Exploit Helpers Contents 1 Who Am I 2


![How IDA Pro works? DWORD PTR [esp+0 x 8], 0 x 3 mov DWORD How IDA Pro works? DWORD PTR [esp+0 x 8], 0 x 3 mov DWORD](https://slidetodoc.com/presentation_image_h2/60b6e126ea8d084e553215e4c3739fa5/image-9.jpg)



- Slides: 25

박주현 Exploit Helpers

Contents 1. Who Am I 2. Exploit sequence 1. Checking protection in binary – checksec. sh 2. Finding exploitable vector – IDA Pro, Gdb-peda, Qira, Core dump 3. Exploit – Pwntools

Who Am I Xㅡ ㅁ Terminal cdor 1@Ubuntu ~$ whoami 1. 누구세요? Name = 박 주 현 Nick = cdor 1 Age = 17 School = 한세사이버보안고등학교 해킹보안과 Team = H 3 X 0 R Belong to = 서울여대정보보호영재교육원 3기, KSIA 2. 뭐 좋아하세요? Pwnable, Reversing 3. 뭐 하고 계세요? Pwnable. kr 문제풀이. . Heap exploit 공부. . OS 원리 공부. . arm, mips공부. . cdor 1@Ubuntu ~$ https: //fb. com/parkcdor 1

Exploit sequence 1. Checking protection in binary - checksec. sh 2. Finding exploitable vector Static analyze : IDA Pro Dynamic analyze : Gdb-peda, Qira, Core dump 3. Exploit - Pwntools

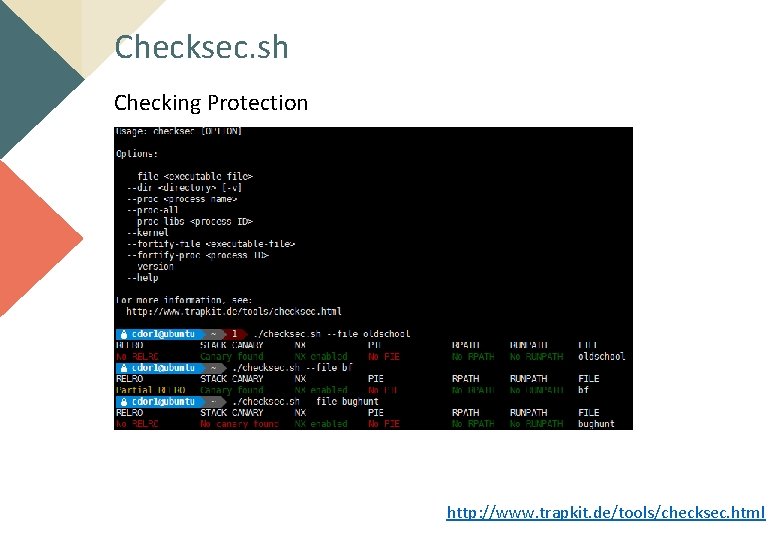
Checksec. sh Checking Protection http: //www. trapkit. de/tools/checksec. html

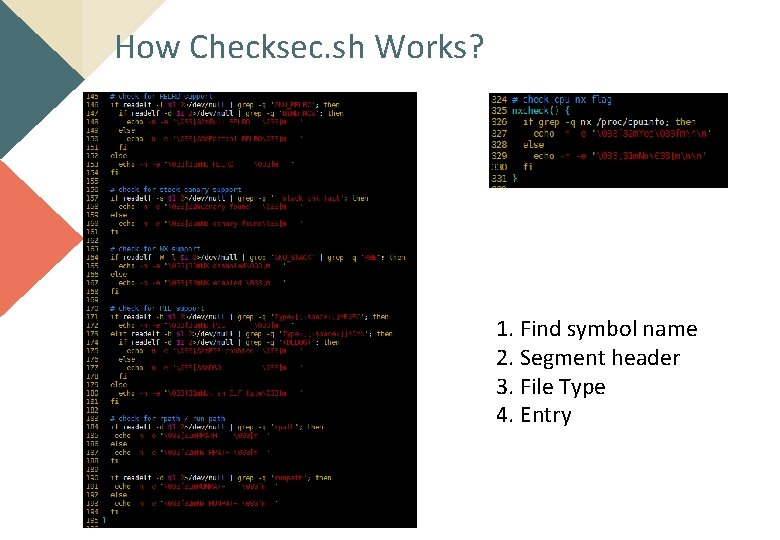
How Checksec. sh Works? 1. Find symbol name 2. Segment header 3. File Type 4. Entry

