Exeter IT Secure by Design Our Mission We

Exeter IT – Secure by Design

Our Mission We will develop and deliver a robust approach to IT security that will define what “good security” looks like; build information security in to all services by design; and deliver demonstrable security and compliance to better protect and serve the University.

Secure by Design Process We need a coherent and consistent secure-by-design process to cover the University’s information security requirements for all new and existing technologies and to support the University’s legislative requirements and strategic digital journey.

Secure by Design Process The process will be proportionate so that: • All security objectives are identified early and become part of project requirements; • Effort and attention is focussed where it will have the greatest impact; • Risks are managed effectively in accordance with the criticality of the service and/or data; and • The appropriate level of assurance is obtained for compliance purposes.
Secure by Design Process By adopting such a process the University will avoid common issues within projects / new and existing services: • Not fully understanding the extent and scope of all security requirements, e. g. NHS DSPT; • Failing to consider, and manage, third-party security requirements; and • Failing to identify, and perform, key assurance activities, e. g. penetration testing; • Managing end of life and unsupported services.
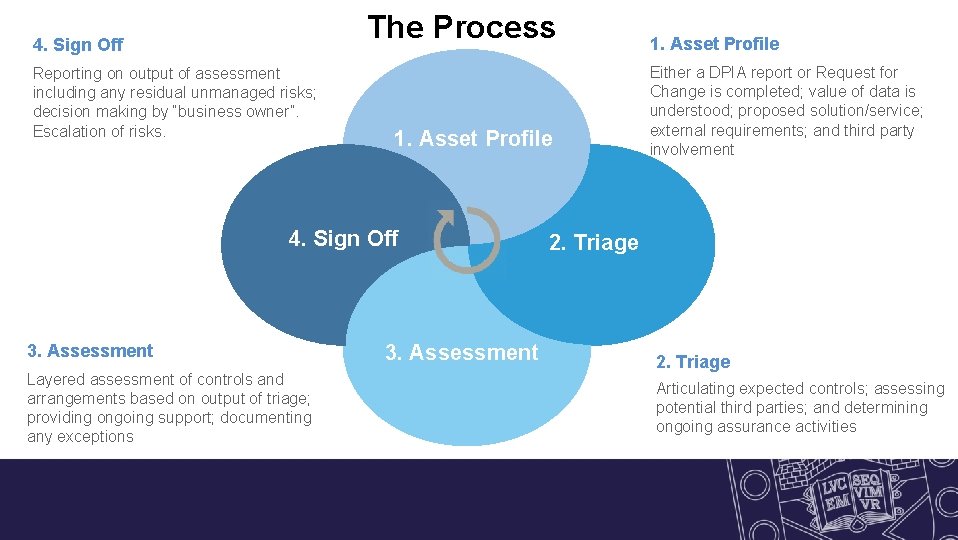
The Process 4. Sign Off Reporting on output of assessment including any residual unmanaged risks; decision making by “business owner”. Escalation of risks. 1. Asset Profile 4. Sign Off 3. Assessment Layered assessment of controls and arrangements based on output of triage; providing ongoing support; documenting any exceptions 3. Assessment 1. Asset Profile Either a DPIA report or Request for Change is completed; value of data is understood; proposed solution/service; external requirements; and third party involvement 2. Triage Articulating expected controls; assessing potential third parties; and determining ongoing assurance activities
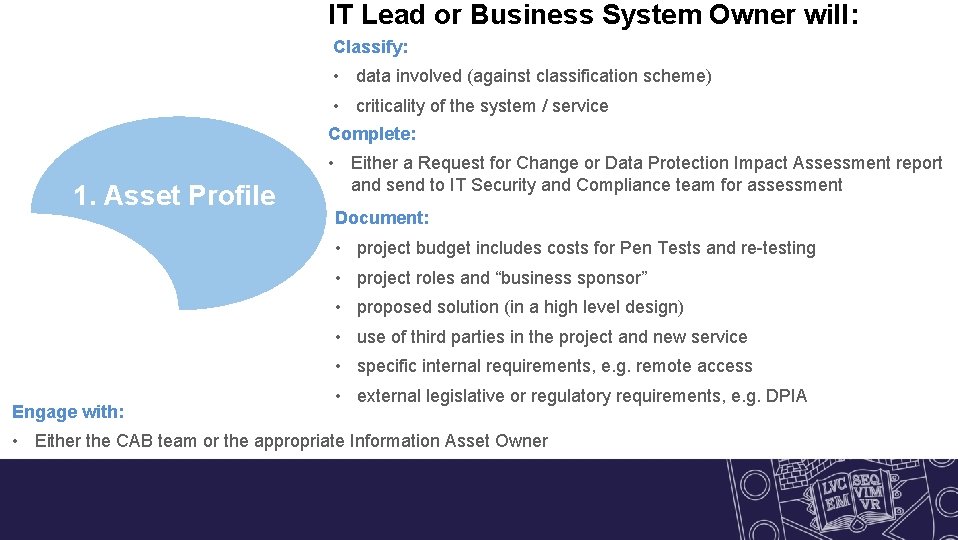
IT Lead or Business System Owner will: Classify: • data involved (against classification scheme) • criticality of the system / service Complete: 1. Asset Profile • Either a Request for Change or Data Protection Impact Assessment report and send to IT Security and Compliance team for assessment Document: • project budget includes costs for Pen Tests and re-testing • project roles and “business sponsor” • proposed solution (in a high level design) • use of third parties in the project and new service • specific internal requirements, e. g. remote access Engage with: • external legislative or regulatory requirements, e. g. DPIA • Either the CAB team or the appropriate Information Asset Owner

