inter -Radio Communication • Why? – Security context mismatches between device and the target radio technology during inter-radio switch. • Attack – Rendering device to be unreachable from the network 9

Findings Overview Lack of Access Control/Non-Authorization • Why? – Device does not have authorization process • Attack – Draining victims’ battery 10

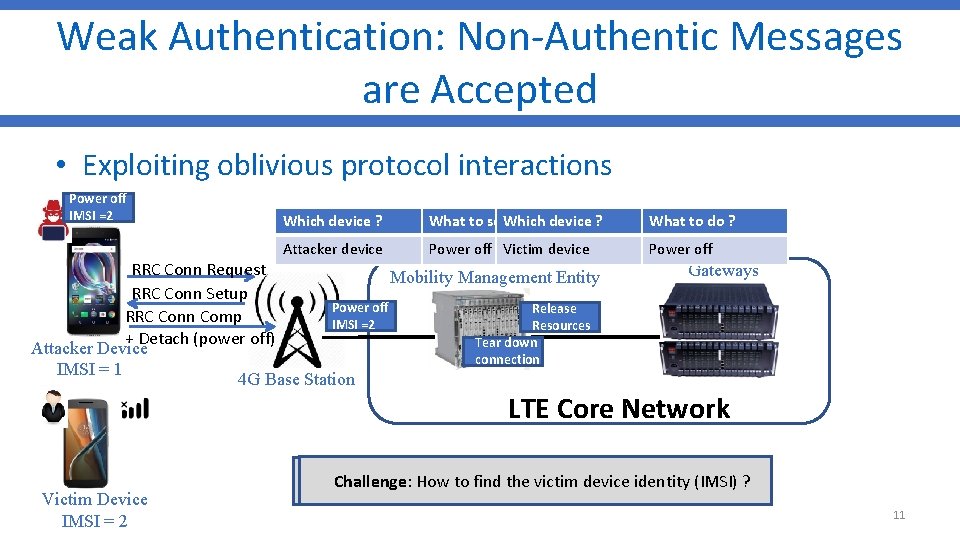
Weak Authentication: Non-Authentic Messages are Accepted • Exploiting oblivious protocol interactions Power off IMSI =2 Which device ? What to send Which ? device ? What to do ? Attacker device Power off NAS Victim msgdevice Power off RRC Conn Request Mobility Management Entity RRC Conn Setup Power off Release RRC Conn Comp IMSI =2 Resources + Detach (power off) Tear down Attacker Device connection IMSI = 1 4 G Base Station Gateways LTE Core Network Victim Device IMSI = 2 Why: LTE standard allows the MME to process Detach Request Challenge: How to the victim (IMSI) ? message with power offfind condition evendevice if the identity device MAC fails 11

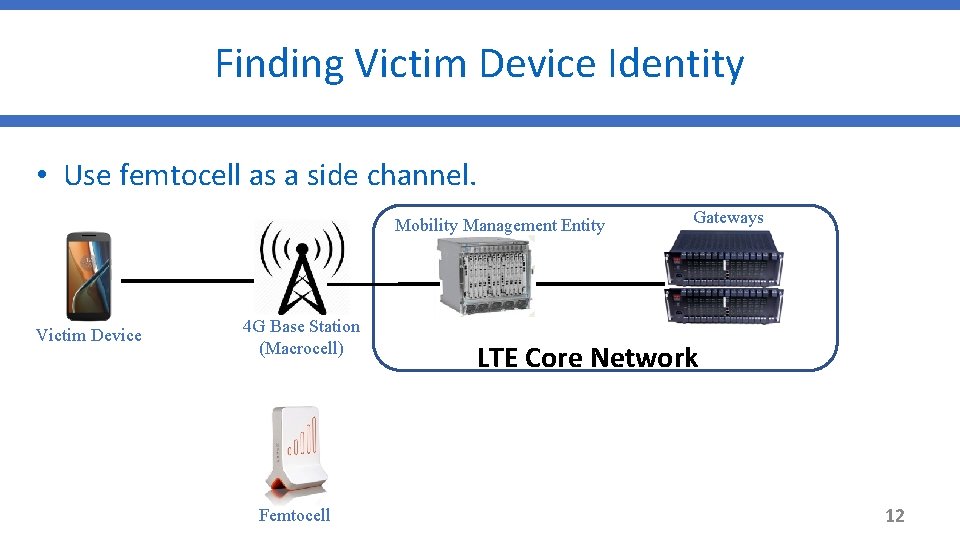
Finding Victim Device Identity • Use femtocell as a side channel. Mobility Management Entity Victim Device 4 G Base Station (Macrocell) Femtocell Gateways LTE Core Network 12