Exploit sequence 1. Checking protection in binary - checksec. sh 2. Finding exploitable vector Static analyze : IDA Pro Dynamic analyze : Gdb-peda, Qira, Core dump 3. Exploit - Pwntools

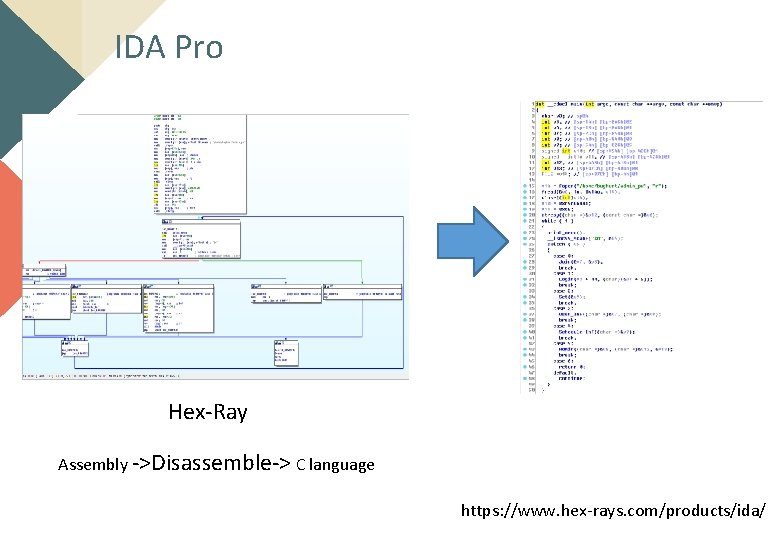
IDA Pro Hex-Ray Assembly ->Disassemble-> C language https: //www. hex-rays. com/products/ida/
![How IDA Pro works DWORD PTR esp0 x 8 0 x 3 mov DWORD How IDA Pro works? DWORD PTR [esp+0 x 8], 0 x 3 mov DWORD](https://slidetodoc.com/presentation_image_h2/60b6e126ea8d084e553215e4c3739fa5/image-9.jpg)
How IDA Pro works? DWORD PTR [esp+0 x 8], 0 x 3 mov DWORD PTR [esp+0 x 4], 0 x 2 mov DWORD PTR [esp], 0 x 1 call 0 x 80483 c 4 <babo> mov edx, DWORD PTR [ebp+0 x 8] mov DWORD PTR [esp+0 x 4], edx mov DWORD PTR [esp], eax call 0 x 80482 f 4 <printf@plt> (gdb) x/s 0 x 8048510: "%dn" Automate hand-ray into Algorithm babo(1, 2, 3); printf(“%dn”, argv[1]);

Exploit sequence 1. Checking protection in binary - checksec. sh 2. Finding exploitable vector Static analyze : IDA Pro Dynamic analyze : Gdb-peda, Qira, Core dump 3. Exploit - Pwntools

