EXPLOITATION By Joshua Schwartz Overview What is it

EXPLOITATION By Joshua Schwartz

Overview � What – is it? � Why – do I care? � How – is it done? � Where – can I find more info?

What � � � Buffer Overflow: Input into a buffer overflows into memory corrupting it and changing the flow of execution. Robert Morris worm 1988 Most basic memory corruption My example is best/worst case scenario Current real world examples are much more complex

Why � If you want to be a Pen-tester this is where you need to start � Things like buffer overflows often defined but not demonstrated � Understanding how the attack works can help protect from it. � It is fun

How: Buffer Overflow � � � Oversized input – “fuzzing” Program Crashes Data in the stack can get overwritten with the input Best case scenario is that the EIP and ESP registers are both overwritten The input is then tailored to overwrite the return address with a memory address that contains our payload
Ability Server

Crashing the Program � � We send “AAAA…” to the ftp server with a STOR function. The program crashes We link a debugger to the program and crash it again We then examine the state of the program the moment it crashed
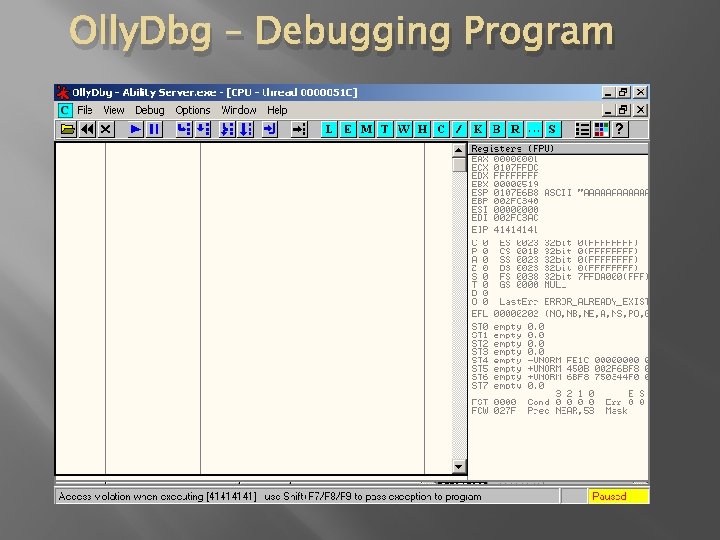
Olly. Dbg – Debugging Program
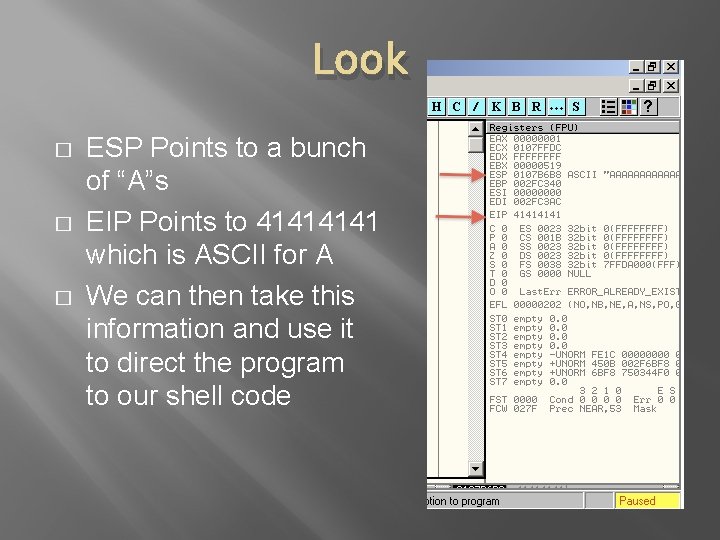
Look � � � ESP Points to a bunch of “A”s EIP Points to 4141 which is ASCII for A We can then take this information and use it to direct the program to our shell code

Automated with Tools � � � This is part of the process used to develop exploits These Exploits are packaged into frameworks like Metasploit or Core. Impact This makes it much quicker to reuse previously discovered exploits

Where to find more Info Lectures and Resources from NYU-Poly course http: //pentest. cryptocity. net/ � � Hacking: The Art of Exploitation Book � Certified Ethical Hacker Offensive Security Certified Professional www. offensive-security. com �

Final Thoughts � Discussed why this is important � Talked about Buffer Overflows � If you are interested in this you now know where to find it.

Where to find more Info Lectures and Resources from NYU-Poly course http: //pentest. cryptocity. net/ � � Hacking: The Art of Exploitation Book � Certified Ethical Hacker Offensive Security Certified Professional www. offensive-security. com �
- Slides: 13