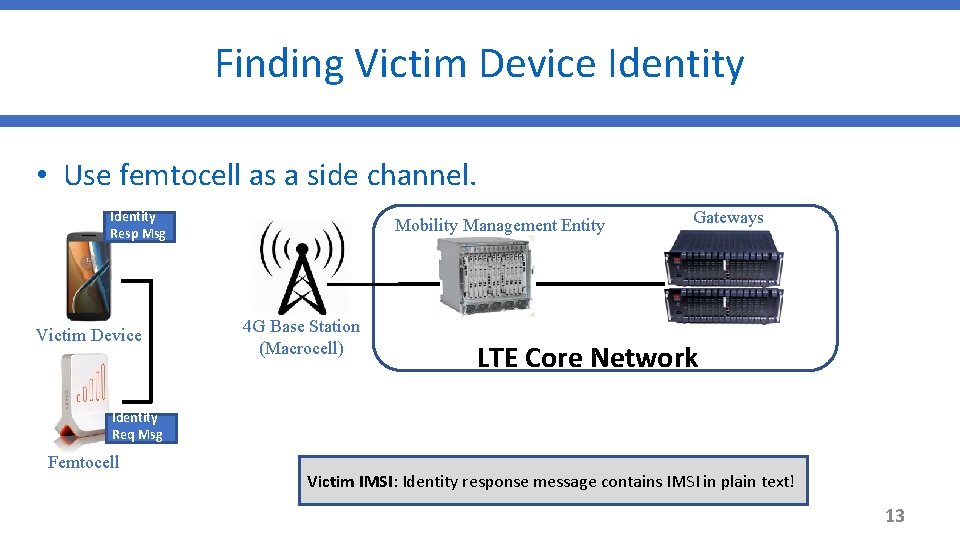
Finding Victim Device Identity • Use femtocell as a side channel. Identity Resp Msg Victim Device Mobility Management Entity 4 G Base Station (Macrocell) Gateways LTE Core Network Identity Req Msg Femtocell Victim IMSI: Identity response message contains IMSI in plain text! 13

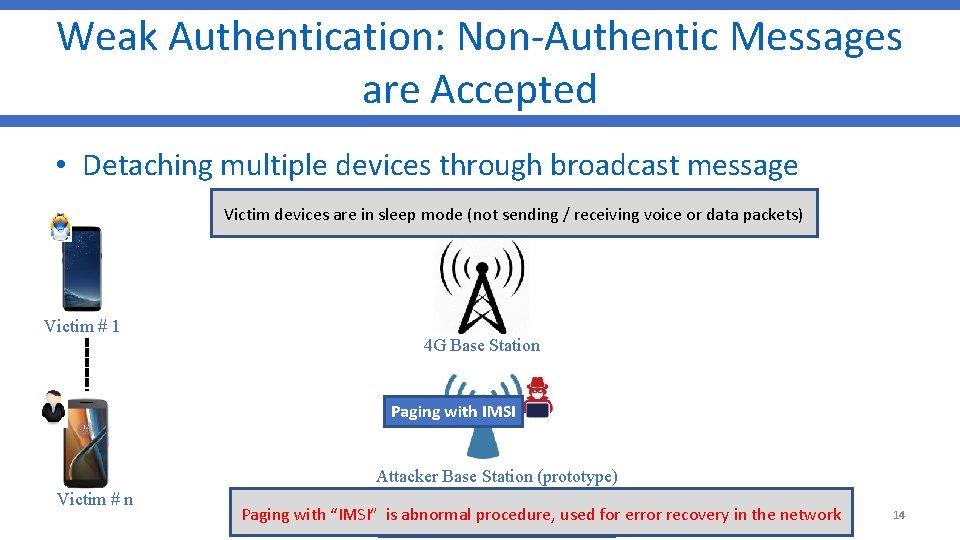
Weak Authentication: Non-Authentic Messages are Accepted • Detaching multiple devices through broadcast message Victim devices are in sleep mode (not sending / receiving voice or data packets) Victim # 1 4 G Base Station Paging with IMSI Attacker Base Station (prototype) Victim # n is a broadcast message Paging with “IMSI” Paging is abnormal procedure, used for error recovery in the network 14