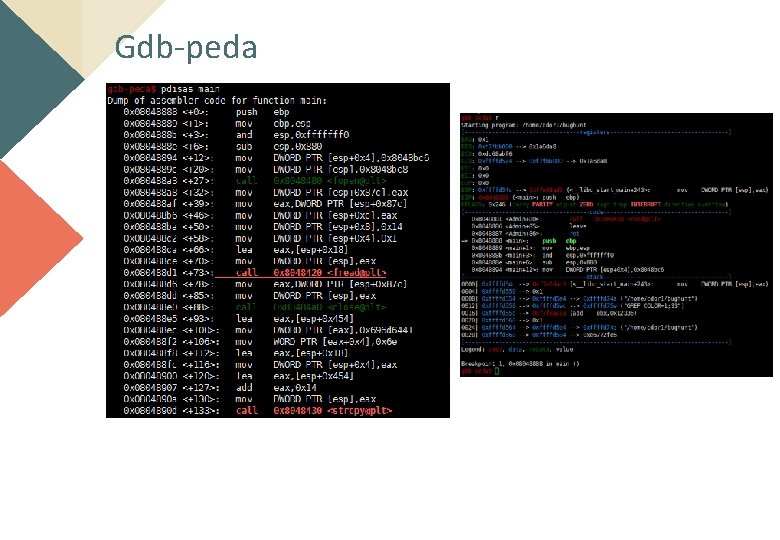
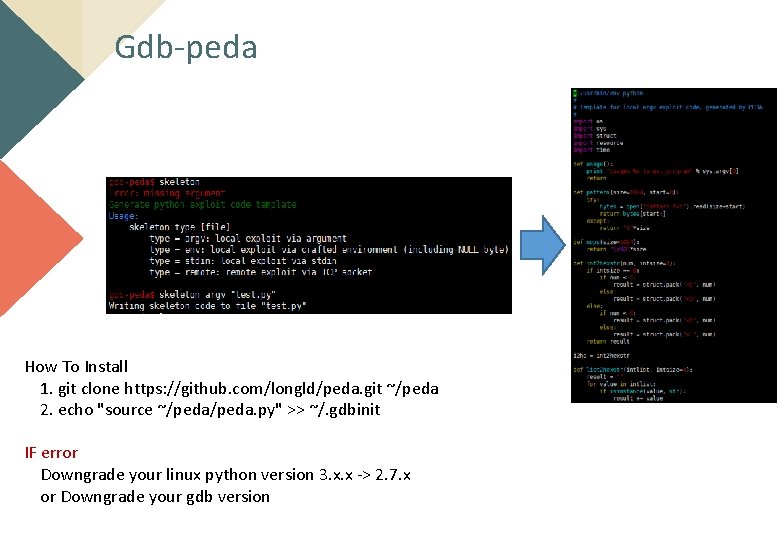
Gdb-peda

Gdb-peda How To Install 1. git clone https: //github. com/longld/peda. git ~/peda 2. echo "source ~/peda. py" >> ~/. gdbinit IF error Downgrade your linux python version 3. x. x -> 2. 7. x or Downgrade your gdb version

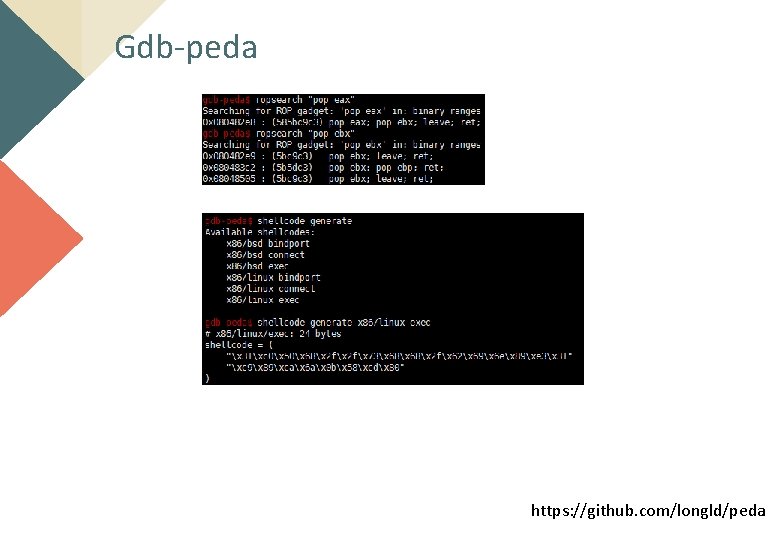
Gdb-peda https: //github. com/longld/peda