IT Security and Compliance Team will: Determine • the risks by reviewing the Request for Change or DPIA document • applicable controls for the change or new service (baseline technical controls) 2. Triage • any additional controls per external requirements • level of assurance and assessment required throughout the project (self assessments – facilitated review – control testing) • third party security requirements (self assessments - facilitated review – independent assurance – onsite visits) • nature of security testing required (non – peer code review – vulnerability scanning – external penetration testing) Document • scope of security work • resource and timing requirements
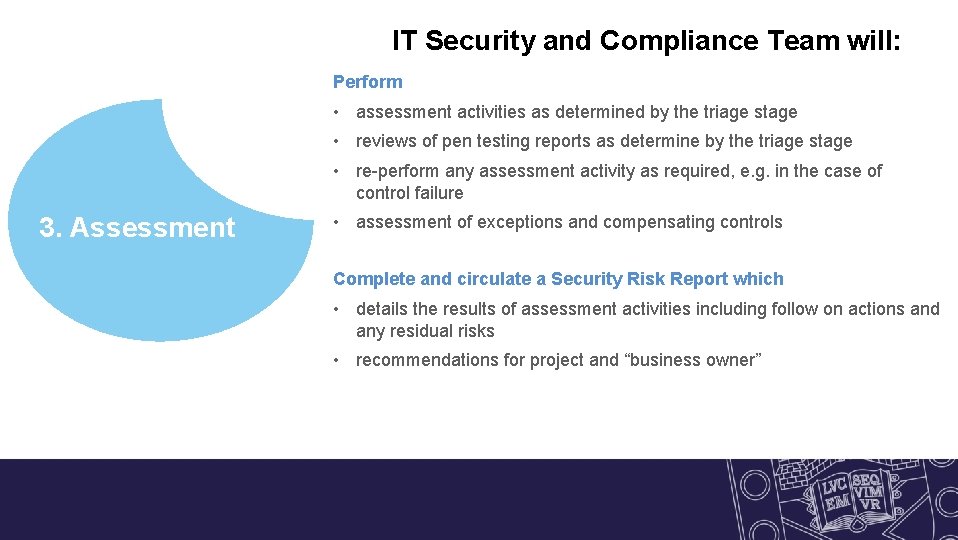
IT Security and Compliance Team will: Perform • assessment activities as determined by the triage stage • reviews of pen testing reports as determine by the triage stage • re-perform any assessment activity as required, e. g. in the case of control failure 3. Assessment • assessment of exceptions and compensating controls Complete and circulate a Security Risk Report which • details the results of assessment activities including follow on actions and any residual risks • recommendations for project and “business owner”
Business System and Information Asset owner will: Consider (as documented in the Security Risk Report) • results of assessment activity and follow on actions 4. Sign Off • recommendations from IT Security & Compliance Team • impact of any residual risks Document • the decision made on how to proceed to be detailed in the Secure by Design Certificate of Approval form and to include any future review points
IT Security and Compliance Team will: Document 4. Sign Off • Details of the Security Risk Report in the exceptions database • Add details of the supplier (if any) in a third party assurance database, including date of next review Review and consider • The Business System Owner and Information Asset Officer’s response to the Security Risk Report
- Slides: 11