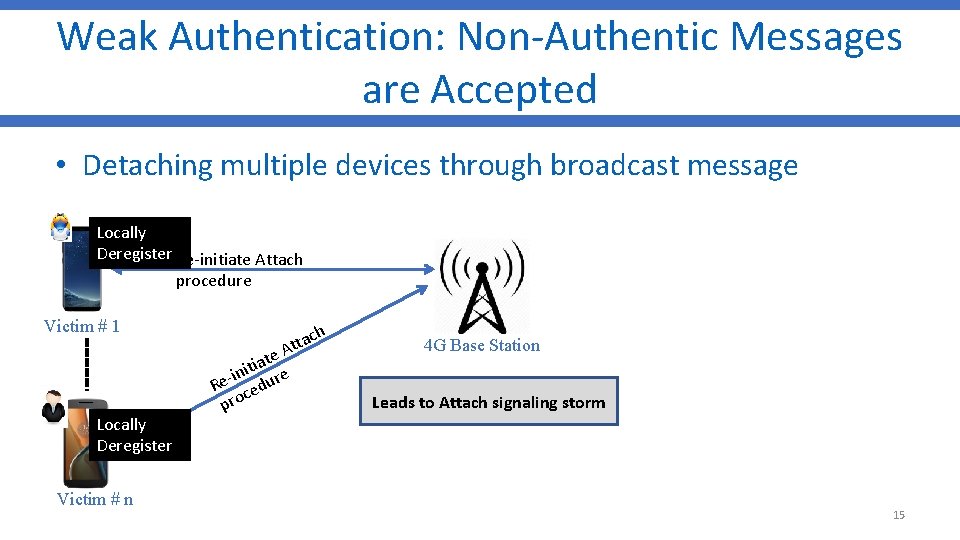
Weak Authentication: Non-Authentic Messages are Accepted • Detaching multiple devices through broadcast message Locally Deregister Re-initiate Attach procedure Victim # 1 Locally Deregister Victim # n ch a Att ate i t i in ure e R ced pro 4 G Base Station Leads to Attach signaling storm 15

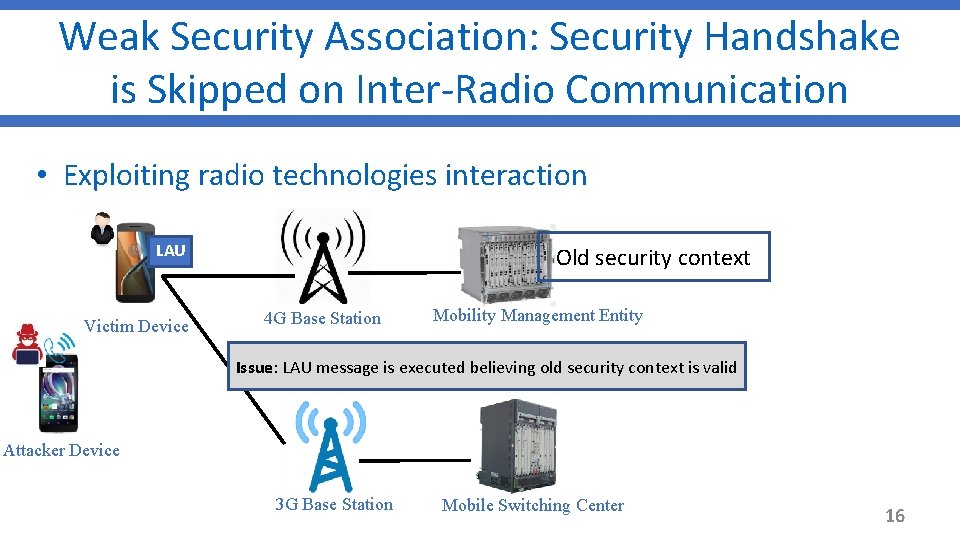
Weak Security Association: Security Handshake is Skipped on Inter-Radio Communication • Exploiting radio technologies interaction LAU Victim Device Old security context 4 G Base Station Mobility Management Entity Issue: LAU message is executed believing old security context is valid Attacker Device 3 G Base Station Mobile Switching Center 16