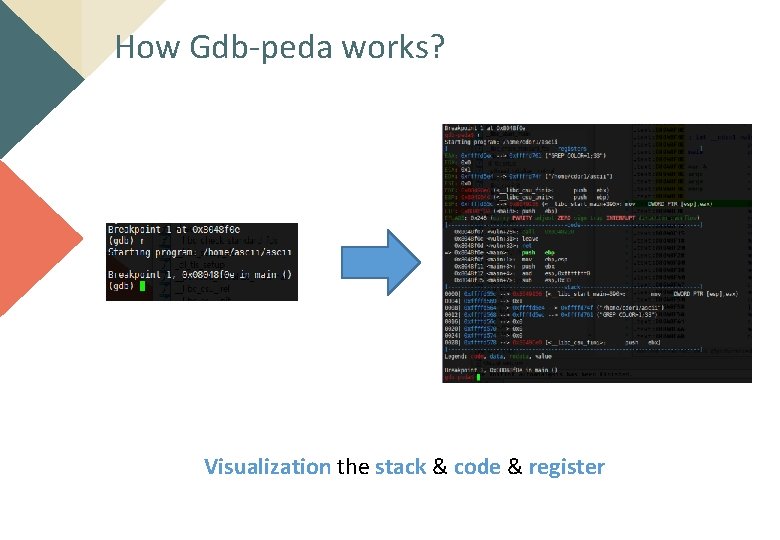
How Gdb-peda works? Visualization the stack & code & register

Exploit sequence 1. Checking protection in binary - checksec. sh 2. Finding exploitable vector Static analyze : IDA Pro Dynamic analyze : Gdb-peda, Qira, Core dump 3. Exploit - Pwntools

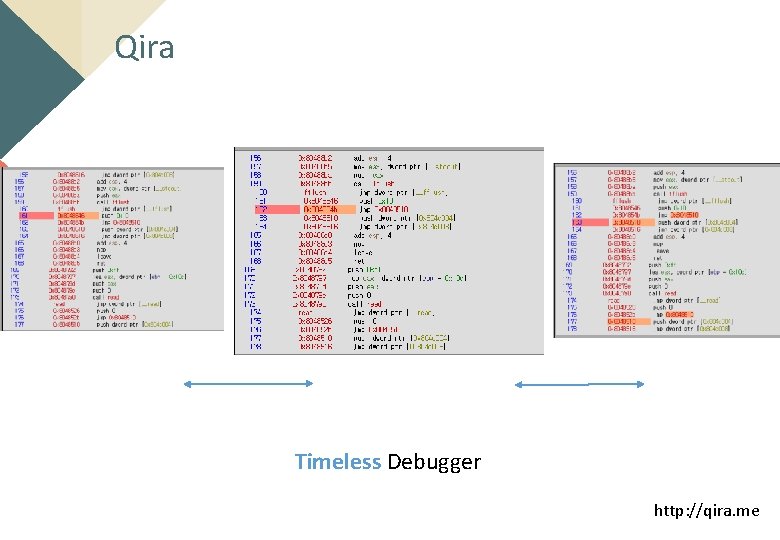
Qira Timeless Debugger http: //qira. me

How Qira works? Save the status at the Previous command

Exploit sequence 1. Checking protection in binary - checksec. sh 2. Finding exploitable vector Static analyze : IDA Pro Dynamic analyze : Gdb-peda, Qira, Core dump 3. Exploit - Pwntools

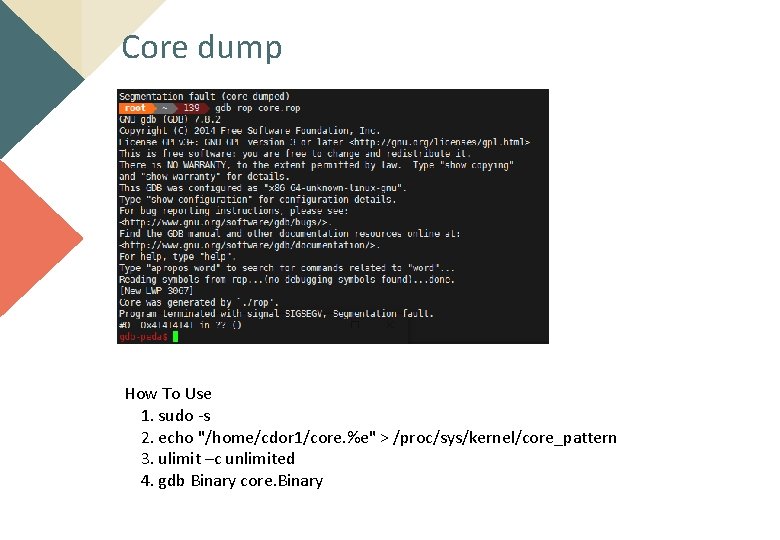
Core dump How To Use 1. sudo -s 2. echo "/home/cdor 1/core. %e" > /proc/sys/kernel/core_pattern 3. ulimit –c unlimited 4. gdb Binary core. Binary