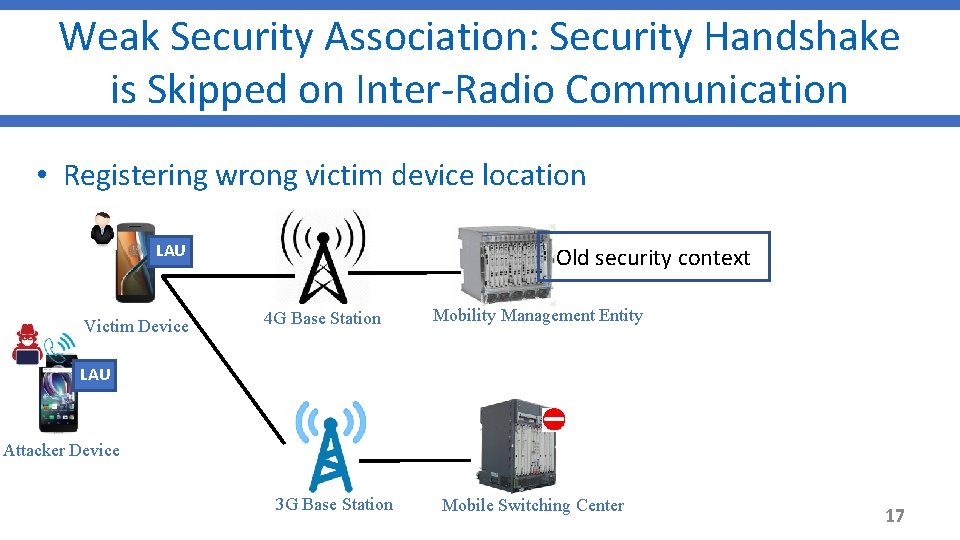
Weak Security Association: Security Handshake is Skipped on Inter-Radio Communication • Registering wrong victim device location LAU Victim Device Old security context 4 G Base Station Mobility Management Entity LAU Attacker Device 3 G Base Station Mobile Switching Center 17

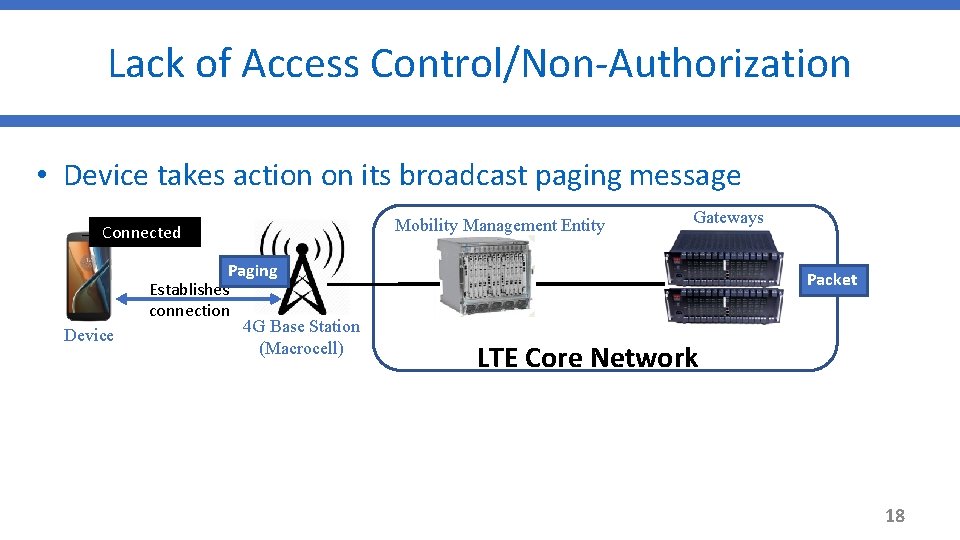
Lack of Access Control/Non-Authorization • Device takes action on its broadcast paging message Idle Connected Device Paging Establishes connection 4 G Base Station (Macrocell) Mobility Management Entity Gateways Packet LTE Core Network 18

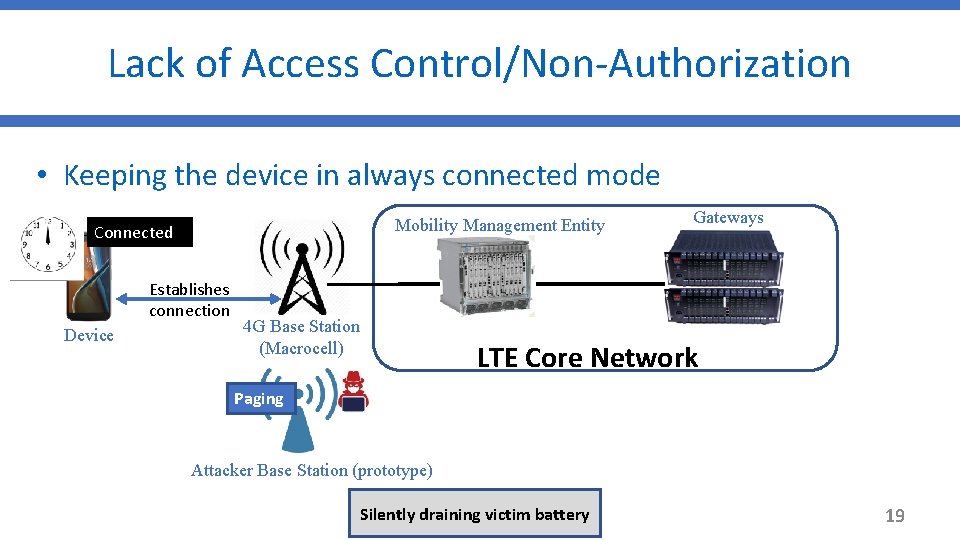
Lack of Access Control/Non-Authorization • Keeping the device in always connected mode Mobility Management Entity Idle Connected Establishes connection Device 4 G Base Station (Macrocell) Gateways LTE Core Network Paging Attacker Base Station (prototype) Silently draining victim battery 19

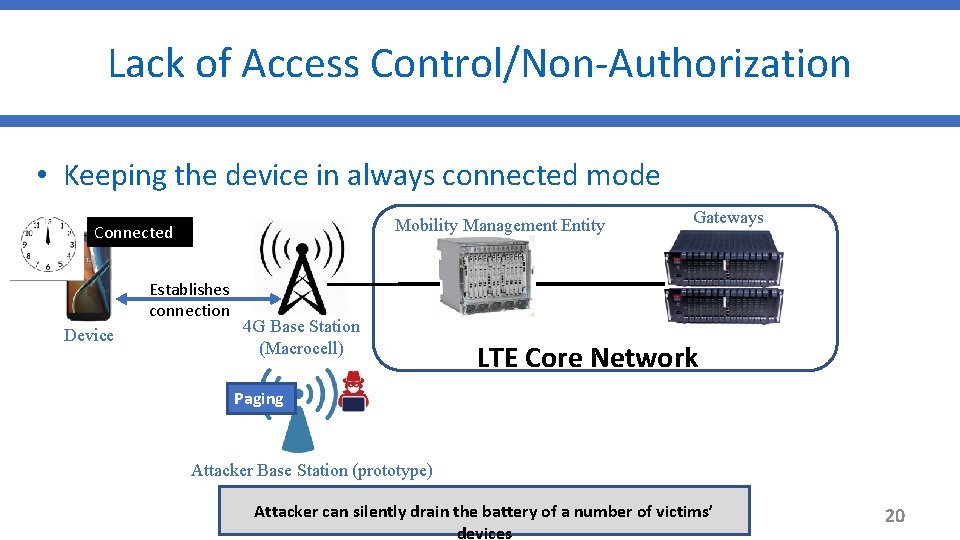
Lack of Access Control/Non-Authorization • Keeping the device in always connected mode Mobility Management Entity Idle Connected Establishes connection Device 4 G Base Station (Macrocell) Gateways LTE Core Network Paging Attacker Base Station (prototype) Attacker can silently drain the battery of a number of victims’ devices 20

Methodology • Vulnerabilities are validated in operational LTE networks • Logs were gathered by changing device non-volatile memory • Attacks were gathered in control prototype environment 21

Suggested Remedies • Detach attack prevention – Network should consult its database to resolve device radio and corenetwork identities • Location update hijack attack prevention – The device should re-authenticate whenever it switches its radio technology • Battery drain attack prevention – The device should keep a mapping between paging request and gaining network resource 22

Conclusion • Found new vulnerabilities in standardized LTE protocol operations • We propose that no message is executed without integrity protection • The broadcast messages must also be integrity protected 23

Conclusion • Found new vulnerabilities in standardized LTE protocol operations • We propose that no message is executed without integrity protection • The broadcast messages must also be integrity protected 23