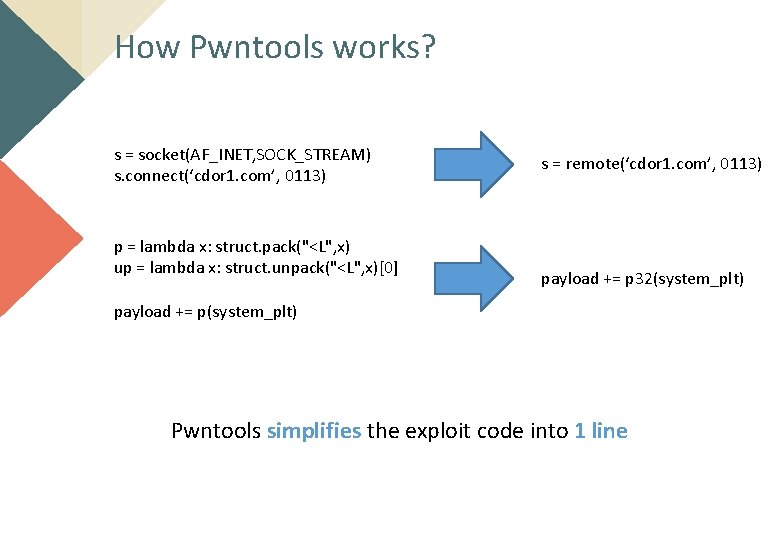
How Core dump works? When the interruption occurred, system makes core dump Like SIGSEGV 0 x 4141 in () ?

Exploit sequence 1. Checking protection in binary - checksec. sh 2. Finding exploitable vector Static analyze : IDA Pro Dynamic analyze : Gdb-peda, Qira, Core dump 3. Exploit - Pwntools

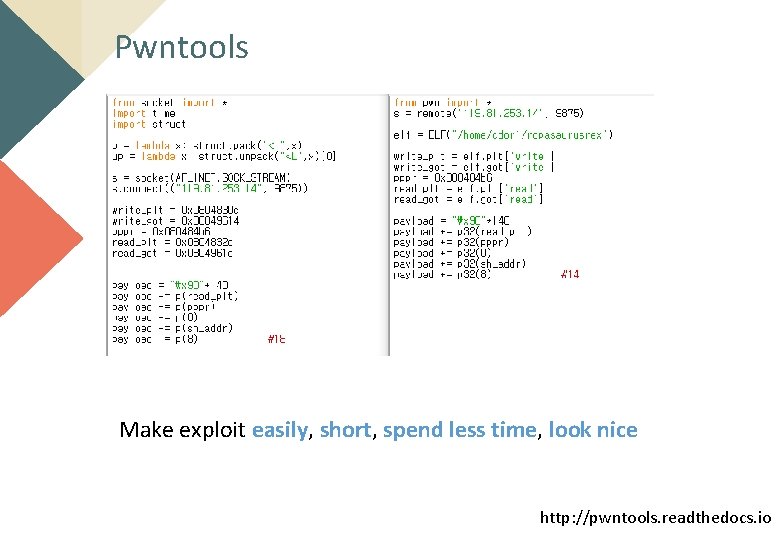
Pwntools Make exploit easily, short, spend less time, look nice http: //pwntools. readthedocs. io

How Pwntools works? s = socket(AF_INET, SOCK_STREAM) s. connect(‘cdor 1. com’, 0113) p = lambda x: struct. pack("<L", x) up = lambda x: struct. unpack("<L", x)[0] s = remote(‘cdor 1. com’, 0113) payload += p 32(system_plt) payload += p(system_plt) Pwntools simplifies the exploit code into 1 line

Practice With Plaid CTF 2013 Ropasaurusrex

THANK YOU http: //cdor 1. tistory. com